Takahiro Locker es el nombre de un ransomware, los cuales tiene su mensaje de rescate escrita en japonés. A pesar de eso, Los usuarios japoneses podrían no ser los únicos dirigidos. El ransomware busca para cifrar archivos con un pequeño número de extensiones, pero aquellos con los datos más importantes para los usuarios. Para ver cómo eliminar este ransomware y qué puede intentar restaurar sus archivos, usted debe leer este artículo a su fin.

Resumen de amenazas
| Nombre | Takahiro Locker |
| Escribe | El ransomware |
| Descripción breve | El ransomware cifra los archivos y solicita un rescate de 3 Bitcoins. |
| Los síntomas | El ransomware bloquea principalmente documentos e imágenes entre archivos multimedia. Crea una nota de rescate escrita en japonés.. |
| Método de distribución | Los correos electrónicos de spam, Archivos adjuntos de correo electrónico, Los archivos ejecutables |
| Herramienta de detección |
Ver si su sistema ha sido afectado por malware
Descargar
Herramienta de eliminación de software malintencionado
|
| Experiencia de usuario | Unirse a nuestro foro hablar sobre Takahiro Locker. |
| Herramienta de recuperación de datos | Ventanas de recuperación de datos de Stellar Phoenix darse cuenta! Este producto escanea los sectores del disco para recuperar archivos perdidos y no puede recuperarse 100% de los archivos cifrados, pero sólo unos pocos de ellos, dependiendo de la situación y de si está o no han reformateado la unidad. |

Takahiro Locker Ransomware - Entrega
El ransomware Takahiro Locker tiene un archivo .exe que entrega su carga útil. Ese archivo ejecutable se entrega de varias formas. Una de las formas es si el archivo es eliminado por otro malware, y otro - si el usuario descargó el archivo sin saberlo. Sitios web maliciosos, las redes de medios sociales, y los servicios de intercambio de archivos pueden ser la fuente de descarga.
Los correos electrónicos no deseados no están excluidos de la transmisión de esta infección de ransomware. Correos electrónicos internos, podría haber código malicioso, ya sea como archivo adjunto o en el cuerpo del correo electrónico. Descargar un archivo adjunto o simplemente abrir un correo electrónico puede descargar el ejecutable de malware de Takahiro Locker. Tenga mucho cuidado con los correos electrónicos no deseados y los archivos de origen desconocido si desea evitar la infección..

Takahiro Locker Ransomware - Descripción técnica
Takahiro Locker así se llama este ransomware. Ese es el nombre que se muestra en la pantalla de bloqueo después del cifrado de archivos.. Se cree que es de origen japonés, pero también podría apuntar a otros hablantes de japonés en todo el mundo..
A continuación se muestra una lista con los nombres más populares de Takahiro Locker se muestra como detecciones en programas anti-malware:
- Trojan.Win32.Scar.nzln (Kaspersky)
- Trojan.GenericKD.3222895 (BitDefender)
- W32 / Scar.NZLN!tr (Fortinet)
- Ransom_TAKALOCKER.A (TrendMicro)
Una vez que se desata la carga útil, el ransomware creará nuevas carpetas en la computadora comprometida y creará el siguiente directorio:
→%Temperatura de usuario% Google Chrome
En su interior se copiará a sí mismo con el nombre "Update.exe", y esto se verá exactamente como una actualización temporal para el navegador Google Chrome. Después de esto, Se realizarán dos entradas de registro dentro del Registro de Windows..
→HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run Google Chrome Update Check =% User Temp% Google Chrome Update.exe
→HKEY_CURRENT_USER Software Google Update SEND SENDING = [dirección aleatoria]
La primera entrada del registro integra un mecanismo de inicio automático en Windows para que el ransomware pueda iniciarse con cada inicio del sistema operativo.. La segunda cadena del registro probablemente enviará información al propietario del malware a través de alguna dirección electrónica..
