Læs artiklen for at se, hvordan du kan undgå Revolut Phishing-svindel og fjerne malware som blev distribueret af sådanne svindel. E-mails, beskeder og hjemmesider er alle involveret i disse typer af spoofing. Artiklen vil også hjælpe dig til at genkende Revolut Phishing-svindel og den officielle Revol meddelelser fra hinanden. Hvis du opdager, at din computer er inficeret eller opfører sig mærkeligt, Vi anbefaler, at du scanner det med et sikkerhedsværktøj.
Revolut Phishing-svindel er almindelige i verden. Mange variationer af disse fupnumre findes, featuring hjemmesider specielt designet til at generere spoof sider, beskeder bevidst forsøger at narre du har et problem, eller meddelelser, der kan føre til stjålne legitimationsoplysninger eller din pc bliver inficeret med malware. Alle disse typer af Revolut svindel er stadig i omløb, og gennem dem, en masse af følsomme oplysninger eller penge bliver stjålet. Folk bliver ved med at blive ofre for relaterede spoof beskeder, trods i hvilken form de er sendt på. I årenes løb Revol bruges i mange svindelnumre og med hver ny, cyberkriminelle at forbedre deres færdigheder for at gøre en fidus så tæt som muligt på den oprindelige messaging bruges af store brand. Hvis du er målrettet med en misvisende besked, vil du blive bedt om at logge ind på ”Revol”Eller besøger et websted domæne og udføre en handling der ligesom at betale for en mislykket forsendelse.

Trussel Summary
| Navn | |
| Type | Phishing, PUP, malware |
| Kort beskrivelse | Phishing-meddelelser, der forsøger at narre dig til at klikke på links. Når du har klikket, et link vil omdirigere dig på en landing page. Du vil blive bedt om at gøre en handling der, såsom at give legitimationsoplysninger, personlige oplysninger eller fyldning i en form. En gang imellem, klikke på et link, vil hente malware på din computer. |
| Symptomer | Du modtager en e-mail, der er angiveligt fra Revol. Du vil blive opfordret til at klikke på et link. Du kan derefter få malware på computeren enhed eller lander på en side, der efterligner den officielle Revol internet side, mens krævende af dig at udfylde personlige oplysninger. |
| Distributionsmetode | phishing e-mails, Pop-up-meddelelser, Omdirigeringer |
| Værktøj Detection |
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
| Brugererfaring | Tilmeld dig vores forum at diskutere . |

Revolut phishing-svindel oktober 2019 Opdatering - fup Verifikation Links
Sikkerhedseksperter advarer om en farlig social engineering kampagne er rettet mod Revolut brugere. Den valgte af hackere metode er at sende falske e-mails, meddelelser og alle sind meddelelser for at manipulere dem til at tro, at deres konto vil blive låst. Disse meddelelser betragtes scareware taktik og som regel har en høj chance for succes, da de fleste brugere vil være bekymret for at miste adgangen til deres midler.
Sikkerhedstjek kan ske, hvis Systemet hvidvaskning af penge er blevet udløst dog Revolut vil aldrig bede om loginoplysninger eller finansielle oplysninger, som kan anvendes i ører til at stjæle penge. Modtagerne af meddelelserne vil blive vist et link til en hacker-kontrollerede side, som kan være et af følgende:
- Log Prompts - De links vil føre til en login-prompt, der vil anmode om, at brugere indtaste deres Revolut legitimationsoplysninger for at kontrollere dem. Dermed vil automatisk giver hackere adgang til deres midler og personlige oplysninger.
- Filer Upload - Gennem de falske apps hackere vil anmode personlige dokumenter og følsomme til at blive uploadet.
- APK Download og installation - I nogle tilfælde kan brugerne blive snydt i at downloade og installere en malware APK fra en hacker-kontrolleret arkiv.

Revolut Phishing-svindel - Distribution Metoder
Den Revolut phishing-svindel bliver langt mere forskellige som den finansielle tjenesteydelse bliver stadig mere populære blandt mobilbrugere. I øjeblikket har der været flere kampagner, der har vist sig at være blandt de største svindelnumre for tjeneste. I de fleste tilfælde vil de bruge den såkaldte direkte metoder der vil nå ud til brugerne og forsøger at manipulere dem til at give deres personlige oplysninger eller app legitimationsoplysninger. Der er flere populære vigtigste metoder, der er almindeligt anvendt af hackere:
- spam e-mails - De hackere kan sende meddelelser i bulk under anvendelse af en SPAM fremgangsmåde, hvor meddelelserne synes at være sendt af Revolut, bank, Google, Apple eller en anden part, der er bundet til den finansielle tjenesteydelse. Indholdet vil højst sandsynligt blive stjålet eller ligne en, der er normalt sendes til ofrene. Normalt infektioner er forårsaget gennem omdirigeringer, der udføres, når brugerne klikker på tekstlinks, multimediefiler eller deltage i visse aktiviteter - downloade filer, rulning og etc. Dette gøres ved at indlejre i avancerede JavaScript-scripts som nogle e-mail-udbydere sætte dem som standard.
- Malware Websites - De kriminelle kan altid skabe falske websteder, der præsenterer sig selv som legitime destinationssider, dele af Revolut stedet eller login prompter. Der er to hovedtyper - dem, der hostes på lignende klingende domænenavne og muligvis en underskrevet og gyldig sikkerhedscertifikat og de websteder, der vises gennem en forkortet webadresse tjeneste. Disse sider er normalt logge prompter eller dele af Revolut webstedet.
- Omdirigeringer - De omdirigeringer som regel resultat af at have installeret en browser flykaprere vil automatisk præsentere endpoint side til ofrene. Hvis browseren manipulation er gjort adresselinjen kan vise den legitime Revolut site, men i virkeligheden den falske websted vil blive vist.
- annoncenetværk - Hackerne kan skabe liste malware sites på annoncenetværk bruger deres egne legitimationsoplysninger eller gennem hackede / falske dem. Dette er en meget effektiv strategi, da det vil blive lagt ud på både sikre websteder og samfund og på tværs af sider, der integrerer den relevante annoncenetværk. Ved hjælp af denne metode alene de Revolut phishing-svindel kan nå en meget stor og muligvis globalt publikum.
Den phishing scams omdirigeringer kan også være forårsaget ved at interagere med forskellige filer og programmer. Dette kan præsenteres ved hjælp af forskellige filtyper og malware læssemaskiner. Et godt eksempel er det ofte skabt makro-inficerede dokumenter som kan være af alle populære formater: tekstfiler, databaser, regneark og præsentationer. Når de er åbnet af ofrene en prompt vil blive vist beder dem om at gøre det muligt for de indbyggede scripts. Hvis dette gøres den tilhørende malware motor vil blive startet. Et alternativ er at skabe ondsindede bundt installatører der er normalt legitime setup bundle installatører af populære programmer, som downloades af slutbrugere: kreativitet suiter, produktivitet og kontor apps, systemværktøjer og endda computerspil. De er uploadet til forskellige steder, herunder download-portaler og fildeling netværk som BitTorrent.
Husk på, at en stor del af de infektioner er færdig ved at hente og interagere med browser hijackers - de er farlige plugins, der er lavet kompatibel med de mest populære webbrowsere. De bogførte beskrivelser vil løfte tilsætning af ekstra funktioner eller ydeevne optimeringer. For at gøre det de kriminelle vil bruge falske brugeranmeldelser og skrive beskrivelserne gennem efterlignede eller stjålne udvikler credenials. Et stort antal Revolut phishing-svindel kan orkestreret ved at offentliggøre falske apps til både Android og iOS og offentliggjort på deres respektive depoter.

Sim-kort Swap Revolut Phishing-svindel
En af de mest almindelige taktik, som er blevet fundet at plage Revolut kunder er SIM-kort swap, organiseret af de hacking gruppe. Dette gøres ved hjælp af andre svindel for at tage kontrol over målet telefonnummer. De svindlere gøre det ved at indsamle nok personlige oplysninger for at overbevise de mobile tjenester i uddele kontrol af den tilhørende SIM-kort til de kriminelle. I sidste ende vil dette gøre det muligt for hackere at overtage kontrollen af regnskabet ved at levere deres egne kort og hævder, at de er brugerne.

Revolut Phishing-svindel - Protection Tips
For at beskytte sig mod Revolut phishing brugerne bliver nødt til at tage ekstra forsigtig, når at levere oplysninger om sig selv eller i forbindelse med deres Revolut konti. Vær særlig opmærksom på, at hackere kan nemt udgive Revolut personale og social ingeniør ofrene til at afsløre deres kort PIN-numre eller sikkerhedsforanstaltninger reaktioner såsom adgangskoder. Den bedste indsats for at gøre i dette tilfælde er at tage et screenshot og rapportere dem direkte til Revolut.
Vær opmærksom, at kommunikation sker hovedsagelig gennem legitime applikationer støttefunktion. Revolut vil aldrig nå ud til de enkelte brugere via sociale netværk profiler, særlig hjemmeside eller portaler. Vi rådgiver også alle Revolut brugere til konstant at holde øje med opdateringer og holde deres ansøgninger opdateret på alle tidspunkter.
I de sidste par måneder har der været flere observationer af falske og forfalskede meddelelser, der vil omdirigere brugerne til en falsk log ind eller verifikation side. Vi minder vore læsere, at sådanne meddelelser er falske og bør behandles med mistænksomhed. De kan tage form af pop-ups og e-mails.

