.Nenhum vírus de arquivo vicioso, também conhecido como Sem ransomware vicioso, é uma infecção de ransomware que criptografa os arquivos da vítima e anexa o .Extensão HakunaMatata assim que a criptografia for finalizada. O criptovírus exibirá uma nota de resgate contendo instruções sobre o processo de pagamento. Como sempre, o resgate é exigido em Bitcoin, e desta vez é relatado ser 0.5 Bitcoin.

Resumo ameaça
| Nome | .Nenhum vírus violento de arquivo |
| Tipo | ransomware, vírus de arquivo |
| Pequena descrição | O vírus de arquivo criptografa arquivos no computador da vítima, provavelmente usando criptografia RSA-2048 e AES-256 bits. |
| Os sintomas | O vírus de arquivo criptografará os arquivos de destino e anexará a extensão .HakunaMatata a cada um deles quando o processo de criptografia for concluído. |
| distribuição Método | Os e-mails de spam, Anexos de e-mail |
| Ferramenta de detecção |
Veja se o seu sistema foi afetado por malware
Baixar
Remoção de Malware Ferramenta
|
Experiência de usuário | Participe do nosso Fórum para discutir o vírus de arquivo .HakunaMatata. |
| Ferramenta de recuperação de dados | Windows Data Recovery por Stellar Phoenix Aviso prévio! Este produto verifica seus setores de unidade para recuperar arquivos perdidos e não pode recuperar 100% dos arquivos criptografados, mas apenas alguns deles, dependendo da situação e se você tem ou não reformatado a unidade. |
.Distribuição de vírus de arquivo HakunaMatata
O vírus do arquivo pode infectar o computador da vítima, dependendo de vários métodos. O arquivo de carga útil que contém o script malicioso provavelmente está espalhado online. O dropper de carga útil pode estar espalhado em sites de mídia social e redes de compartilhamento de arquivos. Também pode ser "empacotado" em pacotes de freeware. Para a segurança de seus próprios arquivos, é altamente recomendado que você não abra arquivos desconhecidos, incluindo anexos de e-mail.
.Descrição técnica do vírus de arquivo HakunaMatata
Lembre-se de que o .Nenhum vírus de arquivo vicioso pode alterar o registro do Windows para que se torne persistente. Podem ser adicionadas novas entradas de registro que iniciarão o vírus de arquivo automaticamente a cada reinicialização do sistema.
Assim que o processo de criptografia for concluído, o vírus ransomware exibirá uma nota de resgate na área de trabalho informando suas demandas, como valor do resgate e meios de pagamento. A pesquisa de segurança mostra que a nota de resgate está localizada em um arquivo denominado Recuperar arquivos yako.html. A palavra “yako” significa “seu” em Swahili.
Este é o texto da nota de resgate:
Os arquivos criptografados!
Todos os seus arquivos estão criptografia AES256-bit encrypted.Using e criptografia bits RSA-2048.
O que torna impossível recuperar os arquivos sem a chave privada correta.
Se você estiver interessado em obter é a chave e recuperar seus arquivos
Você deve proceder com os seguintes passos.
-
Para entrar em contato você deve usar o sistema Bitmessage,
Você pode baixar o software Bitmessage em https://bitmessage.org/
Após a instalação você deve enviar uma mensagem para o endereço
Bitmsg: BM-2cWcp ***
Se preferir, você pode enviar seus Bitmenssages de um navegador da web
Por meio da página https://bitmsg.me este é certamente o método mais prático!
Abaixo está um tutorial sobre como enviar bitmessage via navegador web: https://bitmsg.me/
1 B ° Abra no seu navegador o link
https://bitmsg.me/users/sign_up
Faça o cadastro inserindo nome e-mail e senha.
2 B ° Você deve confirmar o registro, retorne ao seu email e siga as instruções que foram enviadas.
3 B ° Voltar ao site entrar
https://bitmsg.me/users/sign_in
4 B ° Clique no botão Criar endereço aleatório.
5 B ° Clique no botão Nova massagem
6 B ° Enviando mensagem
Para: Insira o endereço: BM-2cWcp ***
Sujeito: Digite sua chave: afe299 ***
Menssage: Descreva o que você acha necessário
Clique no botão Enviar mensagem.
Sua mensagem será recebida e respondida o mais rápido possível!.
