Hvad er MacOS Security Center Virus?
Hvis din browser oplever omdirigeringer til svindelsiden MacOS Security Center, tage øjeblikkelig handling. Ryd din browsers cache og cookies, deaktiver mistænkelige udvidelser, og kør en malware-scanning for at fjerne potentielle trusler.
MacOS Security Center er et eksempel på en fidus rettet mod Mac-brugere, der også kan sprede et trojaniseret program. Det ser ud som et rigtigt program uden at give nogen tegn på, at det er en fidusapplikation. Fidustilgangen kan kategoriseres som en scareware besked og en falsk pop-up virusadvarsel.
I en nøddeskal, MacOS Security Center er et fupnummer, der udsætter din Mac for adskillige onlinetrusler. Fidusen vises muligvis i Safari-browseren, når du har klikket på mistænkelige links. På grund af de dermed forbundne risici, MacOS Security Center og dets tilsvarende apps bør fjernes.
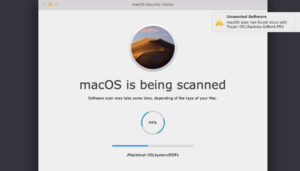
MacOS Security Center detaljer
| Navn | MacOS Sikkerhedscenter |
| Type | PUP/Rogue Application/Tech-Support Scam |
| Fjernelsestid | Mindre end 15 minutter (Komplet system scanning) |
| Removal Tool |
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
Hvordan blev jeg inficeret af MacOS Security Center?
Da MacOS Security Center er en pop-up browser fidus, dens distributionsmetode er højst sandsynligt risikabelt browsing. Surfing på nettet skjuler sine potentielle risici, især hvis du besøger mistænkelige websteder, og din computer mangler beskyttelse. Websites kan kapret med reklamer og omdirigere links, og du kan blive omdirigeret til svindelsider, som kan udløse advarsler falske virus.
Freeware programmer, betragtes som PUP (potentielt uønskede programmer) kunne også distribuere tech-support-svindel, og kan medføre, at scareware besked vises i dine browsere. Gratis download hjemmesider normalt har tonsvis af tredjeparts installationer og bundtede installatører. Denne praksis udføres med monetisering i tankerne.
MacOS Security Center er blot et eksempel på mange falske pop-ups udløst af teknisk support-svindel. Bemærk, at forskellige telefonnumre kan fremmes, og selve meddelelsen kan variere. Selvfølgelig, formålet med hver sådan besked forbliver den samme. For at narre dig til at udføre en handling, som direkte bringer din computer i fare. Disse svindelnumre påvirker brugernes forskellige operativsystemer, herunder Windows, MacOS, iPhone og Android.
MacOS Security Center – Hvad gør det?
Svindlere bruger falske virusdetektioner og -advarsler for at skabe en følelse af uopsættelighed og få dig til at ringe til et bestemt telefonnummer eller udføre en anden handling, der afslører din online sikkerhed. Der er ingen at fortælle, hvad der kunne ske næste, især hvis du tillader fjernsupport eller afsløre følsomme oplysninger, såsom dine betalingsdata.
For at gøre deres svindel mere troværdigt, svindlere bruger logoer fra troværdige virksomheder som Microsoft, Google, og Apple, eller anti-virus software virksomheder som McAfee og Avira. Men, se logoet for et populært selskab bør ikke narre dig på nogen måde, da disse virksomheder ikke implementere sådanne metoder til at advare deres brugere af spørgsmål. Dette er, hvad teknisk support svindlere gøre i deres desperate forsøg på at narre brugere.
Pas på svindlere med teknisk support, der kan ringe til dig. De vil foregive at være fra Microsoft eller Apple, men det hele er løgn. Disse svindlere er professionelle og arbejder endda i callcentre. Det er en lukrativ forretning, så vær smart og fald ikke for det.
Er MacOS Security Center et virus?
Nej, dette er ikke en virus, men snarere en fidus, der ønsker at få dig til at tro, at dit system har en virus. I dette særlige tilfælde, svindlerne forsøger at narre dig til at tro det en bagdørstrojaner har infiltreret dit system. Må ikke bekymre dig, da dette kun er en scareware tilgang til at presse dig til at udføre en bestemt handling, som at downloade et useriøst softwareprogram. Afstå fra at interagere med noget af det indhold, som denne fidus udløser.
