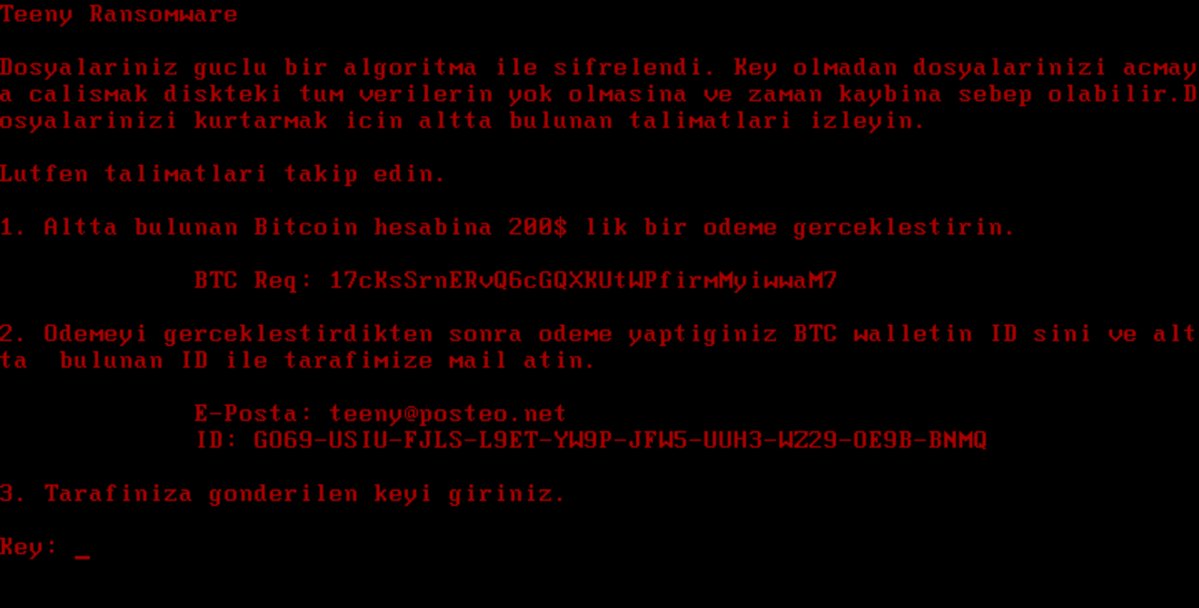
Cet article va vous aider à enlever Teeny Ransomware. Suivez les instructions de suppression ransomware prévues à la fin de l'article.
Teeny Ransomware est celui qui crypte votre enregistrement de démarrage principal (MBR) avec et exige de l'argent comme rançon pour le restaurer. La Teeny Ransomware laissera des instructions ransomware sous forme de fichier texte. Continuez à lire l'article et voir comment vous pourriez essayer de récupérer potentiellement certains de vos fichiers verrouillés et les données.

Menace Résumé
| Nom | Teeny ransomware |
| Type | Ransomware, Cryptovirus |
| brève description | Le ransomware crypte le master boot record (MBR) sur votre système informatique et exige une rançon à payer pour les récupérer prétendument. |
| Symptômes | Le ransomware va chiffrer vos fichiers et laisser une note de rançon avec les instructions de paiement. |
| Méthode de distribution | spams, Email Attachments |
| Detection Tool |
Voir si votre système a été affecté par des logiciels malveillants
Télécharger
Malware Removal Tool
|
Expérience utilisateur | Rejoignez notre Forum pour discuter du ransomware Teeny. |
| Outil de récupération de données | Windows Data Recovery Stellar Phoenix Avis! Ce produit numérise vos secteurs d'entraînement pour récupérer des fichiers perdus et il ne peut pas récupérer 100% des fichiers cryptés, mais seulement quelques-uns d'entre eux, en fonction de la situation et si oui ou non vous avez reformaté votre lecteur. |

Teeny Ransomware - Techniques de distribution
Le ransomware Teeny peut être distribué en utilisant une variété de mécanismes, les échantillons capturés sont très faibles afin de déterminer quelle est la méthode principale.
Habituellement, les menaces de ransomware comme celle-ci sont envoyées via email messages de phishing dans lequel les échantillons peuvent être directement attachés ou liés. Le contenu du corps peut servir différents types de contenu: pop-ups, redirections, images qui, lorsqu'elles interagissent, peuvent entraîner une infection virale.
