Ikke kun din personlige computer og smartphone er tilbøjelige til ransomware -angreb. TrendMicro -forskere afslørede netop, at dit Android TV også er udsat for risikoen for at blive låst og blive ubrugelig, indtil der er betalt en løsesum.
truslen, kaldet FLocker (oprindeligt opdaget som ANDROIDOS_FLOCKER.A og forkortelse for Frantic Locker) har eksisteret siden maj 2015. Men, en version af flere tusinde varianter er nu blevet opdateret til at angribe smart -tv.
Mere Android Malware at holde sig væk fra
Hvordan inficerer FLockers Android Smart TV -version enheder?
TrendMicros forskning angiver ikke ligefrem, hvordan et smart -tv ville blive angrebet. Men, det er meget sandsynligt, at angrebet udløses af SMS eller ondsindede links.
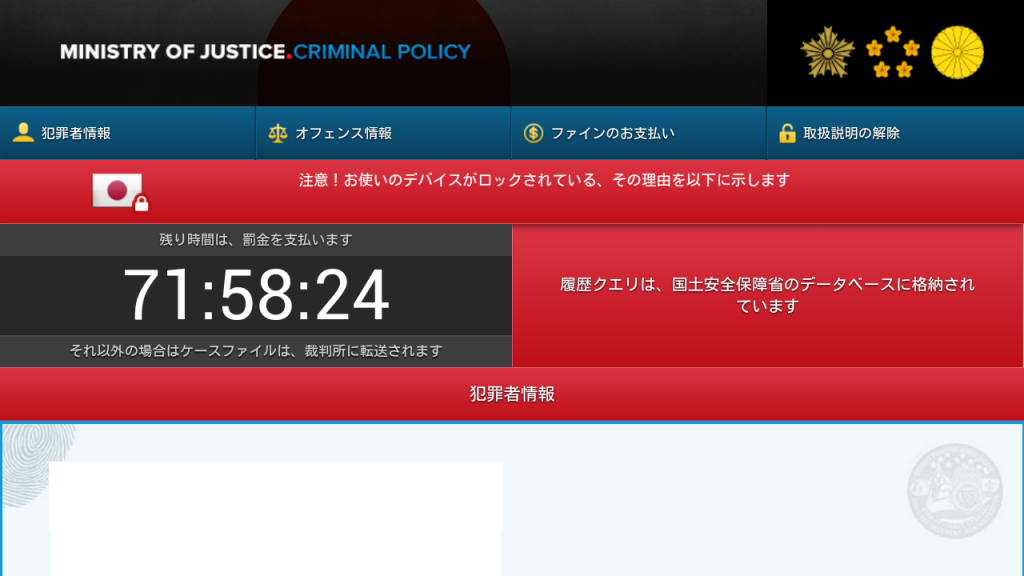
Som med andre skærmskabe, FLocker låser skærmen på den målrettede enhed og viser en løsesummeddelelse skrevet på det lokale sprog. Beskeden ville være fra US Cyber Police eller en anden lignende institution.
Den ransomware, som FLocker efterspørger, findes ikke i Bitcoins, men i… iTunes -gavekort. Ransomware -operatørerne ønsker at modtage $200 i gavekort for at låse enheden op. Faktisk, ransomware's handlinger matcher smartphoneskabe.
En underlig kendsgerning er, at truslen ikke vil angribe enheder, der er placeret i nogen af disse lande: Kasakhstan, Aserbajdsjan, Bulgarien, Georgien, Ungarn, Ukraine, Rusland, Armenien, og Hviderusland. Desuden, hvis FLocker bliver installeret på en enhed i nogen af disse regioner, den vil “stå stille” for 30 minutter og vil derefter anmode om enhedsadministratorrettigheder. Hvis anmodningen afvises, truslen viser en falsk systemopdateringsskærm.
Selvom FLocker låser skærmen på enhederne, det vil ikke kryptere nogen filer. Ikke desto mindre, det vil høste oplysninger fra (og om) enheden.
Sådan fjernes FLocker fra berørte enheder
Teknisk kyndige brugere kan afinstallere ransomware, men ikke før de fjerner dens enhedsadministratorrettigheder.
TrendMicros råd:
Vi foreslår, at brugeren først kontakter enhedssælgeren for at få en løsning, hvis deres Android TV bliver inficeret. En anden måde at fjerne malware på er mulig, hvis brugeren kan aktivere ADB -fejlfinding. Brugere kan forbinde deres enhed med en pc og starte ADB -skallen og udføre kommandoen "PM clear %pkg %". Dette dræber ransomware -processen og låser skærmen op. Brugere kan derefter deaktivere den enhedsadministratorrettighed, der er givet til applikationen, og afinstallere appen.