Trin til fjernelse af MacOS Security Center
Når de er ramt af svindel, den hurtigste måde at fjerne årsagen på er at scanne dit system med anti-malware. Denne proaktive foranstaltning fjerner ikke kun potentielle trusler, men sikrer også en sikrere og mere sikker browsingoplevelse.
Trin til at forberede før fjernelse:
Inden du begynder at følge nedenstående trin, tilrådes, at du først skal gøre følgende forberedelser:
- Backup dine filer i tilfælde det værste sker.
- Sørg for at have en enhed med disse instruktioner om standy.
- Arm dig selv med tålmodighed.
- 1. Scan efter Mac Malware
- 2. Afinstaller Risky Apps
- 3. Rens dine browsere
Trin 1: Scan efter og fjern MacOS Security Center-filer fra din Mac
Når du står over for problemer på din Mac som følge af uønskede scripts og programmer såsom MacOS Security Center, den anbefalede måde at eliminere truslen er ved hjælp af en anti-malware program. SpyHunter til Mac tilbyder avancerede sikkerhedsfunktioner sammen med andre moduler, der forbedrer din Mac's sikkerhed og beskytter den i fremtiden.
Hurtig og nem Mac Malware Video Removal Guide
Bonustrin: Sådan får du din Mac til at køre hurtigere?
Mac-maskiner opretholder nok det hurtigste operativsystem der findes. Stadig, Mac'er bliver nogle gange langsomme og træge. Videoguiden nedenfor undersøger alle de mulige problemer, der kan føre til, at din Mac er langsommere end normalt, samt alle de trin, der kan hjælpe dig med at fremskynde din Mac.