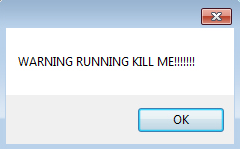
Puede ver que este error aparece en su pantalla en algún momento posterior (Imagen a la derecha). El mensaje de error dice: "ADVERTENCIA CORRER MATA! ". El mensaje sirve como inicio para la trama de la nota de rescate.. Todo es parte del plan de miedo para engañarte para que pagues el rescate.. Después, Takahiro Locker ransomware comenzará a cifrar archivos.
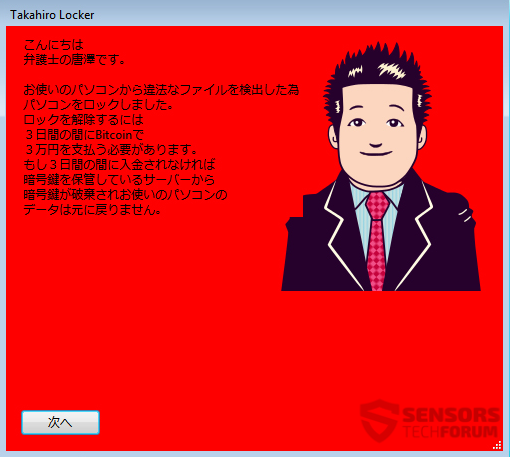
Los archivos cifrados suelen ser documentos e imágenes., pero puede bloquear otros archivos que la gente usa a diario. Una vez que el cifrado se realiza, se crea una nota de rescate, y aparece esta pantalla de bloqueo:
La nota de rescate en la pantalla de bloqueo está escrita en japonés, pero una traducción aproximada dice:
¡Hola,
esto es Tang, un abogado.
Ha realizado una transferencia de archivo ilegal, así que he bloqueado tu PC.
Para desbloquear sus archivos, usted tiene que pagar 3 bitcoins dentro 3 días.
Necesitas tener 30,000 Yen japonés, para transferirlos a Bitcoins y enviármelos.
Si no paga en el plazo 3 días, la clave para el descifrado se eliminará de donde se almacena el servidor y los datos de su PC ya no se podrán devolver.
Clic en el botón “Siguiente”.
Como vemos en la nota de arriba, el precio del rescate 3 Bitcoins. Y la amenaza de no enviar una clave de descifrado si el rescate no se paga dentro 3 días es probablemente cierto.
Todo, desde el mensaje de error hasta la nota de rescate, está hecho de forma muy inteligente.. En la mayoría de los países, el truco podría funcionar, porque los gobiernos vigilan las descargas de archivos, y esta acción está sancionada por la ley. Tener leyes estrictas sobre descargas podría funcionar en los pocos países que hablan japonés: Japón, Palau, Brasil, Estados Unidos, Perú, Filipinas, Francia.
Hacer NO pagar el rescate si reconoce que ha sido atacado con este ransomware. Pagar solo proporcionará dinero a los creadores de malware, que probablemente se utilizará para otros actos delictivos. No existe ninguna prueba de que la herramienta de descifrado proporcionada por dinero funcione siquiera.
