Adskillige ransomware varianter har været kendt for at dekryptere flere og flere brugerfiler sidst. Den ransomware selv og er også kendt som DecryptorMax eller CryptInfinite. Denne ødelæggende cyber-trussel mod brugernes pc'er har bevist, at det kan være ganske effektiv ved at kryptere vigtige brugerfiler og ardannelse brugere, at deres nøgler til dekryptering vil blive slettet i 24 timer, hvilket gør det umuligt for dem at dekryptere deres filer. Men, sikkerhedseksperter kraftigste råde brugerne til aldrig at betale løsepenge og finansiere de cyberkriminelle at fortsætte og øge deres ransomware kampagner. Også, der er flere metoder, som nogle .crinf filer kan dekrypteres, nævnt efter denne artikel.
| Navn | .Crinf Ransomware Trojan |
| Type | Ransomware Trojan |
| Kort beskrivelse | Den virus er kendt for at udføre administrrative kommandoer og kryptere brugerdata at afpresse brugeren om midler. |
| Symptomer | Brugeren kan have sit tapet ændret med løsepenge instruktioner og se hans filer krypteres, og ude af stand til at blive åbnet med den .crinf browserudvidelsen. |
| Distributionsmetode | Ondsindede weblinks eller inficerede vedhæftede filer. |
| Værktøj Detection | Hent Malware Removal Tool, for at se, om dit system er blevet påvirket af malware |
| Brugererfaring | Tilmeld dig vores forum at læse om, hvordan man dekryptere dine filer og diskutere.Crinf Ransomware. |
| Data Recovery Tool | Windows Data Recovery af Stellar Phoenix Varsel! Dette produkt scanner dine drev sektorer til at gendanne mistede filer, og det kan ikke komme sig 100% af de krypterede filer, men kun få af dem, afhængigt af situationen og uanset om du har omformateret drevet. |
.Crinf Ransomware - Hvordan klarede jeg mig det
En måde at være inficeret med denne modbydelige online trussel er ved blot at besøger den forkerte hjemmeside eller bliver omdirigeret til det. Dette kan ske, hvis du har klikket på et ondsindet URL i en kommentar, besked. Brugere rapporterer også omdirigeres ved at have adware-programmer på deres computere, skærm pop-ups og andre annoncer til sådanne ondsindede online steder.
Den anden måde, at denne ransowmare kan komme ind i brugerens pc'er og den mest udbredte ene er via e-mail. Nogle brugere rapporterer modtager beskeder på websites såsom Craigslist med vedhæftede .doc-filer med tilfældige navne som 28312-d21.docx, for eksempel. Disse inficerede vedhæftede filer kan enten have ekstra fil af følgende formater – .exe, .flagermus, .tmp, .etc. eller de kan have modificerede makroer, der skaber udnytter og lad den faktiske trojan trænge forsvaret af brugerens PC.
Enten måde, sikkerhedseksperter rådgive brugerne til at bruge ekstern mail management software som Mozilla Thunderbird eller Microsoft Outlook, for eksempel. Det er også stærkt anbefales ikke at åbne vedhæftede filer i meddelelser fra eksterne websteder, der har private beskeder tilstand. I tilfælde af at du ikke har andet valg, en avanceret anti-malware værktøj anbefales, at har en aktiv beskyttelse, blokere de indkommende indtrængen.
.Crinf Ransomware - Hvad gør det
Denne særlige form for ransomware er blevet analyseret af eksperter i informationssikkerhed til at udføre følgende aktiviteter når aktiveret på et kompromitteret system
Første, det genererer et offer id eller entydigt nummer til id den specifikke pc bliver inficeret. Det gør det ved at lave en ondsindet .exe-fil, der har et unikt sæt af tal og cifre med symboler så godt på det. Den .exe er normalt gemt i% User Files% biblioteket.
Den .crinf malware tager derefter fordel af vinduerne kommandoprompten indtaste disse kommandoer for at delete Fil Historie (Shadow Volume Kopier) således at berørte brugere ikke har backup af deres krypterede data:
→cmd.exe / k vssadmin.exe Slet Shadows / Alle / Stille
cmd.exe / k Bcdedit.exe / sæt {misligholdelse} recoveryenabled Nej
cmd.exe / k Bcdedit.exe / sæt {misligholdelse} bootstatuspolicy ignoreallfailures
Derudover de abovewritten kommandoer bruger bootstatuspolicy for at deaktivere Windows Startup Repair. Den gode nyhed er, at disse kommandoer kræver at køre som administrator, så du kan få besked en anmodning om at køre dem.
Efter at gøre følgende denne malware kan også dræbe nogle processer, mens den analyserer de filer, den ønsker at dekryptere.
Ifølge malware eksperter på BleepingComputer.com dette sker som regel ved at angive følgende kommandoer:
→Taskkill / F / IM msconfig.exe
Taskkill / F / IM rstrui.exe
Taskkill / F / IM tcpview.exe
Taskkill / F / IM procexp.exe
Taskkill / F / IM procmon.exe
Taskkill / F / IM regmon.exe
Taskkill / F / IM wireshark.exe
Taskkill / F / IM LordPE.exe
Taskkill / F / IM regedit.exe
Taskkill / F / IM cmd.exe
Taskkill / F / IM filemon.exe
Taskkill / F / IM procexp64.exe
Efter den tvivlsomme malware er scannet for filer til at kryptere, det begynder krypteringsprocessen.