Trin 2: Afinstaller MacOS Security Center og fjern relaterede filer og objekter
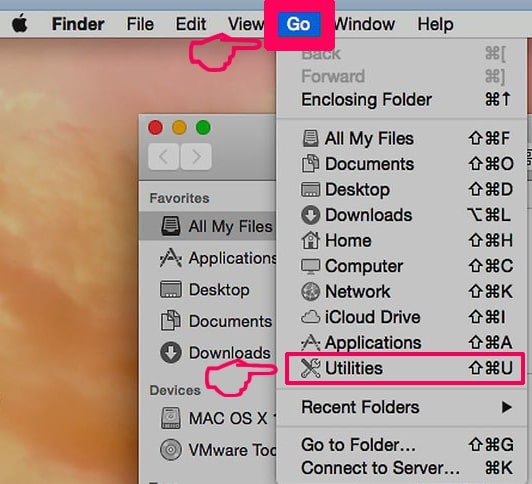
1. ramte ⇧ + ⌘ + U nøgler til at åbne Utilities. En anden måde er at klikke på "Go" og derefter klikke på "Utilities", ligesom på billedet nedenfor viser:
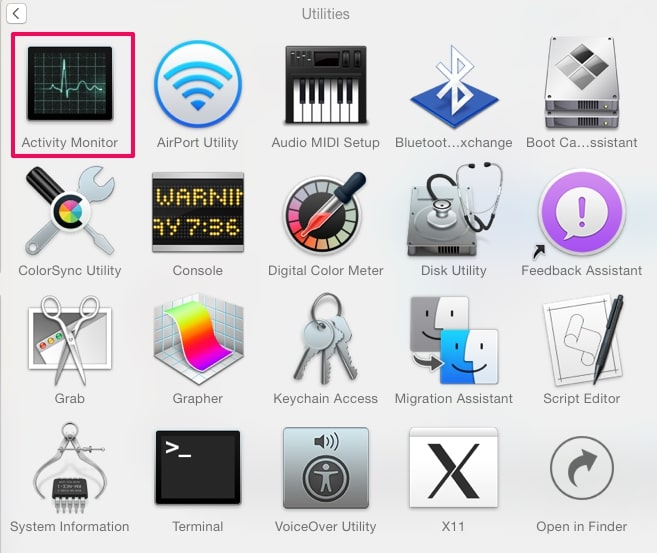
2. Find Activity Monitor og dobbeltklik på den:
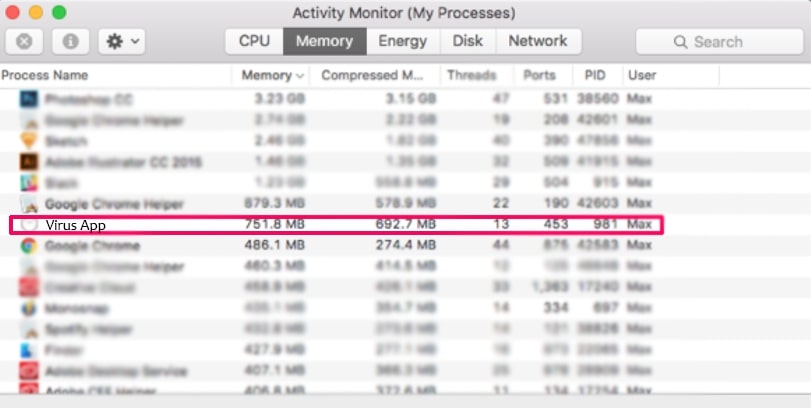
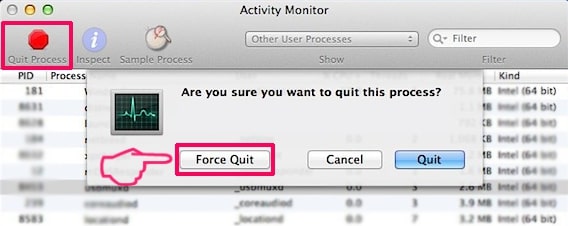
3. I Aktivitetsovervågning kigge efter eventuelle mistænkelige processer, tilhører eller relateret til MacOS Security Center:
4. Klik på "Gå" knappen igen, men denne gang skal du vælge Programmer. En anden måde er med knapperne ⇧+⌘+A.
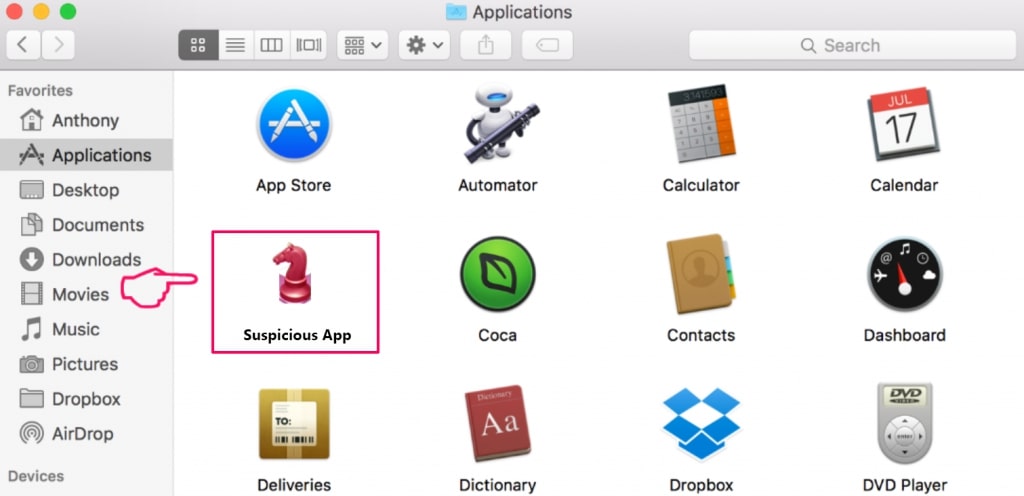
5. I menuen Applikationer, ser for enhver mistænkelig app eller en app med et navn, ligner eller er identisk med MacOS Security Center. Hvis du finder det, højreklik på appen og vælg "Flyt til papirkurven".
6. Vælg Konti, hvorefter du klikke på Log ind-emner præference. Din Mac vil så vise dig en liste over emner, starte automatisk når du logger ind. Kig efter eventuelle mistænkelige apps identiske eller lignende til MacOS Security Center. Marker den app, du vil stoppe med at køre automatisk, og vælg derefter på Minus ("-") ikonet for at skjule det.
