Den PirateMatryoshka Malware er et farligt våben brugt mod computerbrugere over hele verden. Det inficerer hovedsageligt via The Pirate Bay torrent trackere. Vores artikel giver et overblik over sin adfærd i overensstemmelse med de indsamlede prøver og tilgængelige rapporter, også det kan være nyttigt i forsøget på at fjerne virus.

Trussel Summary
| Navn | PirateMatryoshka Trojan |
| Type | Trojan |
| Kort beskrivelse | PirateMatryoshka Malware er et fidusprogram, der er designet til at infiltrere computersystemer. |
| Symptomer | Ofrene kan ikke opleve nogen synlige symptomer på infektion. |
| Distributionsmetode | Torrent Trackers, Freeware installationer, Bundtede pakker, Scripts og andre. |
| Værktøj Detection |
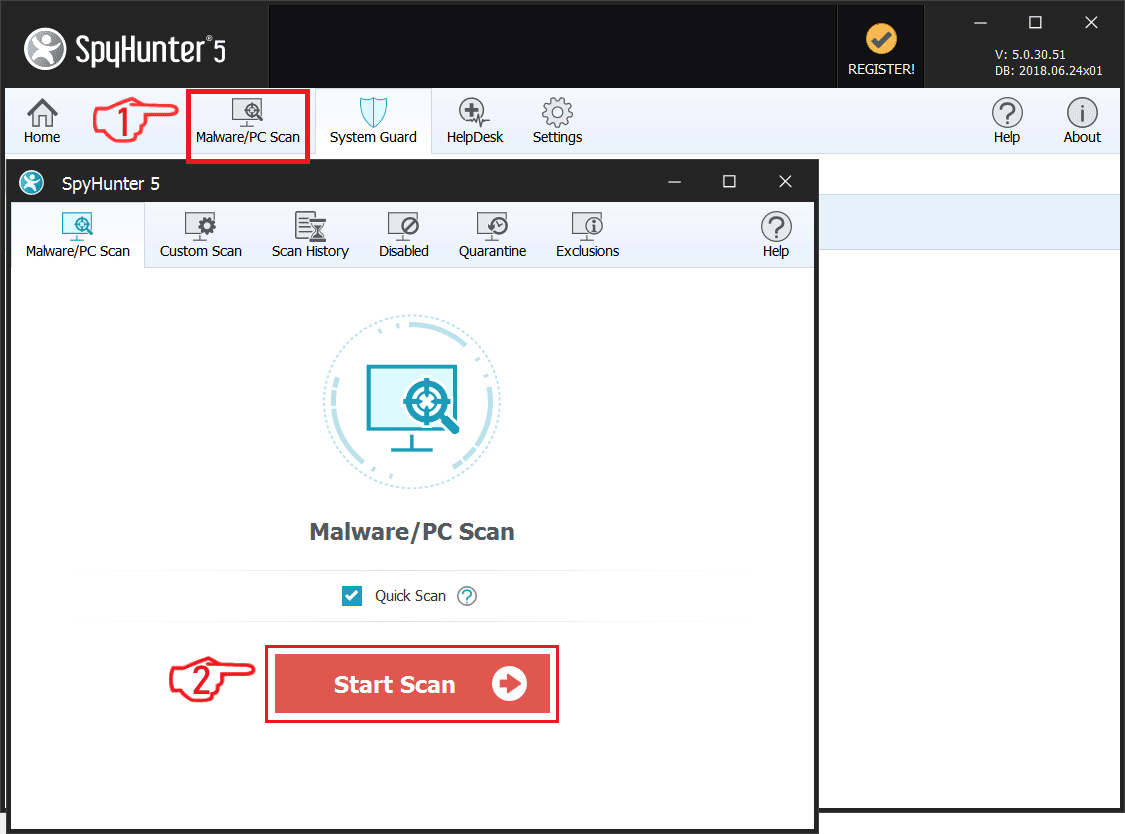
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
| Brugererfaring | Tilmeld dig vores forum at diskutere PirateMatryoshka Trojan. |

