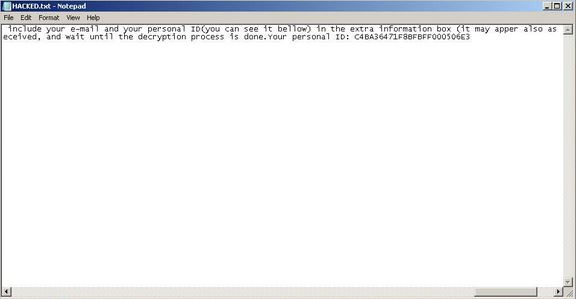
Den .b00m virus er en ransomware, der i øjeblikket sat mod mål slutbrugere på globalt plan. Der er ingen oplysninger om hacking gruppen bag det. Det menes at være en ny iteration af den berømte ransomware familie. Dette er en af grundene til, at vi mener, at hackere er erfarne.
Når .b00m virus er begyndt, vil udføre sit indbyggede sekvens af farlige kommandoer. Afhængig af lokale forhold eller særlige hacker instruktioner forskellige aktioner vil finde sted. Filen kryptering vil begynde efter dem - kryptere komponent vil bruge en indbygget liste over mål filtype extensions. I sidste ende offeret filer vil blive omdøbt med .b00m udvidelse.

Trussel Summary
| Navn | b00m Virus |
| Type | Ransomware, Cryptovirus |
| Kort beskrivelse | Den ransomware krypterer filer på computeren maskine og kræver en løsesum, der skal betales til angiveligt gendanne dem. |
| Symptomer | Den ransomware vil afpresse ofrene til at betale dem en dekryptering gebyr. Følsomme brugerdata kan være krypteret med ransomware kode. |
| Distributionsmetode | Spam e-mails, Vedhæftede filer |
| Værktøj Detection |
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
Brugererfaring | Tilmeld dig vores forum at diskutere b00m Virus. |
| Data Recovery Tool | Windows Data Recovery af Stellar Phoenix Varsel! Dette produkt scanner dine drev sektorer til at gendanne mistede filer, og det kan ikke komme sig 100% af de krypterede filer, men kun få af dem, afhængigt af situationen og uanset om du har omformateret drevet. |

.b00m Virus - Distribution og Impact
Den .b00m virus er en ny variant af den CryptoJoker familie af trusler, som sandsynligvis bliver sendt af en erfaren hacking kollektiv. Det er blevet rapporteret i en global aktiv kampagne, der er målrettet primært hjemmebrugere. I øjeblikket de fleste af de infektioner bekræftes at komme fra inficerede software installatører - de kriminelle vil tage de originale setup filer af populære programmer og indsæt i dem virus installation kode. I dette særlige tilfælde infektioner er forårsaget af lanceringen af en eksekverbar fil kaldet installer.exe som ikke viser for nøjagtigt hvilke app de falske setup filer er lavet. De kan være af programmer såsom følgende: kreativitet og produktivitet suiter, kontorprogrammer, systemværktøjer og endda hoax sikkerhedsløsninger.
Der er flere store metoder, hvorigennem disse filer kan spredes:
- e-mails - De kriminelle kan konstruere e-mails, der er designet til at efterligne kendte tjenester og virksomheder og manipulere brugerne i at interagere med indholdet. De er som regel stjålet eller forfalsket.
- Phishing steder - En lignende fremgangsmåde er oprettelsen af talrige hacker-kontrollerede websteder, der synes at være dele af kendte virksomheder. De er hostet på lignende klingende domænenavne eller adgang til via URL afkortning tjenester. For eksempel i dette tilfælde de kriminelle kan gøre websteder, der vises som download-portaler eller officielle produkt download sider.
- Fildeling netværk - De installatører kan deles på peer-to-peer-netværk som BitTorrent, som er meget populær for at sprede både lovlige og pirat-data.
- Malware Browserudvidelser - Disse kaldes også “flykaprere” og er ofte uploades til depoter af browsere.
Da det kopier ned den typiske ransomware funktioner .b00m virus vil sandsynligvis udføre flere ondsindede komponenter, inden kryptering af brugerdata. Afhængigt af de lokale forhold eller hackere instruktioner dette kan variere på tværs af forskellige kategorier af systemets manipulation. En fælles
Sådanne infektioner begynder normalt med udvinding af data fra de kompromitterede værter. Dette kan indeholde personlige oplysninger, der kan afsløre identiteten af ofrene og bruges til relaterede forbrydelser. Hvis nogen maskine data kapret derefter en algoritme kan automatisk generere en unik profil ID for hver kompromitteret maskine.