7. Fjern eventuelle resterende filer, der kan være relateret til denne trussel, manuelt ved at følge undertrinene nedenfor:
- Gå til Finder.
- I søgefeltet skriv navnet på den app, du vil fjerne.
- Over søgefeltet ændre to rullemenuerne til "System Files" og "Er Inkluderet" så du kan se alle de filer, der er forbundet med det program, du vil fjerne. Husk på, at nogle af filerne kan ikke være relateret til den app, så være meget forsigtig, hvilke filer du sletter.
- Hvis alle filerne er relateret, hold ⌘ + A knapperne til at vælge dem og derefter køre dem til "Affald".
I tilfælde af at du ikke fjerne MacOS Security Center via Trin 1 over:
I tilfælde af at du ikke finde virus filer og objekter i dine programmer eller andre steder, vi har vist ovenfor, kan du manuelt søge efter dem i bibliotekerne i din Mac. Men før du gør dette, læs den fulde ansvarsfraskrivelse nedenfor:
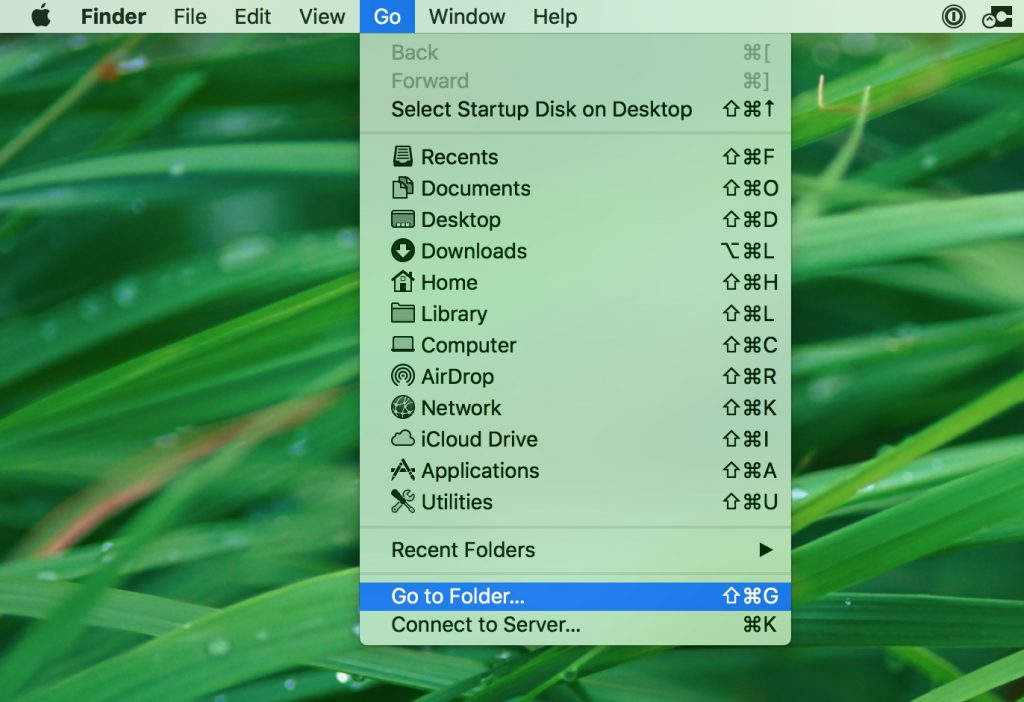
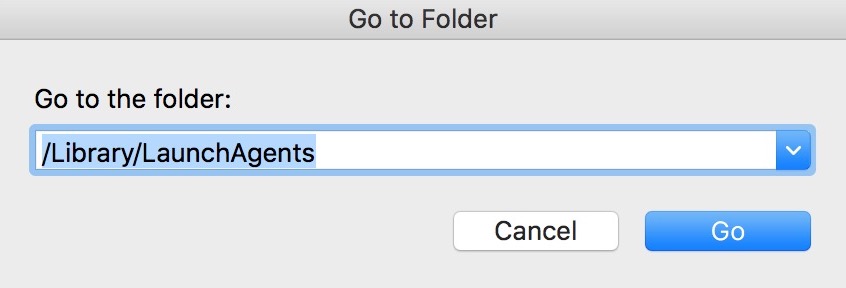
1. Klik på "Gå" og så "Gå til mappe" som vist nedenunder:
2. Indtaste "/Bibliotek / LauchAgents /" og klik på OK:
3. Slet alle de virus filer, der har lignende eller samme navn som MacOS Security Center. Hvis du mener, der er ingen sådan fil, skal du ikke slette noget.