Enviar mensagem para: BM-2cWcp ***
Sua chave: afe299 ***
O resgate exigido pelos operadores do vírus de arquivo .HakunaMatata é 0.5 Bitcoin. Supostamente, os cibercriminosos enviariam a chave de descriptografia dos arquivos criptografados para que a vítima pudesse restaurá-los. Infelizmente, Mais frequentemente do que não, os cibercriminosos aceitam os pagamentos e nunca enviam a chave de descriptografia. É por isso que os pesquisadores de segurança nunca recomendam o pagamento do resgate. Em vez de, métodos alternativos de recuperação podem ser tentados.
Com relação às extensões de arquivo, o vírus de arquivo se destina, nenhuma informação está disponível ainda. O que se sabe é que os arquivos direcionados são criptografados com a extensão .HakunaMatata. De acordo com a nota de resgate, o algoritmo de criptografia aplicado pelo vírus é uma combinação de RSA de 2048 bits e AES de 256 bits.
por fim, infecções recentes de ransomware tendem a excluir as cópias de volume de sombra usando o comando this no prompt de comando:
→ vssadmin.exe excluir sombras / tudo / Silencioso
.Remoção e restauração de arquivos HakunaMatata File Virus
Se você é um usuário experiente, você pode tentar remover o vírus de arquivo seguindo as instruções do manual fornecidas abaixo. Em qualquer outro caso, usar um programa anti-malware é preferível.
- Degrau 1
- Degrau 2
- Degrau 3
- Degrau 4
- Degrau 5
Degrau 1: Verifique se há vírus de arquivo .HakunaMatata com a ferramenta Anti-Malware SpyHunter



Remoção automática de ransomware - Guia de Vídeo
Degrau 2: Uninstall .HakunaMatata File Virus and related malware from Windows
Aqui é um método em alguns passos simples que deve ser capaz de desinstalar a maioria dos programas. Não importa se você estiver usando o Windows 10, 8, 7, Vista ou XP, esses passos vai começar o trabalho feito. Arrastando o programa ou a sua pasta para a lixeira pode ser um muito má decisão. Se você fizer isso, pedaços e peças do programa são deixados para trás, e que pode levar a um trabalho instável do seu PC, erros com as associações de tipo de arquivo e outras atividades desagradáveis. A maneira correta de obter um programa fora de seu computador é para desinstalá-lo. Fazer isso:


 Siga as instruções acima e você excluirá com sucesso a maioria dos programas maliciosos e indesejados.
Siga as instruções acima e você excluirá com sucesso a maioria dos programas maliciosos e indesejados.
Degrau 3: Limpe quaisquer registros, criado por .HakunaMatata File Virus no seu computador.
Os registros normalmente alvo de máquinas Windows são os seguintes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Você pode acessá-los abrindo o editor de registro do Windows e excluir quaisquer valores, criado por .HakunaMatata File Virus lá. Isso pode acontecer, seguindo os passos abaixo:


 Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Antes de começar "Degrau 4", por favor Arrancar de novo para o modo Normal, no caso em que você está no Modo de Segurança.
Isto irá permitir-lhe instalar e uso SpyHunter 5 com sucesso.
Degrau 4: Inicialize seu PC no modo de segurança para isolar e remover .HakunaMatata File Virus





Degrau 5: Try to Restore Files Encrypted by .HakunaMatata File Virus.
Método 1: Use o STOP Decrypter da Emsisoft.
Nem todas as variantes deste ransomware pode ser descriptografado gratuitamente, mas nós adicionamos o decryptor utilizado por pesquisadores que é frequentemente atualizado com as variantes que se tornam, eventualmente descriptografado. Você pode tentar e descriptografar seus arquivos usando as instruções abaixo, mas se eles não funcionam, então, infelizmente, a sua variante do vírus ransomware não é decryptable.