Det kravler gennem alle drevbogstaver til at kryptere filer, der indeholder nogen af følgende udvidelser:
→*.accdb, *.BUGT, *.DBF, *.DET, *.DNG, *.DOCX, *.DXF, *.ERF, *.INDD, *.MEF, *.MRW, *.ODB, *.RIP, *.PDD, *.PEF, *.pptm, *.PSD, *.PTX, *.RÅ, *.SRF, *.XLK, *.XLS, *.men, *.gå, *.ARW, *.ASF, *.ASX, *.avi, *.tilbage, *.backup, *.bag, *.er, *.blanding, *.cdr, *.himmel, *.cpp, *.crt, *.CRW, *.hvilken, *.dcr, *.dds, *.af, *.dette, *.doc, *.docm, *.dtd, *.dwg, *.DXG, *.edb, *.bryst, *.EPS, *.fla, *.flac, *.flvv, *.gif, *.grupper, *.hdd, *.HPP, *.IIf, *.java, *.KDC, *.nøgle, *.historie, *.log, *.tage, *.m2ts, *.max, *.CIS, *.mdf, *.mkv, *.mov, *.mpeg, *.mpg, *.msg, *.ndf, *.kirkeskibet, *.NRW, *.NVRAM, *.OAB, *.obj, *.Ep, *.ODM, *.afsnit, *.odt, *.ogg, *.orf'en, *.ost, *.hjælpe, *.ikke, *.pct, *.bps, *.pdf, *.PEM, *.pfx, *.pif, *.png, *.pps, *.ppt, *.pptx, *.PRF, *.pst, *.PWM, *.altoverskyggende, *.QBB, *.QBM, *.ICBm'ere, *.QBW, *.qbx, *.qby, *.qcow, *.qcow2, *.er, *.raf, *.rtf, *.RVT, *.RWL, *.sikker, *.sav, *.sql, *.srt, *.SRW, *.stm, *.svg, *.swf, *.tex, *.tga, *.THM, *.pcs, *.VBOX, *.VDI, *.vhd, *.vhdx, *.VMDK, *.vmsd, *.VMX, *.vmxf, *.vob, *.wav, *.wma, *.wmv, *.WPD, *.WPS, *.XLR, *.xlsb, *.xlsm, *.XLSX, *.lavere satser,*.JPEG,*.JPE, *.jpg
Efter en fil er blevet krypteret, det kan se ud på følgende måde - /Filnavn/.jpg.crinf eller simpelthen /filnavn /.crinf.
Når det krypterer filer med .crinf-udvidelsen i slutningen af det, malware kan ekskludere alle andre filer, der indeholder følgende strenge-Vinduer, Program Files, NØGLE, .crinf
Mens det udfører krypteringsprocessen, trojanen kan tilføje en registreringsværdi for hver af de udfyldninger, der er under nøglen “HKCU Software CryptInfinite”:
For eksempel, hvis filerne indeholder følgende navne:
→HKCU Software CryptInfinite Files 11
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21983.jpg
HKCU Software CryptInfinite Files 12
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21234983.jpg
HKCU Software CryptInfinite Files 13
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21454564983.jpg
HKCU Software CryptInfinite Files 14
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21342983.jpg
HKCU Software CryptInfinite Files 15
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21983.jpg
HKCU Software CryptInfinite Files 16
C:\Brugere Offentlige Billeder Eksempelbilleder DSC21912312383.jpg
HKCU Software CryptInfinite Files 17
C:\Brugere Offentlige Billeder Eksempelbilleder DSC2146983.jpg
Ransomware-trojanen kan også tilføje yderligere oplysninger i Windows Registreringseditor til den samme registreringsdatabasenøgle. Dens sidste fase er at ændre skrivebordsbaggrunden for at vise en løsesumnote og dermed automatisk starte dens eksekverbare filer ved at tilføje den sædvanlige HKEY_LOCAL_USER Run-nøgle i den.
Ransomware kan også tilføje følgende nøgler med forskellige værdier:
→HKCU Software CryptInfinite
HKCU Software CryptInfinite Files
HKCU Software CryptInfinite Info
HKCU Software CryptInfinite Info KEY 000000
HKCU Software CryptInfinite Info 1 000000
HKCU Software CryptInfinite Info c 23
HKCU Software CryptInfinite Info m 57
HKCU Software CryptInfinite Info s 21
HKCU Software CryptInfinite Info Finish True
HKCU Software Microsoft Windows CurrentVersion Run Microsoft Corporation C:\Brugere
HKCU Kontrolpanel Desktop WallpaperStyle “0”
HKCU Control Panel Desktop Wallpaper “C:\Brugere
Endelig, den ransomware ændrer brugerens tapet til en løsesum notat besked:
Den trojanske falder også en fil med samme løsesum instruktioner. Det kaldes ReadDecryptFilesHere.txt og den tabes i hver mappe, hvor krypterede filer kan findes.