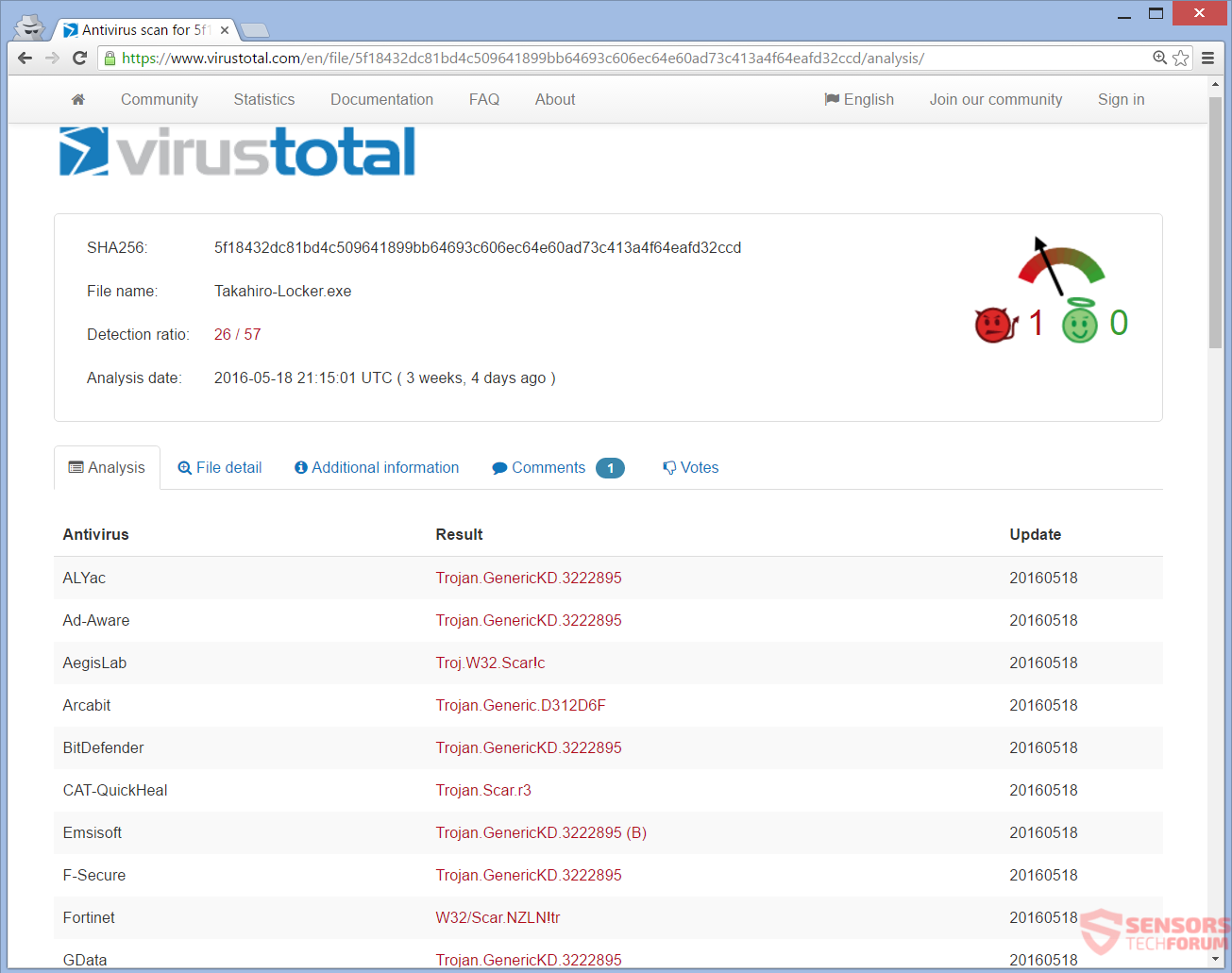
Takahiro Locker se detecta en VirusTotal de muchos programas de seguridad:
El Takahiro Locker ransomware bloquea archivos con extensiones relacionadas con documentos, fotos, torrentes, vídeos, música y archivos. Las extensiones que el ransomware busca cifrar son muy específicas y pequeñas en número., pero son lo que la gente todavía usa para almacenar sus datos importantes. Las extensiones cifradas son estas:
→.txt, .jpg, .png, .bmp, .cremallera, .rar, .torrente, .7desde, .sql, .pdf, .toma, .mp3, .mp4, .flv, .lnk, .html, .php
Curiosamente, Takahiro Locker no manipula ningún archivo en estas ubicaciones:
- Ventanas
- Vapor
- Origen
- Archivos de programa
- la papelera de reciclaje
Takahiro Locker ransomware, probablemente, también se eliminan Instantáneas de volumen desde el sistema operativo Windows.

Retire Takahiro Locker ransomware y restauración de archivos cifrados
Si su PC está infectado con el Takahiro Locker ransomware, debe tener experiencia en la eliminación de malware. Debe deshacerse del ransomware lo antes posible antes de que tenga la oportunidad de continuar cifrando archivos o extenderse más profundamente en su red.. Le recomendamos que siga las instrucciones paso a paso que se proporcionan aquí.