Disse oplysninger kan derefter overvåges og bruges til en sikkerhed bypass der vil kigge efter eventuelle installerede programmer eller software, der kan detektere og blokere .b00m virus. Når dette er færdig med at køre forskellige systemændringer kan opstå - opsætningen af .b00m virus som en vedvarende trussel for eksempel. Dette er den fase af infektion, hvor dens tilknyttede hovedmotor starter hver gang computeren startes, og også blokere adgang til bestemte opstartsmuligheder.
Når dybdegående forandringer er bekymrede i de fleste tilfælde ransomware også vælge at påvirke Registry Windows - nye poster kan foretages eller eksisterende kan redigeres. Konsekvenser kan omfatte tab af data, problemer med ydeevnen og fejl.
Når alle komponenter er færdig med at køre den faktiske fil kryptering starter. Dette gøres ved at lancere den stærke cipher mod brugerdata fra de populære filtyper: dokumenter, arkiv, sikkerhedskopier, multimediefiler og etc. De vil modtage .b00m udvidelse

.b00m Virus - hvad betyder det gøre?
.b00m Virus kunne sprede sin smitte på forskellige måder. En nyttelast dropper, som initierer skadeligt script for denne ransomware bliver spredt rundt på internettet. .b00m Virus kan også distribuere sin nyttelast fil på sociale medier og fildelingstjenester. Freeware som findes på internettet kan præsenteres som nyttige også skjule skadeligt script til cryptovirus. Læs tips til forebyggelse ransomware fra vores forum.
.b00m Virus er en cryptovirus der krypterer dine filer og viser et vindue med instruktioner på computerskærmen. De extortionists vil have dig til at betale en løsesum for den påståede restaurering af dine filer. Hovedmotoren kunne gøre poster i Windows-registreringsdatabasen for at opnå vedholdenhed, og forstyrre processer i Windows.
Den .b00m Virus er en krypto-virus er programmeret til at kryptere brugerdata. Så snart alle moduler er færdig med at køre i deres foreskrevne rækkefølge lockscreen vil starte et program ramme, som vil forhindre brugerne i at interagere med deres computere. Det vil vise ransomware note til ofrene.
Du burde IKKE under ingen omstændigheder betale løsesum sum. Dine filer kan ikke få tilbagebetalt, og ingen kunne give dig en garanti for, at.
Den .b00m Virus cryptovirus kunne indstilles til at slette alle de Shadow Volume Kopier fra Windows operativsystemet ved hjælp af følgende kommando:
→vssadmin.exe slette skygger / alle / Stille
Hvis din computer enhed blev inficeret med denne ransomware og dine filer er låst, læs videre igennem for at finde ud af, hvordan du potentielt kunne gendanne dine filer tilbage til normal.

Fjern .b00m Virus
Hvis din computer-system fik inficeret med .b00m filer ransomware virus, du skal have lidt erfaring med at fjerne malware. Du bør slippe af med denne ransomware så hurtigt som muligt, før det kan få mulighed for at sprede sig yderligere og inficere andre computere. Du bør fjerne ransomware og følg trin-for-trin instruktioner guide nedenfor.
- Trin 1
- Trin 2
- Trin 3
- Trin 4
- Trin 5
Trin 1: Scan efter b00m Virus med SpyHunter Anti-Malware Tool



Automatisk fjernelse af ransomware - Videoguide
Trin 2: Uninstall b00m Virus and related malware from Windows
Her er en metode i nogle få nemme trin, der bør være i stand til at afinstallere de fleste programmer. Uanset om du bruger Windows 10, 8, 7, Vista eller XP, disse skridt vil få arbejdet gjort. At trække det program eller dets mappe til papirkurven kan være en meget dårlig beslutning. Hvis du gør det, stumper og stykker af programmet er efterladt, og det kan føre til ustabile arbejde på din PC, fejl med filtypen foreninger og andre ubehagelige aktiviteter. Den rigtige måde at få et program fra din computer er at afinstallere det. For at gøre dette:


 Følg instruktionerne ovenfor, og du vil med succes slette de fleste uønskede og ondsindede programmer.
Følg instruktionerne ovenfor, og du vil med succes slette de fleste uønskede og ondsindede programmer.
Trin 3: Rens eventuelle registre, oprettet af b00m Virus på din computer.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, skabt af b00m Virus der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Inden start "Trin 4", be om boot tilbage til normal tilstand, hvis du er i øjeblikket i fejlsikret tilstand.
Dette vil gøre det muligt for dig at installere og brug SpyHunter 5 succesfuld.