Fjern Revolut phishing-svindel og relaterede Malware
Alt, hvad der kræves for at fjerne nogle Revolut Phishing-svindel er at ignorere meddelelsen, aldrig reagere på det og slette den. Andre svindel kræver en smule handling, såsom grundigt scanne din computer maskine med sikkerhedssoftware at afgøre, om du har nogle malware komponent, der skubber Revol spoof beskeder til din computer, browser eller e-mail-adresse.
Vi anbefaler, at alle computerbrugere scanne deres system for aktive infektioner og malware ved hjælp af et sikkerhedsprogram. Det kunne forhindre mange ondsindede handlinger og stoppe malware distribuere yderligere.
Spy Hunter scanner kun detektere trussel. Hvis du ønsker, at truslen skal fjernes automatisk, du nødt til at købe den fulde version af anti-malware værktøj.Læs mere om SpyHunter Anti-Malware værktøj / Sådan fjernes SpyHunter
- Vinduer
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop push-pop op-vinduer
Sådan fjernes fra Windows.
Trin 1: Scan efter med SpyHunter Anti-Malware værktøj



Trin 2: Start din pc i fejlsikret tilstand





Trin 3: Afinstaller og tilhørende software fra Windows
Afinstaller Steps til Windows 11
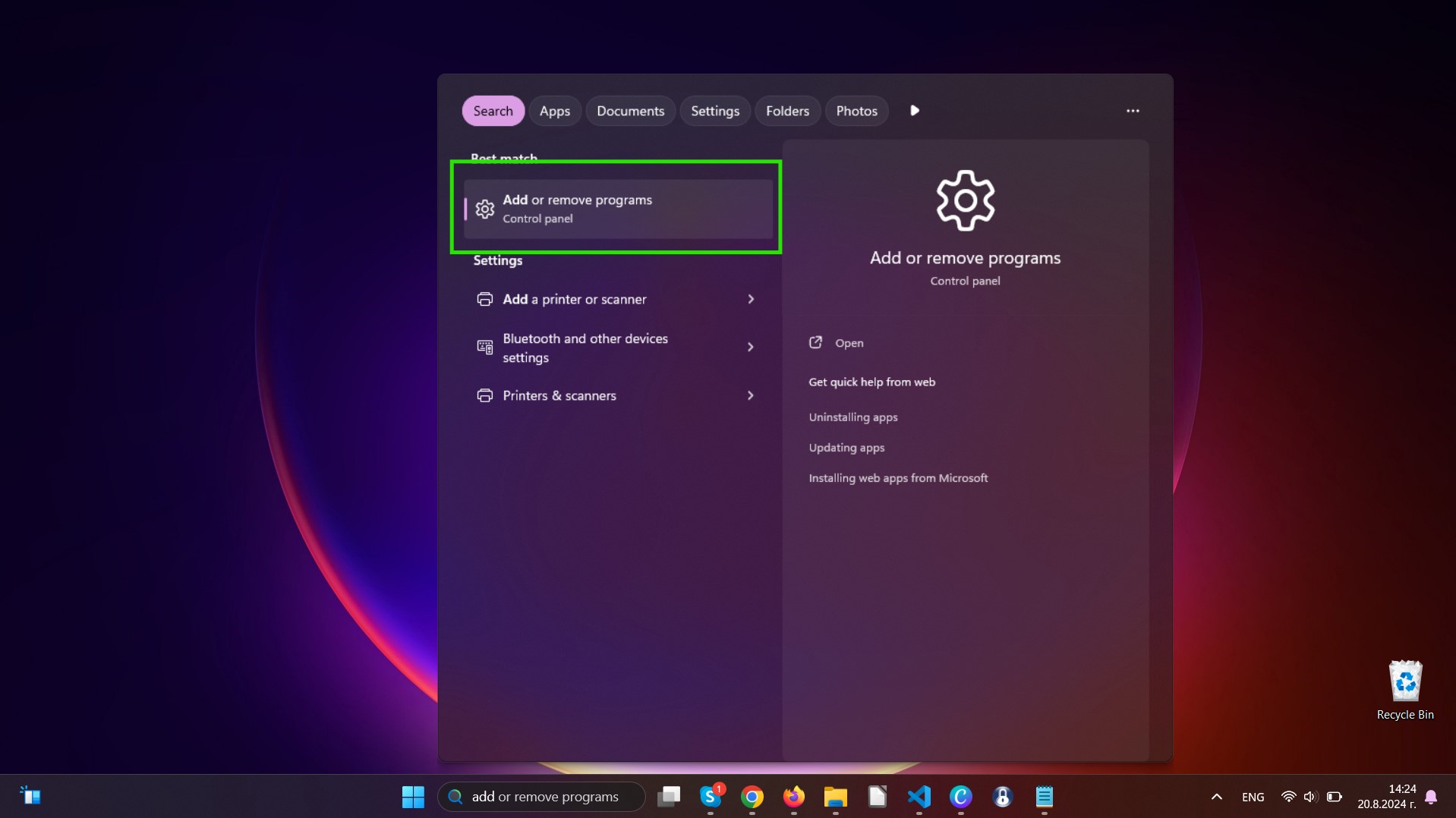
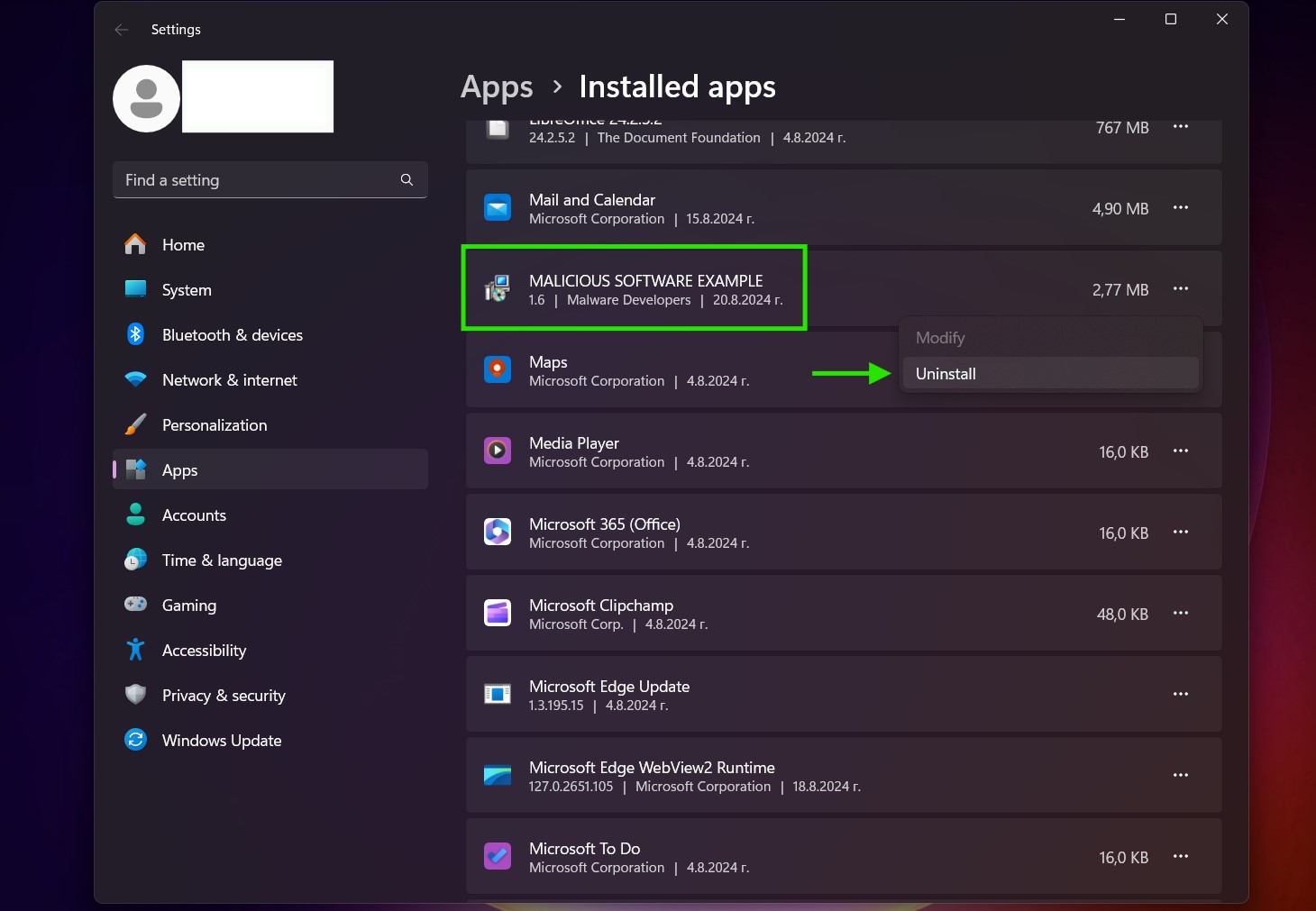
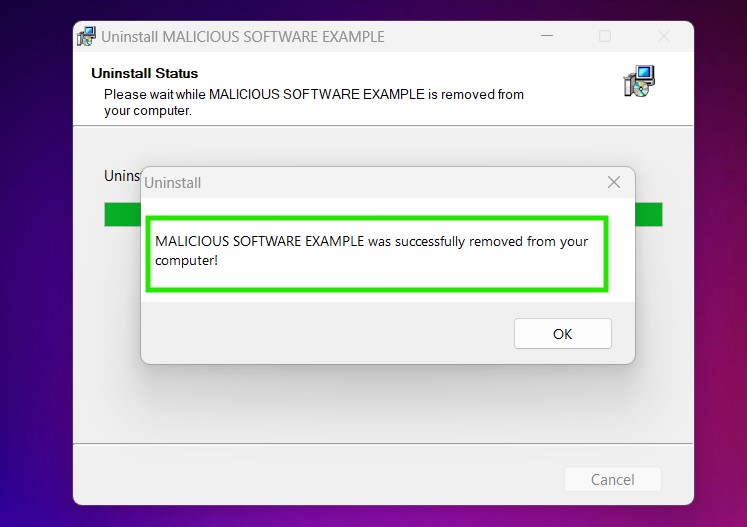
Afinstaller Steps til Windows 10 og ældre versioner
Her er en metode i nogle få nemme trin, der bør være i stand til at afinstallere de fleste programmer. Uanset om du bruger Windows 10, 8, 7, Vista eller XP, disse skridt vil få arbejdet gjort. At trække det program eller dets mappe til papirkurven kan være en meget dårlig beslutning. Hvis du gør det, stumper og stykker af programmet er efterladt, og det kan føre til ustabile arbejde på din PC, fejl med filtypen foreninger og andre ubehagelige aktiviteter. Den rigtige måde at få et program fra din computer er at afinstallere det. For at gøre dette:


 Følg anvisningerne ovenfor, og du vil afinstallere de fleste programmer.