- Paso 1
- Paso 2
- Paso 3
- Paso 4
- Paso 5
Paso 1: Analizar en busca de Takahiro Locker con la herramienta de SpyHunter Anti-Malware



Eliminación automática de ransomware - Guía de video
Paso 2: Uninstall Takahiro Locker and related malware from Windows
Aquí es un método en pocos y sencillos pasos que debe ser capaz de desinstalar la mayoría de los programas. No importa si usted está utilizando Windows 10, 8, 7, Vista o XP, esos pasos conseguirán el trabajo hecho. Arrastrando el programa o su carpeta a la papelera de reciclaje puede ser una muy mala decisión. Si lo haces, partes y piezas del programa se quedan atrás, y que puede conducir a un trabajo inestable de su PC, errores con las asociaciones de tipo de archivo y otras actividades desagradables. La forma correcta de obtener un programa de ordenador es de desinstalarla. Para hacer eso:


 Siga las instrucciones anteriores y eliminará con éxito la mayoría de los programas maliciosos y no deseados..
Siga las instrucciones anteriores y eliminará con éxito la mayoría de los programas maliciosos y no deseados..
Paso 3: Limpiar los registros, creado por Takahiro Locker en tu computadora.
Los registros normalmente dirigidos de máquinas Windows son los siguientes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Puede acceder a ellos abriendo el editor del registro de Windows y eliminar cualquier valor, creado por Takahiro Locker allí. Esto puede ocurrir siguiendo los pasos debajo:


 Propina: Para encontrar un valor creado por virus, usted puede hacer clic derecho sobre él y haga clic "Modificar" para ver qué archivo que está configurado para ejecutarse. Si esta es la ubicación del archivo de virus, quitar el valor.
Propina: Para encontrar un valor creado por virus, usted puede hacer clic derecho sobre él y haga clic "Modificar" para ver qué archivo que está configurado para ejecutarse. Si esta es la ubicación del archivo de virus, quitar el valor.
Antes de empezar "Paso 4", Por favor arrancar de nuevo en el modo Normal, en caso de que usted está actualmente en modo seguro.
Esto le permitirá instalar y uso SpyHunter 5 exitosamente.
Paso 4: Inicie su PC en modo seguro para aislar y eliminar Takahiro Locker





Paso 5: Intente restaurar archivos cifrados por Takahiro Locker.
Método 1: Utilice STOP Decrypter de Emsisoft.
No todas las variantes de este ransomware se pueden descifrar de forma gratuita, pero hemos añadido el descifrador utilizado por los investigadores que a menudo se actualiza con las variantes que se convierten finalmente descifrado. Se puede tratar de descifrar los archivos mediante las siguientes instrucciones, pero si no funcionan, luego, por desgracia su variante del virus ransomware no es descodificarse.
