Wat onderzoekers geloven dat een variant van de beruchte HDDCryptor malware familie heeft het Muni metro van San Francisco hit. De hack geresulteerd in meer dan 2,000 systemen om gecompromitteerde worden en hun harde schijven te versleutelen. De ransomware gaf een kort bericht weer op het opstartscherm, linken naar de e-mail cryptom73@yandex.com. Dan, de cybercriminelen die erom vroegen 73 duizend dollar als losgeld te betalen om de toegang tot de systemen in de metro te herstellen. Dit is nog een ander geval van hoe IoT (internet van dingen) kan invloed hebben op ons dagelijks leven.
Wat onderzoekers geloven dat een variant van de beruchte HDDCryptor malware familie heeft het Muni metro van San Francisco hit. De hack geresulteerd in meer dan 2,000 systemen om gecompromitteerde worden en hun harde schijven te versleutelen. De ransomware gaf een kort bericht weer op het opstartscherm, linken naar de e-mail cryptom73@yandex.com. Dan, de cybercriminelen die erom vroegen 73 duizend dollar als losgeld te betalen om de toegang tot de systemen in de metro te herstellen. Dit is nog een ander geval van hoe IoT (internet van dingen) kan invloed hebben op ons dagelijks leven.

bedreiging Samenvatting
| Naam |
Cryptom |
| Type | Ransomware |
| Korte Omschrijving | De malware versleutelt de harde schijf van de gebruiker met een aangepaste password, het ontkennen van alle toegang toe. Het vraagt om 100 BTC losgeld betaling aan een wachtwoord voor codering ontvangen en verzenden. |
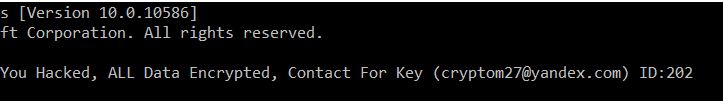
| Symptomen | Bij opstarten van het systeem geeft de volgende losgeldnota – “Je hebt gehackt, ALLE gegevens versleuteld, Contactpersoon voor sleutel (cryptom27@yandex.com) ID:” |
| Distributie Methode | Via een exploit kit, Dll-bestand aanval, kwaadaardige JavaScript of een drive-by download van de malware zich in een verduisterd wijze. Schadelijke uitvoerbare bestanden kunnen de eerste infectie zijn, maar er wordt gemeld dat ze zich verder verspreiden met behulp van wormverspreidende functies (automatisch).. |
| Detection Tool |
Zien of je systeem is getroffen door malware
Download
Malware Removal Tool
|
| Gebruikerservaring | Word lid van onze forum om Bespreek Cryptom Ransomware. |
| Data Recovery Tool | Windows Data Recovery door Stellar Phoenix kennisgeving! Dit product scant uw schijf sectoren om verloren bestanden te herstellen en het kan niet herstellen 100% van de gecodeerde bestanden, maar slechts weinigen van hen, afhankelijk van de situatie en of u uw schijf hebt geformatteerd. |

De Cryptom Ransomware viel verschillende systemen aan
Niet alleen systemen binnen het gemeentelijk transportbureau van de metro van San Francisco waren besmet. De ransomware wist ook veel andere gerelateerde systemen te beïnvloeden, zoals administratieve computers, systemen voor betaling, SQL-database computers, terminals en kiosken. De malware is hoogstwaarschijnlijk gecodeerd door iemand met ervaring omdat het een wormachtig vermogen had om zich over verschillende soorten apparaten te verspreiden, suggereert de verfijning erachter. Niet alleen dit, maar ook andere computers, zelfs Macs en andere pc's werden ook geraakt, stijgt het aantal geïnfecteerde apparaten grofweg 8,500.

Wat doet Cryptom Ransowmare
Het doel van Cryptom is om winst te genereren op kosten van de gebruiker. De aanval door het virus kan een wormachtig gedrag vertonen, wat betekent dat het zich verspreidt van een geïnfecteerd apparaat naar een geïnfecteerd apparaat, wat ernstige beveiligingsproblemen opriep in verschillende IoT-apparaten.
Na het infecteren van een bepaalde machine, de ransomware versleutelt niet alleen de bestanden op het gecompromitteerde apparaat. Plaats, het richt zich op het uitvoeren van verschillende taken die zijn gericht op het aanvallen van de MBR (Master Boot Record) die indien overschreven, stelt het in staat om de SSD of HDD op het gecompromitteerde apparaat rechtstreeks te versleutelen.
