o kshowonline.stream redirect é um sequestrador de navegador perigoso que faz parte de uma grande rede de sites e vírus que tentam sequestrar dados confidenciais dos usuários infectados. Pode levar a infecções por malware com outras ameaças e é distribuído usando vários métodos. Nosso guia de remoção completo mostra como as vítimas podem restaurar seus navegadores facilmente a partir dele.

Resumo ameaça
| Nome | kshowonline.stream |
| Tipo | navegador Hijacker, PUP, Mineiro de criptomoeda |
| Pequena descrição | o kshowonline.stream redirect é um sequestrador de navegador que redireciona as vítimas para uma página de malware e também instala um minerador de criptomoedas. |
| Os sintomas | As configurações do navegador mudam e problemas de desempenho devido à execução do processo de mineração. |
| distribuição Método | mensagens de spam, Extensões de navegador falsas, pacotes integrados |
| Ferramenta de detecção |
Veja se o seu sistema foi afetado por malware
Baixar
Remoção de Malware Ferramenta
|
| Experiência de usuário | Participe do nosso Fórum para discutir kshowonline.stream. |

kshowonline.stream Redirect - Técnicas de difusão
o kshowonline.stream redirect é um sequestrador de navegador típico que é distribuído usando as táticas de entrega comuns. No momento, um deles depende de instâncias de plug-in de malware. Eles são carregados para os repositórios de software dos plug-ins populares usando vários nomes. Na maioria dos casos, eles utilizam credenciais e análises de contas falsas para manipular as vítimas para fazer o download. Os usuários recebem a promessa de funcionalidade adicional ou controle e recursos aprimorados dos existentes.
Se os criminosos planejam campanhas de spam por e-mail então, diferentes métodos de entrega de malware podem ser utilizados - autônomo ou vários de uma vez. Praticamente em todos os casos Engenharia social são usados para coagir e manipular os usuários a interagir com ele. As táticas a seguir são muito usadas com sequestradores de navegador semelhantes ao kshowonline.stream redirect:
- Malware hiperlinks - Os criminosos podem optar por inserir links perigosos no conteúdo do corpo das mensagens. Eles geralmente são disfarçados como links de redefinição de senha ou páginas de login em modelos que se assemelham a serviços da web legítimos. Alguns até usam os gráficos originais de sites famosos para imitá-los o mais próximo possível. Depois de abertos, os visitantes são direcionados para uma página de download ou para o próprio arquivo executável.
- Anexos de arquivo - Em outros casos, o executável do sequestrador de navegador pode ser anexado diretamente às mensagens. Dependendo do esquema exato, ele pode ser renomeado ou arquivado para ocultar sua verdadeira forma.
- Documentos infectados - Os criminosos podem infectar documentos de diferentes tipos com códigos de vírus que podem trazer a ameaça. Esses arquivos são normalmente documentos de texto rico, planilhas ou apresentações. Assim que forem abertos pelas vítimas, iráaparecer uma mensagem de notificação que lhes pede para activar as macros integradas (Scripts). Se isso for feito, o arquivo de vírus é baixado de um site remoto e a infecção segue.
- site de redirecionamento - Os e-mails podem ser configurados para redirecionar para páginas controladas por hackers, anúncios e banners da web que podem levar à infecção de redirecionamento kshowonline.stream.
Os criminosos geralmente fazem trabalhos específicos páginas de redirecionamento que pode ser espalhado em redes sociais e diferente comunidades online. Outra tática seria incorporar o código do malware em instaladores de software de malware. Nesse caso, os operadores de hackers pegam arquivos de configuração legítimos de aplicativos populares do site oficial do fornecedor e os modificam para incluir o código perigoso. Eles são então distribuídos em falso portais de download e redes de compartilhamento de arquivos como o BitTorrent.
Finalmente, o kshowonline.stream redirect pode ser entregue usando malware adicional.

kshowonline.stream Redirect - Descrição técnica
o kshowonline.stream redirect segue os padrões de comportamento padrão associados a malware semelhante. Depois de se instalar nos computadores das vítimas, ele começa a executar o código embutido de acordo com a configuração do hacker. Esse tipo de infecção por malware é perigoso, pois cada campanha de ataque pode ter parâmetros diferentes. O comportamento padrão é alterar as configurações mais importantes do navegador da web para redirecionar para uma página controlada por hacker. Todos os exemplos populares de malware desta categoria são compatíveis com os navegadores mais usados: Mozilla Firefox, Google Chrome, Safári, Microsoft borda, Opera e Internet Explorer. As configurações modificadas incluem a página inicial padrão, motor de busca e novas guias página.
Uma vez feito isso, outras ações perigosas podem ocorrer. o kshowonline.stream redirect foi observado para instituir um cookie de rastreamento que começa automaticamente a coletar informações detalhadas que são enviadas para os operadores do hacker. Pode ser dados anônimos que inclui informações estatísticas, como a versão do sistema operacional, hora e data da infecção e etc. Outro tipo de dados inclui informações de exposição de identidade que está relacionado aos próprios usuários vítimas. O código pode sequestrar informações como seus nomes, endereço, números de telefone e senhas. Como as infecções começam nos próprios navegadores, os operadores de hackers também podem obter informações do cache armazenado: dados do formulário, biscoitos, favoritos, história, preferências, senhas e credenciais de conta.