PirateMatryoshka Malware - Distributionsmetoder
PirateMatryoshka-malware er en farlig trussel, der primært distribueres i The Pirate Bay torrent tracker, ifølge de frigivne sikkerhedsrapporter er det allerede blevet downloadet ca. 10,000 gange.
Pirate Bay er hostet gennem forskellige internetspejle, der findes på Internettet, og mange af dem har vist sig at sprede malware. Det findes i torrents, der uploades af snesevis af konti, der bruges til dette formål. Det primære mål med PirateMatryoshka malware er at inficere målcomputere ved at være en del af det distribuerede indhold. Denne form for nyttelast levering kan have mange former, der er en del af alt populært indhold, der deles på disse steder:
- Dokumenter - Levering af malware kan udløses via scripts, der kan findes på tværs af alle populære filformater: regneark, præsentationer, rige tekstdokumenter og databaser. Hver gang de åbnes af ofrene, vises der en prompt, der beder brugerne om at aktivere de indbyggede scripts. Den citerede årsag er, at dette er påkrævet for korrekt at se indholdet af filerne.
- Software Installers - Den anden populære teknik er at integrere de nødvendige virusfiler i installationspakkerne til applikationer, som ofte downloades af slutbrugere: kreativitet suiter, systemværktøjer, produktivitet og kontorpakker og etc. De laves ved at tage de officielle eksekverbare filer og tilføje de nødvendige scripts for at oprette de resulterende filer.
- Multimedieindhold - Virusinfektioner kan forårsages via interaktion med al slags indhold inklusive musik, videoer, billeder og etc.
- E-bøger - Malwareinfektioner kan forekomme, selv når du downloader e-bøger og andre relaterede dokumenter.

PirateMatryoshka Malware - Detaljeret beskrivelse
PirateMatryoshka malware-servere som en nyttelastdropper til andre trusler. De lavede infektioner kan ændres afhængigt af den igangværende angrebskampagne. De indfangede prøver hidtil ser ud til at levere en Trojan instans, forskellige adware-komponenter er også en vigtig del af det.
Infektionen konfronteres med et indbygget infektionsmønster, der implementerer en hovedinstallatør med de relevante handlinger. Analysen viser, at følgende:
- Windows Registry Ændringer - Den tilknyttede trojan har vist sig at indeholde evnen til at skabe, redigere og slette registreringsdatabaseværdier, der findes i Windows-registreringsdatabasen. Dette kan få PirateMatryoshka-malware til at starte automatisk, når computeren starter. Derudover kan ændringer i disse værdier føre til alvorlige ydeevneproblemer, så det gør computeren praktisk talt ubrugelig. Andre virkninger af dette det pludselige udseende af fejl, uventet opførsel og tab af data.
- Forbindelse til ekstern server - Motoren downloader en speciel fil fra et fjerntliggende sted, hvorfra adresserne til kommando- og kontrolserverne er hentet. Der oprettes en vedvarende forbindelse, der gør det muligt for hackere at overtage kontrollen med maskinerne, stjæle data og loa yderligere trusler.
- Browser Redirect - En af de farligste handlinger, der foretages af denne type infektioner, er brugeromdirigering. malware vil ændre indstillingerne for de mest populære webbrowsere for at få vist et forudindstillet hackerstyret websted. Dette gøres ved at ændre indstillinger såsom standardhjemmesiden, nye faner side og søgemaskine.
Inden du kører andre handlinger, udfører PirateMatryoshka malware en sikkerhedskontrol at sikre, at ingen anden forekomst er blevet implementeret før den. En kompleks filleveringstaktik følger, og det sikres, at den tilsigtede nyttelast med succes implementeres til de tilsigtede mål. Analysen viser, at der er installeret en autoclicker-software, der forhindrer brugerne i at forsøge at unddrage sig levering af nyttelasten.

