Bing(.)vc er en velkendt browser hijacker, der har eksisteret i et stykke tid nu. Den nyeste version af flykaprer, dog, er blevet rapporteret at sprede sig via legitime-lignende applikationer. At skyde skylden for dette er den berygtede metode bundling.
Intel og McAfee sikkerhedsforskere har opdaget, at Bing(.)vc malware er nu samlet med apps af Lavians Inc.. Sådan lyder rapporten:
Vi er stødt på flere filer fra Lavians Inc.. der ligner legitime applikationer, men kan udgøre en alvorlig risiko. Vi har observeret, at Lavians Inc.. ompakker rene applikationer med en browserkaprer for at undgå mistanke og for at øge dens rækkevidde.
Ifølge Intel, de fleste af de inficerede filer er skjult som driverværktøjer og har navne som:
→Opsætning af HP DESKJET F4580 driverværktøj, DELL Inspiron 5100 Opsætning af Drivers Utility, eller Acer Aspire ONE ZG5 Drivers Utility Setup.
Nye versioner af Bing(.)vc Hijacker påvirker Chrome, Firefox, og IE
Ved installation af filerne, brugeren installerer den særlige app, men får også sin browser kapret med bing(.)vc. Kapreren er skjult inde i en fil, der er identificeret som IconOverlayEx(.)etc..
En gang i et system, flykapreren installerer sig selv i Chrome, Firefox, og IE, og ændrer browserens hjemmeside. Derudover, annoncer injiceres på alle websteder, brugeren besøger.
Trods navnet, siden, bing(.)vc har ikke noget at gøre med Microsofts Bing -søgemaskine. Forskere påpeger, at det er underligt, at Microsoft ikke har gjort noget for at tage domænet ned. Den mest nysgerrige del af denne nye kampagne, dog, er, at det omdirigerer brugere til en side, der sælger et meget dyrt værktøj til at reparere offerets browser.
Kan Bing(.)vc fjernes?
Desværre, brugere har delt negative oplevelser i deres forsøg på at rense deres browsere og systemer. Selvom de med succes har fjernet driverværktøjet, der bragte flykapreren, flykapreren selv vedvarer. En fil, der er tilbage efter afinstallationen af appen, er faktisk IconOverlayEx(.)etc..
Endvidere, Bing(.) ville også ændre offerets registreringsdatabase ved at tilføje to nye poster for at indlæse DLL'en ved hver genstart af systemet:
- HKLM SOFTWARE Microsoft Windows CurrentVersion Explorer ShellIconOverlayIdentifiers IconOverlayEx : "{E1773C0E-364D-4210-B831-72F5A359E88F}"
- HKLMSOFTWAREMicrosoftWindowsCurrentVersionShell ExtensionsApproved{E1773C0E-364D-4210-B831-72F5A359E88F}: "Ikonoverlay Shell -udvidelse"
Den eneste måde at fjerne den ondsindede fil er ved manuelt at fjerne ovenstående registreringsnøgler, eller, hvis brugeren er uerfaren, køre et automatisk værktøj, der tilbyder denne service. Udover at gøre det, brugere skal gøre som vist på billedet herunder - de berørte browsers genveje skal rettes ved at slette webadressen i slutningen af appmålparameteren.
Også, sørg for at lære det grundlæggende at kende pay-per-install affilieret virksomhed ansvarlig for mange af de medfølgende downloads, der i øjeblikket spreder malware og adware.
Spy Hunter scanner kun detektere trussel. Hvis du ønsker, at truslen skal fjernes automatisk, du nødt til at købe den fulde version af anti-malware værktøj.Læs mere om SpyHunter Anti-Malware værktøj / Sådan fjernes SpyHunter
- Vinduer
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop push-pop op-vinduer
Sådan fjernes fra Windows.
Trin 1: Scan efter med SpyHunter Anti-Malware værktøj



Trin 2: Start din pc i fejlsikret tilstand





Trin 3: Afinstaller og tilhørende software fra Windows
Her er en metode i nogle få nemme trin, der bør være i stand til at afinstallere de fleste programmer. Uanset om du bruger Windows 10, 8, 7, Vista eller XP, disse skridt vil få arbejdet gjort. At trække det program eller dets mappe til papirkurven kan være en meget dårlig beslutning. Hvis du gør det, stumper og stykker af programmet er efterladt, og det kan føre til ustabile arbejde på din PC, fejl med filtypen foreninger og andre ubehagelige aktiviteter. Den rigtige måde at få et program fra din computer er at afinstallere det. For at gøre dette:


 Følg anvisningerne ovenfor, og du vil afinstallere de fleste programmer.
Følg anvisningerne ovenfor, og du vil afinstallere de fleste programmer.
Trin 4: Rens eventuelle registre, Oprettet af på din pc.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, skabt af der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Videofjernelsesvejledning til (Vinduer).
Slip af med Mac OS X.
Trin 1: Afinstaller og fjerne relaterede filer og objekter
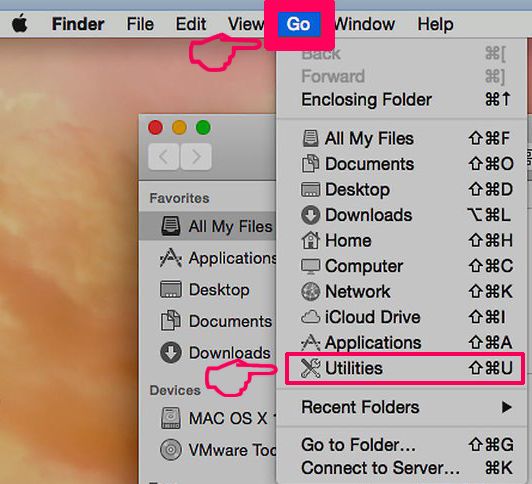
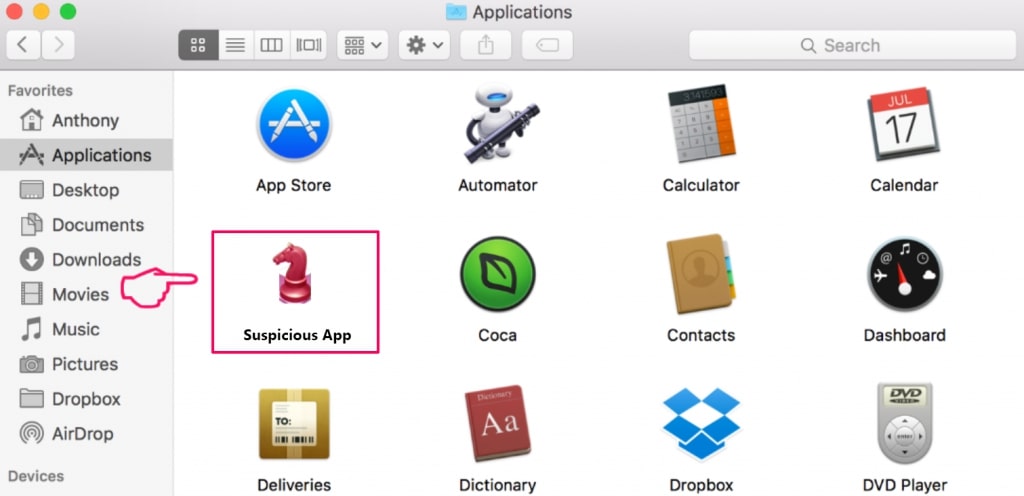
Din Mac vil så vise dig en liste over emner, starte automatisk når du logger ind. Kig efter eventuelle mistænkelige apps identiske med eller ligner . Tjek den app, du ønsker at stoppe i at køre automatisk, og vælg derefter på Minus ("-") ikonet for at skjule det.
- Gå til Finder.
- I søgefeltet skriv navnet på den app, du vil fjerne.
- Over søgefeltet ændre to rullemenuerne til "System Files" og "Er Inkluderet" så du kan se alle de filer, der er forbundet med det program, du vil fjerne. Husk på, at nogle af filerne kan ikke være relateret til den app, så være meget forsigtig, hvilke filer du sletter.
- Hvis alle filerne er relateret, hold ⌘ + A knapperne til at vælge dem og derefter køre dem til "Affald".