Em certos casos, o redirecionamento kshowonline.stream pode ser configurado para implantar módulos adicionais, como um componente Trojan. Nestes casos, os operadores criminosos podem espionar as vítimas em tempo real, bem como assumir o controle de suas máquinas a qualquer momento. Em outros casos, o sequestrador de navegador pode se conectar a um C&servidor C para obter mais instruções. Essas conexões permitem que os hackers executem comandos arbitrários para as máquinas comprometidas, bem como entregar o malware adicional.
Nossa análise mostra que o sequestrador de navegador kshowonline.stream também instala um mineiro criptomoeda. Aproveita os recursos do sistema disponíveis para gerar renda para os operadores de hackers.
É muito possível que as campanhas de ataque atuais e futuras associadas a esta ameaça sejam executadas como um ameaça persistente. Isso significa que eles podem alterar componentes dos próprios sistemas operacionais, como o registro do Windows e arquivos de configuração. Estratégias de execução avançada permitem que ele se proteja de tentativas de remoção manual, monitorando continuamente as ações dos usuários.
O site em si não revela a empresa real que está por trás dele. A política de privacidade diz que usa o cookie de rastreamento e beacons da web para pesquisar os usuários o tempo todo. Observe que se o sequestrador de navegador oferece opções de pesquisa ou outros métodos para exibir as consultas do usuário, ele pode fazer parceria com patrocinadores para exibir resultados que podem não mostrar as melhores fontes possíveis de informação.
Outro perigo associado ao seu uso é o fato de o serviço compartilhar as informações com seus parceiros. Como resultado, as vítimas podem receber mensagens de spam visando seus interesses específicos.

kshowonline.stream Redirect - Política de privacidade
A política de privacidade fornecida lista uma lista parcial do tipo de dados que o redirecionamento sequestra dos navegadores infectados. Ele usa cookies de rastreamento e outras tecnologias da web, como beacons, para obter dados de vários tipos que são enviados automaticamente para os controladores do hacker. Ao ter a infecção disponível, os usuários autorizam automaticamente os procedimentos de segurança que seguem de acordo com a política de privacidade. Os dados são agrupados em grandes bancos de dados que são compartilhados entre redes invasoras. Os seguintes tipos de dados são alguns dos tipos listados na política de privacidade:
- Endereço de e-mail
- Identidades de rede social
- Informações de hardware
- Geolocation
- Endereço de IP
- Detalhes do sistema operacional
- Configurações do navegador da web
- Credenciais e senhas da conta
- Arquivos de log
- preferências
- Interesses do usuário

Remover kshowonline.stream Redirect
Remover kshowonline.stream manualmente a partir de seu computador, siga as instruções de remoção passo a passo a seguir indicados. No caso da remoção manual não se livrar do seqüestrador de navegador inteiramente, você deve procurar e remover quaisquer itens que sobraram com uma ferramenta anti-malware avançado. Tal software ajuda a manter seu computador seguro no futuro.
- janelas
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft borda
- Safári
- Internet Explorer
- Parar pop-ups push
Como remover kshowonline.stream do Windows.
Degrau 1: Procure por kshowonline.stream com a ferramenta SpyHunter Anti-Malware



Degrau 2: Inicialize seu PC no modo de segurança





Degrau 3: Desinstale kshowonline.stream e software relacionado do Windows
Etapas de desinstalação para Windows 11
Etapas de desinstalação para Windows 10 e versões mais antigas
Aqui é um método em alguns passos simples que deve ser capaz de desinstalar a maioria dos programas. Não importa se você estiver usando o Windows 10, 8, 7, Vista ou XP, esses passos vai começar o trabalho feito. Arrastando o programa ou a sua pasta para a lixeira pode ser um muito má decisão. Se você fizer isso, pedaços e peças do programa são deixados para trás, e que pode levar a um trabalho instável do seu PC, erros com as associações de tipo de arquivo e outras atividades desagradáveis. A maneira correta de obter um programa fora de seu computador é para desinstalá-lo. Fazer isso:


 Siga as instruções acima e você vai com sucesso desinstalar a maioria dos programas.
Siga as instruções acima e você vai com sucesso desinstalar a maioria dos programas.
Degrau 4: Limpe todos os registros, Created by kshowonline.stream on Your PC.
Os registros normalmente alvo de máquinas Windows são os seguintes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Você pode acessá-los abrindo o editor de registro do Windows e excluir quaisquer valores, criado por kshowonline.stream lá. Isso pode acontecer, seguindo os passos abaixo:


 Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Video Removal Guide for kshowonline.stream (janelas).
Livre-se de kshowonline.stream do Mac OS X.