Siga las instrucciones a continuación para utilizar el descifrador squared y descifrar sus archivos de forma gratuita. Puedes descargar la herramienta de descifrado squared vinculado aquí y luego siga los pasos indicados a continuación:
1 Botón derecho del ratón en el descifrador y haga clic en Ejecutar como administrador Como se muestra abajo:
2. De acuerdo con los términos de la licencia:
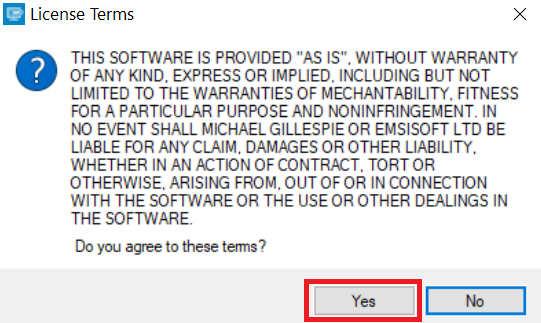
3. Haga clic en "Agregar carpeta" y luego agregar las carpetas en las que desea archivos descifrados como se muestra debajo:
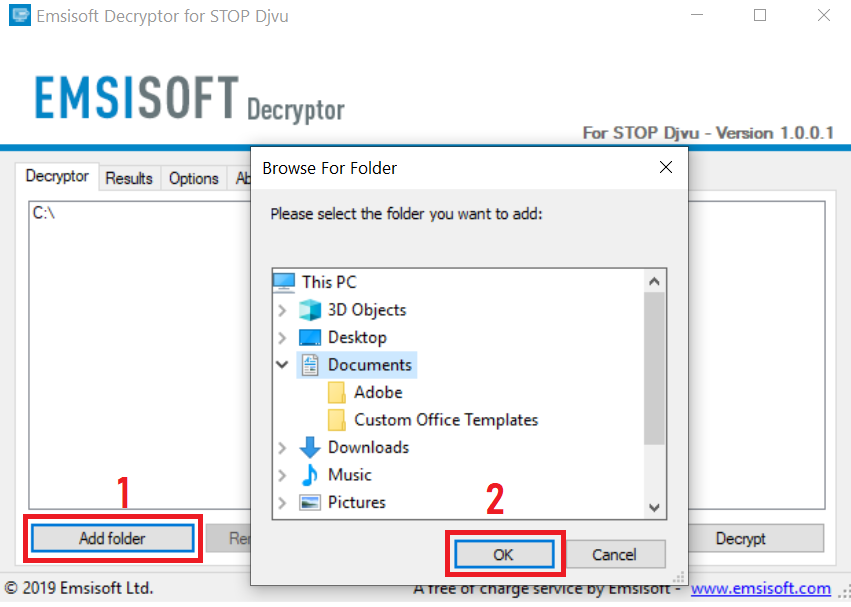
4. Haga clic en "desencriptar" y esperar a que los archivos a ser decodificados.
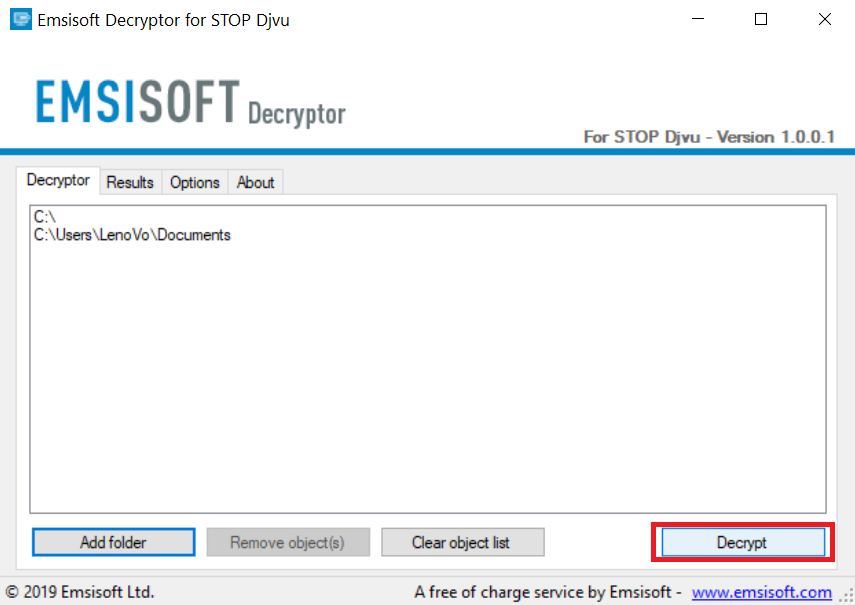
Nota: El crédito para el descifrador va a Emsisoft investigadores que han hecho el gran avance con este virus.
Método 2: Utilice software de recuperación de datos
Las infecciones de ransomware y Takahiro Locker tienen como objetivo cifrar sus archivos mediante un algoritmo de cifrado que puede ser muy difícil de descifrar. Es por esto que hemos sugerido un método de recuperación de datos que pueden ayudar a ir alrededor de descifrado directa e intentar restaurar sus archivos. Tenga en cuenta que este método puede no ser 100% eficaz, pero también puede ayudarle un poco o mucho en diferentes situaciones.