Det er det budskab set i både tapet, .txt dokument og .exe selve softwaren:
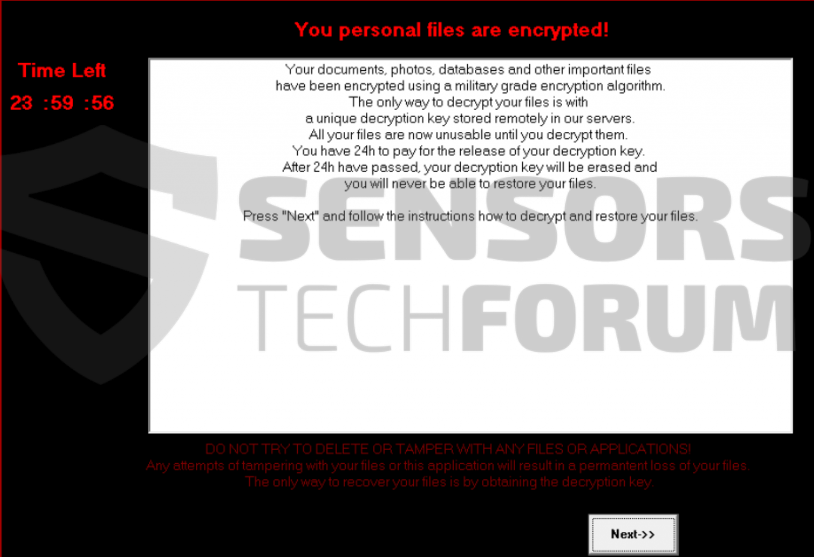
→”Dine personlige filer er blevet krypteret!
Dine dokumenter, billeder, databaser og andre vigtige filer er blevet krypteret ved hjælp af en militær kvalitet krypteringsalgoritme.
Den eneste måde at dekryptere dine filer er med en unik krypteringsnøgle gemt eksternt i vores servere. Alle dine filer er nu
ubrugelig, indtil du dekryptere dem. Du har 24 timer til at betale for udgivelsen af din dekrypteringsnøgle. Efter 24 timer er gået, dine
dekrypteringsnøgle vil blive slettet, og du vil aldrig være i stand til at gendanne dine filer.
For at få din unikke dekrypteringsnøgle du bliver nødt til at betale $500 under anvendelse af en PayPal MyCash kupon.
Hvis betalingen ikke fremsendes inden 12h beløbet for at få din dekryptering nøgle vil være $1000.
PayPal MyCash værdikuponer kan købes på CVS, 7-Elleve, dollar General, fred`s Super Dollar,
Family Dollar og mange andre butikker.
——————————————————————–
Efter at have fået din PayPal-MyCash rabatkode du har brug for at sende en e-mail til
silasw9pa@yahoo.co.uk med følgende oplysninger.
1. Din $500 PayPal MyCash PIN
2. Dine kryptering id =
Kort efter kuponen er modtaget og kontrolleret, alle dine filer vil blive gendannet til deres tidligere tilstand.
Alle betalinger behandles og verificeret manuelt, ikke forsøger at sende ugyldige PIN-numre.”
Endelig brugeren bliver præsenteret en brugergrænseflade med det samme budskab og ’Næste’ knap byder instruktioner om fil dekryptering.
Fjern .Crinf Ransomware Helt
For at fjerne denne ransomware er det vigtigt at handle, som om du fjerner enhver anden trojansk hest fra din computer og isolere truslen først. Derefter, du skal starte op i fejlsikret tilstand og scanne din computer med en avanceret anti-malware program med henblik på at fjerne ransomware effektivt, da enhver PC infektion er unik i sig selv.
Her er en vejledning i at komme af med denne ransomware. Husk på, at du bør sikkerhedskopiere dine krypterede filer først, da du vil være at forsøge at dekryptere dem senere:
Gendannelse af dine filer
Der er flere metoder til at gendanne dine filer. Vi har arrangeret dem fra de mest simple dem til de mest teknisk dygtige metoder.
Metode 1: Omdøb filtypenavne.
Mange brugere har rapporteret på fora, at det lykkedes at genvinde en lille del af deres filer ved blot at fjerne .Crinf udvidelse fra dem og gemme filen i dens oprindelige. Men dette er ingen garanti at du vil være i stand til at dekryptere alle dine filer, kun at du kan have mulighed for at dekryptere nogle af dem.
Metode 2: Brug Volume Shadow Kopier
Der er en solid chance for, at dine volumen øjebliksbilleder måske ikke er blevet slettet af kommandoerne udført af denne ransomware, da de kræver administrative rettigheder.