Siga as instruções abaixo para usar o decrypter Emsisoft e descriptografar os arquivos de graça. Você pode baixar a ferramenta de decodificação Emsisoft ligados aqui e depois seguir os passos apresentados abaixo:
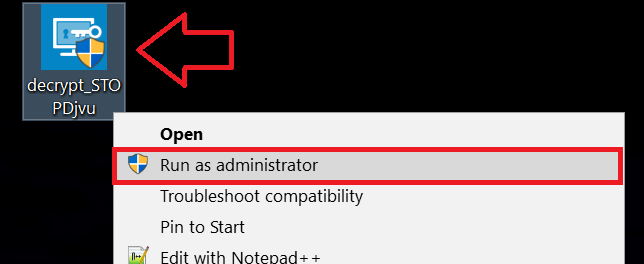
1 Botão direito do mouse na decrypter e clique em Executar como administrador como mostrado abaixo:
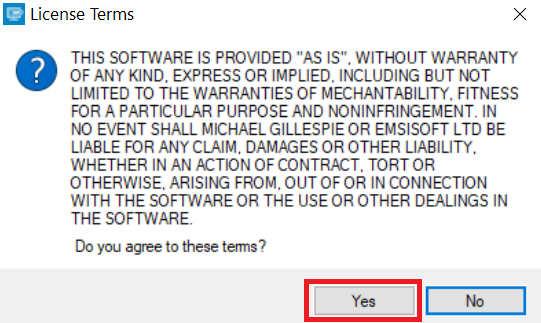
2. Concordo com os termos de licença:
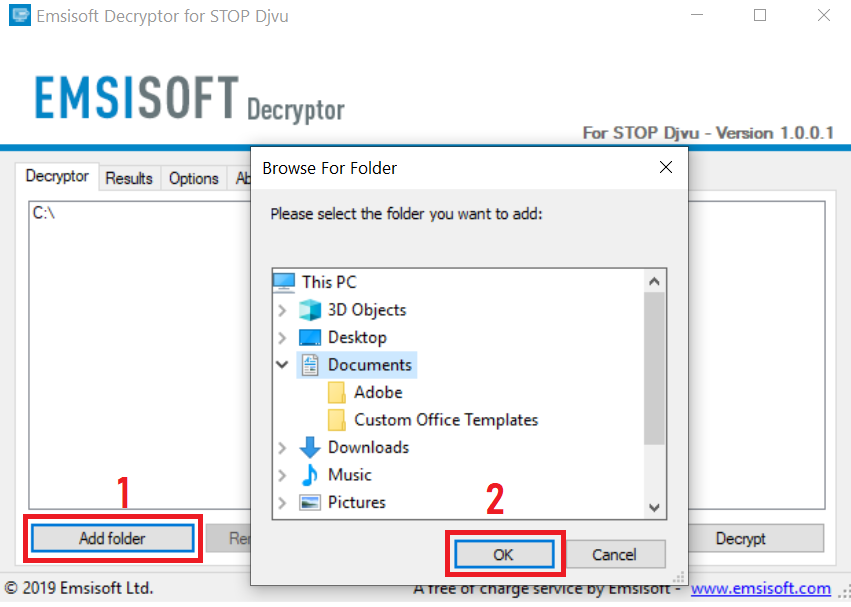
3. Clique em "Adicionar pasta" e em seguida, adicione as pastas onde deseja que os arquivos descriptografado como debaixo mostrado:
4. Clique em "Decrypt" e esperar por seus arquivos para ser decodificado.
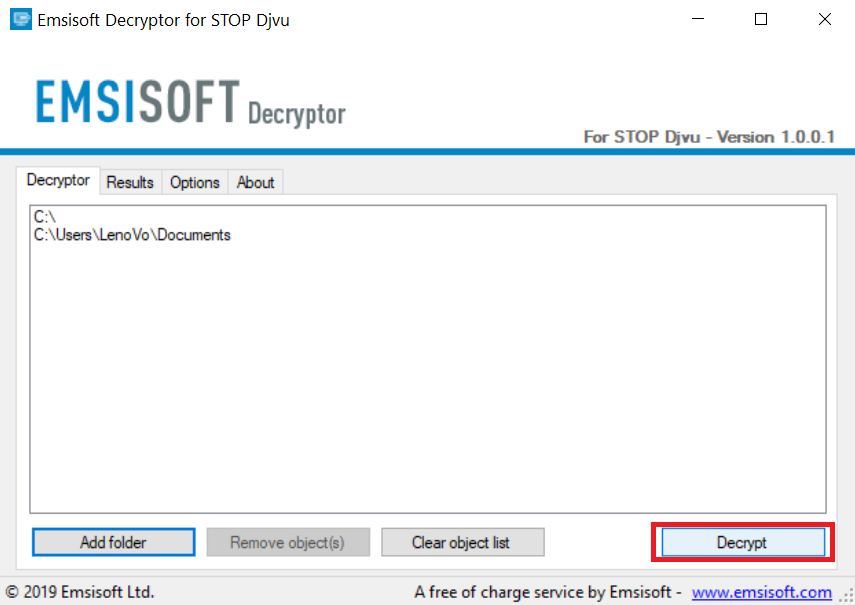
Nota: Crédito para o decryptor vai para pesquisadores Emsisoft que fizeram a descoberta com este vírus.