Følg anvisningerne ovenfor, og du vil afinstallere de fleste programmer.
Trin 4: Rens eventuelle registre, Oprettet af på din pc.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, skabt af der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Videofjernelsesvejledning til (Vinduer).
Slip af med Mac OS X.
Trin 1: Afinstaller og fjerne relaterede filer og objekter
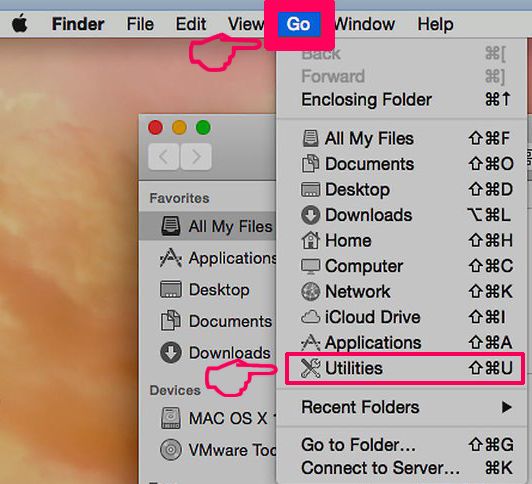
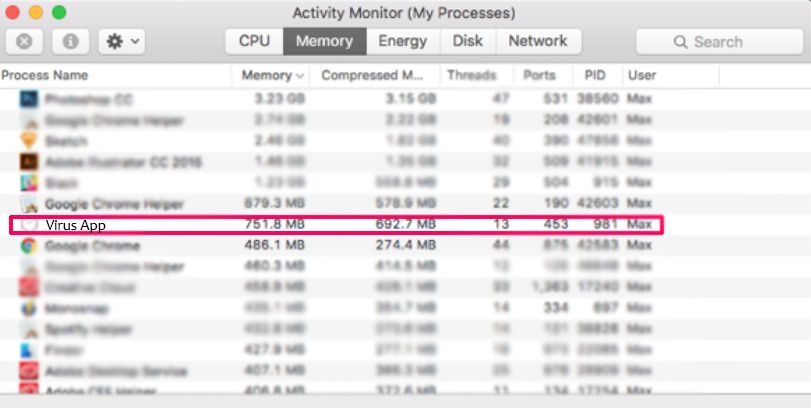
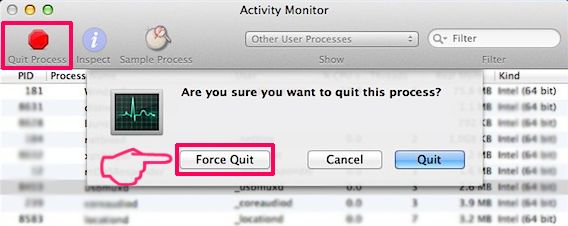
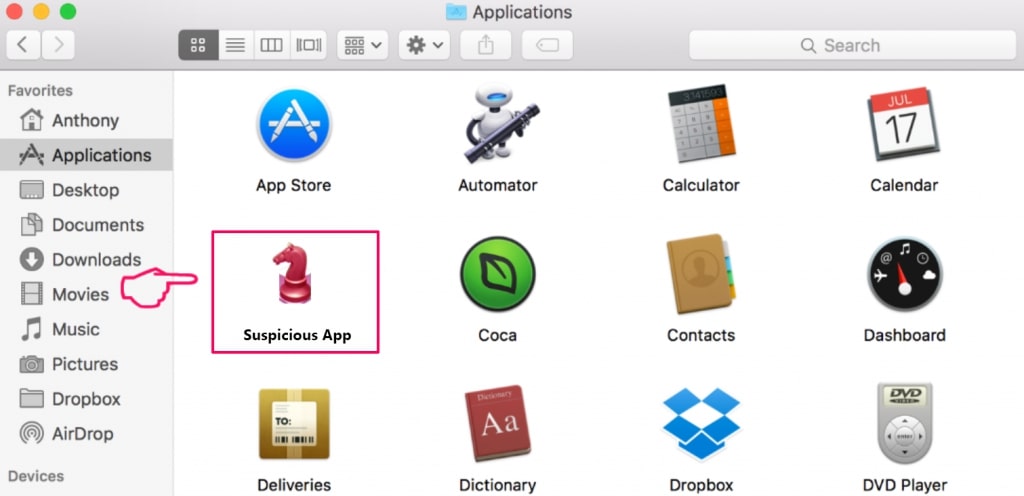
Din Mac vil så vise dig en liste over emner, starte automatisk når du logger ind. Kig efter eventuelle mistænkelige apps identiske med eller ligner . Tjek den app, du ønsker at stoppe i at køre automatisk, og vælg derefter på Minus ("-") ikonet for at skjule det.
- Gå til Finder.
- I søgefeltet skriv navnet på den app, du vil fjerne.
- Over søgefeltet ændre to rullemenuerne til "System Files" og "Er Inkluderet" så du kan se alle de filer, der er forbundet med det program, du vil fjerne. Husk på, at nogle af filerne kan ikke være relateret til den app, så være meget forsigtig, hvilke filer du sletter.
- Hvis alle filerne er relateret, hold ⌘ + A knapperne til at vælge dem og derefter køre dem til "Affald".