Så hvis du har fil historie aktiveret du kan have en god chance for at genskabe dine data. Den sikreste måde at gøre dette kan være at starte op i fejlsikret tilstand og prøv ekstern software kaldet, Shadow Explorer. Du kan hente den, hvis du klikker på dette link:
https://www.shadowexplorer.com/downloads.html
Metode 3: Brug Kasperskys hjælpeprogrammer eller andre værktøjer
Du kan være i stand til at dekryptere dine data direkte i tilfælde kun en del af filen i selve koden er krypteret med svag kryptering. Prøv en af følgende offentliggjorte Kaspersky værktøjer at dekryptere dine data:
https://support.kaspersky.com/viruses/utility#
her er også en RSA dekryptering værktøj det lykkedes os at finde online:
https://www.aeppro.com/download/latest.shtml
Metode 4: Brug Python i Linux
Her er et forslag, hvis filerne har en tilsvarende nøgle, der skal afkodes. Det er en mere teknisk dygtige mulighed, men hvis du er fast besluttet du kan få mulighed for at dekryptere dine data:
https://sensorstechforum.com/restore-files-encrypted-via-rsa-encryption-remove-cryptowall-and-other-ransomware-manually/
- Trin 1
- Trin 2
- Trin 3
- Trin 4
- Trin 5
Trin 1: Scan efter .Crinf Ransomware Trojan med SpyHunter Anti-Malware værktøj



Automatisk fjernelse af ransomware - Videoguide
Trin 2: Uninstall .Crinf Ransomware Trojan and related malware from Windows
Her er en metode i nogle få nemme trin, der bør være i stand til at afinstallere de fleste programmer. Uanset om du bruger Windows 10, 8, 7, Vista eller XP, disse skridt vil få arbejdet gjort. At trække det program eller dets mappe til papirkurven kan være en meget dårlig beslutning. Hvis du gør det, stumper og stykker af programmet er efterladt, og det kan føre til ustabile arbejde på din PC, fejl med filtypen foreninger og andre ubehagelige aktiviteter. Den rigtige måde at få et program fra din computer er at afinstallere det. For at gøre dette:


 Følg instruktionerne ovenfor, og du vil med succes slette de fleste uønskede og ondsindede programmer.
Følg instruktionerne ovenfor, og du vil med succes slette de fleste uønskede og ondsindede programmer.
Trin 3: Rens eventuelle registre, skabt af .Crinf Ransomware Trojan på computeren.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, skabt af .Crinf Ransomware Trojan der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Inden start "Trin 4", be om boot tilbage til normal tilstand, hvis du er i øjeblikket i fejlsikret tilstand.
Dette vil gøre det muligt for dig at installere og brug SpyHunter 5 succesfuld.
Trin 4: Boot din pc i fejlsikret tilstand for at isolere og fjerne .Crinf Ransomware Trojan





Trin 5: Prøv at gendanne filer krypteret med .Crinf Ransomware Trojan.
Metode 1: Brug STOP Decrypter af Emsisoft.
Ikke alle varianter af denne ransomware kan dekrypteres gratis, men vi har tilføjet den decryptor bruges af forskere, der ofte opdateret med de varianter, der i sidste ende blive dekrypteret. Du kan prøve og dekryptere dine filer ved hjælp nedenstående vejledning, men hvis de ikke arbejde, så desværre din variant af ransomware virus er ikke dekrypteres.
Følg instruktionerne nedenfor for at bruge Emsisoft Decrypter og dekryptere dine filer gratis. Du kan downloade Emsisoft dekryptering værktøj knyttet her og derefter følge trinene nedenfor tilvejebragte:
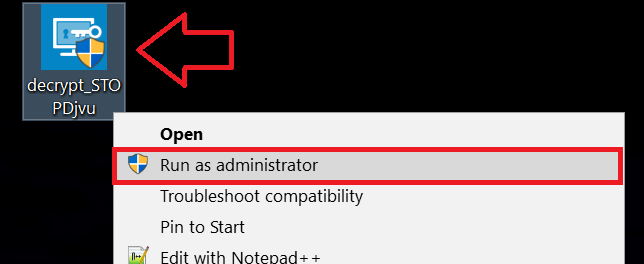
1 Højreklik på Decrypter og klik på Kør som administrator som vist nedenfor:
2. Enig med licensbetingelserne:
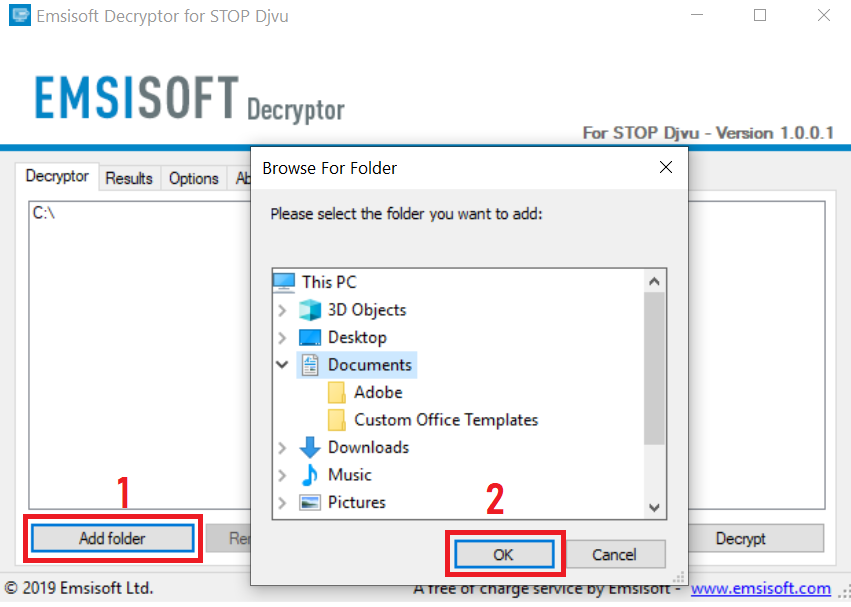
3. Klik på "Tilføj mappe" og derefter tilføje de mapper, hvor du ønsker filerne dekrypteret som vist nedenunder:
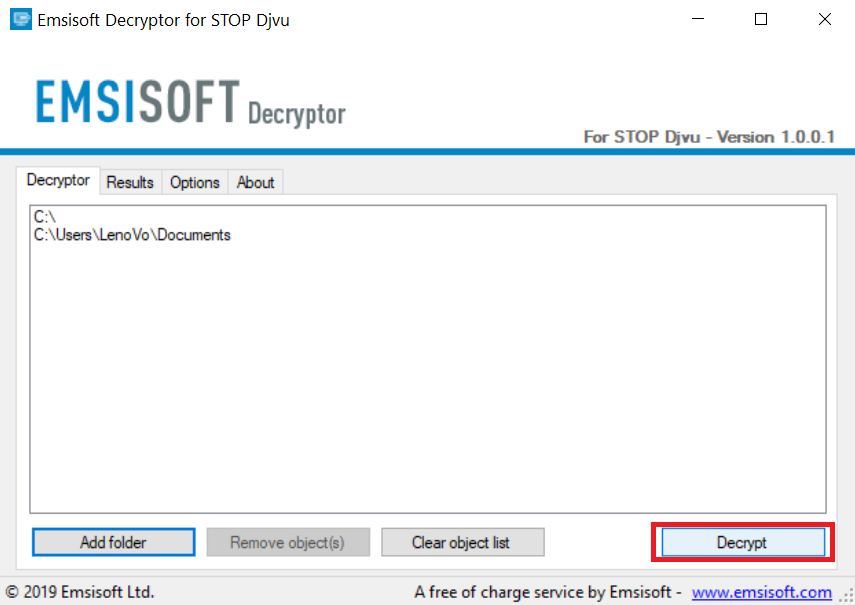
4. Klik på "Dekryptér" og vente på dine filer, der skal afkodes.
Note: Kredit til decryptor går til Emsisoft forskere, der har gjort det gennembrud med denne virus.
Metode 2: Brug datagendannelsessoftware
Ransomware infektioner og .Crinf Ransomware Trojan formål at kryptere dine filer ved hjælp af en krypteringsalgoritme, som kan være meget vanskeligt at dekryptere. Det er derfor, vi har foreslået en data recovery metode, der kan hjælpe dig med at gå rundt direkte dekryptering og forsøge at gendanne dine filer. Husk, at denne metode ikke kan være 100% effektiv, men kan også hjælpe dig lidt eller meget i forskellige situationer.
Du skal blot klikke på linket og på hjemmesidens menuer øverst, vælge data Recovery - Guiden til gendannelse af data til Windows eller Mac (afhængigt af dit operativsystem), og download og kør derefter værktøjet.
.Crinf Ransomware Trojan-FAQ
What is .Crinf Ransomware Trojan Ransomware?
.Crinf Ransomware Trojan er en ransomware infektion - den ondsindede software, der lydløst kommer ind på din computer og blokerer enten adgang til selve computeren eller krypterer dine filer.
Mange ransomware-vira bruger sofistikerede krypteringsalgoritmer til at gøre dine filer utilgængelige. Målet med ransomware-infektioner er at kræve, at du betaler en løsepenge-betaling for at få adgang til dine filer tilbage.
What Does .Crinf Ransomware Trojan Ransomware Do?
Ransomware er generelt en ondsindet software der er designet for at blokere adgangen til din computer eller filer indtil en løsesum er betalt.
Ransomware-virus kan også beskadige dit system, korrupte data og slette filer, resulterer i permanent tab af vigtige filer.
How Does .Crinf Ransomware Trojan Infect?
Via flere måder..Crinf Ransomware Trojan Ransomware inficerer computere ved at blive sendt via phishing-e-mails, indeholder virus vedhæftning. Denne vedhæftning maskeres normalt som et vigtigt dokument, lignende En faktura, bankdokument eller endda en flybillet og det ser meget overbevisende ud for brugerne.
Another way you may become a victim of .Crinf Ransomware Trojan is if you download et falsk installationsprogram, crack eller patch fra et websted med lavt omdømme eller hvis du klikker på et viruslink. Mange brugere rapporterer at få en ransomware-infektion ved at downloade torrents.
How to Open ..Crinf Ransomware Trojan files?
Du can't uden en dekryptering. På dette tidspunkt, den ..Crinf Ransomware Trojan filer er krypteret. Du kan kun åbne dem, når de er dekrypteret ved hjælp af en specifik dekrypteringsnøgle til den bestemte algoritme.
Hvad skal man gøre, hvis en dekryptering ikke virker?
Gå ikke i panik, og sikkerhedskopiere filerne. Hvis en dekrypter ikke dekrypterede din ..Crinf Ransomware Trojan filer med succes, så fortvivl ikke, fordi denne virus stadig er ny.
Kan jeg gendanne "..Crinf Ransomware Trojan" Filer?
Ja, undertiden kan filer gendannes. Vi har foreslået flere filgendannelsesmetoder det kunne fungere, hvis du vil gendanne ..Crinf Ransomware Trojan filer.
Disse metoder er på ingen måde 100% garanteret, at du vil være i stand til at få dine filer tilbage. Men hvis du har en sikkerhedskopi, dine chancer for succes er meget større.