Trin 4: Start din pc i sikker tilstand for at isolere og fjerne b00m Virus





Trin 5: Prøv at gendanne filer, der er krypteret af b00m Virus.
Metode 1: Brug STOP Decrypter af Emsisoft.
Ikke alle varianter af denne ransomware kan dekrypteres gratis, men vi har tilføjet den decryptor bruges af forskere, der ofte opdateret med de varianter, der i sidste ende blive dekrypteret. Du kan prøve og dekryptere dine filer ved hjælp nedenstående vejledning, men hvis de ikke arbejde, så desværre din variant af ransomware virus er ikke dekrypteres.
Følg instruktionerne nedenfor for at bruge Emsisoft Decrypter og dekryptere dine filer gratis. Du kan downloade Emsisoft dekryptering værktøj knyttet her og derefter følge trinene nedenfor tilvejebragte:
1 Højreklik på Decrypter og klik på Kør som administrator som vist nedenfor:
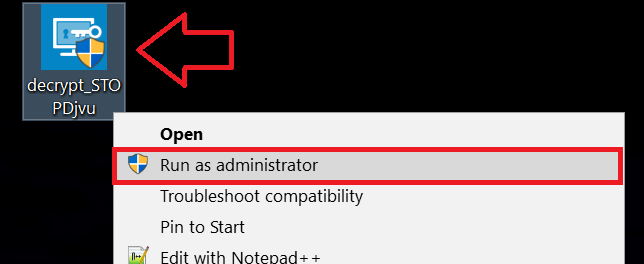
2. Enig med licensbetingelserne:
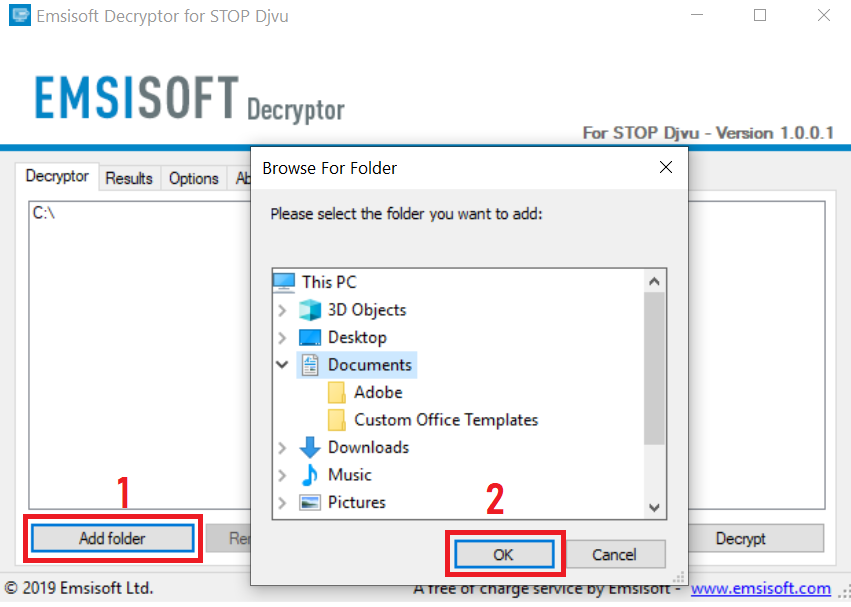
3. Klik på "Tilføj mappe" og derefter tilføje de mapper, hvor du ønsker filerne dekrypteret som vist nedenunder:
4. Klik på "Dekryptér" og vente på dine filer, der skal afkodes.
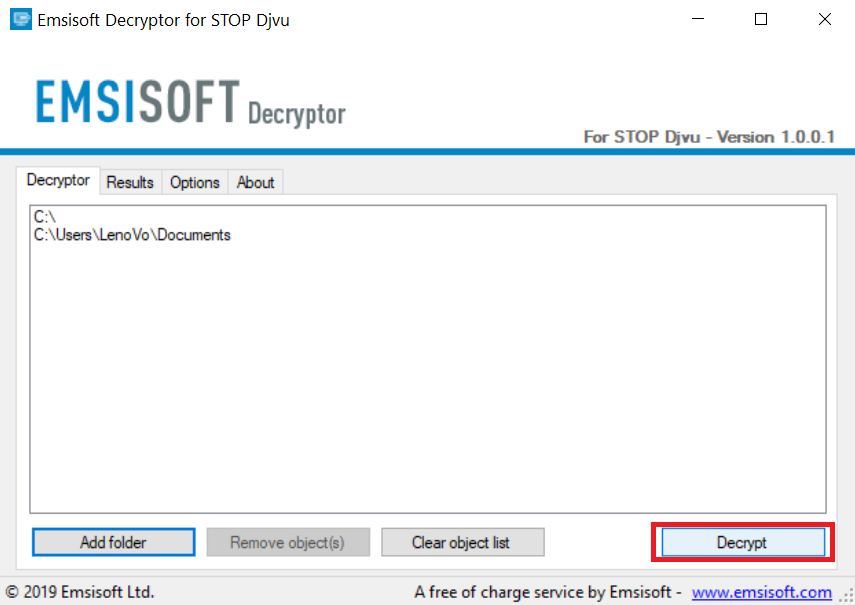
Note: Kredit til decryptor går til Emsisoft forskere, der har gjort det gennembrud med denne virus.