Nadat dit coderingsproces is voltooid, de ransomware genereert een unieke ontgrendelingssleutel via zijn versleutelingsmechanisme waarmee de versleutelde gegevens met succes kunnen worden ontcijferd. En Cryptom genereert eindelijk een opstartbericht waarin staat dat de schijf is gecodeerd:

De oorsprong van HDDCryptor
Vergelijkbaar met andere HDDCryptor-variant, Mamba Ransomware, Cryptom kan hetzelfde gedrag vertonen. Het enige idee voor deze specifieke bestandscoderingsmalware is het gebruik van codeervaardigheden om een geavanceerd ransomwarevirus te genereren door de broncode uit een open source-programma te halen, bekend als DiskCryptor die oorspronkelijk werd gebruikt ter bescherming van harde schijven.
Aangenomen wordt dat niet alleen de ransomware meerdere bestanden creëert op de belangrijkste logische schijf van de geïnfecteerde computer, maar het gebruikt die bestanden ook om beheerdersrechten te verkrijgen. Dit wordt hoogstwaarschijnlijk gebruikt voor Cryptom om een nieuwe gebruiker aan te maken op het gecompromitteerde apparaat en vervolgens waarschijnlijk de volgende cijfers te gebruiken om de harde schijf te versleutelen:
- AES-512-coderingsalgoritme
- XTS-coderingsmodus

Wat is de impact
Duizenden apparaten in het SF metro- en busnetwerk werden opnieuw opgestart met het losgeldbericht erop. Bij het contacteren van het e-mailadres antwoordden de cybercriminelen dat hun software automatisch infecteert en dat ze niet verwachtten dat er losgeld zou worden betaald. Maar hoe dan ook, ze eisten het krankzinnige losgeld van ongeveer 100 BTC voor de uitbetaling.
De impact van deze infectie is dat de SF-openbaarvervoersorganisatie werd gedwongen om de poorten voor toegang tot de metro te openen, zodat iedereen gratis kan rijden.

Cryptom Ransomware - Voorspellingen, Bescherming en Verwijdering
Gezien het feit dat steden, zoals het transportsysteem van San Francisco met elkaar verbonden is, hierdoor kon het Cryptom-virus zich zo snel verspreiden. Zelfs de cybercriminelen hebben toegegeven dat dit niet hun oorspronkelijke doelwit was. Echter, we zouden meer en meer ransomwareaanvallen op onderling verbonden apparaten kunnen zien die ons dagelijks leven beïnvloeden, zoals geldautomaten, beveiligingscamera's, parkeermeters en elk ander apparaat met een OS en een scherm die tot hetzelfde netwerk behoren.
In het geval dat u besmet door dit virus ransomware, we raden u aan uiterst voorzichtig te zijn in wat u doet. HDD-encryptors bestaan al geruime tijd en virussen, zoals "Petya" en "Mischa" hebben bewezen dat ze werken. Zodra je het losgeldbriefje ziet, de eerste stap die we u adviseren te nemen, is om uw harde schijf onmiddellijk van het apparaat los te koppelen. Om te leren hoe u dit kunt doen, u kunt onze instructies volgen (stap 1 stappen 3 in de "Decoderingsfase") in het onderstaande artikel:
Na het uitpakken van de harde schijf, het wordt aanbevolen om er op geen enkele manier mee te knoeien en te wachten tot malware-onderzoekers met een oplossing komen, onmiddellijk waarna we dit artikel zullen bijwerken met een weblink naar de oplossing zelf.
In de tussentijd is het beste wat u kunt doen om de beveiliging te vergroten, een systeem maken dat bestaat uit beschermingstools en een beveiligingsgericht gedrag. Dit is wat we u aanraden te doen:
1. Lees onze tips voor bescherming tegen ransomware.
2. Lezen ons onderzoek naar hoe u uw bestanden veilig kunt opslaan om ze in het algemeen te beschermen tegen ransomware-virussen.