I tilfælde af at du ikke fjerne via Trin 1 over:
I tilfælde af at du ikke finde virus filer og objekter i dine programmer eller andre steder, vi har vist ovenfor, kan du manuelt søge efter dem i bibliotekerne i din Mac. Men før du gør dette, læs den fulde ansvarsfraskrivelse nedenfor:
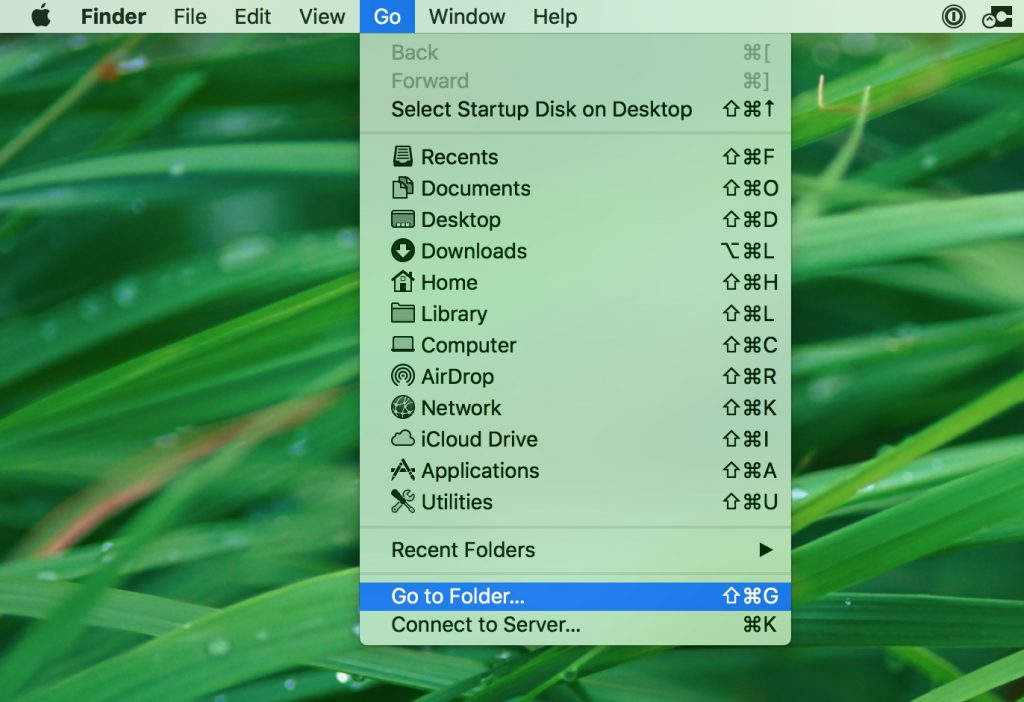
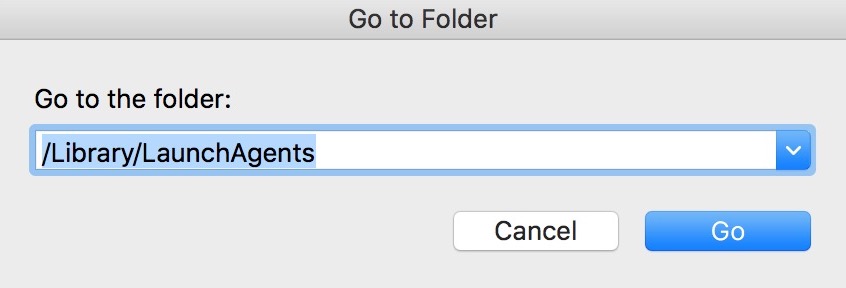
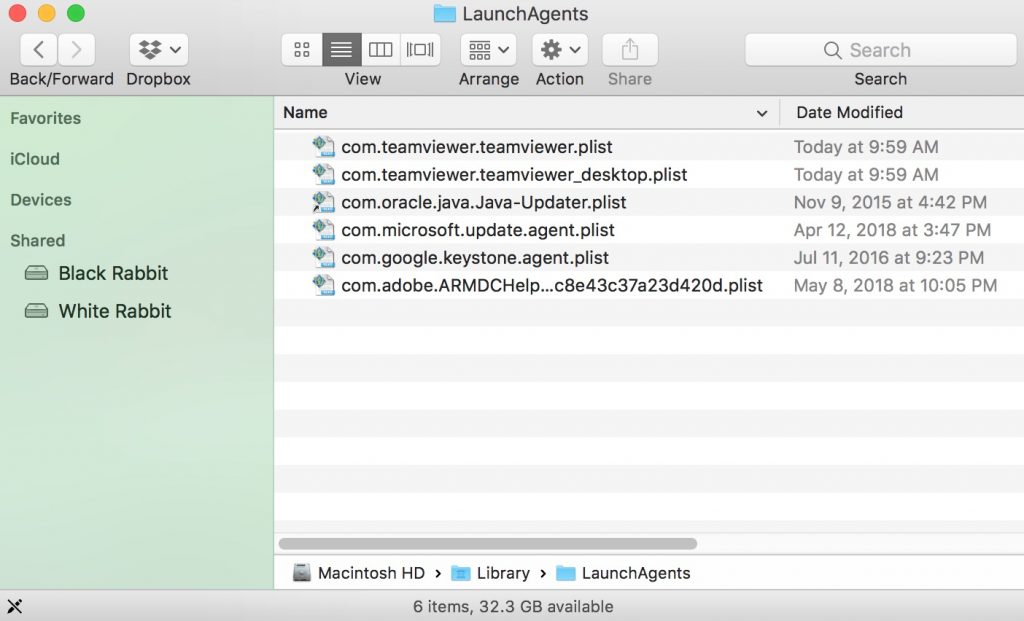
Du kan gentage den samme procedure med den følgende anden Bibliotek mapper:
→ ~ / Library / LaunchAgents
/Bibliotek / LaunchDaemons
Tip: ~ er der med vilje, fordi det fører til flere LaunchAgents.
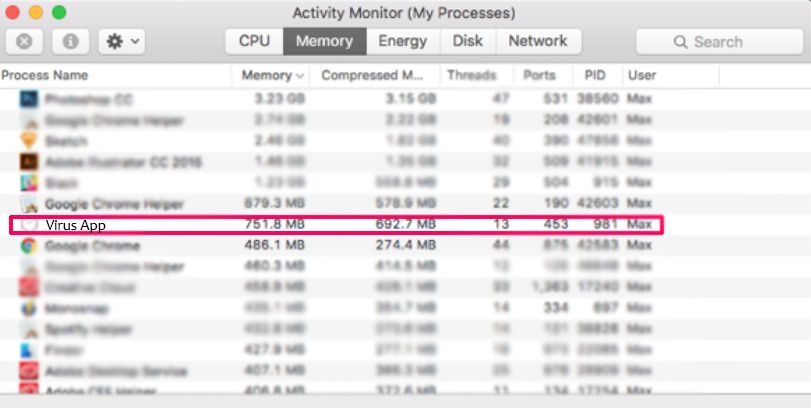
Trin 2: Scan efter og fjern filer fra din Mac
Når du står over for problemer på din Mac som følge af uønskede scripts og programmer såsom , den anbefalede måde at eliminere truslen er ved hjælp af en anti-malware program. SpyHunter til Mac tilbyder avancerede sikkerhedsfunktioner sammen med andre moduler, der forbedrer din Mac's sikkerhed og beskytter den i fremtiden.
Videofjernelsesvejledning til (Mac)
Fjern fra Google Chrome.