Degrau 1: Uninstall kshowonline.stream and remove related files and objects
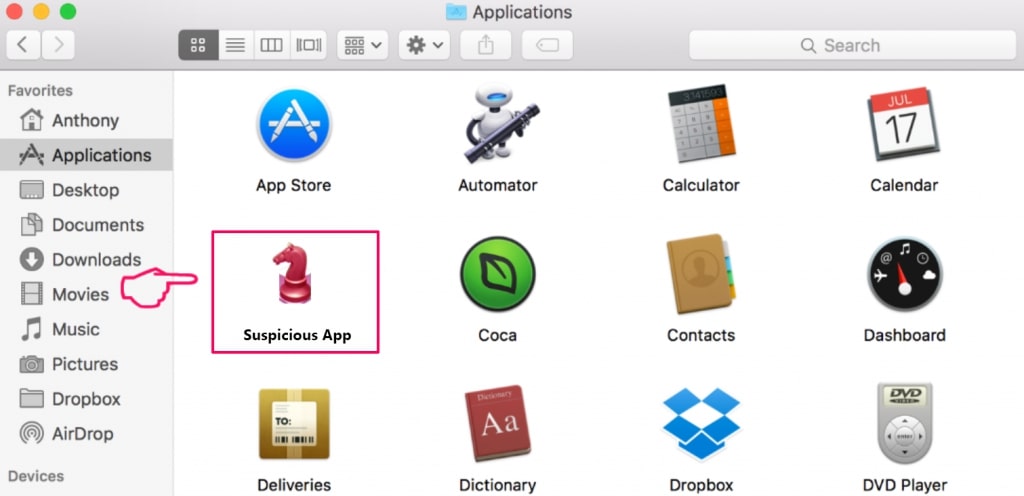
O seu Mac irá então mostrar uma lista de itens que iniciar automaticamente quando você log in. Procure por aplicativos suspeitos idênticos ou semelhantes a kshowonline.stream. Verifique o aplicativo que você deseja parar de funcionar automaticamente e selecione no Minus (“-“) ícone para escondê-lo.
- Vamos para inventor.
- Na barra de pesquisa digite o nome do aplicativo que você deseja remover.
- Acima da barra de pesquisa alterar os dois menus para "Arquivos do sistema" e "Estão incluídos" para que você possa ver todos os arquivos associados ao aplicativo que você deseja remover. Tenha em mente que alguns dos arquivos não pode estar relacionada com o aplicativo que deve ter muito cuidado quais arquivos você excluir.
- Se todos os arquivos estão relacionados, segure o ⌘ + A botões para selecioná-los e, em seguida, levá-los a "Lixo".
Caso você não consiga remover kshowonline.stream via Degrau 1 acima:
No caso de você não conseguir encontrar os arquivos de vírus e objetos em seus aplicativos ou outros locais que têm mostrado acima, você pode olhar para eles manualmente nas Bibliotecas do seu Mac. Mas antes de fazer isso, por favor leia o aviso legal abaixo:
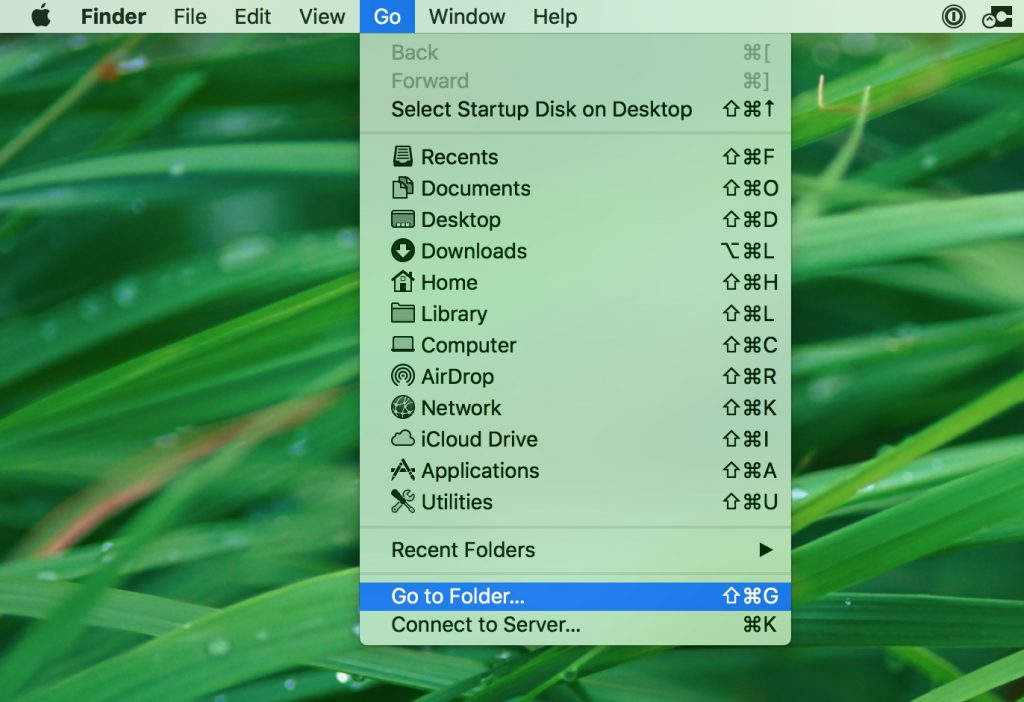