I tilfælde af at du ikke fjerne via Trin 1 over:
I tilfælde af at du ikke finde virus filer og objekter i dine programmer eller andre steder, vi har vist ovenfor, kan du manuelt søge efter dem i bibliotekerne i din Mac. Men før du gør dette, læs den fulde ansvarsfraskrivelse nedenfor:
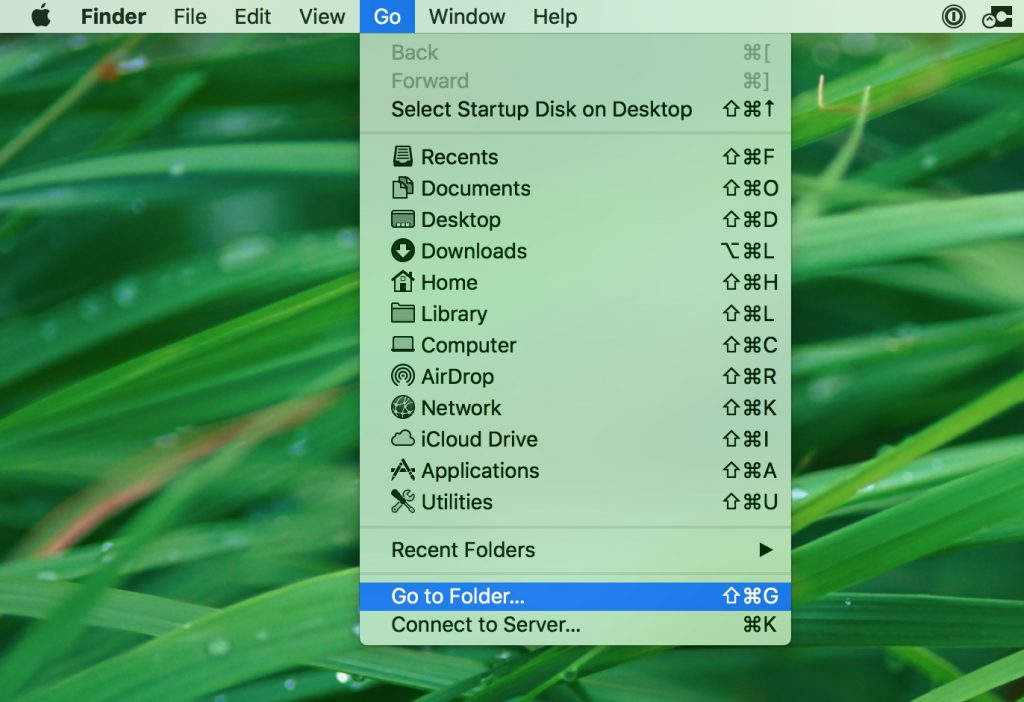
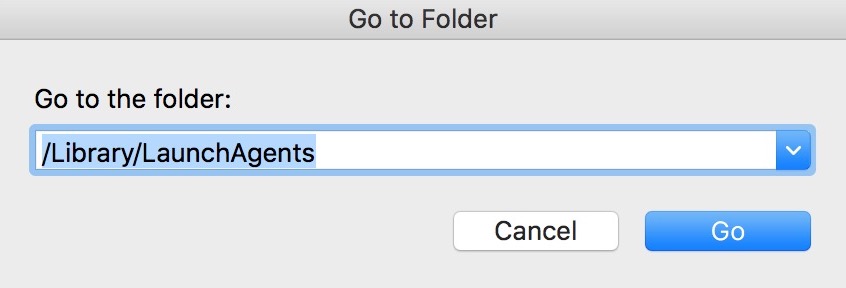
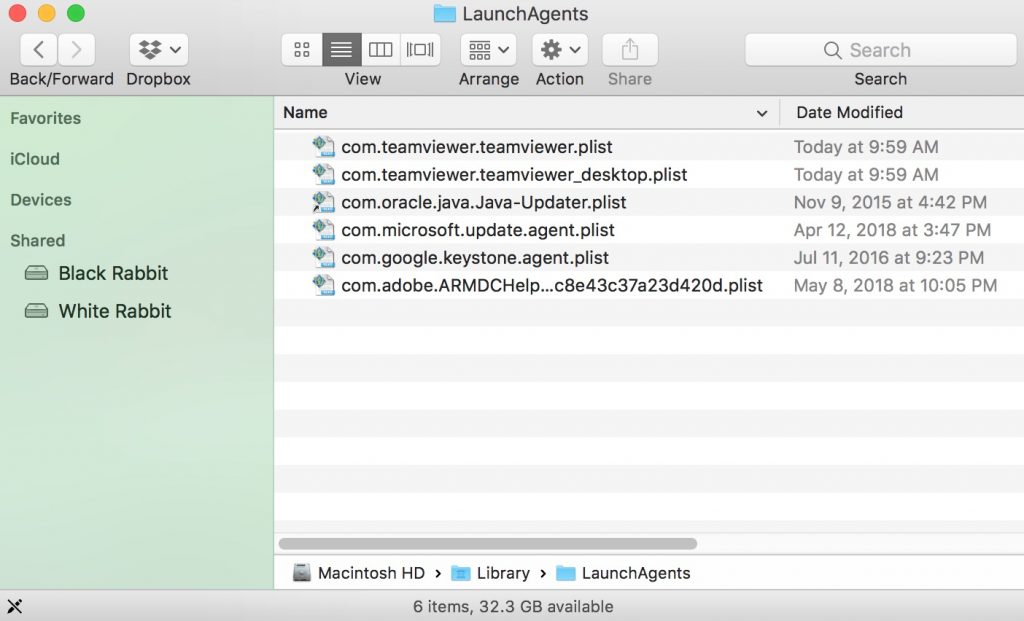
Du kan gentage den samme procedure med den følgende anden Bibliotek mapper:
→ ~ / Library / LaunchAgents
/Bibliotek / LaunchDaemons
Tip: ~ er der med vilje, fordi det fører til flere LaunchAgents.
Trin 2: Scan efter og fjern filer fra din Mac
Når du står over for problemer på din Mac som følge af uønskede scripts og programmer såsom , den anbefalede måde at eliminere truslen er ved hjælp af en anti-malware program. SpyHunter til Mac tilbyder avancerede sikkerhedsfunktioner sammen med andre moduler, der forbedrer din Mac's sikkerhed og beskytter den i fremtiden.
Videofjernelsesvejledning til (Mac)
Fjern fra Google Chrome.
Trin 1: Start Google Chrome, og åbn dropmenuen
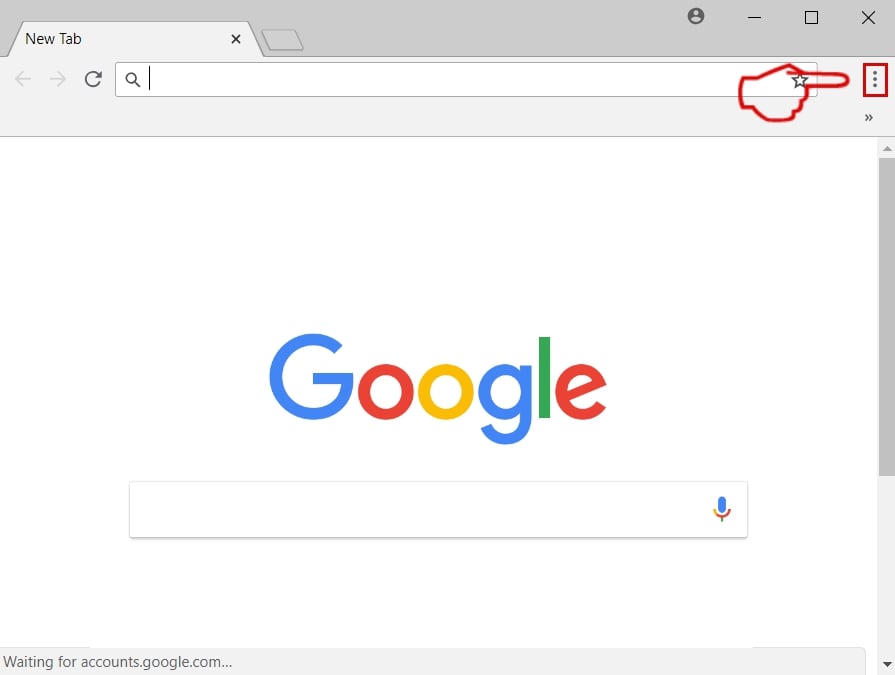
Trin 2: Flyt markøren hen over "Værktøj" og derefter fra den udvidede menu vælge "Udvidelser"
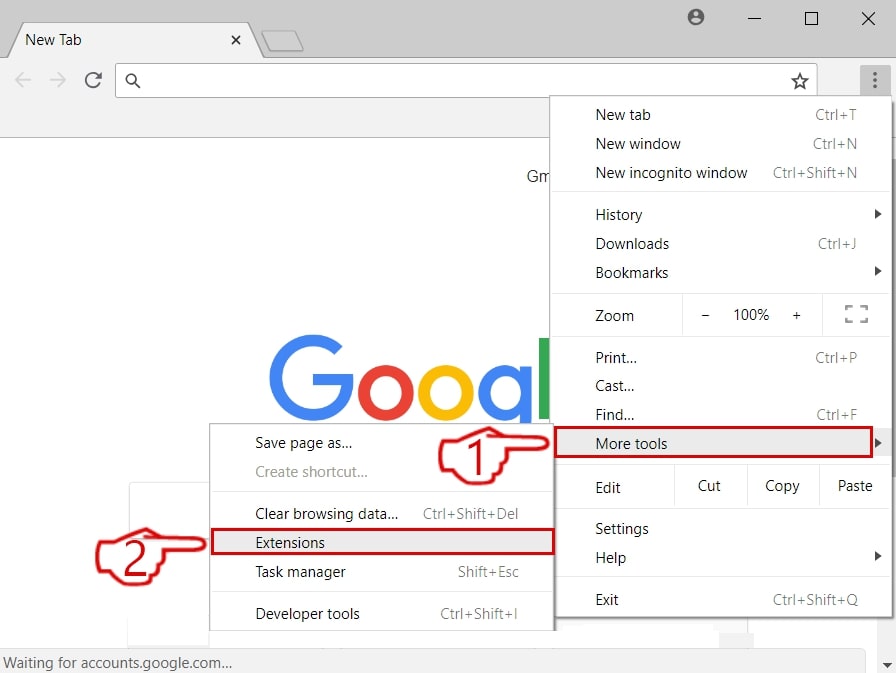
Trin 3: Fra den åbnede "Udvidelser" Menuen lokalisere den uønskede udvidelse og klik på dens "Fjerne" knap.