How To Get Rid of .Crinf Ransomware Trojan Virus?
Den sikreste måde og den mest effektive til fjernelse af denne ransomware-infektion er brugen a professionelt anti-malware program.
Det vil scanne efter og finde .Crinf Ransomware Trojan ransomware og derefter fjerne det uden at forårsage yderligere skade på dine vigtige ..Crinf Ransomware Trojan filer.
Kan jeg rapportere Ransomware til myndigheder?
Hvis din computer blev inficeret med en ransomware-infektion, du kan rapportere det til de lokale politiafdelinger. Det kan hjælpe myndigheder overalt i verden med at spore og bestemme gerningsmændene bag den virus, der har inficeret din computer.
Nedenfor, Vi har udarbejdet en liste med offentlige websteder, hvor du kan indgive en rapport, hvis du er offer for en cyberkriminalitet:
Cybersikkerhedsmyndigheder, ansvarlig for håndtering af ransomware-angrebsrapporter i forskellige regioner over hele verden:
Tyskland - Officiel portal for det tyske politi
Forenede Stater - IC3 Internet Crime Complaint Center
Storbritannien - Action svig politi
Frankrig - Indenrigsministeriet
Italien - Statens politi
Spanien - Nationalt politi
Holland - Retshåndhævelse
Polen - Politi
Portugal - Justitspolitiet
Grækenland - Enhed om cyberkriminalitet (Hellenske politi)
Indien - Mumbai-politiet - CyberCrime-undersøgelsescelle
Australien - Australsk High Tech Crime Center
Rapporter kan besvares inden for forskellige tidsrammer, afhængigt af dine lokale myndigheder.
Kan du stoppe Ransomware i at kryptere dine filer?
Ja, du kan forhindre ransomware. Den bedste måde at gøre dette på er at sikre, at dit computersystem er opdateret med de nyeste sikkerhedsrettelser, bruge et velrenommeret anti-malware program og firewall, sikkerhedskopiere dine vigtige filer ofte, og undgå at klikke videre ondsindede links eller downloade ukendte filer.
Can .Crinf Ransomware Trojan Ransomware Steal Your Data?
Ja, i de fleste tilfælde ransomware vil stjæle dine oplysninger. It is a form of malware that steals data from a user's computer, krypterer det, og kræver derefter en løsesum for at dekryptere den.
I mange tilfælde, den malware forfattere eller angribere vil true med at slette data eller udgive det online medmindre løsesummen er betalt.
Kan Ransomware inficere WiFi?
Ja, ransomware kan inficere WiFi-netværk, da ondsindede aktører kan bruge det til at få kontrol over netværket, stjæle fortrolige data, og låse brugere ud. Hvis et ransomware-angreb lykkes, det kan føre til tab af service og/eller data, og i nogle tilfælde, økonomiske tab.
Skal jeg betale Ransomware?
Nej, du bør ikke betale ransomware-afpressere. At betale dem opmuntrer kun kriminelle og garanterer ikke, at filerne eller dataene bliver gendannet. Den bedre tilgang er at have en sikker backup af vigtige data og være opmærksom på sikkerheden i første omgang.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, hackerne kan stadig have adgang til din computer, data, eller filer og kan fortsætte med at true med at afsløre eller slette dem, eller endda bruge dem til at begå cyberkriminalitet. I nogle tilfælde, de kan endda fortsætte med at kræve yderligere løsepengebetalinger.
Kan et Ransomware-angreb opdages?
Ja, ransomware kan detekteres. Anti-malware-software og andre avancerede sikkerhedsværktøjer kan opdage ransomware og advare brugeren når det er til stede på en maskine.
Det er vigtigt at holde sig ajour med de seneste sikkerhedsforanstaltninger og at holde sikkerhedssoftware opdateret for at sikre, at ransomware kan opdages og forhindres.
Bliver ransomware-kriminelle fanget?
Ja, ransomware-kriminelle bliver fanget. Retshåndhævende myndigheder, såsom FBI, Interpol og andre har haft succes med at opspore og retsforfølge ransomware-kriminelle i USA og andre lande. I takt med at ransomware-trusler fortsætter med at stige, det samme gør håndhævelsesaktiviteten.
About the .Crinf Ransomware Trojan Research
Indholdet udgiver vi på SensorsTechForum.com, this .Crinf Ransomware Trojan how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed til at hjælpe dig med at fjerne den specifikke malware og gendanne dine krypterede filer.
Hvordan udførte vi undersøgelsen af denne ransomware?
Vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, og som sådan, vi modtager daglige opdateringer om de seneste malware- og ransomware-definitioner.
Endvidere, the research behind the .Crinf Ransomware Trojan ransomware threat is backed with VirusTotal og NoMoreRansom projekt.
For bedre at forstå ransomware-truslen, Se venligst følgende artikler, som giver kyndige detaljer.
Som et sted, der siden har været dedikeret til at levere gratis fjernelsesinstruktioner for ransomware og malware 2014, SensorsTechForum's anbefaling er at Vær kun opmærksom på pålidelige kilder.
Sådan genkendes pålidelige kilder:
- Kontroller altid "Om os" hjemmeside.
- Profil af indholdsskaberen.
- Sørg for, at rigtige mennesker er bag webstedet og ikke falske navne og profiler.