Fjern PirateMatryoshka Malware
Hvis din computer-system fik inficeret med PirateMatryoshka Malware, du skal have lidt erfaring med at fjerne malware. Du bør slippe af med denne trojanske så hurtigt som muligt, før det kan få mulighed for at sprede sig yderligere og inficere andre computere. Du bør fjerne den trojanske og følg trin-for-trin instruktioner guide leveres nedenfor.
Note! Dit computersystem kan blive påvirket af PirateMatryoshka Trojan og andre trusler.
Scan din pc med SpyHunter
SpyHunter er en kraftfuld malware fjernelse værktøj designet til at hjælpe brugerne med dybdegående systemets sikkerhed analyse, detektering og fjernelse af PirateMatryoshka Trojan.
Husk, at SpyHunter scanner er kun for malware afsløring. Hvis SpyHunter registrerer malware på din pc, du bliver nødt til at købe SpyHunter har malware fjernelse værktøj til at fjerne malware trusler. Læs vores SpyHunter 5 bedømmelse. Klik på de tilsvarende links til at kontrollere SpyHunter s EULA, Fortrolighedspolitik og Kriterier trusselsvurdering.
For at fjerne PirateMatryoshka Trojan følge disse trin:
Brug SpyHunter at scanne for malware og uønskede programmer
Preparation before removing PirateMatryoshka Trojan.
, Før den egentlige fjernelse proces, Vi anbefaler, at du gør følgende forberedelse trin.
- Sørg for at have disse instruktioner altid åben og foran dine øjne.
- Gør en sikkerhedskopi af alle dine filer, selv om de kunne blive beskadiget. Du bør sikkerhedskopiere dine data med en sky backup-løsning og forsikre dine filer mod enhver form for tab, selv fra de mest alvorlige trusler.
- Vær tålmodig, da det kan tage et stykke tid.
- Scan for malware
- Rette registre
- Fjern virusfiler
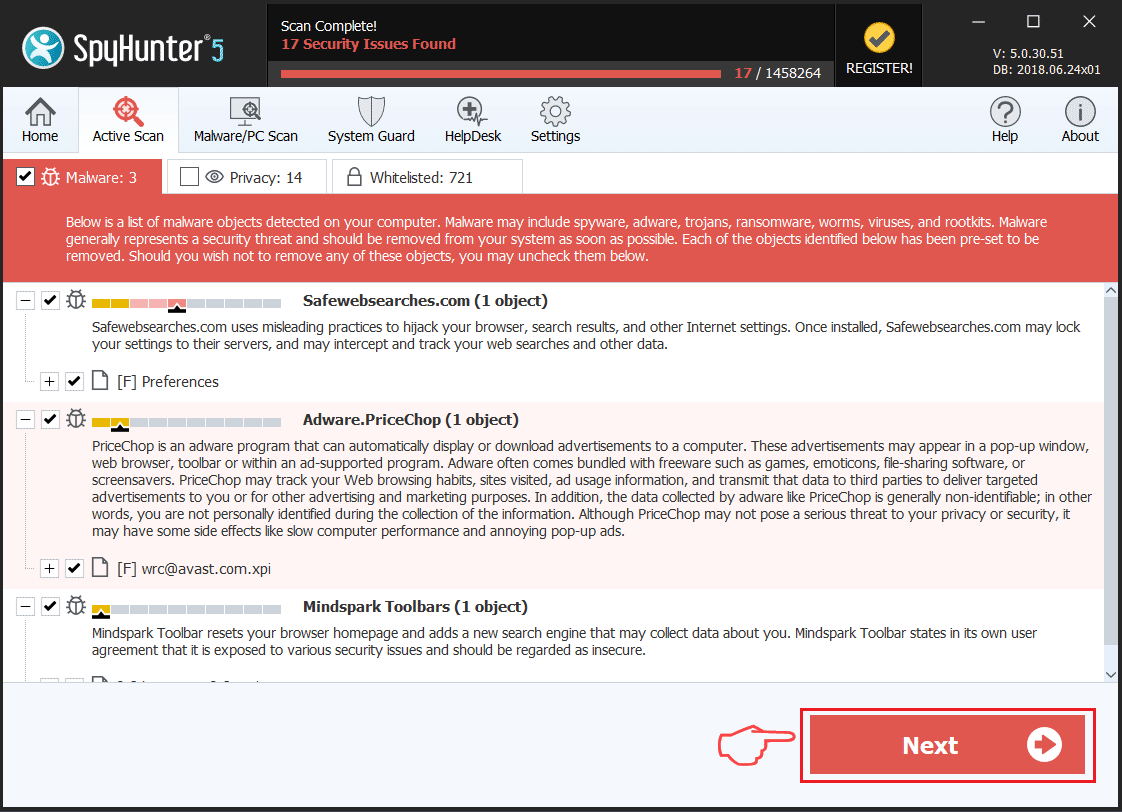
Trin 1: Scan efter PirateMatryoshka Trojan med SpyHunter Anti-Malware-værktøj



Trin 2: Rens eventuelle registre, oprettet af PirateMatryoshka Trojan på din computer.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, oprettet af PirateMatryoshka Trojan der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.Trin 3: Find virus files created by PirateMatryoshka Trojan on your PC.
1.For Windows 8, 8.1 og 10.
For Nyere Windows-operativsystemer
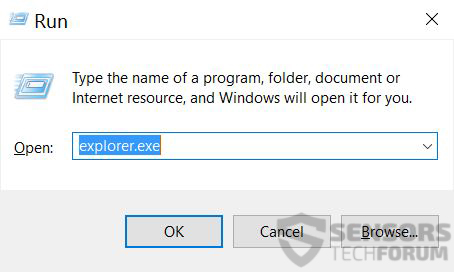
1: På dit tastatur tryk + R og skrive explorer.exe i Løbe tekstboks og derefter klikke på Ok knap.