Une stratégie similaire est lorsque les criminels utilisent sites malveillants qui crée de fausses copies d'entreprises bien connues, services et pages de destination. Ils sont généralement hébergés sur des noms de domaine similaires à ceux d'origine - si les utilisateurs saisissent mal une adresse donnée, ils peuvent atterrir sur un faux copieur sans s'en apercevoir.. Dans de nombreux exemples, une conception Web similaire et même des certificats de sécurité sont mis en œuvre.
L'un des moyens les plus courants de diffuser les ransomwares consiste à intégrer le script d'installation dans les fichiers de l'opérateur - il existe deux types principaux:
- Les installateurs d'application - Les instructions d'installation du rançongiciel Teeny peuvent être intégrées dans les fichiers de configuration de logiciels populaires qui sont souvent téléchargés et installés par les utilisateurs finaux. Les exemples incluent des utilitaires système, productivité et suites bureautiques et même jeux. Dès que les exécutables sont exécutés, le ransomware Teeny sera installé.
- fichiers document - Le script d'installation du virus peut être placé dans des documents de tous types courants: feuilles de calcul, présentations, bases de données et des fichiers texte. Quand ils sont ouverts, un cadre de notification sera généré demandant aux victimes d'activer les macros intégrées afin de visualiser le fichier. Si cela est fait, l'installation sera déclenchée.
Ces supports de charge utile peuvent être répartis à l'aide de réseaux de partage de fichiers tels que BitTorrent qui sont souvent utilisés pour diffuser à la fois du contenu pirate et légitime. Les programmes d'installation et les fichiers de virus infectés sont les variantes les plus courantes pouvant être acquises à partir des trackers.
Le ransomware Teeny peut également être diffusé via plugins, également connu sous pirates de l'air. Ils sont de nature malveillante et sont téléchargés dans les référentiels pertinents avec les avis des utilisateurs et les informations d'identification du développeur.. Les descriptions offriront de nouvelles fonctions et des améliorations de performances mais en réalité seul le mauvais code sera injecté.

Teeny Ransomware - Analyse détaillée
Les échantillons actuellement capturés associés à la menace de ransomware Teeny sont très peu nombreux, ce qui suggère que la campagne d'attaque initiale n'est pas importante.. Il est possible qu'il s'agisse d'une version de test précoce ou d'une version de développement car il n'y a pas de modules disponibles en plus du moteur de ransomware. Aucun code n'a été trouvé provenant des célèbres familles de logiciels malveillants, suggérant également que le code a été développé par les attaquants eux-mêmes..
Il est possible que les futures versions regroupent des ajouts populaires tels que les composants suivants:
- Manipulation des options de démarrage - En reconfigurant les options de démarrage par clé, fichiers de configuration et paramètres système, le ransomware Teeny peut être démarré à chaque fois que l'ordinateur est mis sous tension. Cela peut rendre les guides de récupération manuelle de l'utilisateur non fonctionnels car l'accès aux options de récupération peut être bloqué.
- Informations vol - Le moteur peut être configuré pour analyser le contenu du disque dur local pour les données d'identification de la machine et les informations personnelles de l'utilisateur. Ceci est fait afin de générer un ID d'ordinateur unique qui peut différencier tous les ordinateurs infectés. Les informations utilisateur collectées peuvent exposer directement leur identité en recherchant leur nom, adresse, numéro de téléphone, intérêts et même informations d'identification de compte stockées - combinaisons de noms d'utilisateur, mots de passe et adresses e-mail.
- Modifications du Registre Windows - En accédant et en modifiant le registre Windows, le moteur antivirus peut causer de graves problèmes de stabilité. La manipulation des chaînes utilisées par les services du système d'exploitation et les applications tierces peut entraîner des arrêts inattendus et des erreurs.
- Livraison Payload supplémentaires - Cette infection peut être utilisée pour charger d'autres menaces sur les machines compromises.
- contournement de la sécurité - Le ransomware Teeny peut rechercher les applications de sécurité installées et les désactiver. Cela inclut les programmes anti-virus, environnements de débogage et bac à sable, les pare-feu et des hôtes de machines virtuelles.
Les futures versions du ransomware Teeny peuvent également être mises à niveau avec d'autres options.

Teeny Ransomware - Processus de cryptage
Dès que tous les modules précédents seront terminés, le moteur de ransomware sera démarré. Au lieu de traiter les fichiers utilisateur, il cryptera l'enregistrement de démarrage principal (MBR) et faire chanter les victimes pour qu'elles leur paient des frais de décryptage. Le message est écrit en turc ce qui nous fait croire qu'il provient de ce pays. Les versions futures peuvent également chiffrer les données utilisateur selon une liste intégrée d'extensions de type de fichier cible.