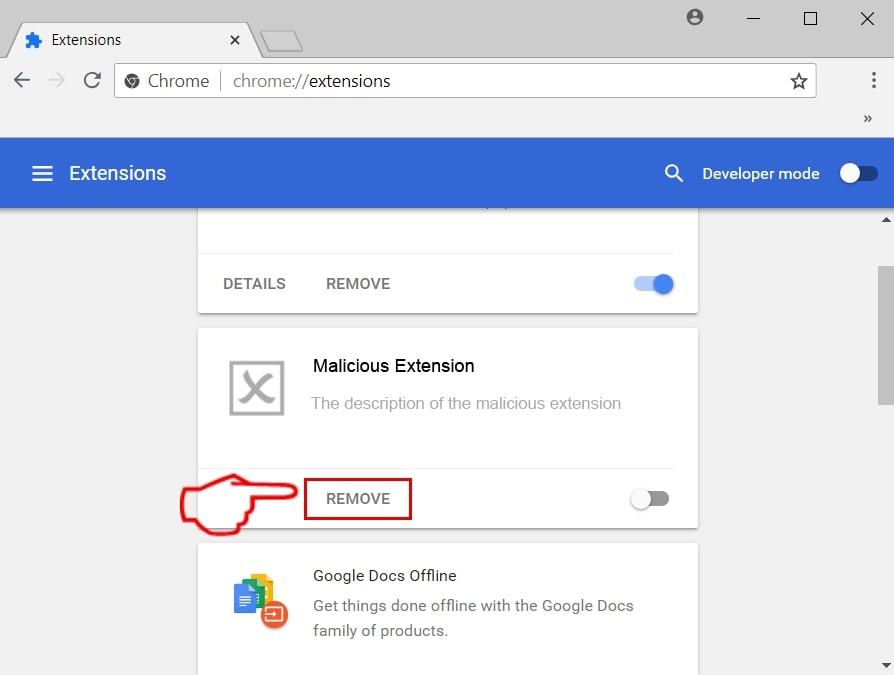
Trin 4: Efter udvidelsen er fjernet, genstarte Google Chrome ved at lukke det fra den røde "X" knappen i øverste højre hjørne, og starte den igen.
Slet fra Mozilla Firefox.
Trin 1: Start Mozilla Firefox. Åbn menuen vindue:
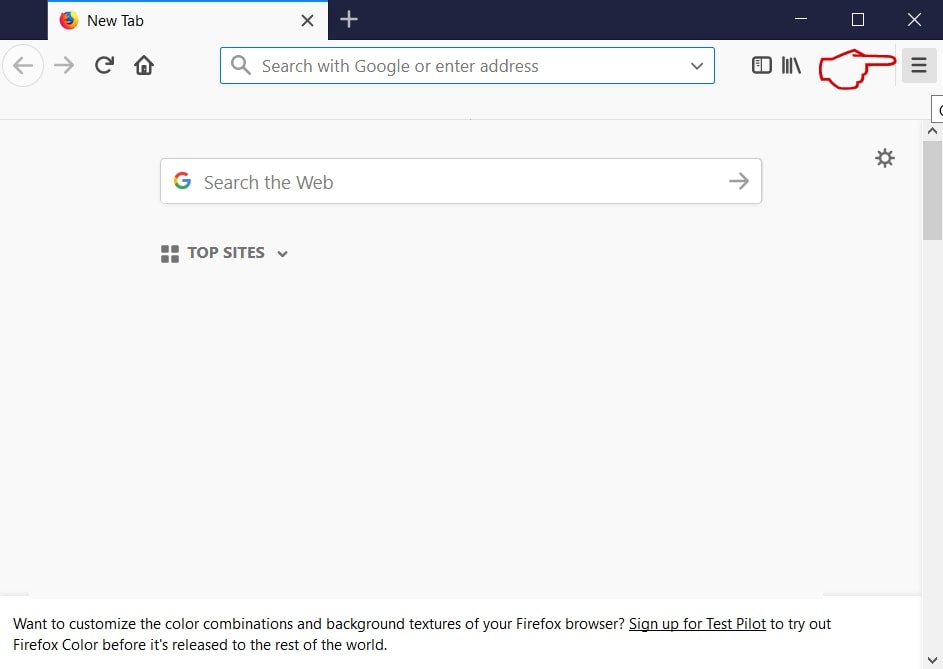
Trin 2: Vælg "Add-ons" ikon fra menuen.
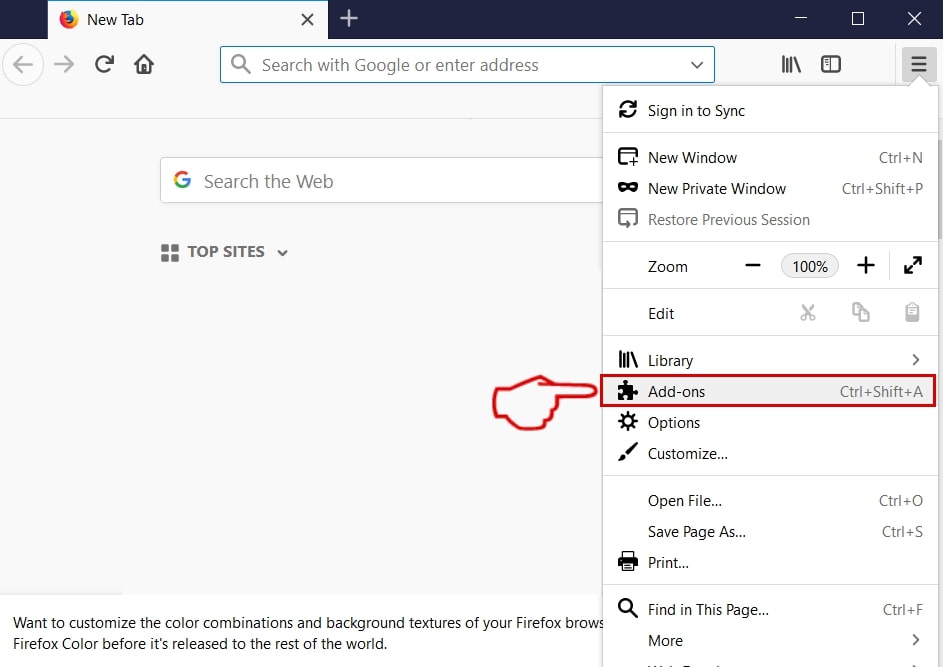
Trin 3: Vælg den uønskede udvidelse og klik "Fjerne"

Trin 4: Efter udvidelsen er fjernet, genstarte Mozilla Firefox ved at lukke det fra den røde "X" knappen i øverste højre hjørne, og starte den igen.
Afinstaller fra Microsoft Edge.
Trin 1: Start Edge-browser.
Trin 2: Åbn drop-menuen ved at klikke på ikonet i øverste højre hjørne.
Trin 3: Fra drop-menuen vælg "Udvidelser".
Trin 4: Vælg den formodede ondsindede udvidelse, du vil fjerne, og klik derefter på tandhjulsikonet.
Trin 5: Fjern den ondsindede udvidelse ved at rulle ned og derefter klikke på Afinstaller.
Fjern fra Safari
Trin 1: Start Safari-appen.
Trin 2: Efter at holde musen markøren til toppen af skærmen, klik på Safari-teksten for at åbne dens rullemenu.
Trin 3: Fra menuen, Klik på "Indstillinger".
Trin 4: Efter at, vælg fanen 'Udvidelser'.
Trin 5: Klik én gang på udvidelse, du vil fjerne.
Trin 6: Klik på 'Afinstaller'.
Et pop-up vindue vises beder om bekræftelse til at afinstallere forlængelsen. Vælg 'Fjern' igen, og vil blive fjernet.
Fjern fra Internet Explorer.
Trin 1: Start Internet Explorer.
Trin 2: Klik på tandhjulsikonet mærket 'Værktøjer' for at åbne drop-menuen og vælg 'Administrer tilføjelser'
Trin 3: I vinduet 'Administrer tilføjelser'.
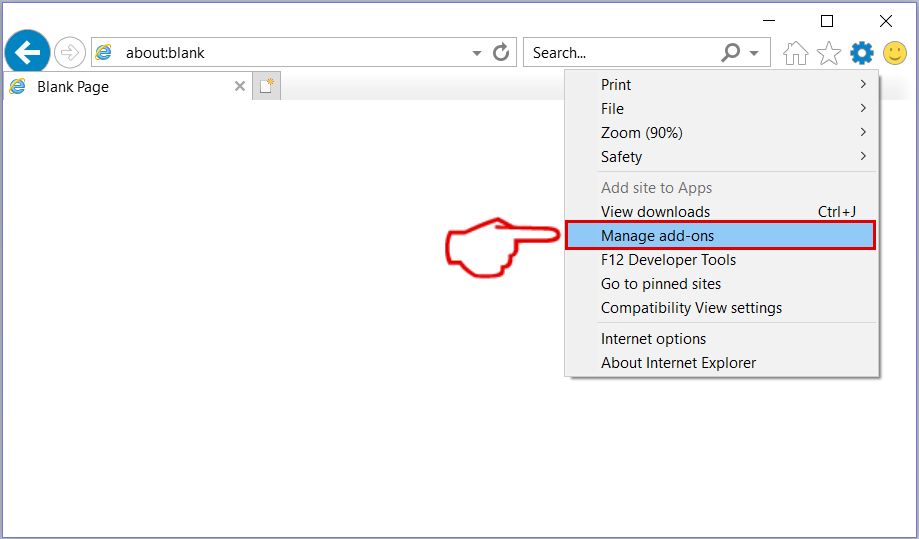
Trin 4: Vælg den udvidelse, du vil fjerne, og klik derefter på 'Deaktiver'. Et pop-up vindue vises for at informere dig om, at du er ved at deaktivere den valgte udvidelse, og nogle flere tilføjelser kan være deaktiveret så godt. Lad alle boksene kontrolleret, og klik på 'Deaktiver'.