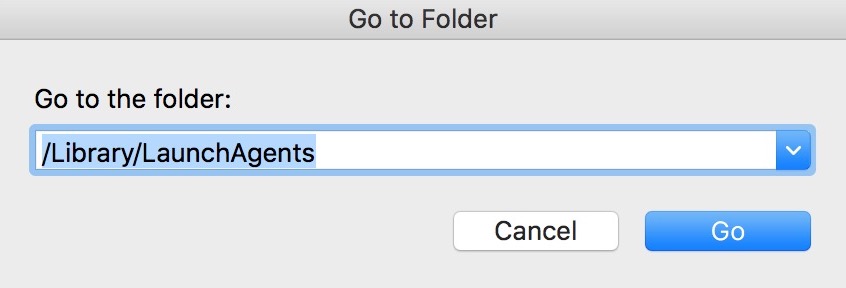
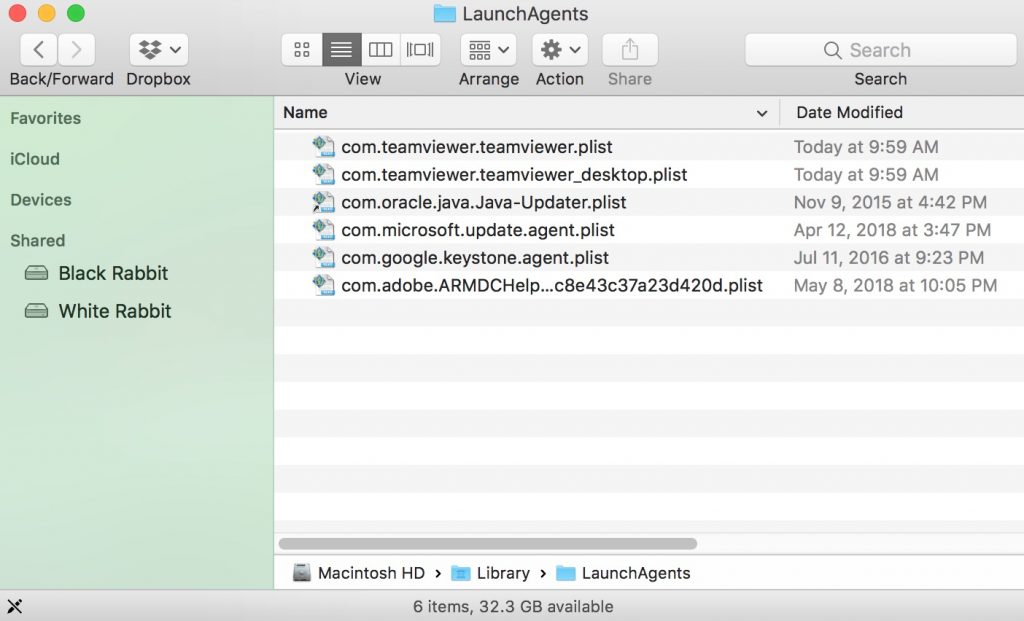
Você pode repetir o mesmo procedimento com os outros Biblioteca diretórios:
→ ~ / Library / LaunchAgents
/Biblioteca / LaunchDaemons
Gorjeta: ~ é ali de propósito, porque leva a mais LaunchAgents.
Degrau 2: Scan for and remove kshowonline.stream files from your Mac
Quando você está enfrentando problemas em seu Mac como resultado de scripts e programas indesejados, como kshowonline.stream, a forma recomendada de eliminar a ameaça é usando um programa anti-malware. O SpyHunter para Mac oferece recursos avançados de segurança, além de outros módulos que melhoram a segurança do seu Mac e a protegem no futuro.
Video Removal Guide for kshowonline.stream (Mac)
Remova kshowonline.stream do Google Chrome.
Degrau 1: Inicie o Google Chrome e abra o menu suspenso
Degrau 2: Mova o cursor sobre "Ferramentas" e, em seguida, a partir do menu alargado escolher "extensões"
Degrau 3: Desde o aberto "extensões" menu de localizar a extensão indesejada e clique em seu "Retirar" botão.
Degrau 4: Após a extensão é removido, reinicie o Google Chrome fechando-o do vermelho "X" botão no canto superior direito e iniciá-lo novamente.
Apagar kshowonline.stream do Mozilla Firefox.
Degrau 1: Inicie o Mozilla Firefox. Abra a janela do menu:
Degrau 2: Selecione os "Add-ons" ícone do menu.