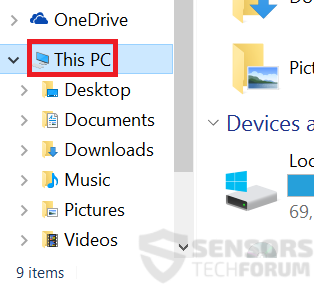
2: Klik på din pc fra hurtig adgang bar. Dette er normalt et ikon med en skærm og dets navn er enten "Min computer", "Min PC" eller "Denne PC" eller hvad du har navngivet det.

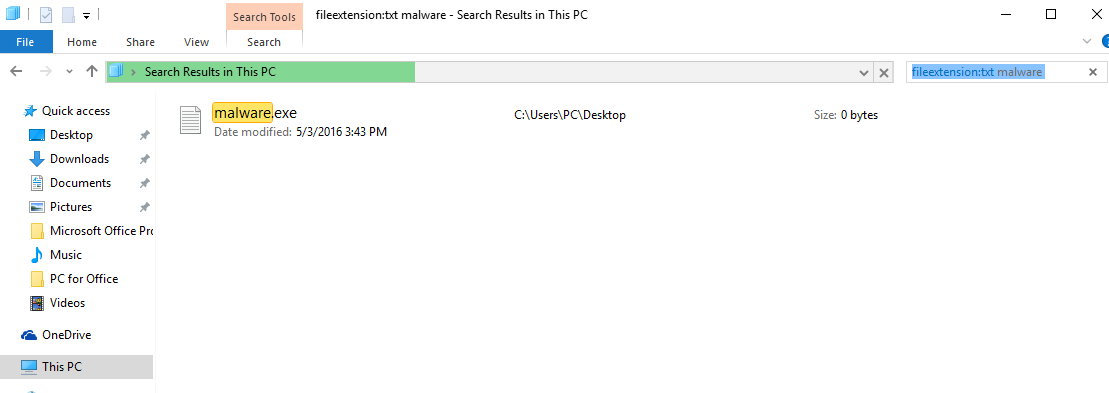
3: Naviger til søgefeltet øverst til højre på din pc's skærm og type "fileextension:" og hvorefter skrive filtypen. Hvis du er på udkig efter ondsindede eksekverbare, et eksempel kan være "fileextension:exe". Efter at gøre det, efterlade et mellemrum og skriv filnavnet du mener malware har skabt. Her er, hvordan det kan se ud, hvis der er fundet din fil:

NB. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.I Windows XP, Vista, og 7.
For ældre Windows-operativsystemer
I ældre Windows OS bør den konventionelle tilgang være den effektive:
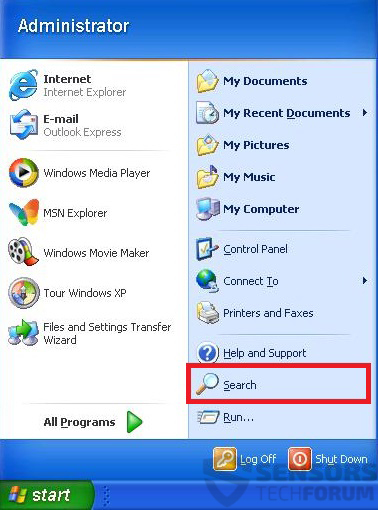
1: Klik på Start Menu ikon (normalt på din nederste venstre) og vælg derefter Søg præference.

2: Efter søgningen vises, vælge Flere avancerede indstillinger fra søgningen assistent boksen. En anden måde er ved at klikke på Alle filer og mapper.