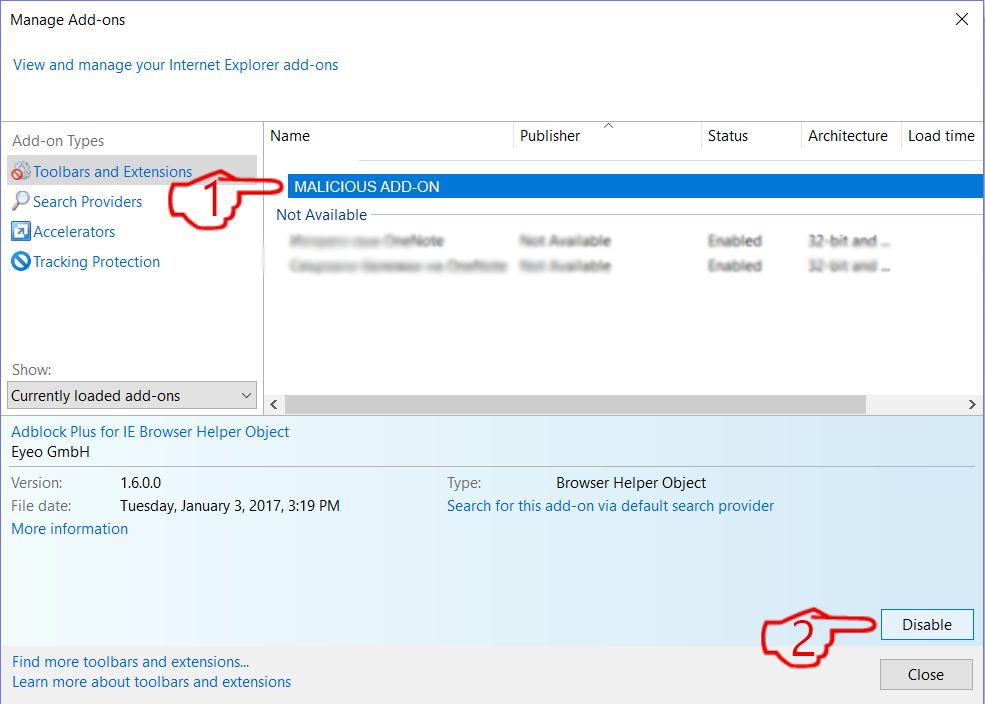
Trin 5: Efter den uønskede udvidelse er blevet fjernet, genstart Internet Explorer ved at lukke den fra den røde 'X'-knap i øverste højre hjørne, og start den igen.
Fjern push-meddelelser fra dine browsere
Sluk for push-meddelelser fra Google Chrome
Sådan deaktiveres push-meddelelser fra Google Chrome-browseren, Følg nedenstående trin:
Trin 1: Gå til Indstillinger i Chrome.
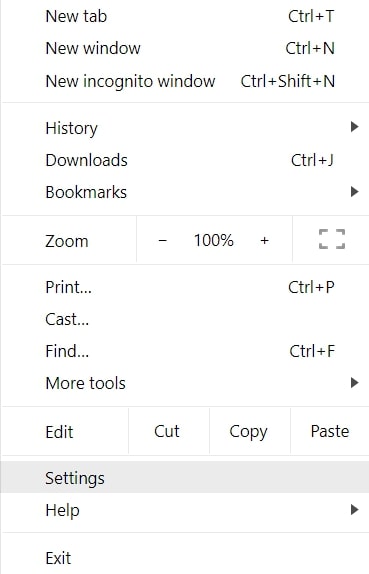
Trin 2: I Indstillinger, Vælg "Avancerede indstillinger":
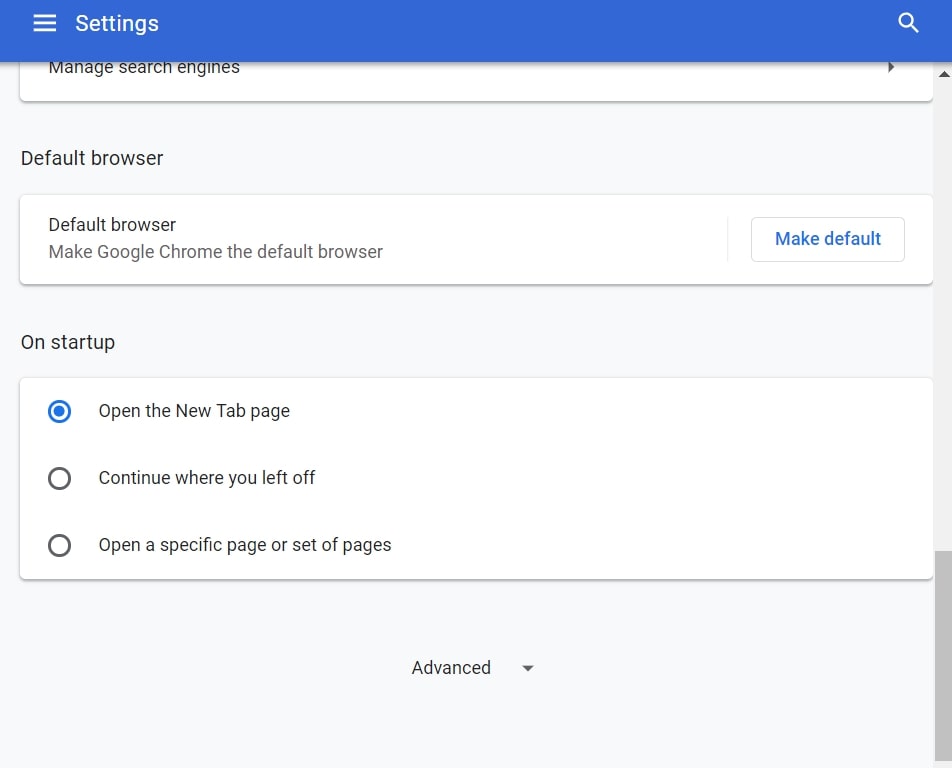
Trin 3: Klik på “Indstillinger for indhold":
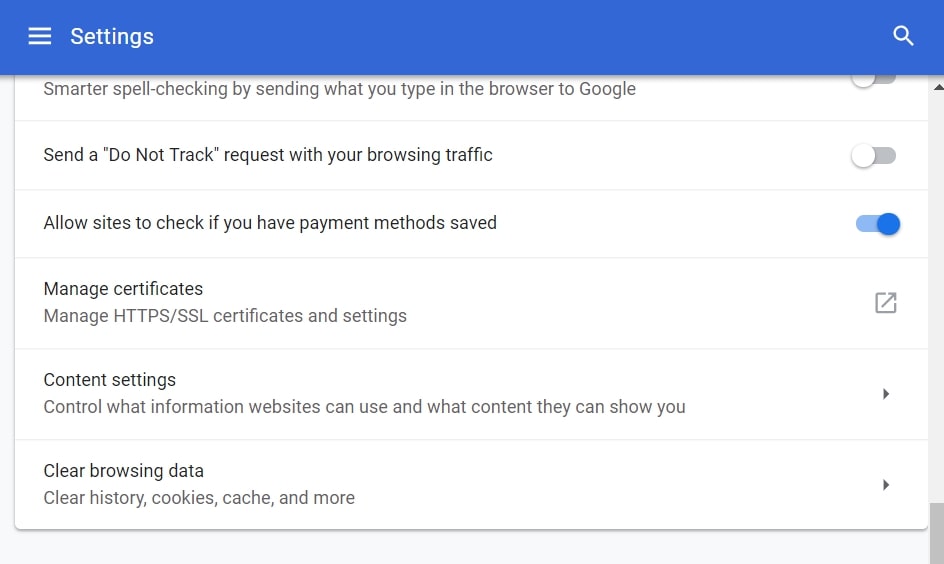
Trin 4: Åbn “underretninger":
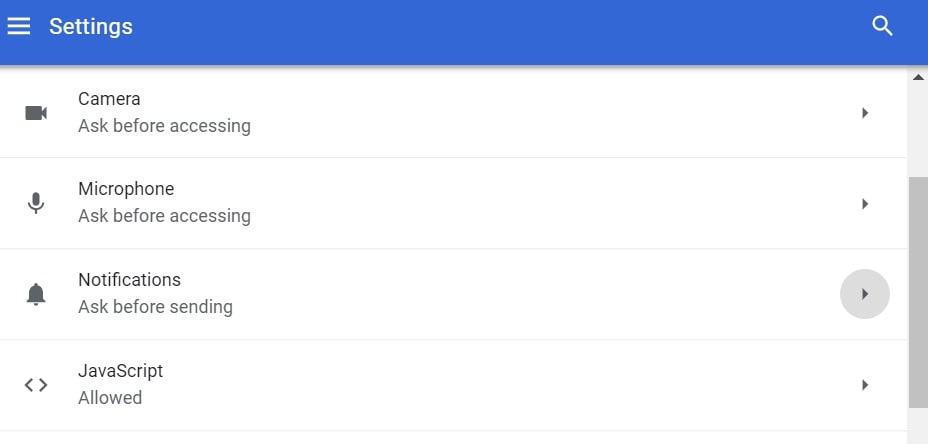
Trin 5: Klik på de tre prikker, og vælg Bloker, Rediger eller fjern muligheder:

Fjern Push Notifications på Firefox
Trin 1: Gå til Firefox-indstillinger.