Simplemente haga clic en el enlace y en los menús del sitio web en la parte superior, escoger Recuperación de datos - Asistente de recuperación de datos para Windows o Mac (dependiendo de su sistema operativo), y luego descargue y ejecute la herramienta.
Takahiro Locker-FAQ
What is Takahiro Locker Ransomware?
Takahiro Locker es un ransomware infección - el software malicioso que ingresa a su computadora en silencio y bloquea el acceso a la computadora o encripta sus archivos.
Muchos virus ransomware usan sofisticados algoritmos de encriptación para hacer que sus archivos sean inaccesibles. El objetivo de las infecciones de ransomware es exigirle que pague un pago de rescate para obtener acceso a sus archivos..
What Does Takahiro Locker Ransomware Do?
El ransomware en general es un software malicioso que esta diseñado para bloquear el acceso a su computadora o archivos hasta que se pague un rescate.
Los virus ransomware también pueden dañar su sistema, corromper datos y eliminar archivos, resultando en la pérdida permanente de archivos importantes.
How Does Takahiro Locker Infect?
A través de varias formas, Takahiro Locker Ransomware infecta las computadoras al ser enviado a través de correos electrónicos de phishing, que contiene un archivo adjunto de virus. Este archivo adjunto generalmente está enmascarado como un documento importante, gusta una factura, documento bancario o incluso un billete de avión y parece muy convincente para los usuarios..
Another way you may become a victim of Takahiro Locker is if you descargar un instalador falso, crack o parche de un sitio web de baja reputación o si haces clic en un enlace de virus. Muchos usuarios informan haber contraído una infección de ransomware descargando torrents.
How to Open .Takahiro Locker files?
Tú can't sin descifrador. En este punto, la .Takahiro Locker son archivos cifrada. Sólo podrá abrirlos una vez que hayan sido descifrados usando una clave de descifrado específica para el algoritmo en particular..
Qué hacer si un descifrador no funciona?
No te asustes, y copia de seguridad de los archivos. Si un descifrador no descifró su .Takahiro Locker archivos con éxito, entonces no te desesperes, porque este virus aún es nuevo.
puedo restaurar ".Takahiro Locker" Archivos?
Sí, a veces los archivos pueden ser restaurados. Hemos sugerido varios métodos de recuperación de archivos eso podría funcionar si quieres restaurar .Takahiro Locker archivos.
Estos métodos no son de ninguna manera 100% garantizado que podrá recuperar sus archivos. Pero si tienes una copia de seguridad, tus posibilidades de éxito son mucho mayores.
How To Get Rid of Takahiro Locker Virus?
La forma más segura y la más eficiente para la eliminación de esta infección de ransomware es el uso de un programa anti-malware profesional.
Buscará y localizará el ransomware Takahiro Locker y luego lo eliminará sin causar ningún daño adicional a sus archivos importantes .Takahiro Locker.
¿Puedo denunciar ransomware a las autoridades??
En caso de que su computadora se infecte con una infección de ransomware, puede denunciarlo a los departamentos de policía locales. Puede ayudar a las autoridades de todo el mundo a rastrear y determinar a los perpetradores detrás del virus que ha infectado su computadora..
Abajo, hemos preparado una lista con sitios web gubernamentales, donde puede presentar una denuncia en caso de ser víctima de un ciberdelincuencia:
Autoridades de ciberseguridad, responsable de manejar los informes de ataques de ransomware en diferentes regiones de todo el mundo:
Alemania - Portal oficial de la policía alemana
Estados Unidos - Centro de quejas de delitos en Internet IC3
Reino Unido - Acción Fraude Policía
Francia - Ministerio del interior
Italia - Policía Estatal
España - Policía Nacional
Países Bajos - Cumplimiento de la ley
Polonia - Policía
Portugal - Policía Judicial
Grecia - Unidad de Delitos Cibernéticos (Policía helénica)
India - Policía de Mumbai - Célula de investigación de delitos cibernéticos
Australia - Centro australiano de delitos de alta tecnología
Los informes se pueden responder en diferentes períodos de tiempo, dependiendo de sus autoridades locales.