Trin 1: Start Google Chrome, og åbn dropmenuen
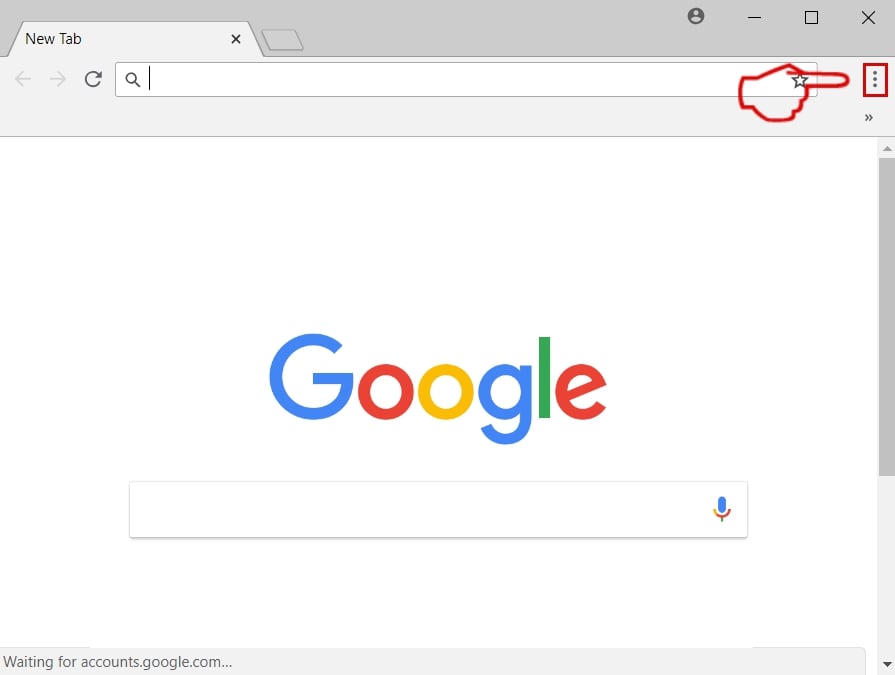
Trin 2: Flyt markøren hen over "Værktøj" og derefter fra den udvidede menu vælge "Udvidelser"
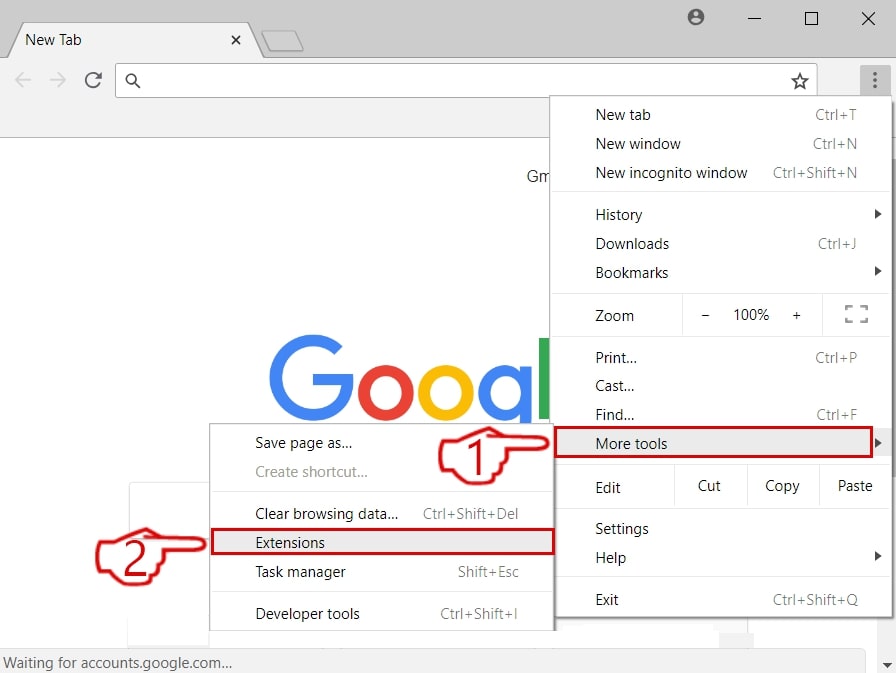
Trin 3: Fra den åbnede "Udvidelser" Menuen lokalisere den uønskede udvidelse og klik på dens "Fjerne" knap.
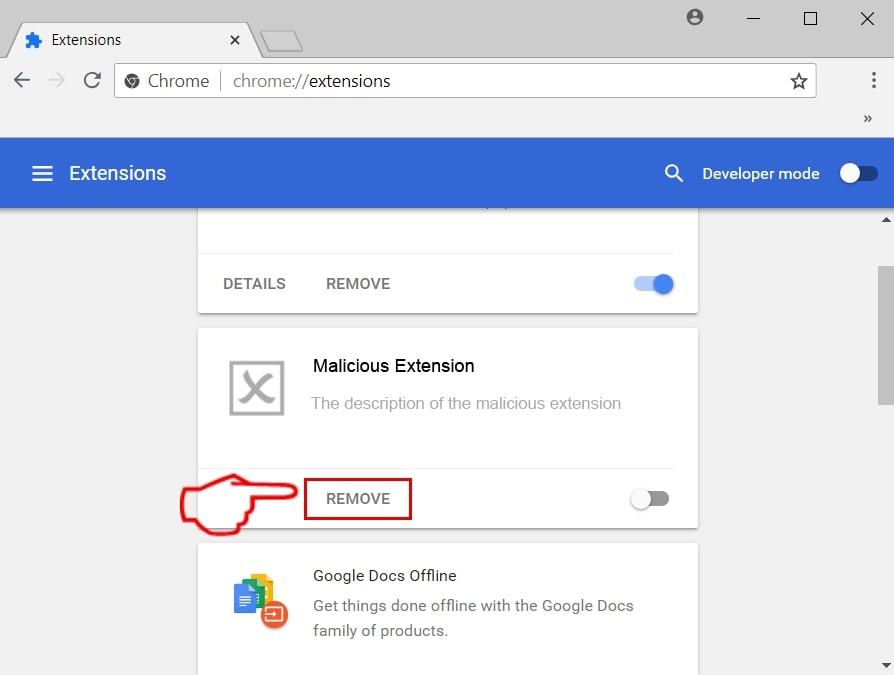
Trin 4: Efter udvidelsen er fjernet, genstarte Google Chrome ved at lukke det fra den røde "X" knappen i øverste højre hjørne, og starte den igen.
Slet fra Mozilla Firefox.
Trin 1: Start Mozilla Firefox. Åbn menuen vindue:
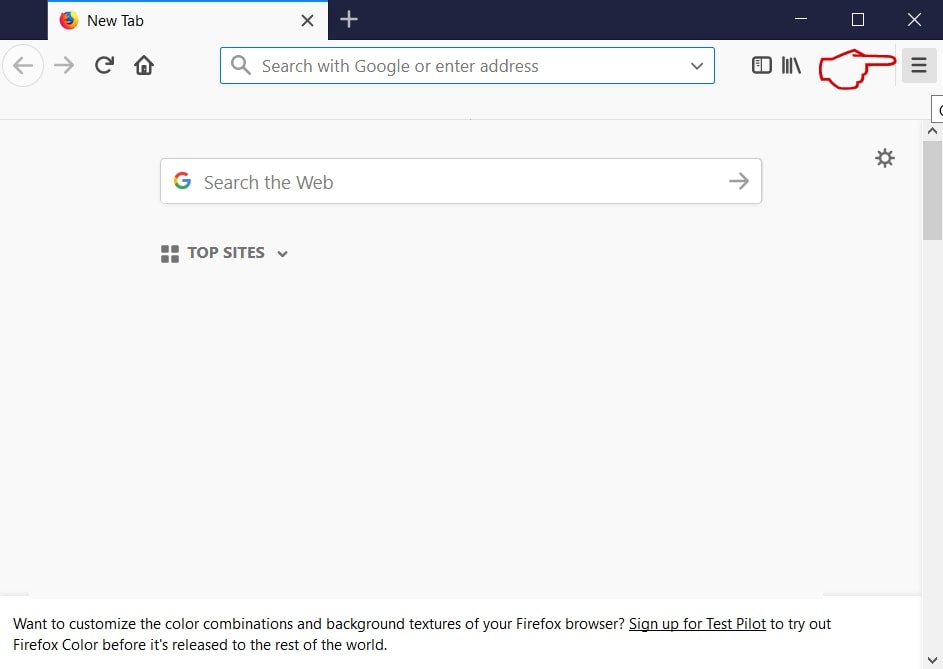
Trin 2: Vælg "Add-ons" ikon fra menuen.
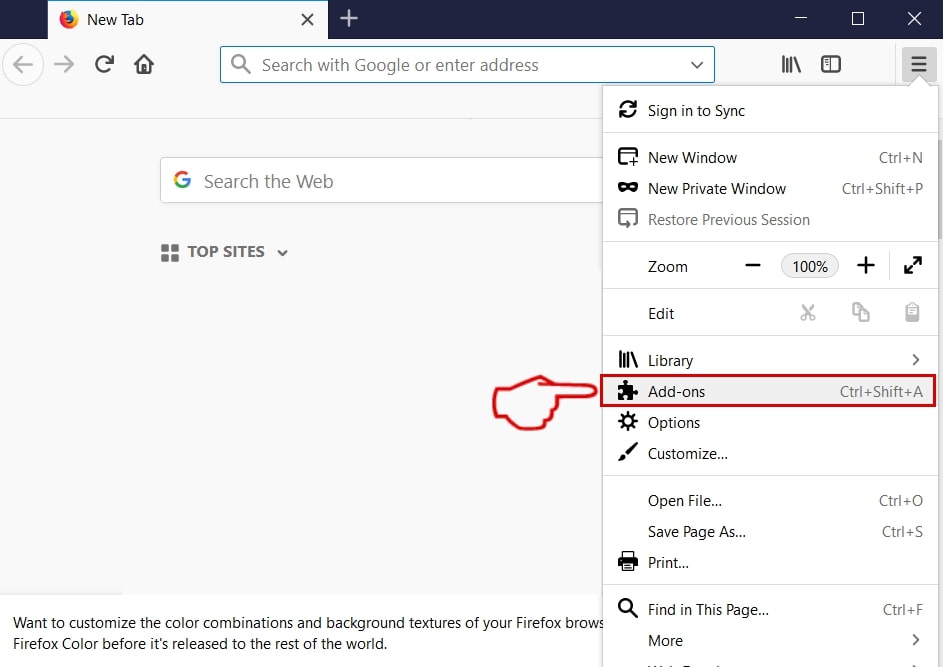
Trin 3: Vælg den uønskede udvidelse og klik "Fjerne"

Trin 4: Efter udvidelsen er fjernet, genstarte Mozilla Firefox ved at lukke det fra den røde "X" knappen i øverste højre hjørne, og starte den igen.