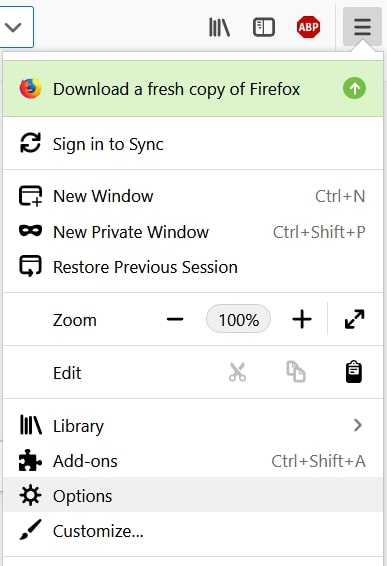
Trin 2: Gå til "Indstillinger", skriv "notifikationer" i søgefeltet, og klik "Indstillinger":
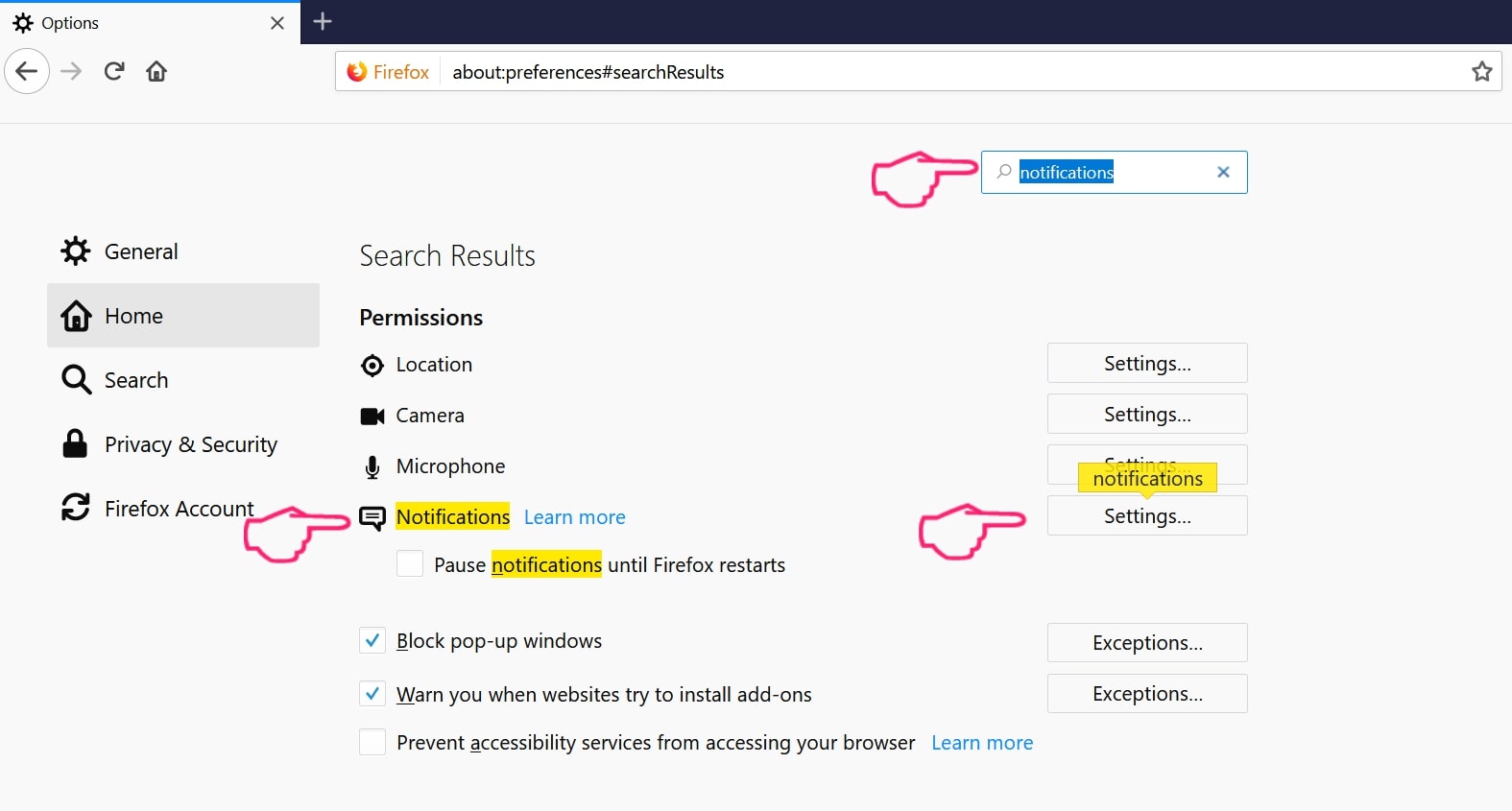
Trin 3: Klik på "Fjern" på ethvert websted, hvor du ønsker, at meddelelser er væk, og klik på "Gem ændringer"
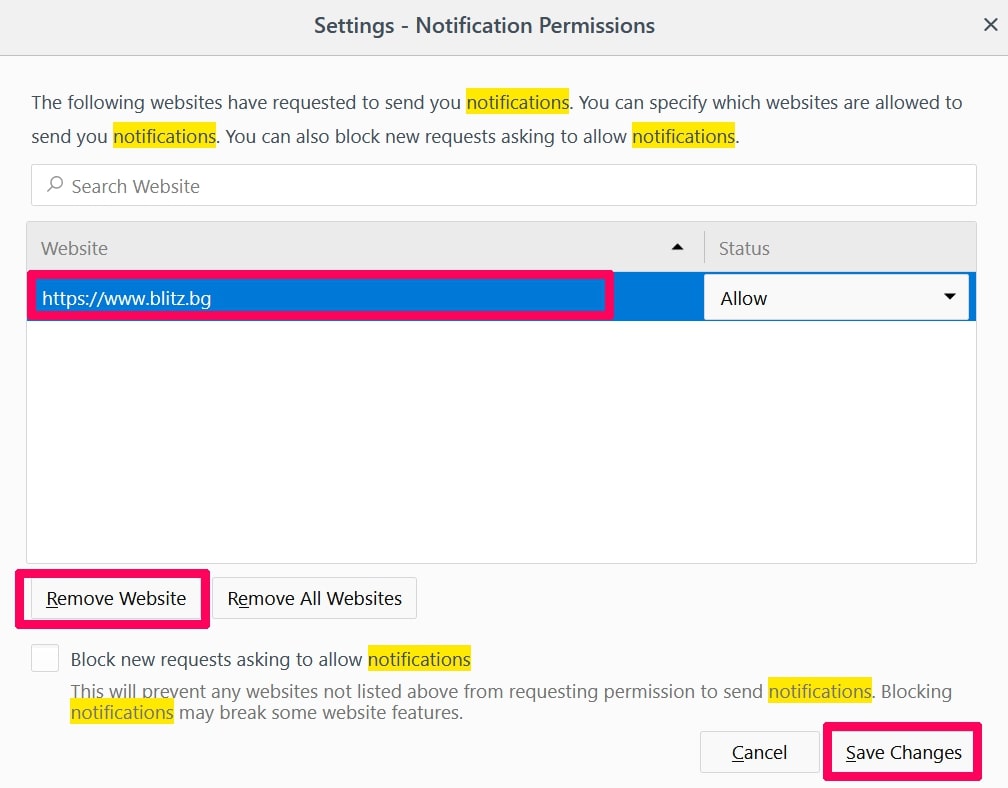
Stop push-meddelelser på Opera
Trin 1: I opera, presse ALT+P for at gå til Indstillinger.
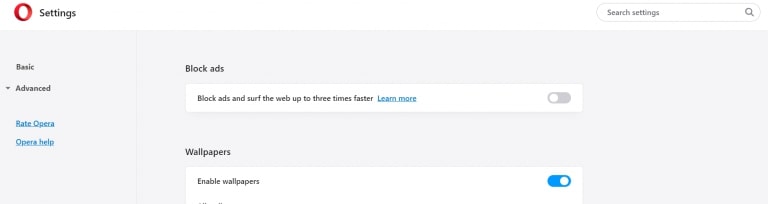
Trin 2: I Indstilling af søgning, skriv "Indhold" for at gå til Indholdsindstillinger.