Método 2: Use software de recuperação de dados
Ransomware infections and .HakunaMatata File Virus aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. É por isso que sugeriram um método de recuperação de dados que podem ajudá-lo a ir descriptografia torno direta e tentar restaurar seus arquivos. Tenha em mente que este método pode não ser 100% eficaz, mas também pode ajudá-lo um pouco ou muito em situações diferentes.
Basta clicar no link e nos menus do site na parte superior, escolher Recuperação de dados - Assistente de Recuperação de Dados para Windows ou Mac (dependendo do seu SO), e depois baixe e execute a ferramenta.
.HakunaMatata File Virus-FAQ
What is .HakunaMatata File Virus Ransomware?
.HakunaMatata File Virus is a ransomware infecção - o software malicioso que entra no computador silenciosamente e bloqueia o acesso ao próprio computador ou criptografa seus arquivos.
Muitos vírus ransomware usam algoritmos de criptografia sofisticados para tornar seus arquivos inacessíveis. O objetivo das infecções por ransomware é exigir que você pague um pagamento por resgate para ter acesso aos seus arquivos de volta.
What Does .HakunaMatata File Virus Ransomware Do?
O ransomware em geral é um software malicioso que é projetado para bloquear o acesso ao seu computador ou arquivos até que um resgate seja pago.
Os vírus ransomware também podem danificar seu sistema, corromper dados e excluir arquivos, resultando na perda permanente de arquivos importantes.
How Does .HakunaMatata File Virus Infect?
Via several ways..HakunaMatata File Virus Ransomware infects computers by being sent através de e-mails de phishing, contendo anexo de vírus. Esse anexo geralmente é mascarado como um documento importante, gostar uma fatura, documento bancário ou até mesmo uma passagem de avião e parece muito convincente para os usuários.
Another way you may become a victim of .HakunaMatata File Virus is if you baixe um instalador falso, crack ou patch de um site de baixa reputação ou se você clicar em um link de vírus. Muitos usuários relatam ter recebido uma infecção por ransomware baixando torrents.
How to Open ..HakunaMatata File Virus files?
Vocês can't sem um descriptografador. Neste ponto, a ..Nenhum vírus violento de arquivo arquivos são criptografado. Você só pode abri-los depois de descriptografados usando uma chave de descriptografia específica para o algoritmo específico.
O que fazer se um descriptografador não funcionar?
Não entre em pânico, e faça backup dos arquivos. Se um decodificador não decifrar seu ..Nenhum vírus violento de arquivo arquivos com sucesso, então não se desespere, porque esse vírus ainda é novo.
posso restaurar "..Nenhum vírus violento de arquivo" arquivos?
sim, às vezes os arquivos podem ser restaurados. Sugerimos vários métodos de recuperação de arquivos isso poderia funcionar se você quiser restaurar ..Nenhum vírus violento de arquivo arquivos.
Esses métodos não são de forma alguma 100% garantido que você será capaz de recuperar seus arquivos. Mas se você tiver um backup, suas chances de sucesso são muito maiores.
How To Get Rid of .HakunaMatata File Virus Virus?
A maneira mais segura e eficiente de remover esta infecção por ransomware é o uso de um programa anti-malware profissional.
It will scan for and locate .HakunaMatata File Virus ransomware and then remove it without causing any additional harm to your important ..HakunaMatata File Virus files.
Posso denunciar ransomware às autoridades?
Caso seu computador tenha sido infectado por uma infecção de ransomware, você pode denunciá-lo aos departamentos de polícia locais. Ele pode ajudar as autoridades em todo o mundo a rastrear e determinar os autores do vírus que infectou seu computador.