3. Download een geavanceerde anti-malware gereedschap dat zal helpen om de algemene bescherming tegen malware en misbruik te vergroten:
Zien of je systeem is getroffen door malware
4. Download de Talos 'hulpmiddel die tot doel heeft de MBR te beschermen tegen ransomware en andere virussen.
- Stap 1
- Stap 2
- Stap 3
- Stap 4
- Stap 5
Stap 1: Scannen op Cryptom met SpyHunter Anti-Malware Tool



Ransomware Automatische verwijdering - Videogids
Stap 2: Uninstall Cryptom and related malware from Windows
Hier is een methode om in een paar eenvoudige stappen die moeten in staat zijn om de meeste programma's te verwijderen. Geen probleem als u Windows 10, 8, 7, Vista of XP, die stappen zal de klus te klaren. Slepen van het programma of de map naar de prullenbak kan een zeer slechte beslissing. Als je dat doet, stukjes van het programma worden achtergelaten, en dat kan leiden tot een instabiel werk van uw PC, fouten met het bestandstype verenigingen en andere onaangename activiteiten. De juiste manier om een programma te krijgen van je computer is deze ook te verwijderen. Om dat te doen:


 Volg de bovenstaande instructies en u zult met succes de meeste ongewenste en kwaadaardige programma's verwijderen.
Volg de bovenstaande instructies en u zult met succes de meeste ongewenste en kwaadaardige programma's verwijderen.
Stap 3: Verwijder eventuele registers, gemaakt door Cryptom op uw computer.
De doorgaans gericht registers van Windows-machines zijn de volgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
U kunt ze openen door het openen van het Windows-register-editor en met weglating van alle waarden, gemaakt door Cryptom daar. Dit kan gebeuren door de stappen onder:


 Tip: Om een virus gecreëerd waarde te vinden, U kunt met de rechtermuisknop op te klikken en klik op "Wijzigen" om te zien welk bestand het is ingesteld om te werken. Als dit het virus bestand locatie, Verwijder de waarde.
Tip: Om een virus gecreëerd waarde te vinden, U kunt met de rechtermuisknop op te klikken en klik op "Wijzigen" om te zien welk bestand het is ingesteld om te werken. Als dit het virus bestand locatie, Verwijder de waarde.