Afinstaller fra Microsoft Edge.
Trin 1: Start Edge-browser.
Trin 2: Åbn drop-menuen ved at klikke på ikonet i øverste højre hjørne.
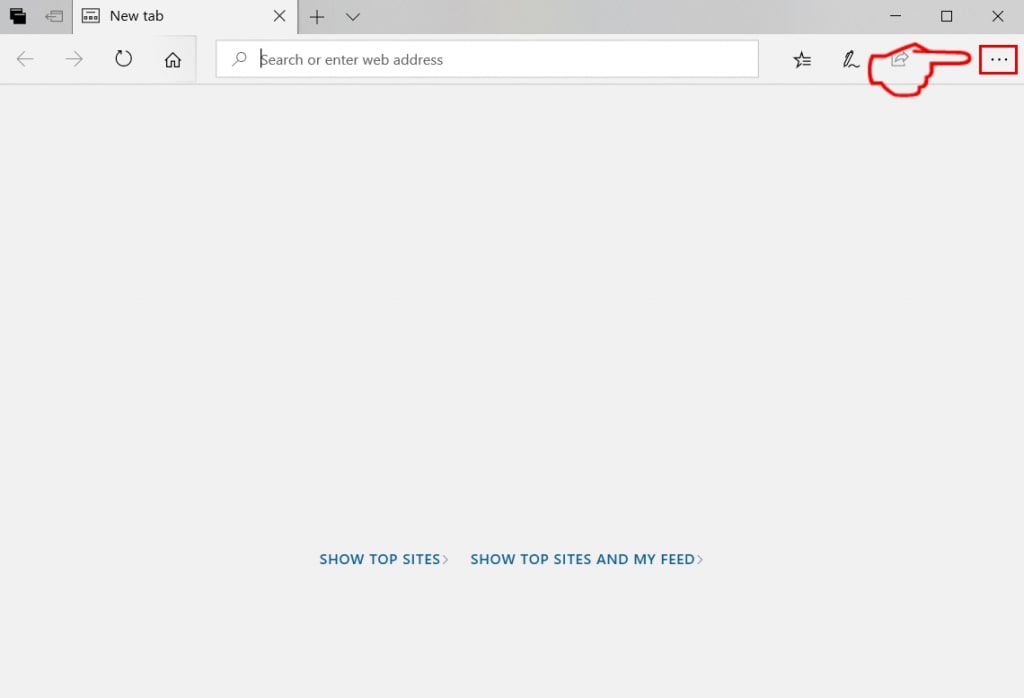
Trin 3: Fra drop-menuen vælg "Udvidelser".
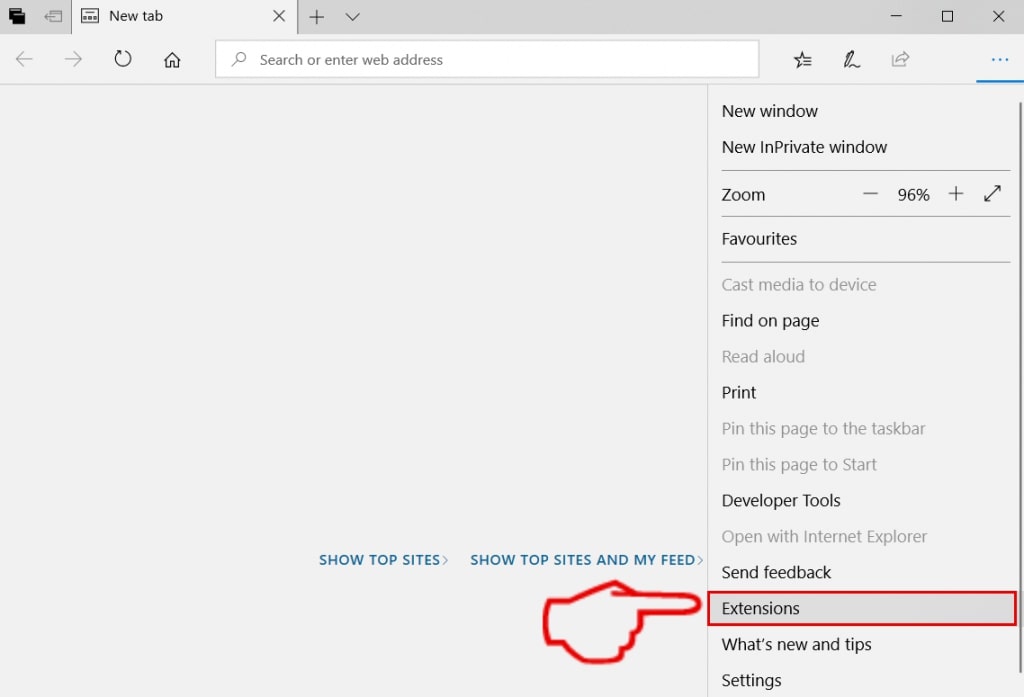
Trin 4: Vælg den formodede ondsindede udvidelse, du vil fjerne, og klik derefter på tandhjulsikonet.
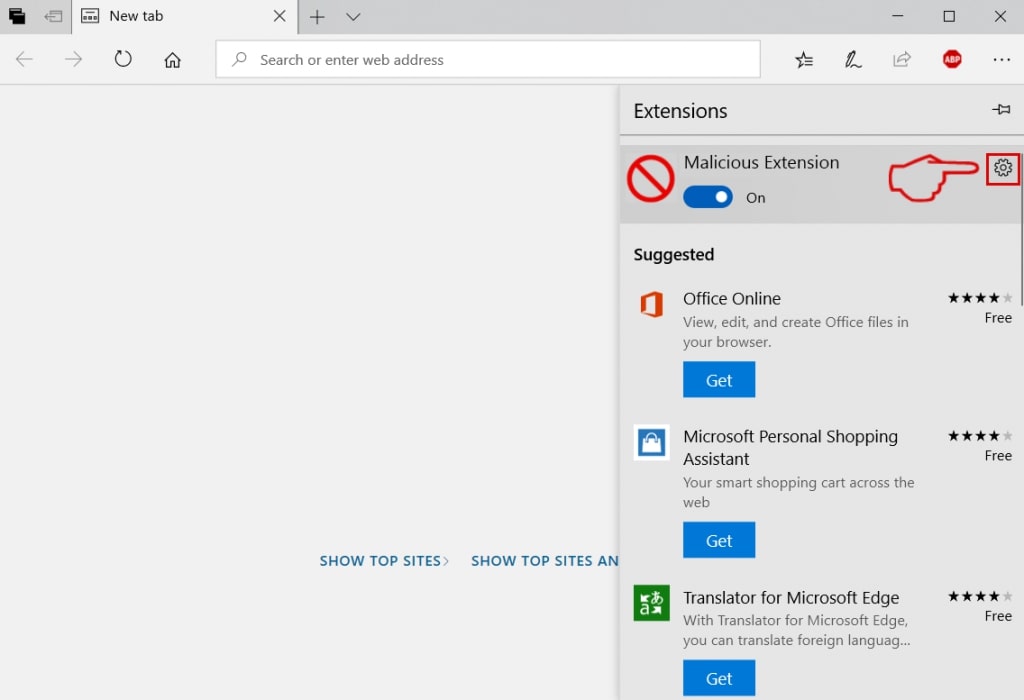
Trin 5: Fjern den ondsindede udvidelse ved at rulle ned og derefter klikke på Afinstaller.