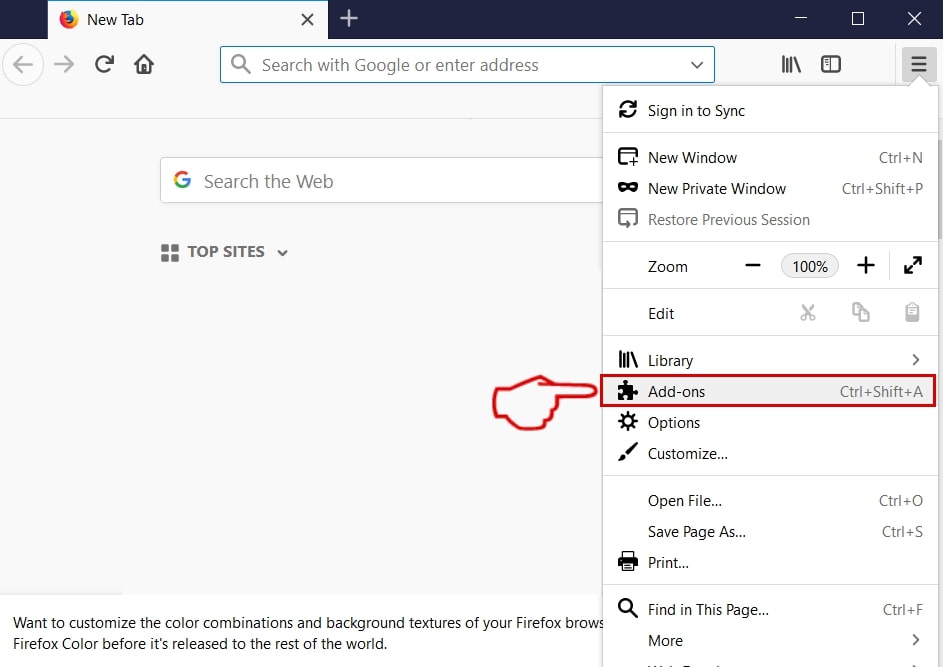
Degrau 3: Selecione a extensão indesejada e clique "Retirar"

Degrau 4: Após a extensão é removido, restart Mozilla Firefox fechando-lo do vermelho "X" botão no canto superior direito e iniciá-lo novamente.
Desinstale kshowonline.stream do Microsoft Edge.
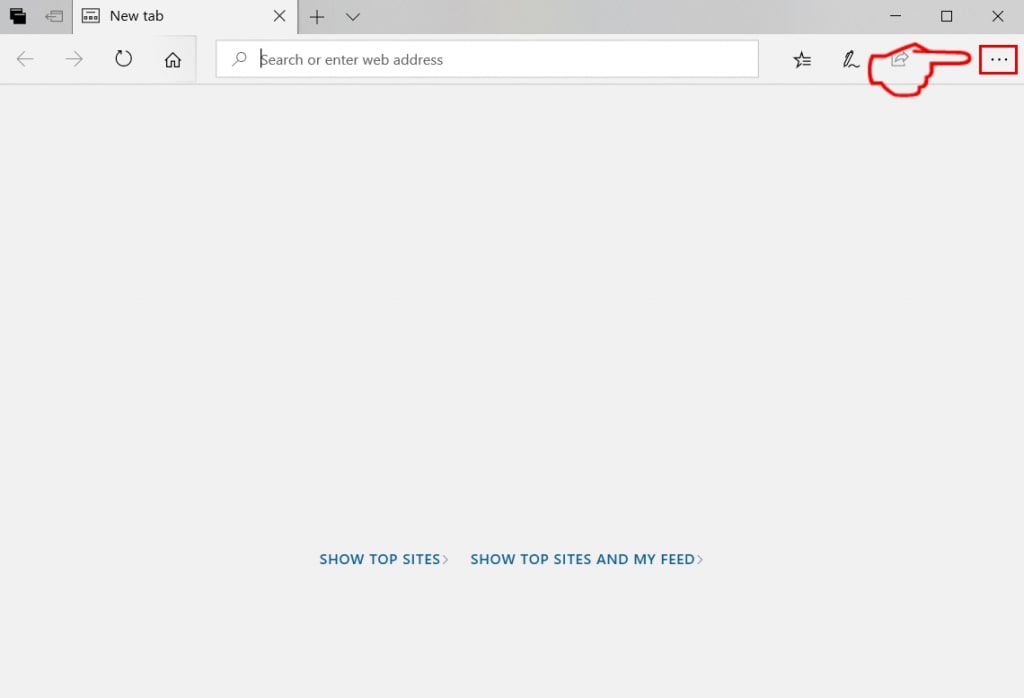
Degrau 1: Inicie o navegador Edge.
Degrau 2: Abra o menu suspenso clicando no ícone no canto superior direito.
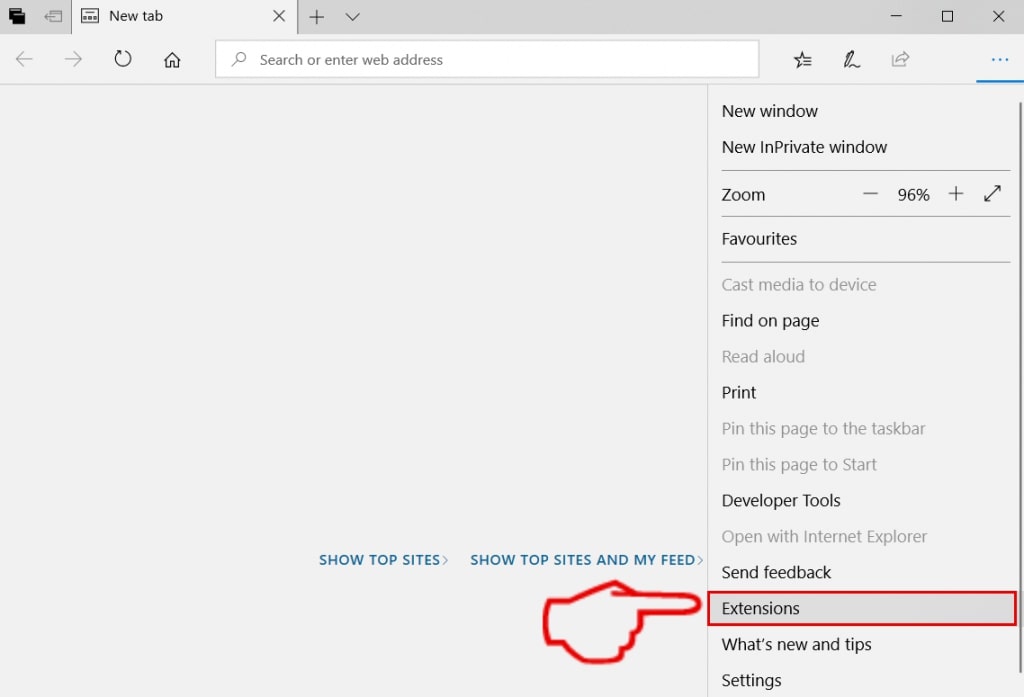
Degrau 3: A partir do menu drop seleccionar "extensões".