Abaixo, preparamos uma lista com sites governamentais, onde você pode registrar uma denúncia caso seja vítima de um cibercrime:
Autoridades de segurança cibernética, responsável por lidar com relatórios de ataque de ransomware em diferentes regiões em todo o mundo:
Alemanha - Portal oficial da polícia alemã
Estados Unidos - IC3 Internet Crime Complaint Center
Reino Unido - Polícia de Fraude de Ação
França - Ministro do interior
Itália - Polícia Estadual
Espanha - Policia Nacional
Países Baixos - Aplicação da lei
Polônia - Polícia
Portugal - Polícia Judiciária
Grécia - Unidade de crime cibernético (Polícia Helênica)
Índia - Polícia de Mumbai - Célula de investigação do CyberCrime
Austrália - Centro de crime de alta tecnologia australiano
Os relatórios podem ser respondidos em prazos diferentes, dependendo das autoridades locais.
Você pode impedir que o ransomware criptografe seus arquivos?
sim, você pode prevenir o ransomware. A melhor maneira de fazer isso é garantir que o sistema do seu computador esteja atualizado com os patches de segurança mais recentes, use um programa anti-malware confiável e firewall, faça backup de seus arquivos importantes com frequência, e evite clicar em links maliciosos ou baixando arquivos desconhecidos.
Can .HakunaMatata File Virus Ransomware Steal Your Data?
sim, na maioria dos casos ransomware roubará suas informações. It is a form of malware that steals data from a user's computer, criptografa isso, e depois exige um resgate para descriptografá-lo.
Em muitos casos, a autores de malware ou invasores ameaçarão excluir os dados ou publicá-lo on-line a menos que o resgate seja pago.
O ransomware pode infectar WiFi?
sim, ransomware pode infectar redes WiFi, como agentes mal-intencionados podem usá-lo para obter o controle da rede, roubar dados confidenciais, e bloquear usuários. Se um ataque de ransomware for bem-sucedido, pode levar a uma perda de serviço e/ou dados, e em alguns casos, perdas financeiras.
Devo Pagar Ransomware?
Não, você não deve pagar extorsionários de ransomware. Pagá-los apenas incentiva os criminosos e não garante que os arquivos ou dados sejam restaurados. A melhor abordagem é ter um backup seguro de dados importantes e estar atento à segurança em primeiro lugar.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, os hackers ainda podem ter acesso ao seu computador, dados, ou arquivos e pode continuar ameaçando expô-los ou excluí-los, ou mesmo usá-los para cometer crimes cibernéticos. Em alguns casos, eles podem até continuar a exigir pagamentos de resgate adicionais.
Um ataque de ransomware pode ser detectado?
sim, ransomware pode ser detectado. Software antimalware e outras ferramentas de segurança avançadas pode detectar ransomware e alertar o usuário quando está presente em uma máquina.
É importante manter-se atualizado sobre as medidas de segurança mais recentes e manter o software de segurança atualizado para garantir que o ransomware possa ser detectado e evitado.
Os criminosos de ransomware são pegos?
sim, criminosos de ransomware são pegos. Agências de aplicação da lei, como o FBI, A Interpol e outras empresas tiveram sucesso em rastrear e processar criminosos de ransomware nos EUA e em outros países. Como as ameaças de ransomware continuam a aumentar, o mesmo acontece com a atividade de fiscalização.
About the .HakunaMatata File Virus Research
O conteúdo que publicamos em SensorsTechForum.com, this .HakunaMatata File Virus how-to removal guide included, é o resultado de uma extensa pesquisa, trabalho árduo e a dedicação de nossa equipe para ajudá-lo a remover o malware específico e restaurar seus arquivos criptografados.
Como conduzimos a pesquisa sobre este ransomware?
Nossa pesquisa é baseada em uma investigação independente. Estamos em contato com pesquisadores de segurança independentes, e como tal, recebemos atualizações diárias sobre as definições de malware e ransomware mais recentes.
além disso, the research behind the .HakunaMatata File Virus ransomware threat is backed with VirusTotal e a projeto NoMoreRansom.
Para entender melhor a ameaça do ransomware, por favor, consulte os seguintes artigos que fornecem detalhes conhecedores.
Como um site dedicado a fornecer instruções gratuitas de remoção de ransomware e malware desde 2014, A recomendação do SensorsTechForum é preste atenção apenas a fontes confiáveis.
Como reconhecer fontes confiáveis:
- Sempre verifique "Sobre nós" página da web.
- Perfil do criador do conteúdo.
- Certifique-se de que pessoas reais estejam por trás do site e não nomes e perfis falsos.
- Verifique o Facebook, Perfis pessoais no LinkedIn e no Twitter.