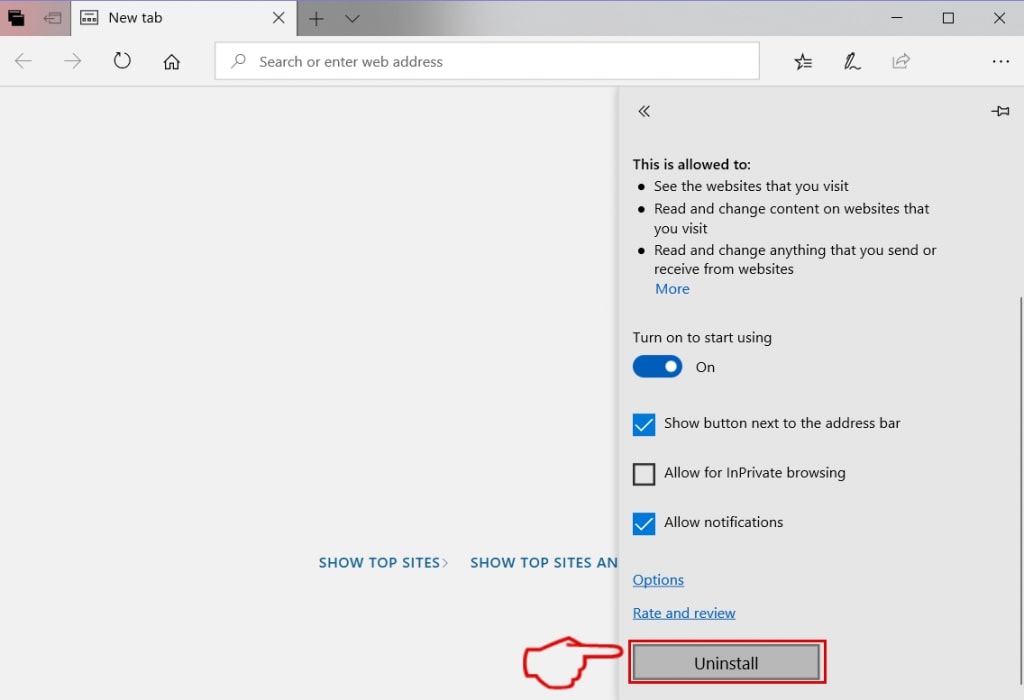
Fjern fra Safari
Trin 1: Start Safari-appen.
Trin 2: Efter at holde musen markøren til toppen af skærmen, klik på Safari-teksten for at åbne dens rullemenu.
Trin 3: Fra menuen, Klik på "Indstillinger".
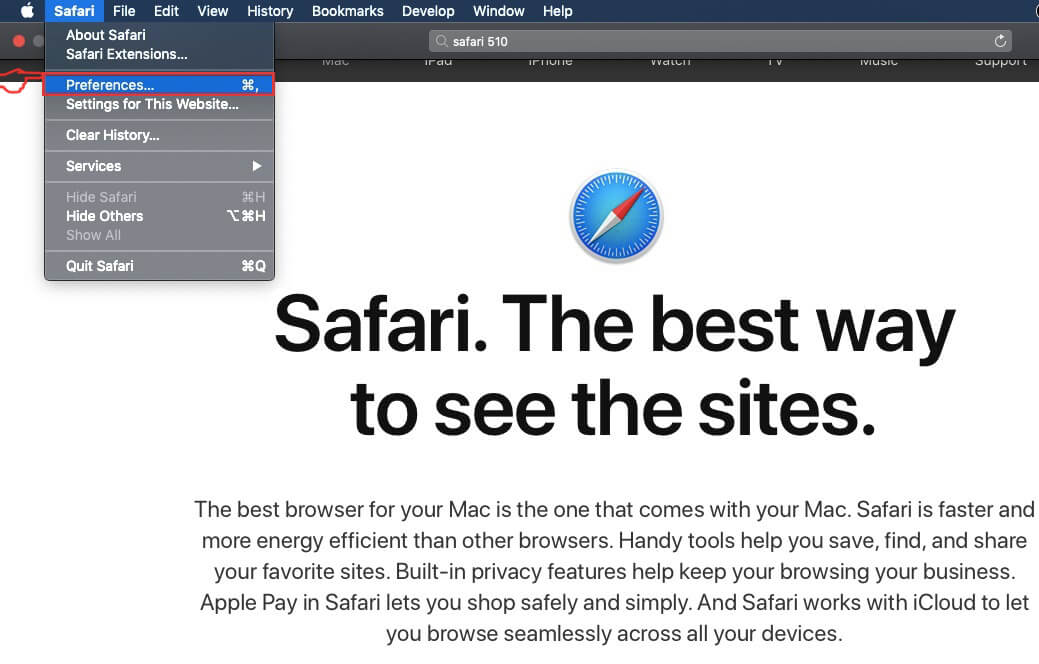
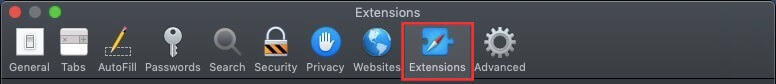
Trin 4: Efter at, vælg fanen 'Udvidelser'.
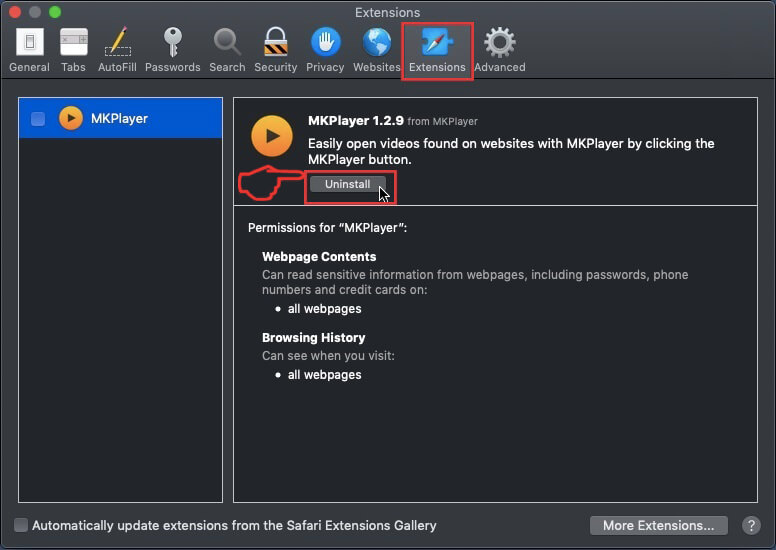
Trin 5: Klik én gang på udvidelse, du vil fjerne.
Trin 6: Klik på 'Afinstaller'.
Et pop-up vindue vises beder om bekræftelse til at afinstallere forlængelsen. Vælg 'Fjern' igen, og vil blive fjernet.
Fjern fra Internet Explorer.
Trin 1: Start Internet Explorer.
Trin 2: Klik på tandhjulsikonet mærket 'Værktøjer' for at åbne drop-menuen og vælg 'Administrer tilføjelser'
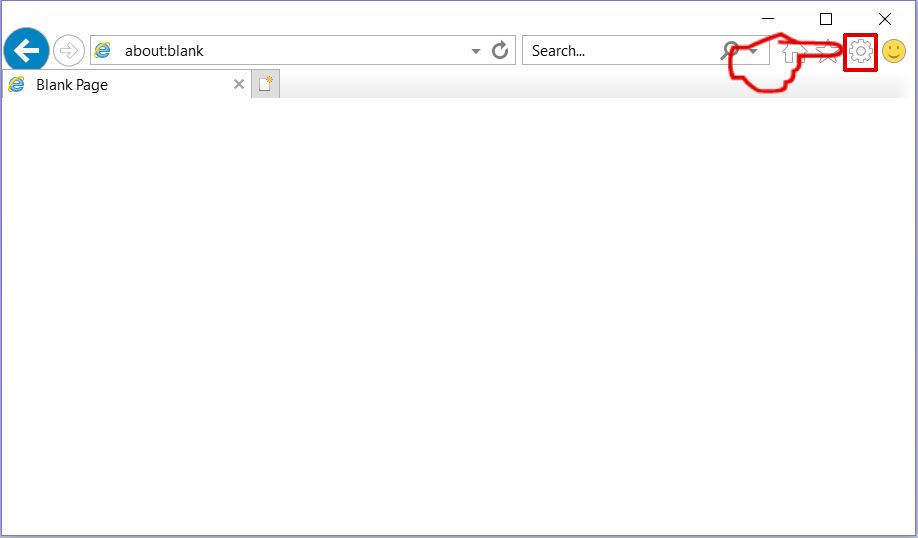
Trin 3: I vinduet 'Administrer tilføjelser'.