Voor het starten "Stap 4", alsjeblieft laars terug in de normale modus, in het geval dat u op dit moment in de Veilige modus.
Dit stelt u in staat om te installeren en gebruik SpyHunter 5 geslaagd.
Stap 4: Start uw pc op in de veilige modus om Cryptom te isoleren en te verwijderen





Stap 5: Try to Restore Files Encrypted by Cryptom.
Methode 1: Gebruik STOP Decrypter van Emsisoft.
Niet alle varianten van deze ransomware kan worden ontsleuteld gratis, maar we hebben de decryptor gebruikt door onderzoekers die vaak wordt bijgewerkt met de varianten die uiteindelijk gedecodeerd toegevoegd. U kunt proberen en decoderen van uw bestanden met behulp van de onderstaande instructies, maar als ze niet werken, dan helaas uw variant van de ransomware virus is niet decryptable.
Volg de onderstaande instructies om de Emsisoft decrypter gebruiken en decoderen van uw bestanden gratis. Je kan Download de Emsisoft decryptiehulpmiddel hier gekoppeld en volg de stappen hieronder:
1 Klik met de rechtermuisknop op de decrypter en klik op Als administrator uitvoeren zoals hieronder getoond:
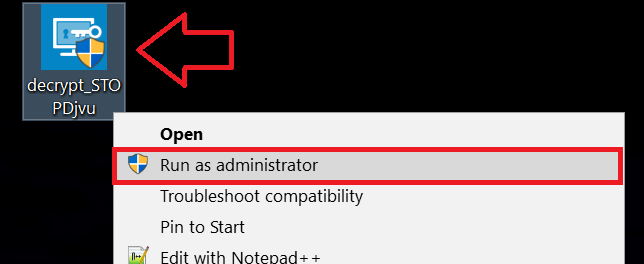
2. Ben het eens met de licentievoorwaarden:
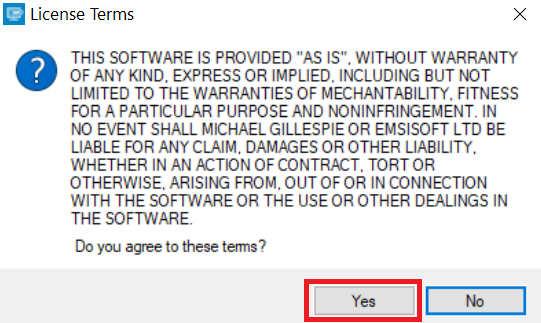
3. Klik op "Map toevoegen" en voeg vervolgens de mappen waarin u bestanden gedecodeerd zoals hieronder afgebeeld:
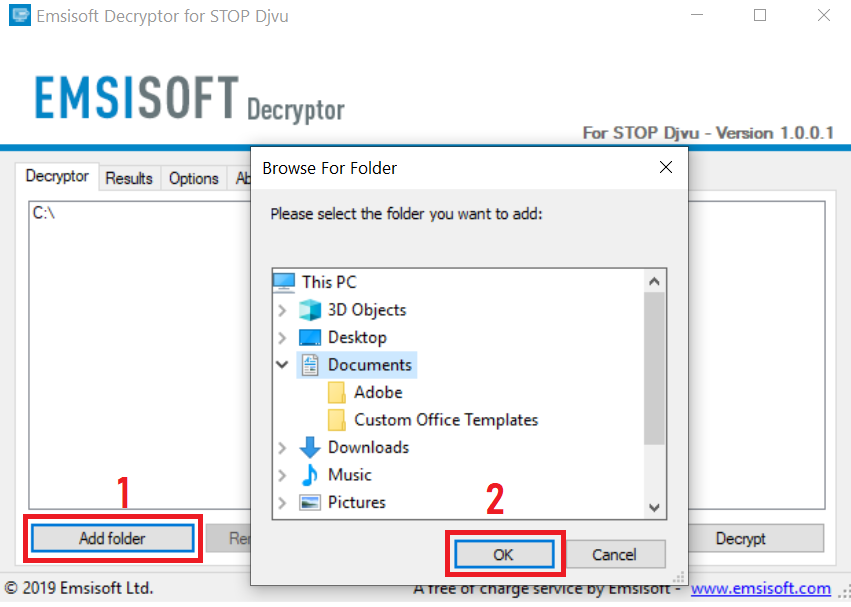
4. Klik op "decoderen" en wacht tot uw bestanden te decoderen.
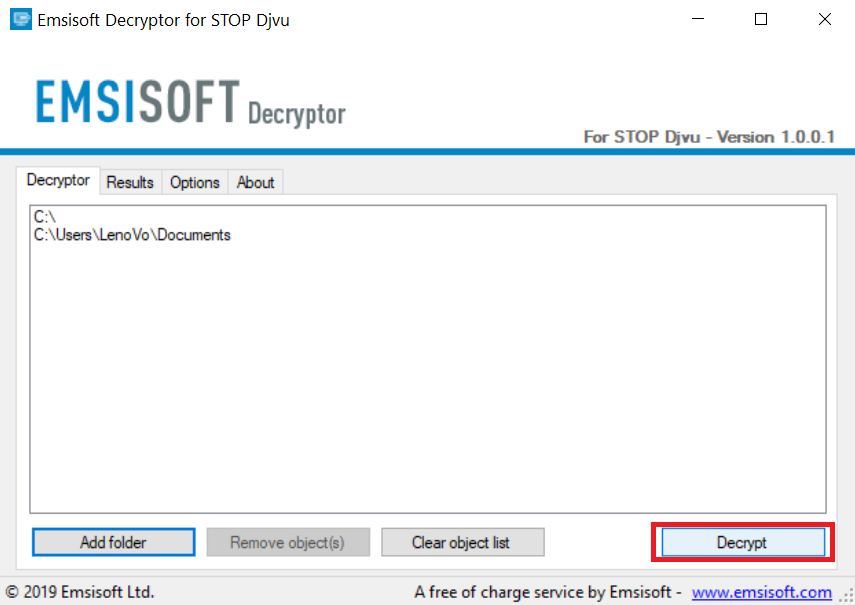
Aantekening: Krediet voor de decryptor gaat naar onderzoekers die de doorbraak hebben gemaakt met dit virus Emsisoft.
Methode 2: Gebruik software voor gegevensherstel
Ransomware infections and Cryptom aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. Dit is de reden waarom we een data recovery-methode die u kunnen helpen rond gaan direct decryptie en proberen om uw bestanden te herstellen hebben gesuggereerd. Houd er rekening mee dat deze methode niet kan worden 100% effectief, maar kan ook u helpen een veel of weinig in verschillende situaties.