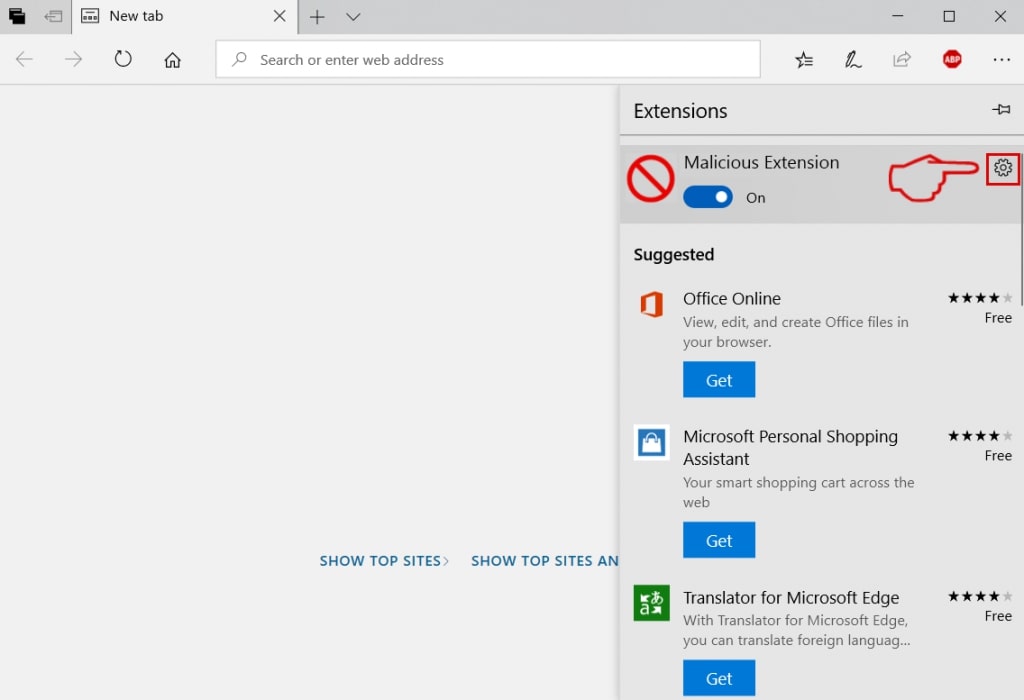
Degrau 4: Escolha a extensão suspeita de malware que deseja remover e clique no ícone de engrenagem.
Degrau 5: Remova a extensão maliciosa rolando para baixo e clicando em Desinstalar.
Remova kshowonline.stream do Safari
Degrau 1: Inicie o aplicativo Safari.
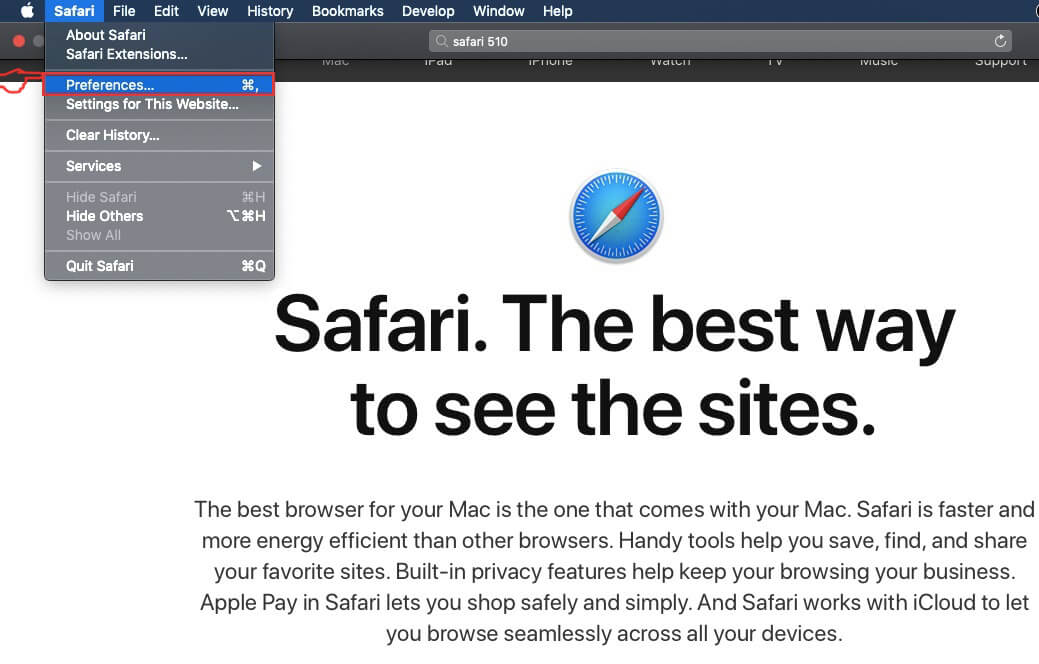
Degrau 2: Depois de passar o cursor do mouse para o topo da tela, clique no texto do Safari para abrir seu menu suspenso.