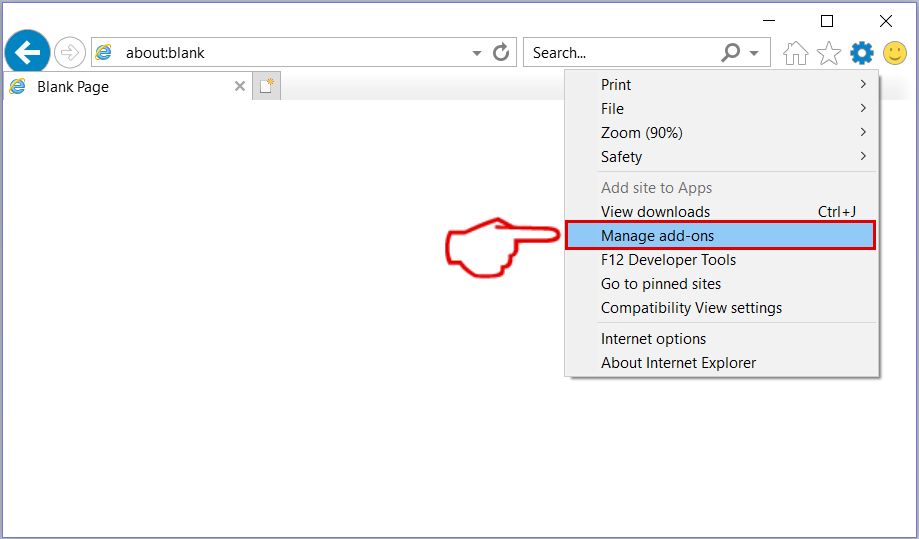
Trin 4: Vælg den udvidelse, du vil fjerne, og klik derefter på 'Deaktiver'. Et pop-up vindue vises for at informere dig om, at du er ved at deaktivere den valgte udvidelse, og nogle flere tilføjelser kan være deaktiveret så godt. Lad alle boksene kontrolleret, og klik på 'Deaktiver'.
Trin 5: Efter den uønskede udvidelse er blevet fjernet, genstart Internet Explorer ved at lukke den fra den røde 'X'-knap i øverste højre hjørne, og start den igen.
Fjern push-meddelelser fra dine browsere
Sluk for push-meddelelser fra Google Chrome
Sådan deaktiveres push-meddelelser fra Google Chrome-browseren, Følg nedenstående trin:
Trin 1: Gå til Indstillinger i Chrome.
Trin 2: I Indstillinger, Vælg "Avancerede indstillinger":
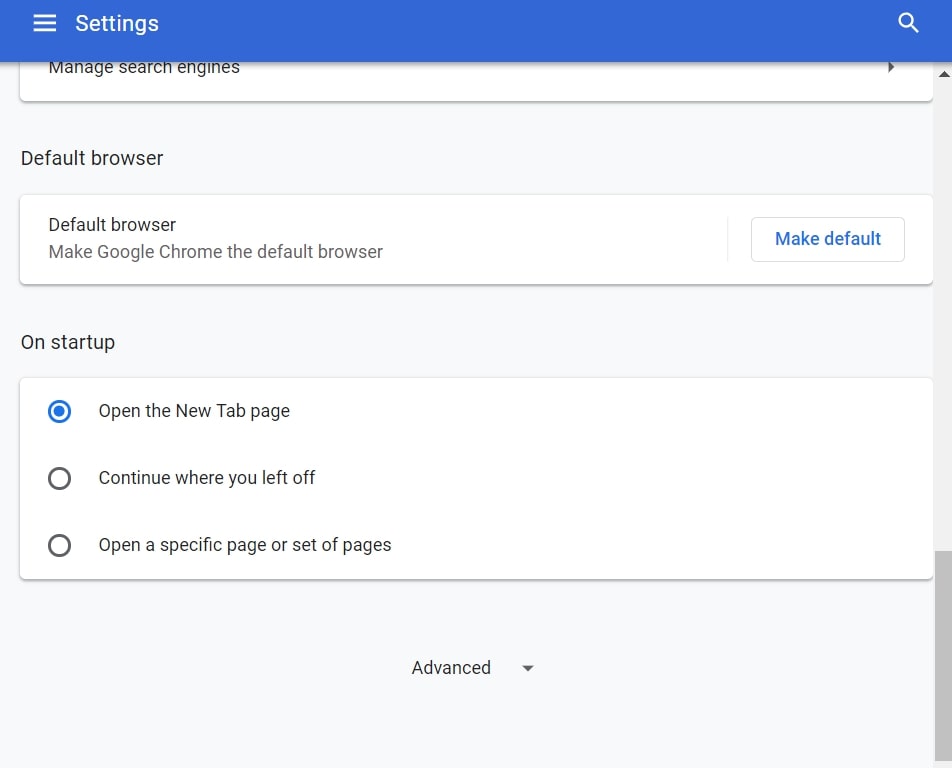
Trin 3: Klik på “Indstillinger for indhold":
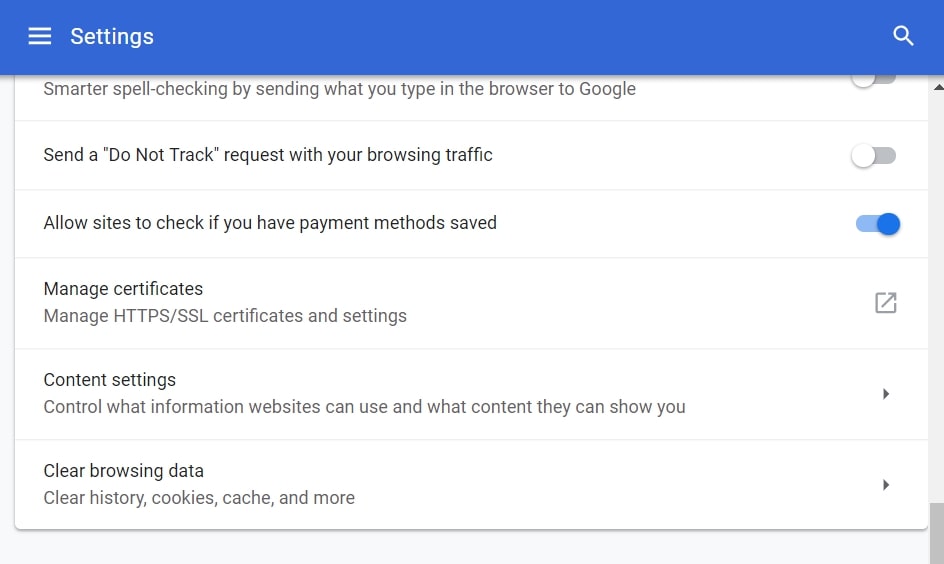
Trin 4: Åbn “underretninger":
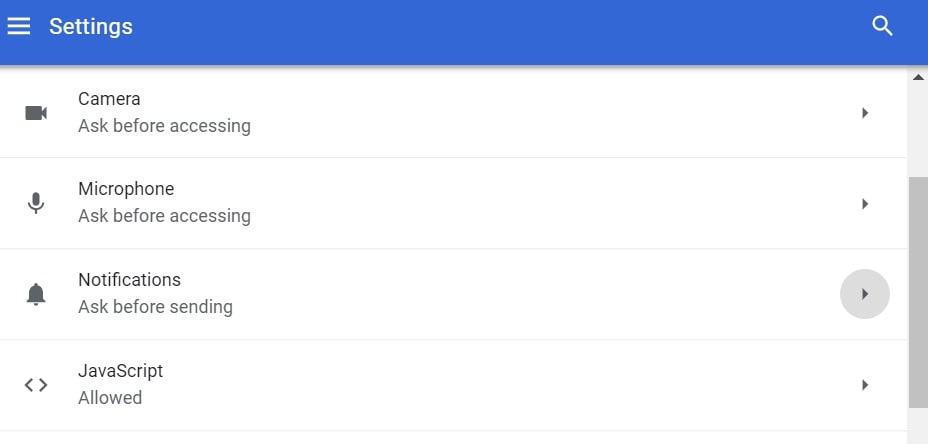
Trin 5: Klik på de tre prikker, og vælg Bloker, Rediger eller fjern muligheder:

Fjern Push Notifications på Firefox
Trin 1: Gå til Firefox-indstillinger.
