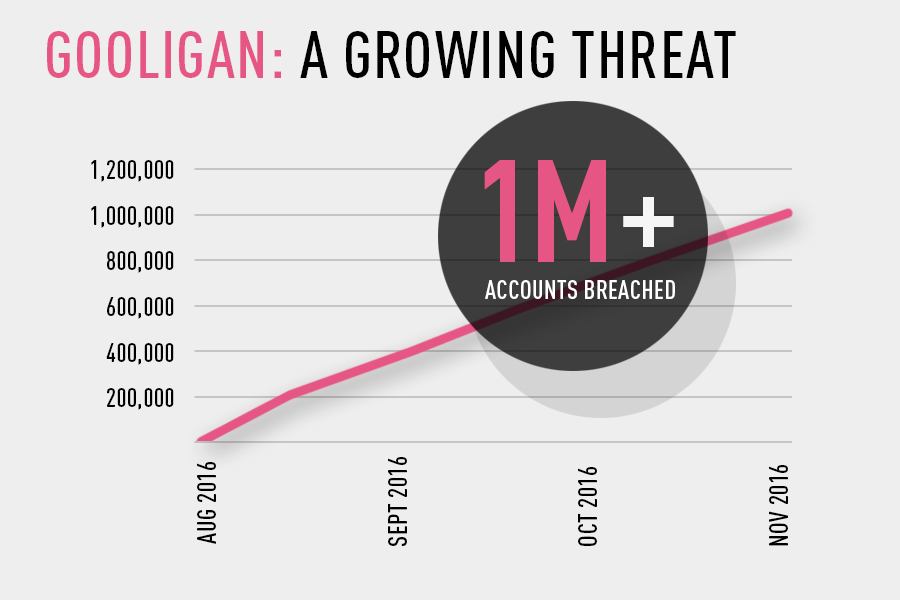
En ny meget farlig ondsindet kampagne blev lige opdaget af forskere ved Check Point. Angrebet kampagne er døbt Gooligan, og det lykkedes at bryde sikkerheden på mere end en million Google-konti. Forskere siger, at dette enorme antal fortsætter med at vokse hver dag, med 13,000 brudte enheder på daglig basis.
Relaterede: Ny Android Malware Mål 15 tyske banker
Malwaren rødder inficerede enheder og stjæler godkendelsestokener. Disse tokens kan bruges til at få adgang til data fra Google Play, Gmail, Google Fotos, Google Docs, G-suite, Google Drev, etc. Dette er faktisk den samme malware, der blev opdaget sidste år i SnapPea -appen. Check Point -teamet har allerede kontaktet Google med deres resultater. Kæmpen investerer i øjeblikket Gooligan.
Adrian Ludwig fra Google har allerede frigivet en erklæring, sige, at:
Flere Ghost Push -varianter bruger offentligt kendte sårbarheder, der ikke er opdateret på ældre enheder, for at opnå privilegier, der giver dem mulighed for at installere applikationer uden brugerens samtykke. I de sidste par uger, vi har arbejdet tæt sammen med Check Point, et cybersikkerhedsfirma, at undersøge og beskytte brugere mod en af disse varianter. Tilnavnet 'Gooligan', denne variant brugte Googles legitimationsoplysninger på ældre versioner af Android til at generere falske installationer af andre apps. Denne morgen, Check Point detaljerede disse fund på deres blog.
Så synlig, den pågældende malware er faktisk en Ghost Push -variant, der i øjeblikket plager ældre versioner af Android.
Hvem påvirkes af Gooligan?
Ifølge forskning, malware er målrettet mod enheder, der kører Android 4 (Jelly Bean, KitKat) og 5 (Slikkepind). Disse versioner af operativsystemet repræsenterer mindst 74% af nutidens in-market-enheder. 40% af disse enheder findes i Asien og 12% – I Europa. Talrige falske applikationer blev opdaget at have været inficeret med Gooligan. Der kan findes en liste over apps, der muligvis har inficeret brugere med malware her.
Relaterede: Ville du tage en selfie til Acecard Android Trojan?
Hvis du har downloadet nogen af dem, du kan være inficeret. Forskere opfordrer brugere til at gennemgå deres applikationsliste i Indstillinger-Apps for at sikre, at de er sikre ... eller ikke sikre. I tilfælde af infektion, et antivirusprodukt til mobil skal bruges hurtigst muligt.
Endvidere, brugere kan også kontrollere, om deres Google -konti er blevet overtrådt ved at få adgang til en internet side oprettet af sikkerhedsfirmaet til lejligheden.
Hvis en brugers konto er blevet brudt, følge disse trin:
1.En ren installation af et operativsystem på din mobile enhed er påkrævet (en proces kaldet "blinkende"). Da dette er en kompleks proces, Vi anbefaler, at du slukker din enhed og henvender dig til en certificeret tekniker, eller din mobiludbyder, for at anmode om, at din enhed "blinker igen".
2.Skift adgangskoder til din Google -konto umiddelbart efter denne proces.