Degrau 3: A partir do menu, Clique em "preferências".
Degrau 4: Depois disso, selecione a guia 'Extensões'.
Degrau 5: Clique uma vez sobre a extensão que você deseja remover.
Degrau 6: Clique em 'Desinstalar'.
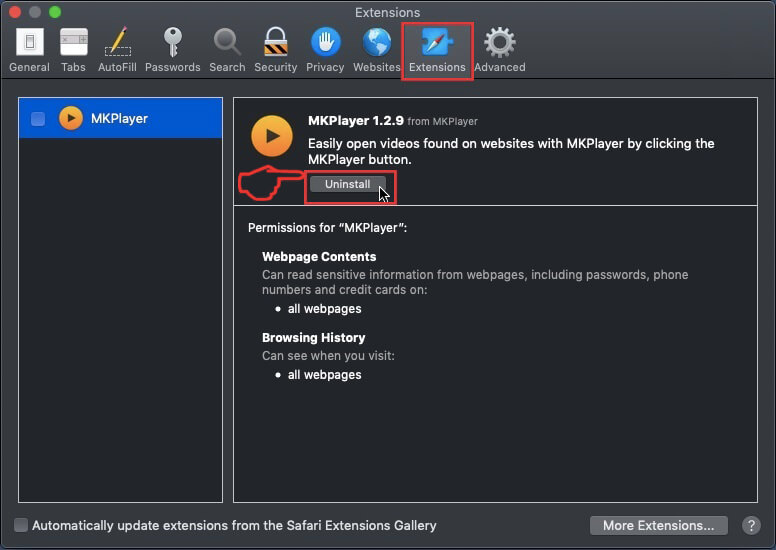
Uma janela pop-up aparecerá pedindo a confirmação de desinstalação a extensão. selecionar 'Desinstalar' novamente, e o kshowonline.stream será removido.
Elimine kshowonline.stream do Internet Explorer.
Degrau 1: Inicie o Internet Explorer.
Degrau 2: Clique no ícone de engrenagem denominado 'Ferramentas' para abrir o menu suspenso e selecione 'Gerenciar Complementos'
Degrau 3: Na janela 'Gerenciar Complementos'.
Degrau 4: Selecione a extensão que deseja remover e clique em 'Desativar'. Uma janela pop-up será exibida para informá-lo que você está prestes a desativar a extensão selecionada, e mais alguns add-ons pode ser desativado assim. Deixe todas as caixas marcadas, e clique em 'Desativar'.
Degrau 5: Após a extensão indesejada foi removido, reinicie o Internet Explorer fechando-o com o botão vermelho 'X' localizado no canto superior direito e reinicie-o.
Remova notificações push de seus navegadores
Desative as notificações push do Google Chrome
Para desativar quaisquer notificações push do navegador Google Chrome, Por favor, siga os passos abaixo:
Degrau 1: Vamos para Configurações no Chrome.