3: Efter denne type navnet på den fil, du søger, og klik på knappen Søg. Dette kan tage noget tid, hvorefter resultater vises. Hvis du har fundet den skadelig fil, du må kopiere eller åbne sin placering ved højreklikke på det.
Nu skulle du være i stand til at opdage en fil på Windows, så længe det er på din harddisk og ikke skjult via speciel software.
PirateMatryoshka Trojan FAQ
What Does PirateMatryoshka Trojan Trojan Do?
The PirateMatryoshka Trojan Trojan er et ondsindet computerprogram designet til at forstyrre, skade, eller få uautoriseret adgang til et computersystem. Det kan bruges til at stjæle følsomme data, få kontrol over et system, eller starte andre ondsindede aktiviteter.
Kan trojanske heste stjæle adgangskoder?
Ja, Trojans, like PirateMatryoshka Trojan, kan stjæle adgangskoder. Disse ondsindede programmer are designed to gain access to a user's computer, spionere på ofrene og stjæle følsomme oplysninger såsom bankoplysninger og adgangskoder.
Can PirateMatryoshka Trojan Trojan Hide Itself?
Ja, det kan. En trojaner kan bruge forskellige teknikker til at maskere sig selv, inklusive rootkits, kryptering, og formørkelse, at gemme sig fra sikkerhedsscannere og undgå registrering.
Kan en trojaner fjernes ved fabriksnulstilling?
Ja, en trojansk hest kan fjernes ved at nulstille din enhed til fabriksindstillinger. Dette skyldes, at det vil gendanne enheden til sin oprindelige tilstand, eliminering af skadelig software, der måtte være blevet installeret. Husk på, at der er mere sofistikerede trojanske heste, der forlader bagdøre og geninficerer selv efter en fabriksnulstilling.
Can PirateMatryoshka Trojan Trojan Infect WiFi?
Ja, det er muligt for en trojaner at inficere WiFi-netværk. Når en bruger opretter forbindelse til det inficerede netværk, trojaneren kan spredes til andre tilsluttede enheder og kan få adgang til følsomme oplysninger på netværket.
Kan trojanske heste slettes?
Ja, Trojanske heste kan slettes. Dette gøres typisk ved at køre et kraftfuldt anti-virus eller anti-malware program, der er designet til at opdage og fjerne ondsindede filer. I nogle tilfælde, manuel sletning af trojaneren kan også være nødvendig.
Kan trojanske heste stjæle filer?
Ja, Trojanske heste kan stjæle filer, hvis de er installeret på en computer. Dette gøres ved at tillade malware forfatter eller bruger for at få adgang til computeren og derefter stjæle filerne, der er gemt på den.
Hvilken anti-malware kan fjerne trojanske heste?
Anti-malware programmer som f.eks SpyHunter er i stand til at scanne efter og fjerne trojanske heste fra din computer. Det er vigtigt at holde din anti-malware opdateret og regelmæssigt scanne dit system for skadelig software.
Kan trojanske heste inficere USB?
Ja, Trojanske heste kan inficere USB enheder. USB-trojanske heste spredes typisk gennem ondsindede filer downloadet fra internettet eller delt via e-mail, allowing the hacker to gain access to a user's confidential data.
About the PirateMatryoshka Trojan Research
Indholdet udgiver vi på SensorsTechForum.com, this PirateMatryoshka Trojan how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed til at hjælpe dig med at fjerne det specifikke trojanske problem.
How did we conduct the research on PirateMatryoshka Trojan?
Bemærk venligst, at vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om de seneste malware-definitioner, herunder de forskellige typer trojanske heste (bagdør, Downloader, infostealer, løsesum, etc.)
Endvidere, the research behind the PirateMatryoshka Trojan threat is backed with VirusTotal.
For bedre at forstå truslen fra trojanske heste, Se venligst følgende artikler, som giver kyndige detaljer.



 1. I Windows XP, Vista og 7.
1. I Windows XP, Vista og 7. 2. For Windows 8, 8.1 og 10.
2. For Windows 8, 8.1 og 10. oplysningerne Fix registreringsdatabasen skabt af malware og PUP på din pc.
oplysningerne Fix registreringsdatabasen skabt af malware og PUP på din pc.
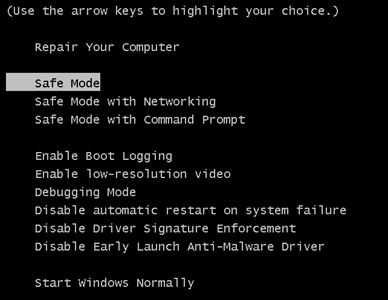
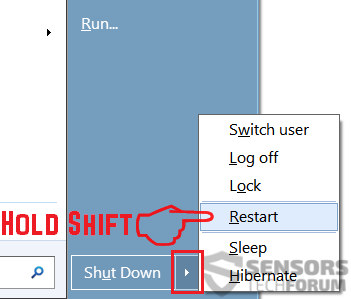
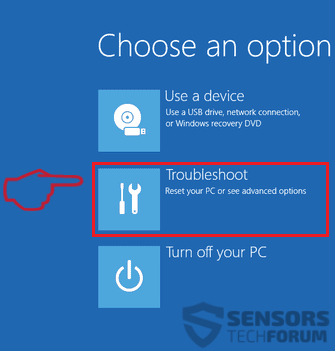
 1. Installer SpyHunter for at scanne efter PirateMatryoshka Trojan og fjerne dem.
1. Installer SpyHunter for at scanne efter PirateMatryoshka Trojan og fjerne dem.