Metode 2: Brug datagendannelsessoftware
Ransomware-infektioner og b00m Virus sigter mod at kryptere dine filer ved hjælp af en krypteringsalgoritme, der kan være meget vanskelig at dekryptere. Det er derfor, vi har foreslået en data recovery metode, der kan hjælpe dig med at gå rundt direkte dekryptering og forsøge at gendanne dine filer. Husk, at denne metode ikke kan være 100% effektiv, men kan også hjælpe dig lidt eller meget i forskellige situationer.
Du skal blot klikke på linket og på hjemmesidens menuer øverst, vælge data Recovery - Guiden til gendannelse af data til Windows eller Mac (afhængigt af dit operativsystem), og download og kør derefter værktøjet.
b00m Virus-FAQ
What is b00m Virus Ransomware?
b00m Virus er en ransomware infektion - den ondsindede software, der lydløst kommer ind på din computer og blokerer enten adgang til selve computeren eller krypterer dine filer.
Mange ransomware-vira bruger sofistikerede krypteringsalgoritmer til at gøre dine filer utilgængelige. Målet med ransomware-infektioner er at kræve, at du betaler en løsepenge-betaling for at få adgang til dine filer tilbage.
What Does b00m Virus Ransomware Do?
Ransomware er generelt en ondsindet software der er designet for at blokere adgangen til din computer eller filer indtil en løsesum er betalt.
Ransomware-virus kan også beskadige dit system, korrupte data og slette filer, resulterer i permanent tab af vigtige filer.
How Does b00m Virus Infect?
Via flere måder.b00m inficerer Virus Ransomware computere ved at blive sendt via phishing-e-mails, indeholder virus vedhæftning. Denne vedhæftning maskeres normalt som et vigtigt dokument, lignende En faktura, bankdokument eller endda en flybillet og det ser meget overbevisende ud for brugerne.
Another way you may become a victim of b00m Virus is if you download et falsk installationsprogram, crack eller patch fra et websted med lavt omdømme eller hvis du klikker på et viruslink. Mange brugere rapporterer at få en ransomware-infektion ved at downloade torrents.
How to Open .b00m Virus files?
Du can't uden en dekryptering. På dette tidspunkt, den .b00m Virus filer er krypteret. Du kan kun åbne dem, når de er dekrypteret ved hjælp af en specifik dekrypteringsnøgle til den bestemte algoritme.
Hvad skal man gøre, hvis en dekryptering ikke virker?
Gå ikke i panik, og sikkerhedskopiere filerne. Hvis en dekrypter ikke dekrypterede din .b00m Virus filer med succes, så fortvivl ikke, fordi denne virus stadig er ny.
Kan jeg gendanne ".b00m Virus" Filer?
Ja, undertiden kan filer gendannes. Vi har foreslået flere filgendannelsesmetoder det kunne fungere, hvis du vil gendanne .b00m Virus filer.
Disse metoder er på ingen måde 100% garanteret, at du vil være i stand til at få dine filer tilbage. Men hvis du har en sikkerhedskopi, dine chancer for succes er meget større.
How To Get Rid of b00m Virus Virus?
Den sikreste måde og den mest effektive til fjernelse af denne ransomware-infektion er brugen a professionelt anti-malware program.
Det vil scanne efter og lokalisere b00m Virus ransomware og derefter fjerne det uden at forårsage yderligere skade på dine vigtige .b00m Virus-filer.
Kan jeg rapportere Ransomware til myndigheder?
Hvis din computer blev inficeret med en ransomware-infektion, du kan rapportere det til de lokale politiafdelinger. Det kan hjælpe myndigheder overalt i verden med at spore og bestemme gerningsmændene bag den virus, der har inficeret din computer.