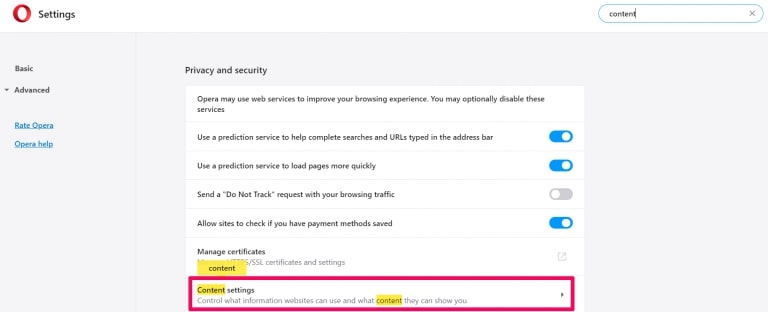
Trin 3: Åbn underretninger:
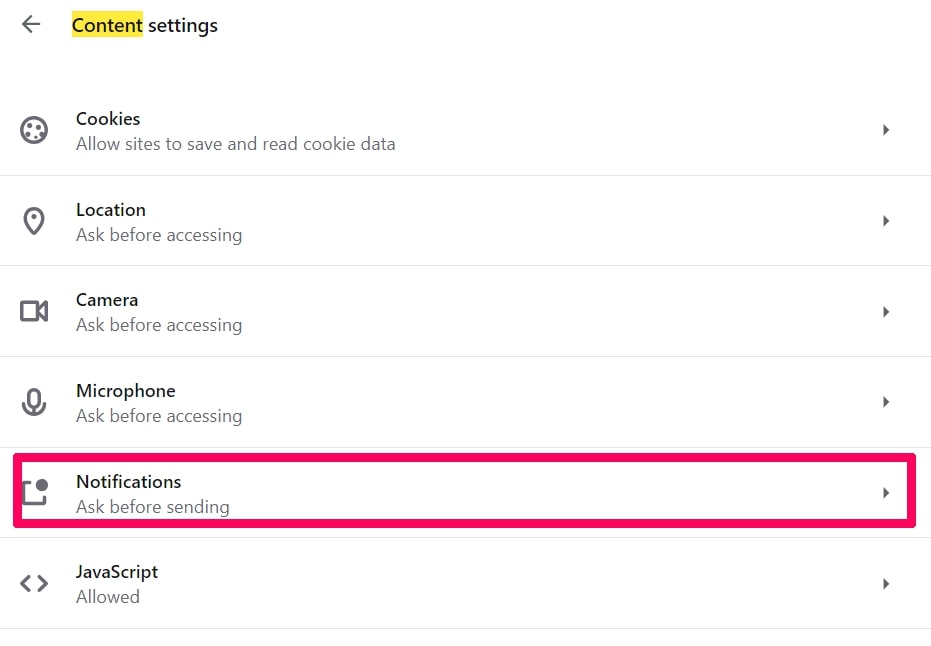
Trin 4: Gør det samme som du gjorde med Google Chrome (forklaret nedenfor):
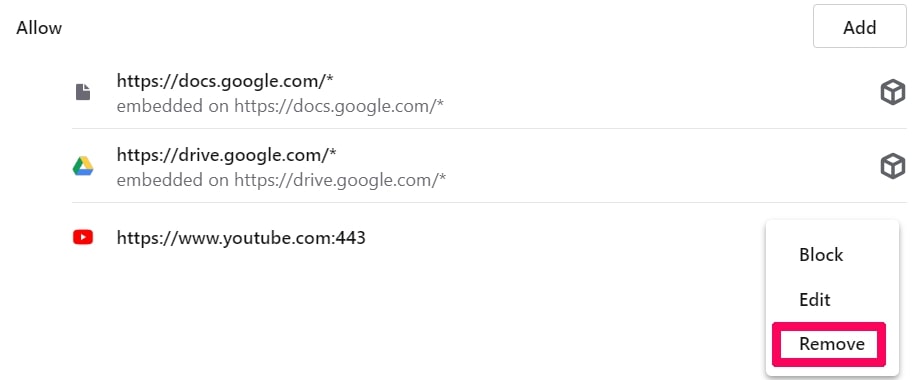
Fjern Push-underretninger på Safari
Trin 1: Åbn Safari-indstillinger.
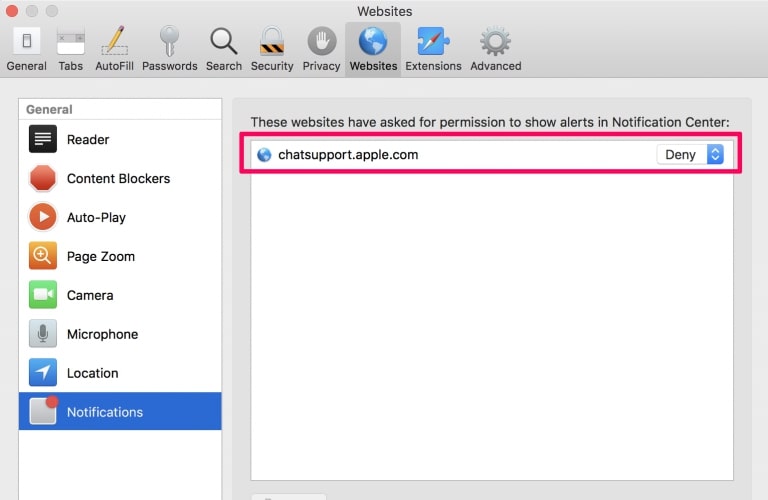
Trin 2: Vælg det domæne, hvorfra du kan lide pop-op-pop op, og skift til "Nægte" fra "Give lov til".
-FAQ
Hvad er ?
Truslen er adware eller browser omdirigering virus.
Det kan gøre din computer langsommere og vise reklamer. Hovedideen er, at dine oplysninger sandsynligvis bliver stjålet, eller at der vises flere annoncer på din enhed.
Skaberne af sådanne uønskede apps arbejder med ordninger for betaling pr. Klik for at få din computer til at besøge risikable eller forskellige typer websteder, der kan generere dem midler. Dette er grunden til, at de ikke engang er ligeglade med, hvilke typer websteder der vises på annoncerne. Dette gør deres uønskede software indirekte risikabelt for dit operativsystem.
Hvad er symptomerne på ?
Der er flere symptomer at se efter, når denne særlige trussel og også uønskede apps generelt er aktive:
Symptom #1: Din computer kan blive langsom og generelt have dårlig ydeevne.
Symptom #2: Du har værktøjslinjer, tilføjelser eller udvidelser på dine webbrowsere, som du ikke kan huske at have tilføjet.
Symptom #3: Du ser alle typer annoncer, som annoncesupporterede søgeresultater, pop op-vinduer og omdirigeringer vises tilfældigt.
Symptom #4: Du ser installerede apps på din Mac køre automatisk, og du kan ikke huske at have installeret dem.
Symptom #5: Du ser mistænkelige processer køre i din Jobliste.
Hvis du ser et eller flere af disse symptomer, så anbefaler sikkerhedseksperter, at du tjekker din computer for virus.
Hvilke typer uønskede programmer findes der?
Ifølge de fleste malware-forskere og cybersikkerhedseksperter, de trusler, der i øjeblikket kan påvirke din enhed, kan være useriøs antivirus-software, adware, browser hijackers, klikkere, falske optimizere og enhver form for PUP'er.
Hvad skal jeg gøre, hvis jeg har en "virus" lignende ?
Med få enkle handlinger. Først og fremmest, det er bydende nødvendigt, at du følger disse trin:
Trin 1: Find en sikker computer og tilslut det til et andet netværk, ikke den, som din Mac blev inficeret i.
Trin 2: Skift alle dine passwords, fra dine e-mail-adgangskoder.
Trin 3: Aktiver to-faktor-autentificering til beskyttelse af dine vigtige konti.
Trin 4: Ring til din bank til ændre dine kreditkortoplysninger (hemmelig kode, etc.) hvis du har gemt dit kreditkort til nethandel eller har lavet online aktiviteter med dit kort.
Trin 5: Sørg for at ring til din internetudbyder (Internetudbyder eller operatør) og bed dem om at ændre din IP-adresse.
Trin 6: Skift din Wi-Fi-adgangskode.
Trin 7: (Valgfri): Sørg for at scanne alle enheder, der er tilsluttet dit netværk for vira, og gentag disse trin for dem, hvis de er berørt.
Trin 8: Installer anti-malware software med realtidsbeskyttelse på alle enheder, du har.
Trin 9: Prøv ikke at downloade software fra websteder, du ikke ved noget om, og hold dig væk fra websteder med lav omdømme i almindelighed.
Hvis du følger disse anbefalinger, dit netværk og alle enheder bliver betydeligt mere sikre mod enhver trussel eller informationsinvasiv software og også være virusfri og beskyttet i fremtiden.
Hvordan virker?
Når det er installeret, kan indsamle data ved brug af trackere. Disse data handler om dine web-browsing-vaner, såsom de websteder, du besøger, og de søgetermer, du bruger. Det bruges derefter til at målrette dig med annoncer eller til at sælge dine oplysninger til tredjeparter.
kan også download anden skadelig software til din computer, såsom virus og spyware, som kan bruges til at stjæle dine personlige oplysninger og vise risikable annoncer, der kan omdirigere til virussider eller svindel.
Er Malware?
Sandheden er, at PUP'er (adware, browser hijackers) er ikke vira, men kan være lige så farligt da de muligvis viser dig og omdirigerer dig til malware-websteder og svindelsider.
Mange sikkerhedseksperter klassificerer potentielt uønskede programmer som malware. Dette er på grund af de uønskede virkninger, som PUP'er kan forårsage, såsom at vise påtrængende annoncer og indsamle brugerdata uden brugerens viden eller samtykke.
Om forskningen
Indholdet udgiver vi på SensorsTechForum.com, denne vejledning til fjernelse medfølger, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed for at hjælpe dig med at fjerne det specifikke, adware-relateret problem, og gendan din browser og computersystem.
Hvordan foretog vi undersøgelsen vedr ?
Bemærk venligst, at vores forskning er baseret på uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om den seneste malware, adware, og browser hijacker definitioner.
Endvidere, forskningen bag truslen bakkes op med VirusTotal.
For bedre at forstå denne online trussel, Se venligst følgende artikler, som giver kyndige detaljer.




Stjæle penge opmærksomhed.. Jeg har en spærret konto med 500 euro på plads af 6 måneder!!! Ingen besvarer ikke-eksisterende bistand!!!