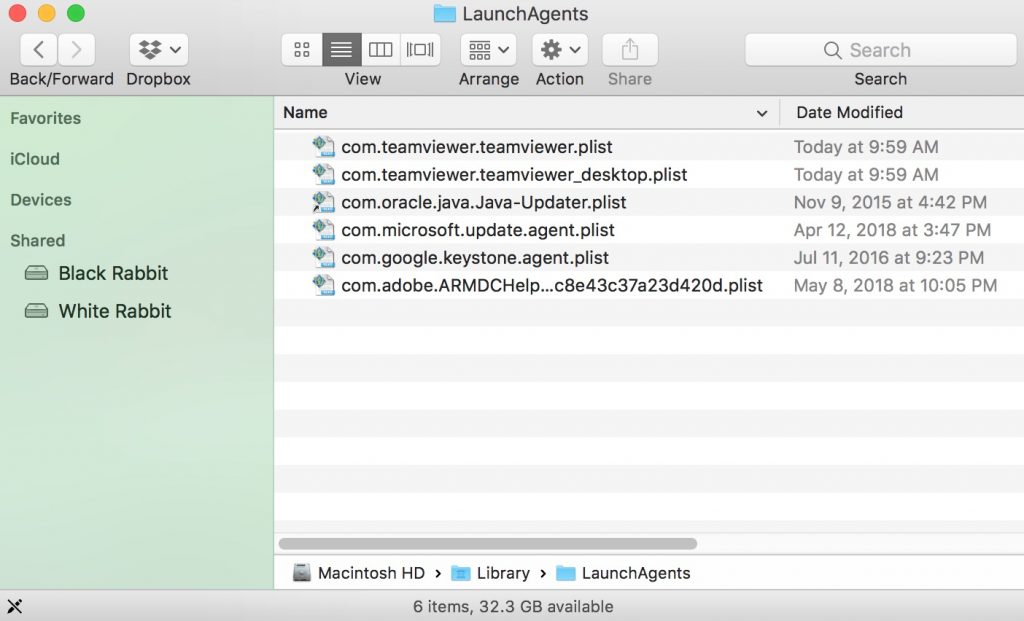
Du kan gentage den samme procedure med følgende andre Bibliotek biblioteker:
→ ~ / Library / LaunchAgents
/Bibliotek / LaunchDaemons