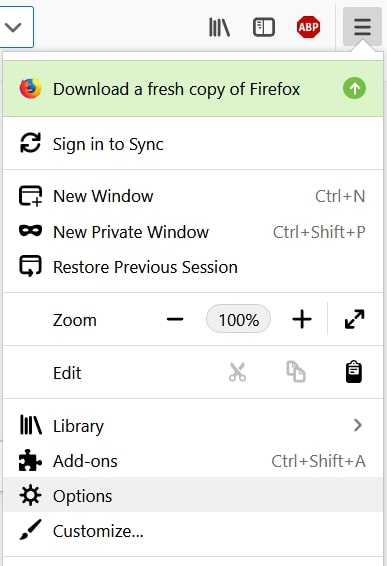
Trin 2: Gå til "Indstillinger", skriv "notifikationer" i søgefeltet, og klik "Indstillinger":
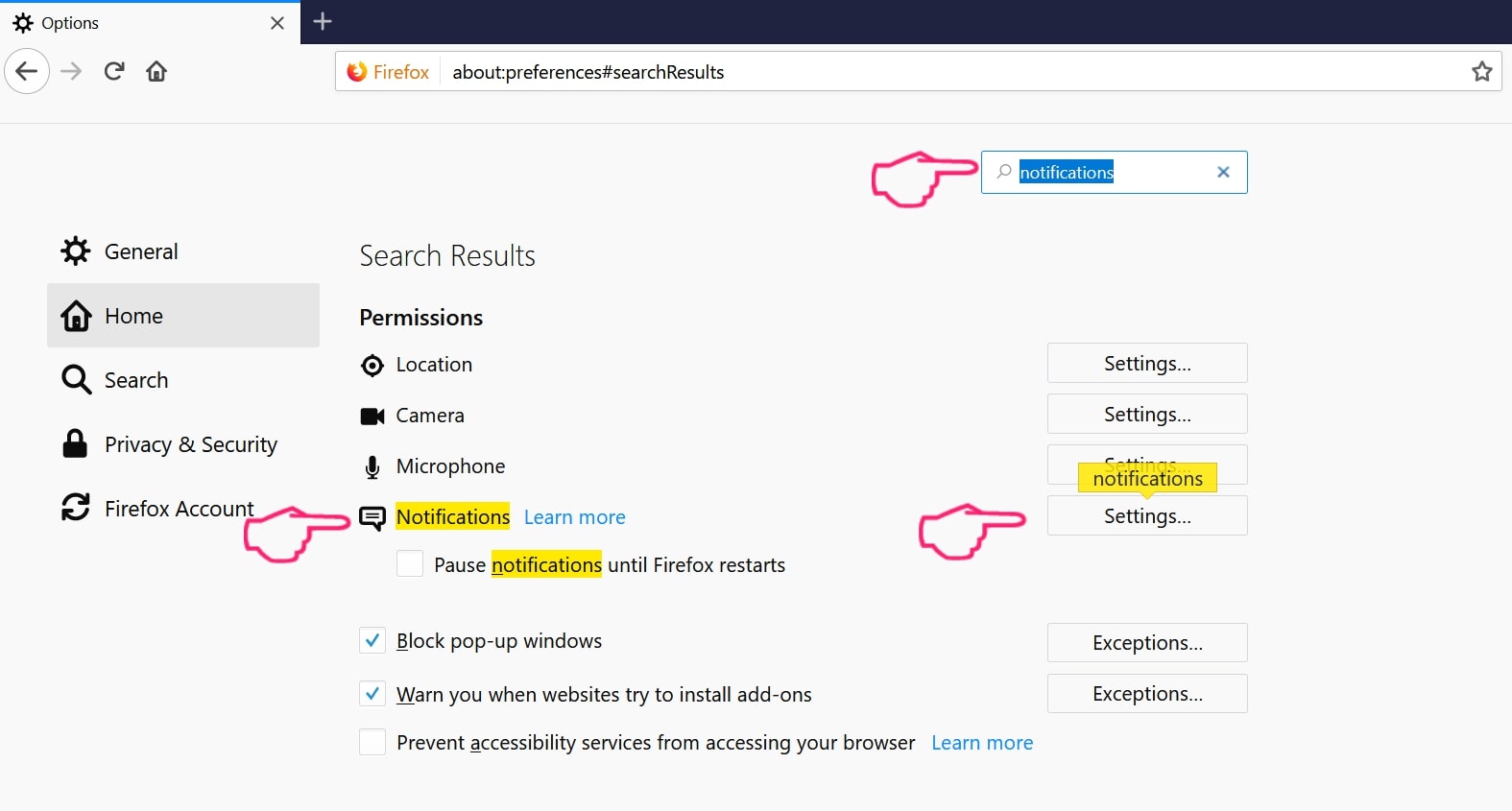
Trin 3: Klik på "Fjern" på ethvert websted, hvor du ønsker, at meddelelser er væk, og klik på "Gem ændringer"
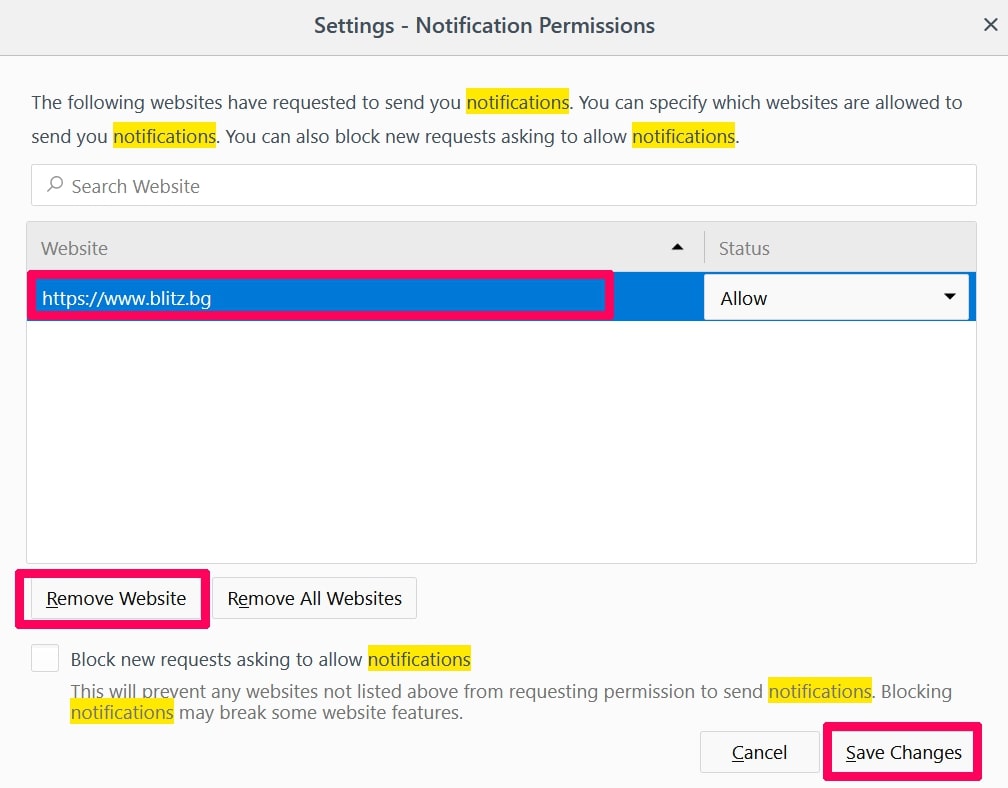
Stop push-meddelelser på Opera
Trin 1: I opera, presse ALT+P for at gå til Indstillinger.
Trin 2: I Indstilling af søgning, skriv "Indhold" for at gå til Indholdsindstillinger.