Supprimer Teeny Ransomware et essayer de restaurer les données
Si votre ordinateur a été infecté par le Minuscule virus ransomware, vous devriez avoir un peu d'expérience dans l'élimination des logiciels malveillants. Vous devriez vous débarrasser de cette ransomware le plus rapidement possible avant qu'il puisse avoir la chance de se propager plus loin et infecter d'autres ordinateurs. Vous devez retirer le ransomware et suivez le guide d'instructions étape par étape ci-dessous.
- Étape 1
- Étape 2
- Étape 3
- Étape 4
- Étape 5
Étape 1: Rechercher les ransomwares Teeny avec SpyHunter Anti-Malware Tool



Suppression automatique des rançongiciels - Guide vidéo
Étape 2: Uninstall Teeny ransomware and related malware from Windows
Voici une méthode en quelques étapes simples qui devraient pouvoir désinstaller la plupart des programmes. Peu importe si vous utilisez Windows 10, 8, 7, Vista ou XP, ces mesures seront faire le travail. Faire glisser le programme ou de son dossier à la corbeille peut être un très mauvaise décision. Si vous faites cela, des morceaux du programme sont laissés, et qui peut conduire à un travail instable de votre PC, erreurs avec les associations de types de fichiers et d'autres activités désagréables. La bonne façon d'obtenir un programme sur votre ordinateur est de le désinstaller. Pour ce faire,:


 Suivez les instructions ci-dessus et vous supprimerez avec succès la plupart des programmes indésirables et malveillants.
Suivez les instructions ci-dessus et vous supprimerez avec succès la plupart des programmes indésirables et malveillants.
Étape 3: Nettoyer les registres, créé par Teeny ransomware sur votre ordinateur.
Les registres généralement ciblés des machines Windows sont les suivantes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Vous pouvez y accéder en ouvrant l'éditeur de Registre Windows et la suppression de toutes les valeurs, créé par Teeny ransomware là-bas. Cela peut se produire en suivant les étapes ci-dessous:


 Pointe: Pour trouver une valeur créée virus, vous pouvez faire un clic droit dessus et cliquez "Modifier" pour voir quel fichier il est configuré pour exécuter. Si cela est l'emplacement du fichier de virus, supprimer la valeur.
Pointe: Pour trouver une valeur créée virus, vous pouvez faire un clic droit dessus et cliquez "Modifier" pour voir quel fichier il est configuré pour exécuter. Si cela est l'emplacement du fichier de virus, supprimer la valeur.
Avant de commencer "Étape 4", S'il vous plaît démarrer en mode normal, dans le cas où vous êtes actuellement en mode sans échec.
Cela vous permettra d'installer et utilisation SpyHunter 5 avec succès.
Étape 4: Démarrez votre PC en mode sans échec pour isoler et supprimer le ransomware Teeny





Étape 5: Essayez de restaurer des fichiers cryptés par Teeny ransomware.
Méthode 1: Utilisez STOP Decrypter par Emsisoft.
Toutes les variantes de ce ransomware peuvent être décryptées gratuitement, mais nous avons ajouté le décrypteur utilisé par des chercheurs qui est souvent mis à jour avec les variantes qui finissent par devenir décryptés. Vous pouvez essayer de décrypter vos fichiers en utilisant les instructions ci-dessous, mais si elles ne fonctionnent pas, puis, malheureusement, votre variante du virus ransomware n'est pas déchiffrable.