Tip: ~ er der med vilje, fordi det fører til flere LaunchAgents.
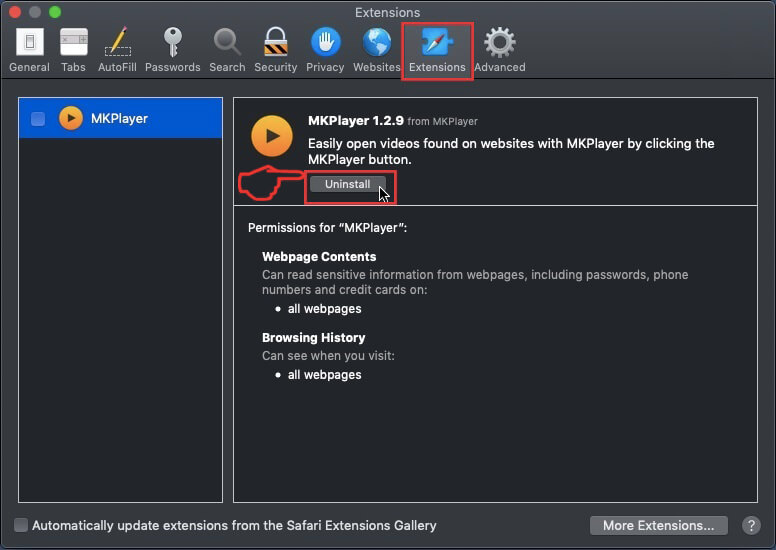
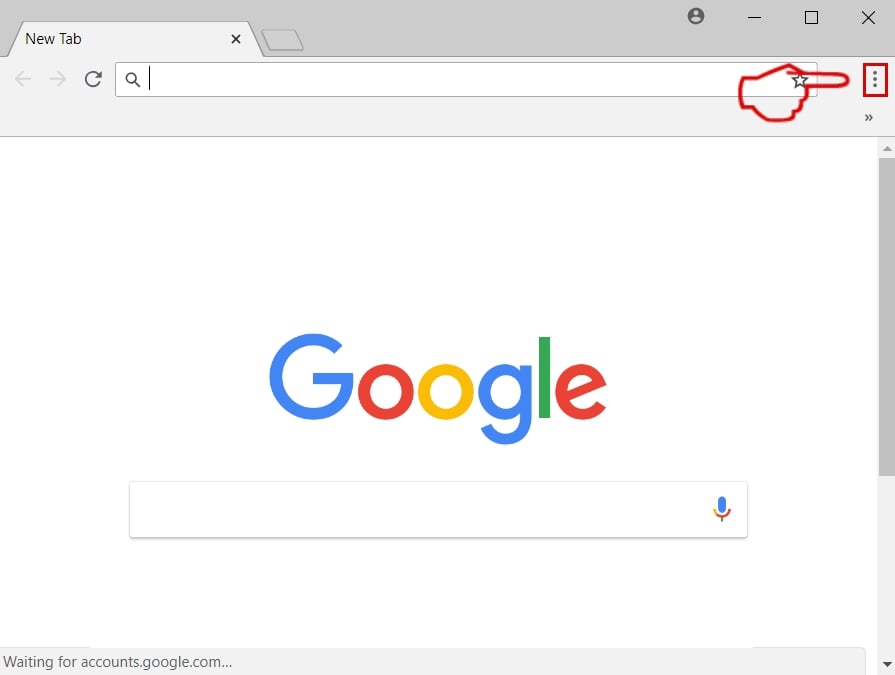
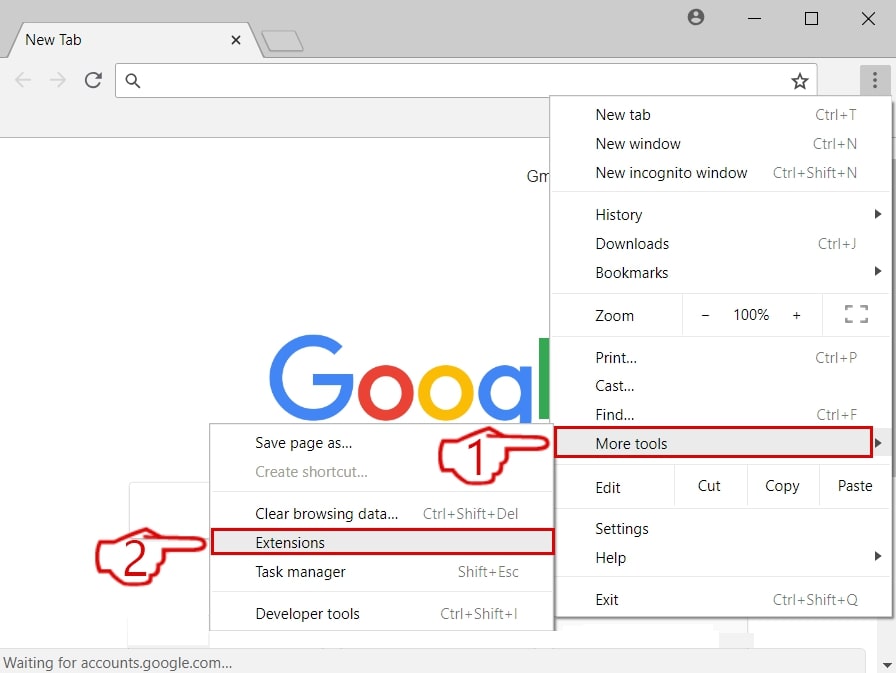
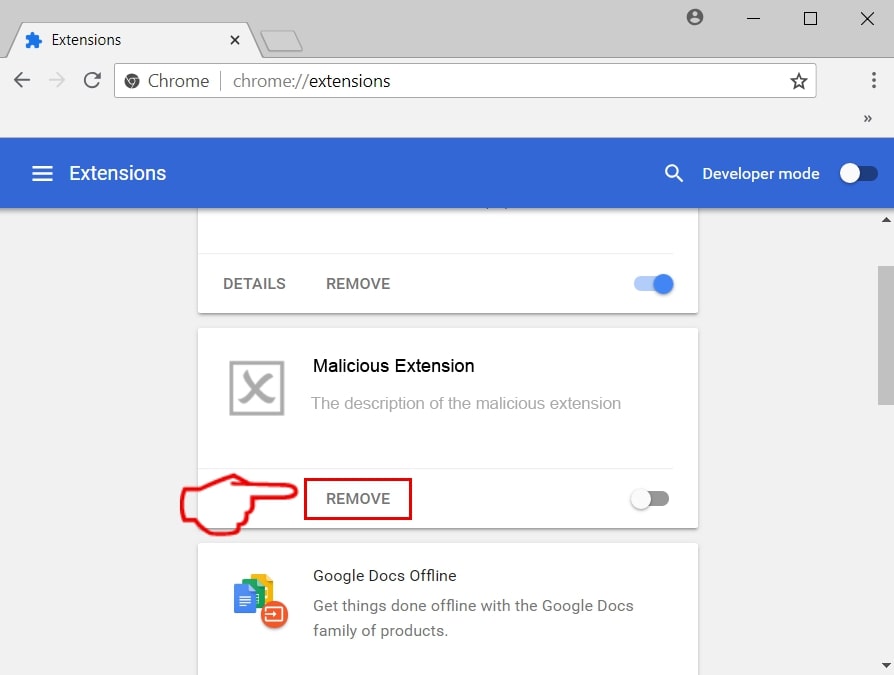