¿Puedes evitar que el ransomware cifre tus archivos??
Sí, puede prevenir el ransomware. La mejor manera de hacer esto es asegurarse de que su sistema informático esté actualizado con los últimos parches de seguridad., Utilice un programa antimalware de buena reputación. y cortafuegos, copia de seguridad de sus archivos importantes con frecuencia, y evita hacer clic en enlaces maliciosos o descargando archivos desconocidos.
Can Takahiro Locker Ransomware Steal Your Data?
Sí, en la mayoría de los casos ransomware robará tu información. It is a form of malware that steals data from a user's computer, lo encripta, y luego exige un rescate para descifrarlo.
En muchos casos, la autores de malware o los atacantes amenazarán con eliminar los datos o publicarlo en línea a menos que se pagó el rescate.
¿Puede el ransomware infectar WiFi??
Sí, ransomware puede infectar redes WiFi, ya que los actores maliciosos pueden usarlo para obtener el control de la red, robar datos confidenciales, y bloquear a los usuarios. Si un ataque de ransomware tiene éxito, podría conducir a una pérdida de servicio y/o datos, y en algunos casos, pérdidas financieras.
¿Debo pagar ransomware??
No, no debe pagar a los extorsionadores de ransomware. Pagarlos solo alienta a los delincuentes y no garantiza que los archivos o datos se restaurarán. El mejor enfoque es tener una copia de seguridad segura de los datos importantes y estar atento a la seguridad en primer lugar..
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, los piratas informáticos aún pueden tener acceso a su computadora, datos, o archivos y puede continuar amenazando con exponerlos o eliminarlos, o incluso utilizarlos para cometer delitos cibernéticos. En algunos casos, incluso pueden continuar exigiendo pagos de rescate adicionales.
¿Se puede detectar un ataque de ransomware??
Sí, ransomware puede ser detectado. Software antimalware y otras herramientas de seguridad avanzadas puede detectar ransomware y alertar al usuario cuando está presente en una máquina.
Es importante mantenerse al día con las últimas medidas de seguridad y mantener el software de seguridad actualizado para garantizar que el ransomware pueda detectarse y prevenirse..
¿Los delincuentes de ransomware son atrapados??
Sí, los criminales de ransomware son atrapados. Las fuerzas del orden, tales como el FBI, Interpol y otros han tenido éxito en rastrear y procesar a delincuentes de ransomware en EE. UU. y otros países.. A medida que las amenazas de ransomware siguen aumentando, también lo hace la actividad de aplicación.
About the Takahiro Locker Research
El contenido que publicamos en SensorsTechForum.com, this Takahiro Locker how-to removal guide included, es el resultado de una extensa investigación, trabajo duro y la dedicación de nuestro equipo para ayudarlo a eliminar el malware específico y restaurar sus archivos encriptados.
¿Cómo llevamos a cabo la investigación sobre este ransomware??
Nuestra investigación se basa en una investigación independiente. Estamos en contacto con investigadores de seguridad independientes, y como tal, recibimos actualizaciones diarias sobre las últimas definiciones de malware y ransomware.
Además, the research behind the Takahiro Locker ransomware threat is backed with VirusTotal y el proyecto NoMoreRansom.
Para comprender mejor la amenaza del ransomware, Consulte los siguientes artículos que proporcionan detalles informados..
Como un sitio que se ha dedicado a proporcionar instrucciones gratuitas de eliminación de ransomware y malware desde 2014, La recomendación de SensorsTechForum es solo preste atención a fuentes confiables.
Cómo reconocer fuentes confiables:
- Siempre verifica "Sobre nosotros" página web.
- Perfil del creador de contenido.
- Asegúrese de que haya personas reales detrás del sitio y no nombres y perfiles falsos.
- Verificar Facebook, Perfiles personales de LinkedIn y Twitter.