Klik gewoon op de link en op de websitemenu's bovenaan, kiezen Data herstel - Data Recovery Wizard voor Windows of Mac (afhankelijk van uw besturingssysteem), en download en voer vervolgens de tool uit.
Cryptom-FAQ
What is Cryptom Ransomware?
Cryptom is a ransomware infectie - de schadelijke software die geruisloos uw computer binnenkomt en de toegang tot de computer zelf blokkeert of uw bestanden versleutelt.
Veel ransomware-virussen gebruiken geavanceerde versleutelingsalgoritmen om uw bestanden ontoegankelijk te maken. Het doel van ransomware-infecties is om te eisen dat u een losgeld betaalt om toegang te krijgen tot uw bestanden.
What Does Cryptom Ransomware Do?
Ransomware is in het algemeen een kwaadaardige software dat is ontworpen om de toegang tot uw computer of bestanden te blokkeren totdat er losgeld wordt betaald.
Ransomware-virussen kunnen dat ook uw systeem beschadigen, corrupte gegevens en verwijder bestanden, resulterend in het permanent verlies van belangrijke bestanden.
How Does Cryptom Infect?
Via several ways.Cryptom Ransomware infects computers by being sent via phishing-e-mails, met virusbijlage. Deze bijlage is meestal gemaskeerd als een belangrijk document, zoals een factuur, bankdocument of zelfs een vliegticket en het ziet er erg overtuigend uit voor gebruikers.
Another way you may become a victim of Cryptom is if you download een nep-installatieprogramma, crack of patch van een website met een lage reputatie of als u op een viruslink klikt. Veel gebruikers melden dat ze een ransomware-infectie hebben opgelopen door torrents te downloaden.
How to Open .Cryptom files?
U can't zonder decryptor. Op dit punt, de .Cryptom bestanden zijn versleutelde. U kunt ze pas openen nadat ze zijn gedecodeerd met een specifieke decoderingssleutel voor het specifieke algoritme.
Wat te doen als een decryptor niet werkt?
Raak niet in paniek, en maak een back-up van de bestanden. Als een decryptor uw niet heeft gedecodeerd .Cryptom bestanden succesvol, wanhoop dan niet, omdat dit virus nog steeds nieuw is.
Kan ik herstellen ".Cryptom" Bestanden?
Ja, soms kunnen bestanden worden hersteld. We hebben er verschillende voorgesteld bestandsherstelmethoden dat zou kunnen werken als je wilt herstellen .Cryptom bestanden.
Deze methoden zijn op geen enkele manier 100% gegarandeerd dat u uw bestanden terug kunt krijgen. Maar als je een back-up hebt, uw kansen op succes zijn veel groter.
How To Get Rid of Cryptom Virus?
De veiligste en meest efficiënte manier voor het verwijderen van deze ransomware-infectie is het gebruik van een professioneel antimalwareprogramma.
It will scan for and locate Cryptom ransomware and then remove it without causing any additional harm to your important .Cryptom files.
Kan ik ransomware melden aan de autoriteiten??
In het geval dat uw computer is geïnfecteerd met een ransomware-infectie, u kunt dit melden bij de lokale politie. Het kan autoriteiten over de hele wereld helpen de daders van het virus dat uw computer heeft geïnfecteerd, op te sporen en te achterhalen.
Onder, we hebben een lijst met overheidswebsites opgesteld, waar u aangifte kunt doen als u slachtoffer bent van een cybercrime:
Cyberbeveiligingsautoriteiten, verantwoordelijk voor het afhandelen van ransomware-aanvalsrapporten in verschillende regio's over de hele wereld:
Duitsland - Officieel portaal van de Duitse politie
Verenigde Staten - IC3 Internet Crime Complaint Center
Verenigd Koninkrijk - Actie Fraude Politie
Frankrijk - Ministerie van Binnenlandse Zaken
Italië - Staatspolitie
Spanje - Nationale politie
Nederland - Politie
Polen - Politie
Portugal - Gerechtelijke politie
Griekenland - Cyber Crime Unit (Griekse politie)
India - Mumbai politie - Cel voor onderzoek naar cybercriminaliteit
Australië - Australisch High Tech Crime Centre
Op rapporten kan in verschillende tijdsbestekken worden gereageerd, afhankelijk van uw lokale autoriteiten.