Trin 3: Fjern MacOS Security Center - relaterede udvidelser fra Safari / Krom / Firefox
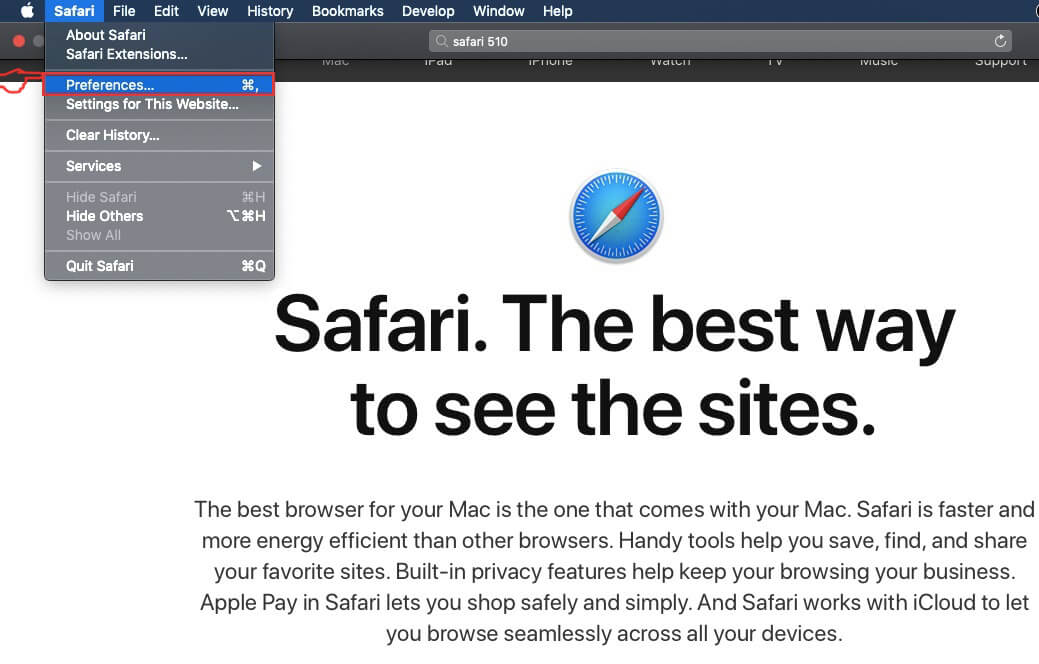
MacOS Security Center-FAQ
Hvad er MacOS Security Center på din Mac?
