La sécurité personnelle commence habituellement avec votre appareil. Les dispositifs plus unsecure sont là, le mieux est le mécanisme derrière les violations de données et les infections de logiciels malveillants. Si, si vous voulez être sûr et son, commencer avec votre appareil.
Sécurité des périphériques et systèmes d'exploitation
Le système d'exploitation de Microsoft a tout à fait la part de marché des utilisateurs. Peut-être que l'une des raisons de Windows est dans la manière de cyberattaques qui, souvent,. Ou peut-être l'intensité des attaques réussies sur Windows est due à l'exécution d'une version obsolète du système d'exploitation?
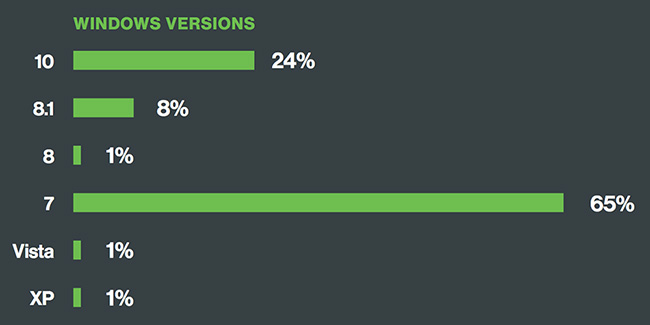
Pour répondre à ces questions ou ou juste pour le plaisir de l'analyse, Sécurité Duo a examiné plus de deux millions d'appareils, plus dont la moitié étaient en cours d'exécution sur une version de Windows.
Les chercheurs ont ensuite découvert que 65 pour cent des périphériques Windows étaient en cours d'exécution sous Windows 7, qui est sensible à plus de 600 les failles de sécurité.
Ce n'est pas le pire. Des dizaines de milliers de machines utilisent encore Windows XP. a été libéré Windows XP 2001. Ce fait signifie que seuls plusieurs scénarios d'attaque littéralement mis à disposition par des centaines de vulnérabilités. Un grand nombre de ces défauts sont de caractère critique.
Il y a beaucoup de raisons pour lesquelles une entreprise préférerait un ancien système d'exploitation sur une nouvelle version
La raison la plus évidente est le coût et le temps nécessaire pour mettre à jour chaque ordinateur et des logiciels dans une organisation. Dans certains cas,, le logiciel de l'entreprise est en cours d'exécution peut ne pas correspondre à plus tard les systèmes d'exploitation et environnements, comme expliqué par Ajay Arora, PDG de Vera.
L'expert estime également que si les entreprises continuent de choisir les fenêtres 7 par rapport aux versions de Windows ultérieures, ils doivent considérer le logiciel de sécurité qui couvre les fonctionnalités qui manquent comme le chiffrement du disque par défaut. "Il se résume à, dépenser de l'argent pour régler la question sous-jacente de l'utilisation d'un système d'exploitation avec une sécurité plus faible, dépenser de l'argent pour mettre à jour les systèmes d'exploitation, ou de dépenser l'argent pour sécuriser la chose que vous essayez de protéger en premier lieu; les données proprement,» Dit Arora.
Le plus gros problème est néanmoins la divulgation continue de nouvelles vulnérabilités. Tout récemment,, Groupe de l'analyse de la menace de Google a révélé un ensemble de défauts zero-day dans Adobe Flash et noyau Microsoft Windows. Cet ensemble de défauts a déjà été exploitée dans la nature contre le navigateur Chrome.
Adobe ont pu rapidement mettre à jour flash contre la CVE-2016-7855
Malheureusement, le bogue du noyau Windows est encore non corrigée. Dans un post du 31 Octobre, Neel Mehta et Billy Leonard du Groupe d'analyse des menaces disent que:
Après 7 journées, par notre politique publié pour exploiter activement les vulnérabilités critiques, aujourd'hui nous dévoilons l'existence d'une vulnérabilité critique qui reste dans Windows pour lesquels aucun conseil ou solution n'a encore été publié. Cette vulnérabilité est particulièrement grave parce que nous savons qu'il est activement exploité.
La vulnérabilité Windows est une escalade des privilèges locaux dans le noyau Windows qui peut être utilisé comme une évasion de bac à sable de sécurité. Elle peut être déclenchée par le système win32k.sys appel NtSetWindowLongPtr() pour l'indice GWLP_ID sur une poignée de fenêtre avec GWL_STYLE réglé sur WS_CHILD. blocs sandbox de Chrome système win32k.sys appels en utilisant l'atténuation des lockdown Win32k sur Windows 10, qui empêche l'exploitation de cette vulnérabilité d'évacuation de bac à sable.
Quels sont quelques bons conseils de sécurité?
les chercheurs en sécurité Duo les organismes suivants, et nous sommes d'accord:
- Les plates-formes de navigateur modernes qui sont plus en sécurité ou aller pour les navigateurs qui sont plus fréquemment mis à jour automatiquement et;
- Ne jamais sous-estimer la puissance des mises à jour de sécurité et des correctifs d'urgence;
- Pensez à utiliser le chiffrement de l'appareil, mots de passe et ID d'empreintes digitales;
- Envisagez d'utiliser une solution d'authentification à deux facteurs pour protéger les systèmes et les données;
- Désactiver Java et empêcher Flash à partir de l'exécution automatique sur les périphériques d'entreprise;
- Cette pratique devrait aller pour les appareils appartenant à l'utilisateur grâce à des politiques d'accès au point final et les contrôles.