Kunt u voorkomen dat ransomware uw bestanden versleutelt??
Ja, u kunt ransomware voorkomen. De beste manier om dit te doen, is ervoor te zorgen dat uw computersysteem is bijgewerkt met de nieuwste beveiligingspatches, gebruik een gerenommeerd anti-malwareprogramma en firewall, maak regelmatig een back-up van uw belangrijke bestanden, en klik niet op kwaadaardige links of het downloaden van onbekende bestanden.
Can Cryptom Ransomware Steal Your Data?
Ja, in de meeste gevallen ransomware zal uw gegevens stelen. It is a form of malware that steals data from a user's computer, versleutelt het, en eist vervolgens losgeld om het te decoderen.
In veel gevallen, de malware-auteurs of aanvallers zullen dreigen de gegevens of te verwijderen publiceer het online tenzij het losgeld wordt betaald.
Kan ransomware WiFi infecteren??
Ja, ransomware kan WiFi-netwerken infecteren, aangezien kwaadwillende actoren het kunnen gebruiken om controle over het netwerk te krijgen, vertrouwelijke gegevens stelen, en gebruikers buitensluiten. Als een ransomware-aanval succesvol is, dit kan leiden tot verlies van service en/of gegevens, en in sommige gevallen, financiële verliezen.
Moet ik ransomware betalen?
Geen, je moet geen afpersers van ransomware betalen. Betalen moedigt criminelen alleen maar aan en geeft geen garantie dat de bestanden of gegevens worden hersteld. De betere aanpak is om een veilige back-up van belangrijke gegevens te hebben en in de eerste plaats waakzaam te zijn over de beveiliging.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, de hackers hebben mogelijk nog steeds toegang tot uw computer, gegevens, of bestanden en kunnen blijven dreigen deze openbaar te maken of te verwijderen, of ze zelfs gebruiken om cybercriminaliteit te plegen. In sommige gevallen, ze kunnen zelfs doorgaan met het eisen van extra losgeld.
Kan een ransomware-aanval worden gedetecteerd??
Ja, ransomware kan worden gedetecteerd. Antimalwaresoftware en andere geavanceerde beveiligingstools kan ransomware detecteren en de gebruiker waarschuwen wanneer het op een machine aanwezig is.
Het is belangrijk om op de hoogte te blijven van de nieuwste beveiligingsmaatregelen en om beveiligingssoftware up-to-date te houden om ervoor te zorgen dat ransomware kan worden gedetecteerd en voorkomen.
Worden ransomware-criminelen gepakt?
Ja, ransomware-criminelen worden gepakt. Wetshandhavingsinstanties, zoals de FBI, Interpol en anderen zijn succesvol geweest in het opsporen en vervolgen van ransomware-criminelen in de VS en andere landen. Naarmate ransomware-bedreigingen blijven toenemen, dat geldt ook voor de handhavingsactiviteiten.
Over het Cryptom-onderzoek
De inhoud die we publiceren op SensorsTechForum.com, deze Cryptom how-to verwijderingsgids inbegrepen, is het resultaat van uitgebreid onderzoek, hard werken en de toewijding van ons team om u te helpen de specifieke malware te verwijderen en uw versleutelde bestanden te herstellen.
Hoe hebben we het onderzoek naar deze ransomware uitgevoerd??
Ons onderzoek is gebaseerd op een onafhankelijk onderzoek. We hebben contact met onafhankelijke beveiligingsonderzoekers, en als zodanig, we ontvangen dagelijkse updates over de nieuwste malware- en ransomware-definities.
Bovendien, the research behind the Cryptom ransomware threat is backed with VirusTotal en NoMoreRansom project.
Om de ransomware-dreiging beter te begrijpen, raadpleeg de volgende artikelen die deskundige details bieden:.
Als een site die sindsdien is toegewijd aan het verstrekken van gratis verwijderingsinstructies voor ransomware en malware 2014, De aanbeveling van SensorsTechForum is let alleen op betrouwbare bronnen.
Hoe betrouwbare bronnen te herkennen:
- Controleer altijd "Over ons" webpagina.
- Profiel van de maker van de inhoud.
- Zorg ervoor dat er echte mensen achter de site staan en geen valse namen en profielen.
- Controleer Facebook, LinkedIn en Twitter persoonlijke profielen.