MacOS Security Center-truslen er sandsynligvis en potentielt uønsket app. Der er også en chance for, at det kan relateres til Mac malware. Hvis ja, sådanne apps har en tendens til at bremse din Mac betydeligt og vise reklamer. De kunne også bruge cookies og andre trackere til at få browserdata fra de installerede webbrowsere på din Mac.
Kan Mac'er få virus?
Ja. Så meget som enhver anden enhed, Apple-computere får malware. Apple-enheder er muligvis ikke et hyppigt mål af malware forfattere, men vær sikker på, at næsten alle Apple-enheder kan blive inficeret med en trussel.
Hvilke typer Mac-trusler er der?
Ifølge de fleste malware-forskere og cybersikkerhedseksperter, den typer af trusler der i øjeblikket kan inficere din Mac, kan være useriøse antivirusprogrammer, adware eller flykaprere (PUP), Trojanske heste, ransomware og crypto-miner malware.
Hvad skal jeg gøre, hvis jeg har en Mac-virus, Like MacOS Security Center?
Gå ikke i panik! Du kan let slippe af med de fleste Mac-trusler ved først at isolere dem og derefter fjerne dem. En anbefalet måde at gøre det på er ved at bruge en velrenommeret software til fjernelse af malware der kan tage sig af fjernelsen automatisk for dig.
Der er mange Mac-anti-malware apps derude, som du kan vælge imellem. SpyHunter til Mac er en af de anbefalede Mac-anti-malware-apps, der kan scanne gratis og opdage vira. Dette sparer tid til manuel fjernelse, som du ellers skulle gøre.
How to Secure My Data from MacOS Security Center?
Med få enkle handlinger. Først og fremmest, det er bydende nødvendigt, at du følger disse trin:
Trin 1: Find en sikker computer og tilslut det til et andet netværk, ikke den, som din Mac blev inficeret i.
Trin 2: Skift alle dine passwords, startende fra dine e-mail-adgangskoder.
Trin 3: Aktiver to-faktor-autentificering til beskyttelse af dine vigtige konti.
Trin 4: Ring til din bank til ændre dine kreditkortoplysninger (hemmelig kode, etc.) hvis du har gemt dit kreditkort til online shopping eller har foretaget onlineaktiviteter med dit kort.
Trin 5: Sørg for at ring til din internetudbyder (Internetudbyder eller operatør) og bed dem om at ændre din IP-adresse.
Trin 6: Skift din Wi-Fi-adgangskode.
Trin 7: (Valgfri): Sørg for at scanne alle enheder, der er tilsluttet dit netværk for vira, og gentag disse trin for dem, hvis de er berørt.
Trin 8: Installer anti-malware software med realtidsbeskyttelse på alle enheder, du har.
Trin 9: Prøv ikke at downloade software fra websteder, du ikke ved noget om, og hold dig væk fra websteder med lav omdømme i almindelighed.
Hvis du følger disse henstillinger, dit netværk og Apple-enheder bliver betydeligt mere sikre mod enhver trussel eller informationsinvasiv software og også være virusfri og beskyttet i fremtiden.
Flere tip, du kan finde på vores MacOS Virus sektion, hvor du også kan stille spørgsmål og kommentere dine Mac-problemer.
Om MacOS Security Center Research
Indholdet udgiver vi på SensorsTechForum.com, denne MacOS Security Center vejledning til fjernelse medfølger, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed for at hjælpe dig med at fjerne det specifikke macOS-problem.
Hvordan foretog vi undersøgelsen af MacOS Security Center?
Bemærk venligst, at vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om de seneste malware-definitioner, herunder de forskellige typer Mac-trusler, især adware og potentielt uønskede apps (tilfreds).
Endvidere, forskningen bag MacOS Security Center-truslen bakkes op med VirusTotal.
For bedre at forstå truslen fra Mac-malware, Se venligst følgende artikler, som giver kyndige detaljer.