- Bekræft Facebook, LinkedIn og Twitter personlige profiler.


 1. For Windows 7, XP og Vista.
1. For Windows 7, XP og Vista. 2. For Windows 8, 8.1 og 10.
2. For Windows 8, 8.1 og 10.
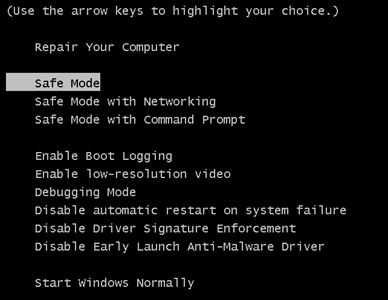
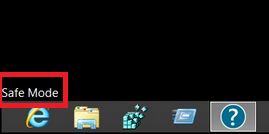
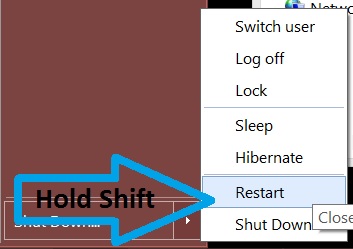
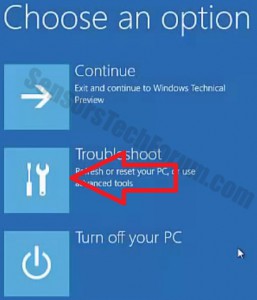
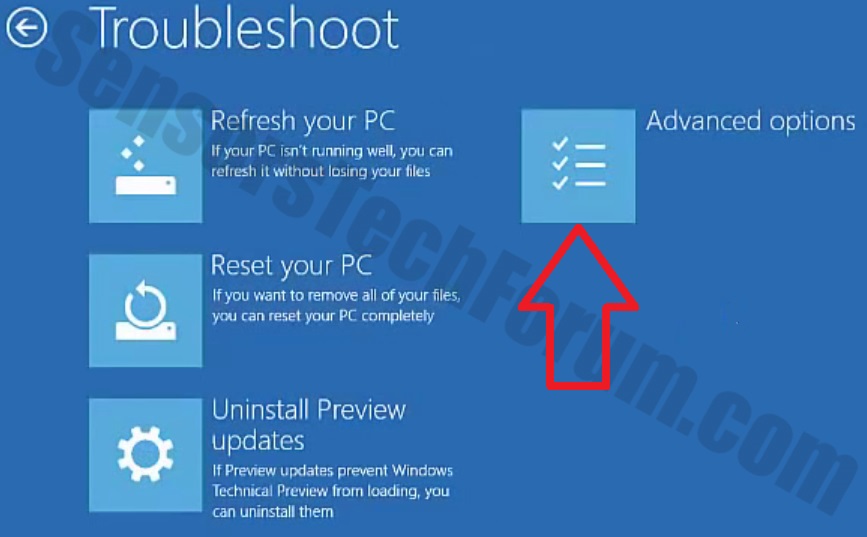
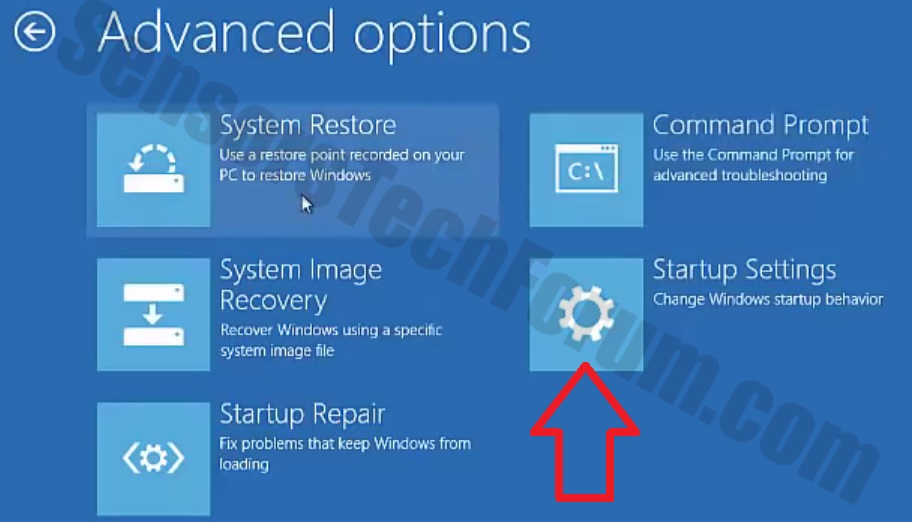