Suivez les instructions ci-dessous pour utiliser le décrypteur Emsisoft et décrypter vos fichiers gratuitement. Tu peux télécharger l'outil de décryptage Emsisoft liée ici puis suivez les étapes indiquées ci-dessous:
1 Clic-droit sur le décrypteur et cliquez sur Exécuter en tant qu'administrateur comme indiqué ci-dessous:
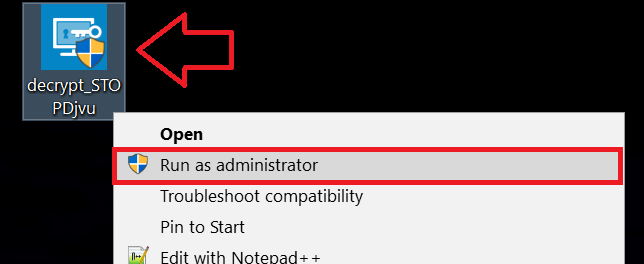
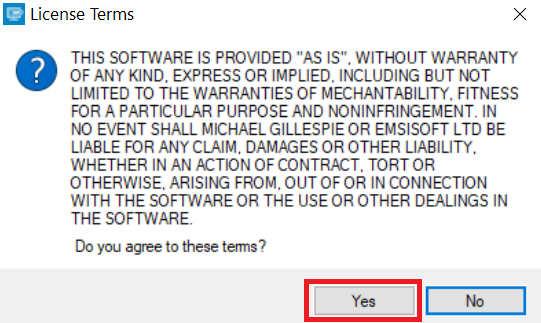
2. D'accord avec les termes de la licence:
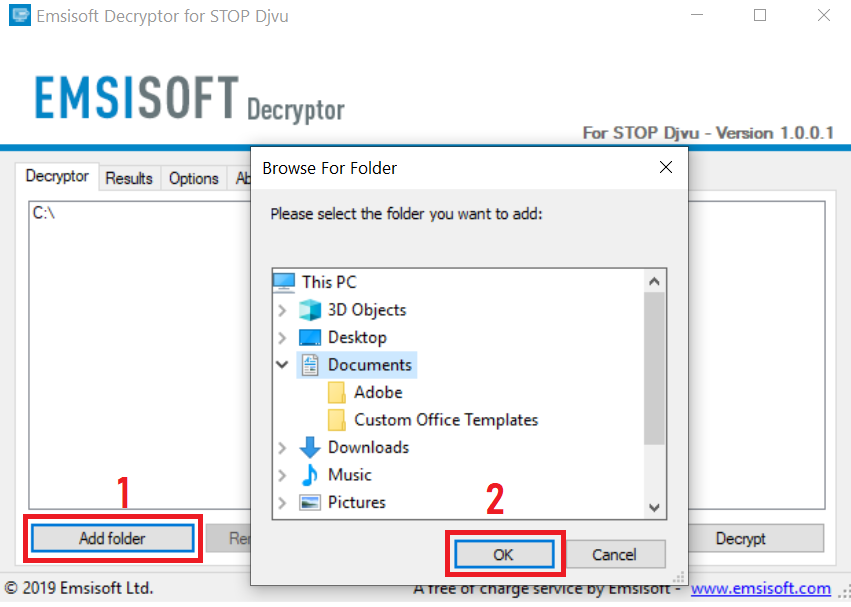
3. Cliquer sur "Ajouter le dossier" puis ajoutez les dossiers où vous voulez que les fichiers décryptés comme indiqué ci-dessous:
4. Cliquer sur "Décrypter" et attendez que vos fichiers à décoder.
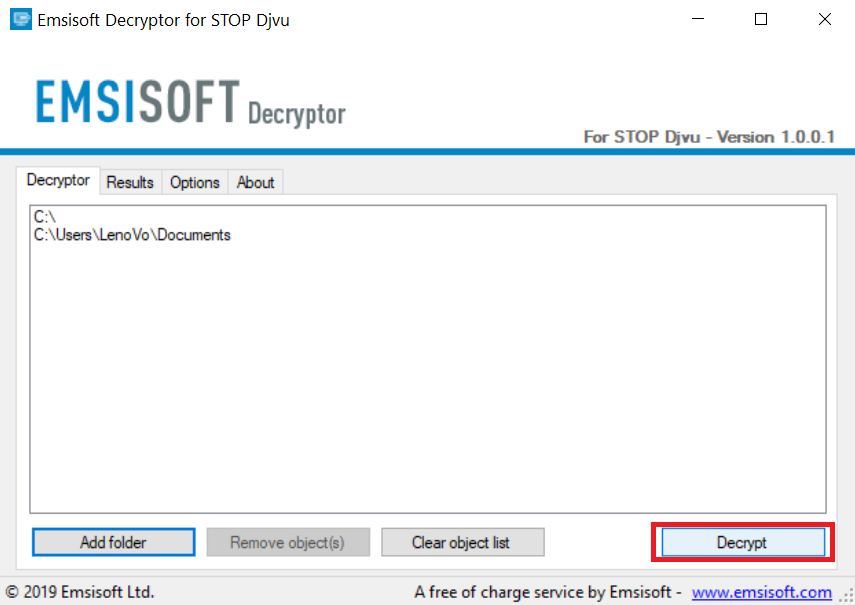
Note: Crédit pour le décrypteur va EMSISOFT chercheurs qui ont fait la percée avec ce virus.