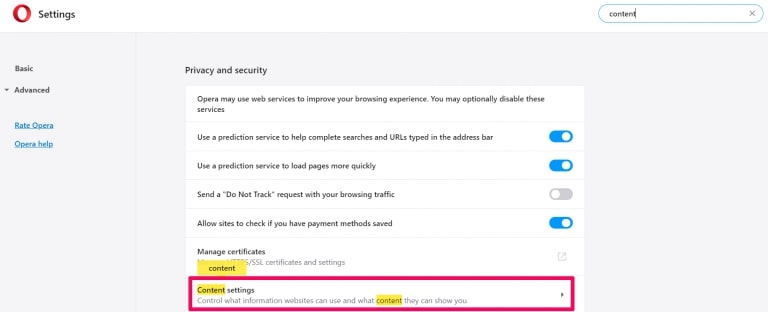
Trin 3: Åbn underretninger:
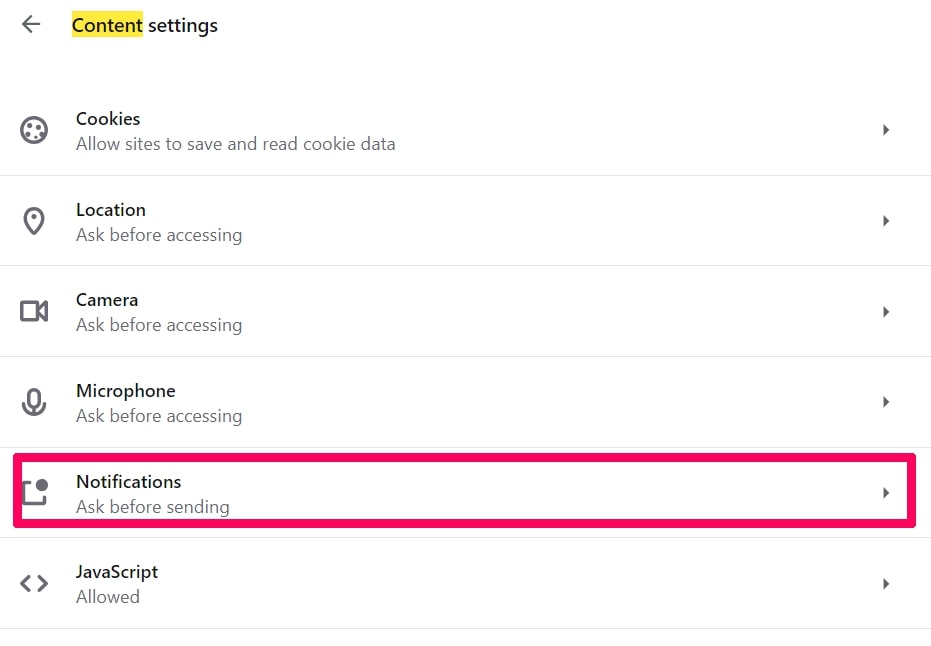
Trin 4: Gør det samme som du gjorde med Google Chrome (forklaret nedenfor):
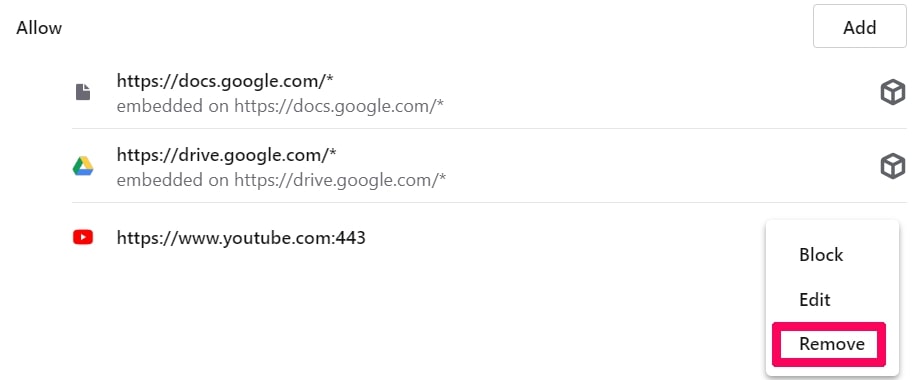
Fjern Push-underretninger på Safari
Trin 1: Åbn Safari-indstillinger.
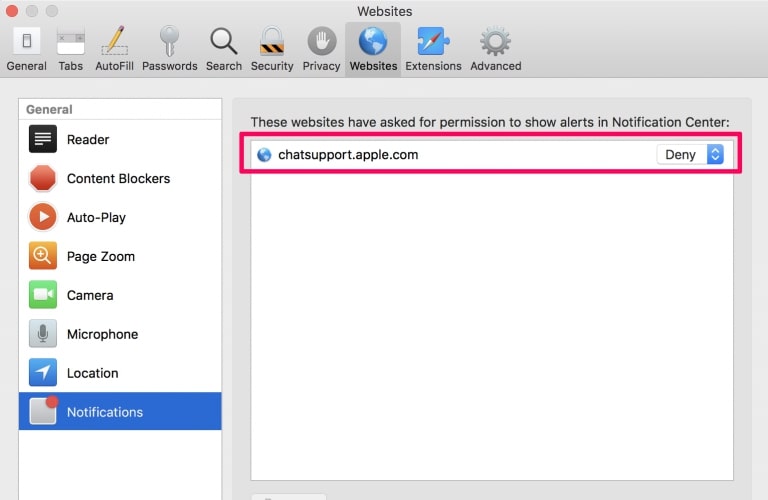
Trin 2: Vælg det domæne, hvorfra du kan lide pop-op-pop op, og skift til "Nægte" fra "Give lov til".
-FAQ
Hvad er ?
Truslen er adware eller browser omdirigering virus.
Det kan gøre din computer langsommere og vise reklamer. Hovedideen er, at dine oplysninger sandsynligvis bliver stjålet, eller at der vises flere annoncer på din enhed.
Skaberne af sådanne uønskede apps arbejder med ordninger for betaling pr. Klik for at få din computer til at besøge risikable eller forskellige typer websteder, der kan generere dem midler. Dette er grunden til, at de ikke engang er ligeglade med, hvilke typer websteder der vises på annoncerne. Dette gør deres uønskede software indirekte risikabelt for dit operativsystem.
Hvad er symptomerne på ?
Der er flere symptomer at se efter, når denne særlige trussel og også uønskede apps generelt er aktive:
Symptom #1: Din computer kan blive langsom og generelt have dårlig ydeevne.
Symptom #2: Du har værktøjslinjer, tilføjelser eller udvidelser på dine webbrowsere, som du ikke kan huske at have tilføjet.
Symptom #3: Du ser alle typer annoncer, som annoncesupporterede søgeresultater, pop op-vinduer og omdirigeringer vises tilfældigt.
Symptom #4: Du ser installerede apps på din Mac køre automatisk, og du kan ikke huske at have installeret dem.
Symptom #5: Du ser mistænkelige processer køre i din Jobliste.
Hvis du ser et eller flere af disse symptomer, så anbefaler sikkerhedseksperter, at du tjekker din computer for virus.
Hvilke typer uønskede programmer findes der?
Ifølge de fleste malware-forskere og cybersikkerhedseksperter, de trusler, der i øjeblikket kan påvirke din enhed, kan være useriøs antivirus-software, adware, browser hijackers, klikkere, falske optimizere og enhver form for PUP'er.
Hvad skal jeg gøre, hvis jeg har en "virus" lignende ?
Med få enkle handlinger. Først og fremmest, det er bydende nødvendigt, at du følger disse trin:
Trin 1: Find en sikker computer og tilslut det til et andet netværk, ikke den, som din Mac blev inficeret i.
Trin 2: Skift alle dine passwords, fra dine e-mail-adgangskoder.
Trin 3: Aktiver to-faktor-autentificering til beskyttelse af dine vigtige konti.
Trin 4: Ring til din bank til ændre dine kreditkortoplysninger (hemmelig kode, etc.) hvis du har gemt dit kreditkort til nethandel eller har lavet online aktiviteter med dit kort.
Trin 5: Sørg for at ring til din internetudbyder (Internetudbyder eller operatør) og bed dem om at ændre din IP-adresse.
Trin 6: Skift din Wi-Fi-adgangskode.
Trin 7: (Valgfri): Sørg for at scanne alle enheder, der er tilsluttet dit netværk for vira, og gentag disse trin for dem, hvis de er berørt.
Trin 8: Installer anti-malware software med realtidsbeskyttelse på alle enheder, du har.
Trin 9: Prøv ikke at downloade software fra websteder, du ikke ved noget om, og hold dig væk fra websteder med lav omdømme i almindelighed.
Hvis du følger disse anbefalinger, dit netværk og alle enheder bliver betydeligt mere sikre mod enhver trussel eller informationsinvasiv software og også være virusfri og beskyttet i fremtiden.
Hvordan virker?
Når det er installeret, kan indsamle data ved brug af trackere. Disse data handler om dine web-browsing-vaner, såsom de websteder, du besøger, og de søgetermer, du bruger. Det bruges derefter til at målrette dig med annoncer eller til at sælge dine oplysninger til tredjeparter.
kan også download anden skadelig software til din computer, såsom virus og spyware, som kan bruges til at stjæle dine personlige oplysninger og vise risikable annoncer, der kan omdirigere til virussider eller svindel.
Er Malware?
Sandheden er, at PUP'er (adware, browser hijackers) er ikke vira, men kan være lige så farligt da de muligvis viser dig og omdirigerer dig til malware-websteder og svindelsider.
Mange sikkerhedseksperter klassificerer potentielt uønskede programmer som malware. Dette er på grund af de uønskede virkninger, som PUP'er kan forårsage, såsom at vise påtrængende annoncer og indsamle brugerdata uden brugerens viden eller samtykke.
Om forskningen
Indholdet udgiver vi på SensorsTechForum.com, denne vejledning til fjernelse medfølger, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed for at hjælpe dig med at fjerne det specifikke, adware-relateret problem, og gendan din browser og computersystem.
Hvordan foretog vi undersøgelsen vedr ?
Bemærk venligst, at vores forskning er baseret på uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om den seneste malware, adware, og browser hijacker definitioner.
Endvidere, forskningen bag truslen bakkes op med VirusTotal.
For bedre at forstå denne online trussel, Se venligst følgende artikler, som giver kyndige detaljer.