 1. Installer SpyHunter at scanne efter og fjerne .Crinf Ransomware Trojan.
1. Installer SpyHunter at scanne efter og fjerne .Crinf Ransomware Trojan.
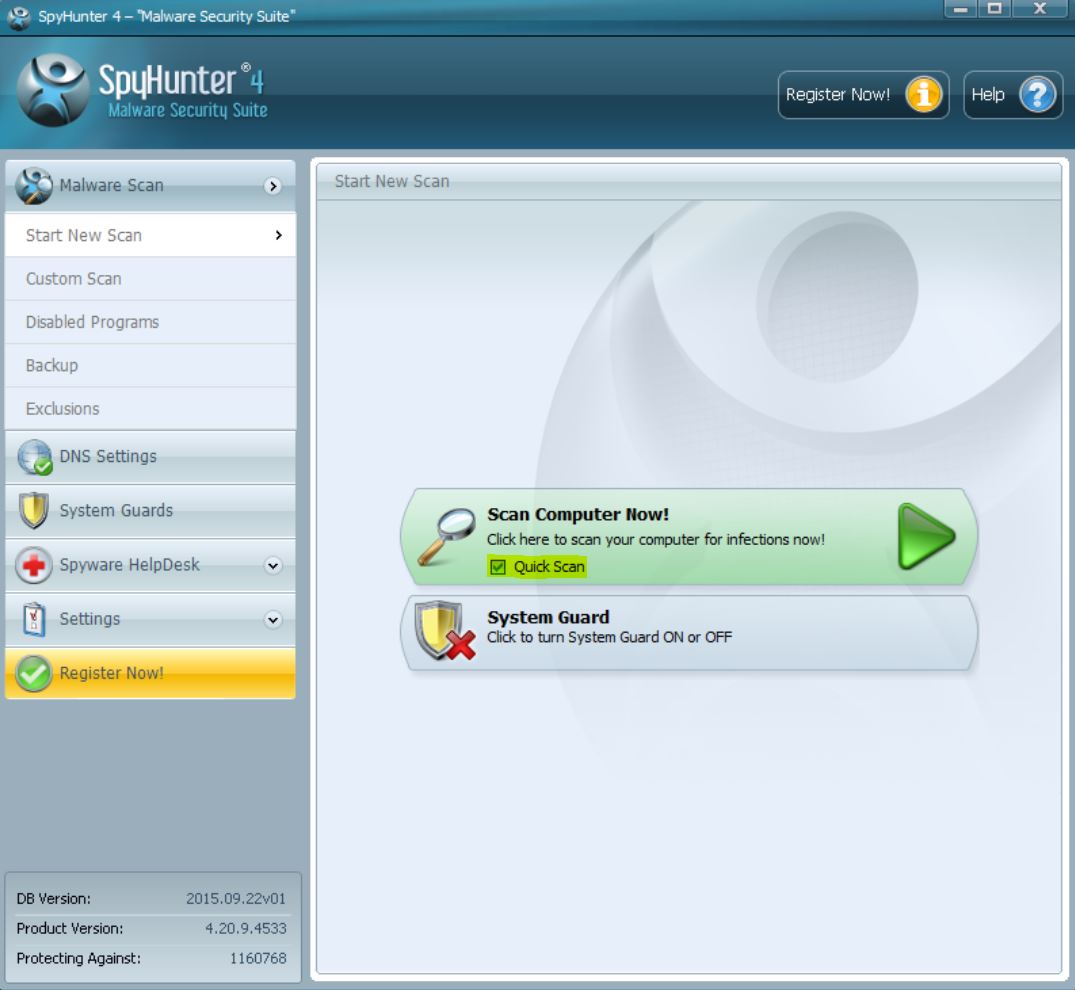
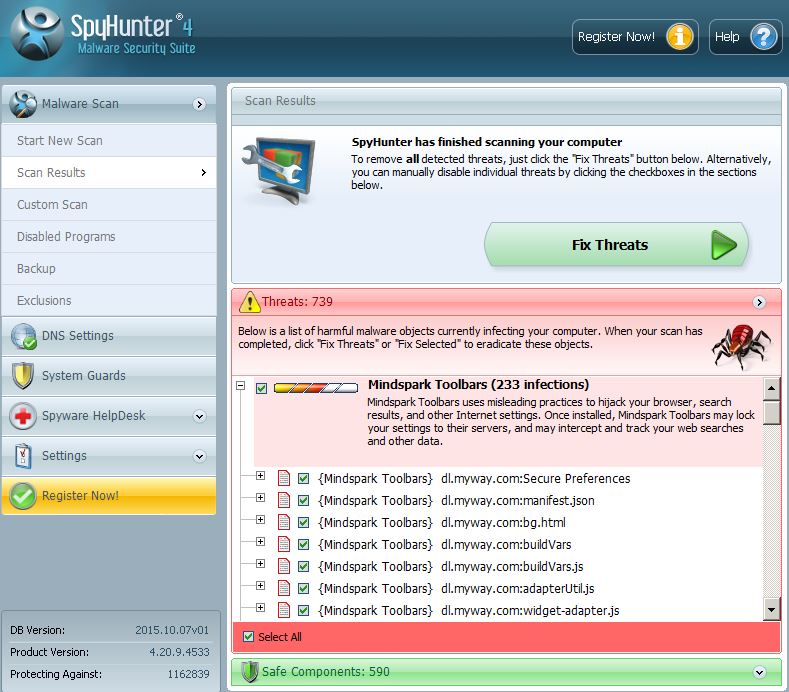
 1. Installer Malwarebytes Anti-Malware til scanning efter og fjerne .Crinf Ransomware Trojan.
1. Installer Malwarebytes Anti-Malware til scanning efter og fjerne .Crinf Ransomware Trojan.
 1. Installer STOPzilla Anti Malware at scanne efter og fjerne .Crinf Ransomware Trojan.
1. Installer STOPzilla Anti Malware at scanne efter og fjerne .Crinf Ransomware Trojan.