Méthode 2: Utiliser un logiciel de récupération de données
Les infections de ransomware et Teeny ransomware visent à crypter vos fichiers à l'aide d'un algorithme de cryptage qui peut être très difficile à décrypter. Voilà pourquoi nous avons proposé une méthode de récupération de données qui peuvent vous aider à faire le tour de décryptage direct et essayer de restaurer vos fichiers. Gardez à l'esprit que cette méthode ne peut pas être 100% efficace, mais peut aussi vous aider un peu ou beaucoup dans différentes situations.
Cliquez simplement sur le lien et sur les menus du site en haut, choisir Récupération de données - Assistant de récupération de données pour Windows ou Mac (en fonction de votre système d'exploitation), puis téléchargez et exécutez l'outil.
Teeny ransomware-FAQ
What is Teeny ransomware Ransomware?
Teeny ransomware est un ransomware infection - les logiciels malveillants qui pénètrent silencieusement dans votre ordinateur et bloquent l'accès à l'ordinateur lui-même ou chiffrent vos fichiers.
De nombreux virus rançongiciels utilisent des algorithmes de cryptage sophistiqués pour rendre vos fichiers inaccessibles. Le but des infections par rançongiciels est d'exiger que vous payiez un paiement de rançon pour avoir accès à vos fichiers..
What Does Teeny ransomware Ransomware Do?
Les ransomwares en général sont un logiciel malveillant qui est conçu pour bloquer l'accès à votre ordinateur ou à vos fichiers jusqu'à ce qu'une rançon soit payée.
Les virus Ransomware peuvent également endommager votre système, corrompre les données et supprimer des fichiers, entraînant la perte permanente de fichiers importants.
How Does Teeny ransomware Infect?
De plusieurs façons: Teeny ransomware Ransomware infecte les ordinateurs en étant envoyé par e-mails de phishing, contenant un virus attaché. Cette pièce jointe est généralement masquée comme un document important, comme une facture, un document bancaire ou encore un billet d'avion et cela semble très convaincant aux utilisateurs.
Another way you may become a victim of Teeny ransomware is if you télécharger un faux installateur, crack ou correctif provenant d'un site Web de mauvaise réputation ou si vous cliquez sur un lien de virus. De nombreux utilisateurs signalent avoir contracté un ransomware en téléchargeant des torrents.
How to Open .Teeny ransomware files?
Toi can't sans décrypteur. À ce point, la .Teeny ransomware les fichiers sont crypté. Vous ne pouvez les ouvrir qu'une fois qu'ils ont été déchiffrés à l'aide d'une clé de déchiffrement spécifique à un algorithme particulier..
Que faire si un décrypteur ne fonctionne pas?
Ne panique pas, et sauvegarder les fichiers. Si un déchiffreur n'a pas déchiffré votre .Teeny ransomware fichiers avec succès, alors ne désespérez pas, parce que ce virus est encore nouveau.
Puis-je restaurer ".Teeny ransomware" dossiers?
Oui, parfois les fichiers peuvent être restaurés. Nous avons proposé plusieurs méthodes de récupération de fichiers cela pourrait fonctionner si vous souhaitez restaurer .Teeny ransomware fichiers.
Ces méthodes ne sont en aucun cas 100% garanti que vous pourrez récupérer vos fichiers. Mais si vous avez une sauvegarde, vos chances de succès sont bien plus grandes.
How To Get Rid of Teeny ransomware Virus?
Le moyen le plus sûr et le plus efficace pour supprimer cette infection par rançongiciel est d'utiliser un programme anti-malware professionnel.
Il recherchera et localisera le ransomware Teeny ransomware, puis le supprimera sans causer de dommages supplémentaires à vos fichiers importants du ransomware .Teeny.
Puis-je signaler un ransomware aux autorités?
Au cas où votre ordinateur serait infecté par une infection ransomware, vous pouvez le signaler aux services de police locaux. Il peut aider les autorités du monde entier à suivre et à déterminer les auteurs du virus qui a infecté votre ordinateur.
Dessous, nous avons préparé une liste de sites Web gouvernementaux, où vous pouvez déposer un rapport au cas où vous seriez victime d'un cybercriminalité:
Autorités de cybersécurité, responsable de la gestion des rapports d'attaque de ransomware dans différentes régions du monde:
Allemagne - Portail officiel de la police allemande
États Unis - IC3 Centre de plaintes contre la criminalité sur Internet
Royaume-Uni - Action Fraud Police
France - Ministère de l'Intérieur
Italie - Police d'État
Espagne - Police nationale
Pays-Bas - Forces de l'ordre
Pologne - Police
le Portugal - Police judiciaire
Grèce - Unité de la cybercriminalité (Police hellénique)
Inde - Police de Mumbai - Cellule d'enquête sur la cybercriminalité
Australie - Australian High Tech Crime Center
Les rapports peuvent recevoir une réponse dans des délais différents, selon vos autorités locales.