Nedenfor, Vi har udarbejdet en liste med offentlige websteder, hvor du kan indgive en rapport, hvis du er offer for en cyberkriminalitet:
Cybersikkerhedsmyndigheder, ansvarlig for håndtering af ransomware-angrebsrapporter i forskellige regioner over hele verden:
Tyskland - Officiel portal for det tyske politi
Forenede Stater - IC3 Internet Crime Complaint Center
Storbritannien - Action svig politi
Frankrig - Indenrigsministeriet
Italien - Statens politi
Spanien - Nationalt politi
Holland - Retshåndhævelse
Polen - Politi
Portugal - Justitspolitiet
Grækenland - Enhed om cyberkriminalitet (Hellenske politi)
Indien - Mumbai-politiet - CyberCrime-undersøgelsescelle
Australien - Australsk High Tech Crime Center
Rapporter kan besvares inden for forskellige tidsrammer, afhængigt af dine lokale myndigheder.
Kan du stoppe Ransomware i at kryptere dine filer?
Ja, du kan forhindre ransomware. Den bedste måde at gøre dette på er at sikre, at dit computersystem er opdateret med de nyeste sikkerhedsrettelser, bruge et velrenommeret anti-malware program og firewall, sikkerhedskopiere dine vigtige filer ofte, og undgå at klikke videre ondsindede links eller downloade ukendte filer.
Can b00m Virus Ransomware Steal Your Data?
Ja, i de fleste tilfælde ransomware vil stjæle dine oplysninger. It is a form of malware that steals data from a user's computer, krypterer det, og kræver derefter en løsesum for at dekryptere den.
I mange tilfælde, den malware forfattere eller angribere vil true med at slette data eller udgive det online medmindre løsesummen er betalt.
Kan Ransomware inficere WiFi?
Ja, ransomware kan inficere WiFi-netværk, da ondsindede aktører kan bruge det til at få kontrol over netværket, stjæle fortrolige data, og låse brugere ud. Hvis et ransomware-angreb lykkes, det kan føre til tab af service og/eller data, og i nogle tilfælde, økonomiske tab.
Skal jeg betale Ransomware?
Nej, du bør ikke betale ransomware-afpressere. At betale dem opmuntrer kun kriminelle og garanterer ikke, at filerne eller dataene bliver gendannet. Den bedre tilgang er at have en sikker backup af vigtige data og være opmærksom på sikkerheden i første omgang.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, hackerne kan stadig have adgang til din computer, data, eller filer og kan fortsætte med at true med at afsløre eller slette dem, eller endda bruge dem til at begå cyberkriminalitet. I nogle tilfælde, de kan endda fortsætte med at kræve yderligere løsepengebetalinger.
Kan et Ransomware-angreb opdages?
Ja, ransomware kan detekteres. Anti-malware-software og andre avancerede sikkerhedsværktøjer kan opdage ransomware og advare brugeren når det er til stede på en maskine.
Det er vigtigt at holde sig ajour med de seneste sikkerhedsforanstaltninger og at holde sikkerhedssoftware opdateret for at sikre, at ransomware kan opdages og forhindres.
Bliver ransomware-kriminelle fanget?
Ja, ransomware-kriminelle bliver fanget. Retshåndhævende myndigheder, såsom FBI, Interpol og andre har haft succes med at opspore og retsforfølge ransomware-kriminelle i USA og andre lande. I takt med at ransomware-trusler fortsætter med at stige, det samme gør håndhævelsesaktiviteten.
About the b00m Virus Research
Indholdet udgiver vi på SensorsTechForum.com, this b00m Virus how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed til at hjælpe dig med at fjerne den specifikke malware og gendanne dine krypterede filer.
Hvordan udførte vi undersøgelsen af denne ransomware?
Vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, og som sådan, vi modtager daglige opdateringer om de seneste malware- og ransomware-definitioner.
Endvidere, the research behind the b00m Virus ransomware threat is backed with VirusTotal og NoMoreRansom projekt.
For bedre at forstå ransomware-truslen, Se venligst følgende artikler, som giver kyndige detaljer.
Som et sted, der siden har været dedikeret til at levere gratis fjernelsesinstruktioner for ransomware og malware 2014, SensorsTechForum's anbefaling er at Vær kun opmærksom på pålidelige kilder.
Sådan genkendes pålidelige kilder:
- Kontroller altid "Om os" hjemmeside.
- Profil af indholdsskaberen.
- Sørg for, at rigtige mennesker er bag webstedet og ikke falske navne og profiler.
- Bekræft Facebook, LinkedIn og Twitter personlige profiler.