Pouvez-vous empêcher les ransomwares de crypter vos fichiers?
Oui, vous pouvez empêcher les ransomwares. La meilleure façon de le faire est de vous assurer que votre système informatique est mis à jour avec les derniers correctifs de sécurité., utiliser un programme anti-malware réputé et pare-feu, sauvegardez fréquemment vos fichiers importants, et évitez de cliquer sur liens malveillants ou télécharger des fichiers inconnus.
Can Teeny ransomware Ransomware Steal Your Data?
Oui, dans la plupart des cas, un rançongiciel va voler vos informations. It is a form of malware that steals data from a user's computer, le crypte, puis demande une rançon pour le décrypter.
Dans de nombreux cas,, la auteurs de logiciels malveillants ou les attaquants menaceront de supprimer les données ou le publier en ligne à moins que la rançon est payée.
Un ransomware peut-il infecter le WiFi?
Oui, un ransomware peut infecter les réseaux WiFi, car des acteurs malveillants peuvent l'utiliser pour prendre le contrôle du réseau, voler des données confidentielles, et verrouiller les utilisateurs. Si une attaque de ransomware réussit, cela pourrait entraîner une perte de service et/ou de données, et dans certains cas, pertes financières.
Dois-je payer un rançongiciel?
Aucun, vous ne devriez pas payer les extorqueurs de rançongiciels. Les payer ne fait qu'encourager les criminels et ne garantit pas que les fichiers ou les données seront restaurés. La meilleure approche consiste à disposer d'une sauvegarde sécurisée des données importantes et à être vigilant quant à la sécurité en premier lieu.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, les pirates peuvent toujours avoir accès à votre ordinateur, données, ou des fichiers et peut continuer à menacer de les exposer ou de les supprimer, ou même les utiliser pour commettre des cybercrimes. Dans certains cas,, ils peuvent même continuer à exiger des paiements de rançon supplémentaires.
Une attaque de ransomware peut-elle être détectée?
Oui, les rançongiciels peuvent être détectés. Logiciel anti-malware et autres outils de sécurité avancés peut détecter les ransomwares et alerter l'utilisateur quand il est présent sur une machine.
Il est important de se tenir au courant des dernières mesures de sécurité et de maintenir les logiciels de sécurité à jour pour s'assurer que les ransomwares peuvent être détectés et empêchés..
Les criminels du ransomware se font-ils prendre?
Oui, les criminels rançongiciels se font prendre. Les organismes d'application de la loi, comme le FBI, Interpol et d'autres ont réussi à traquer et à poursuivre les criminels de ransomware aux États-Unis et dans d'autres pays.. Alors que les menaces de rançongiciels continuent d'augmenter, il en va de même pour l'activité d'application.
About the Teeny ransomware Research
Le contenu que nous publions sur SensorsTechForum.com, this Teeny ransomware how-to removal guide included, est le résultat de recherches approfondies, le travail acharné et le dévouement de notre équipe pour vous aider à supprimer les logiciels malveillants spécifiques et à restaurer vos fichiers cryptés.
Comment avons-nous mené la recherche sur ce ransomware?
Notre recherche est basée sur une enquête indépendante. Nous sommes en contact avec des chercheurs indépendants en sécurité, et en tant que tel, nous recevons des mises à jour quotidiennes sur les dernières définitions de logiciels malveillants et de ransomwares.
En outre, the research behind the Teeny ransomware ransomware threat is backed with VirusTotal et l' projet NoMoreRansom.
Pour mieux comprendre la menace des ransomwares, veuillez vous référer aux articles suivants qui fournissent des détails bien informés.
En tant que site dédié à fournir des instructions de suppression gratuites pour les ransomwares et les malwares depuis 2014, La recommandation de SensorsTechForum est de ne prêter attention qu'aux sources fiables.
Comment reconnaître des sources fiables:
- Vérifiez toujours "À propos de nous" page web.
- Profil du créateur de contenu.
- Assurez-vous que de vraies personnes sont derrière le site et non de faux noms et profils.
- Vérifiez Facebook, Profils personnels LinkedIn et Twitter.