Degrau 2: Em Configurações, selecione “Configurações avançadas”:
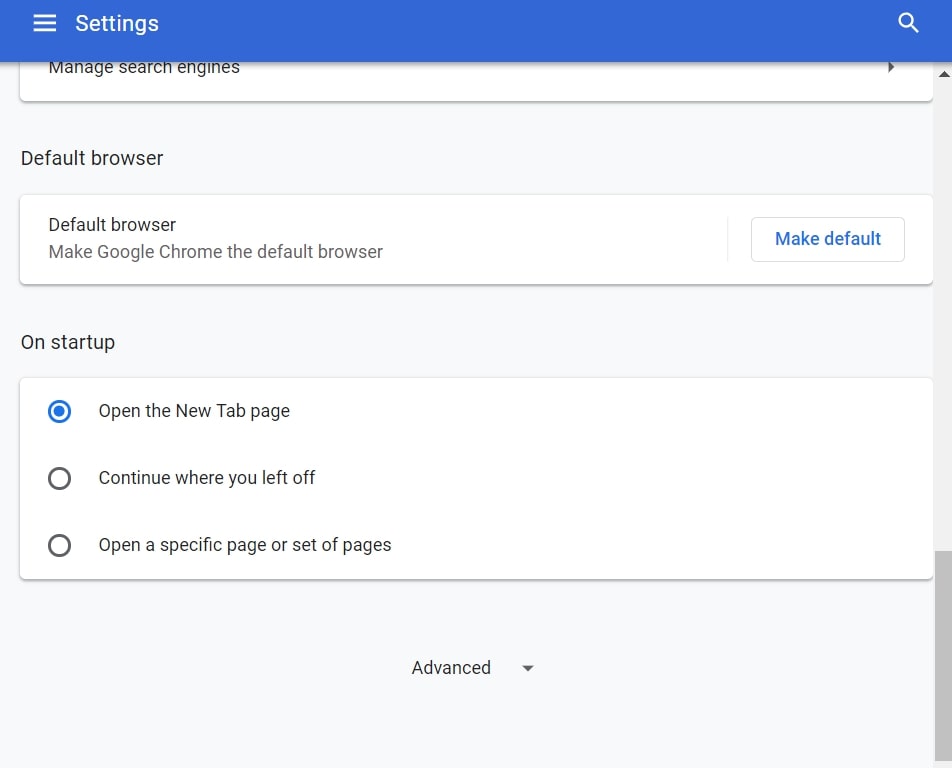
Degrau 3: Clique em “Configurações de conteúdo”:
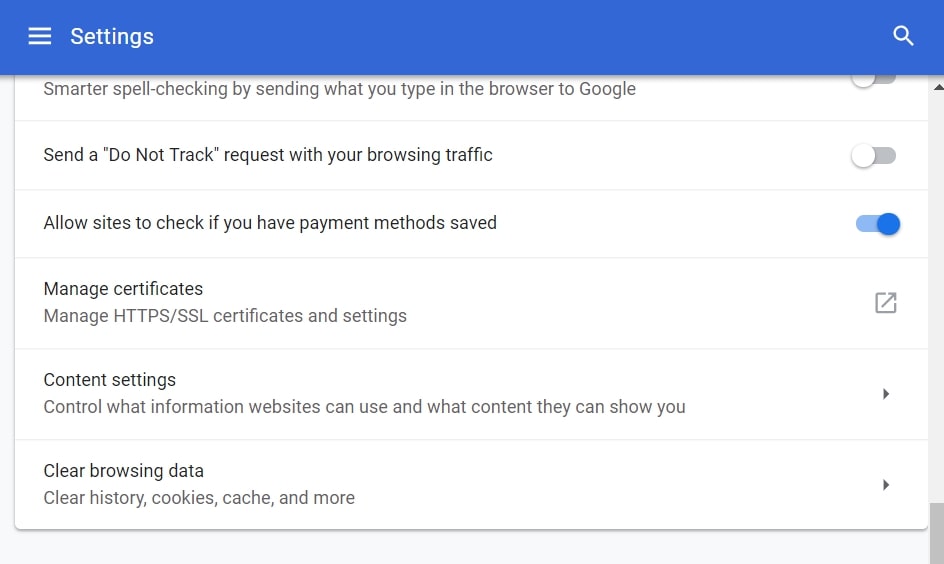
Degrau 4: Abrir "notificações”:
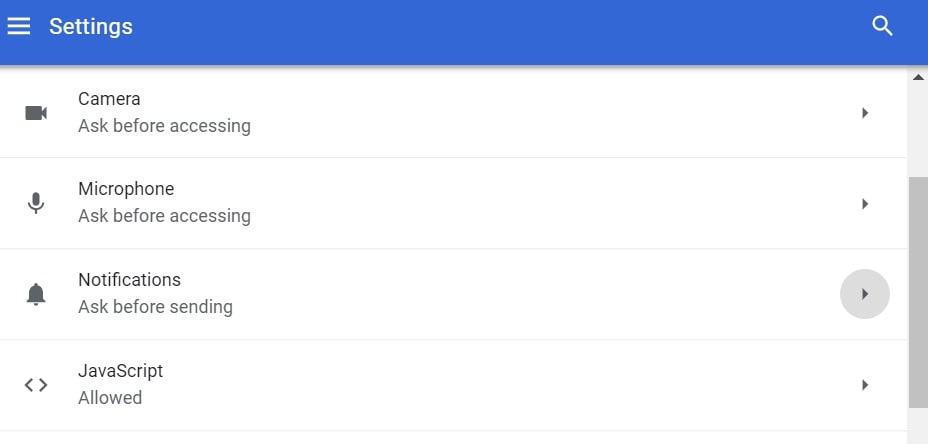
Degrau 5: Clique nos três pontos e escolha Bloco, Editar ou remover opções:

Remover notificações push no Firefox
Degrau 1: Vá para Opções do Firefox.
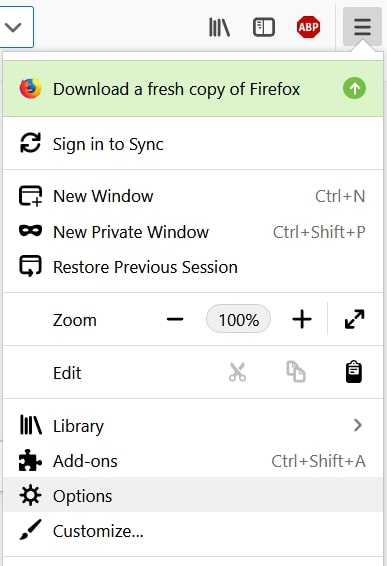
Degrau 2: Vá para as configurações", digite “notificações” na barra de pesquisa e clique "Configurações":
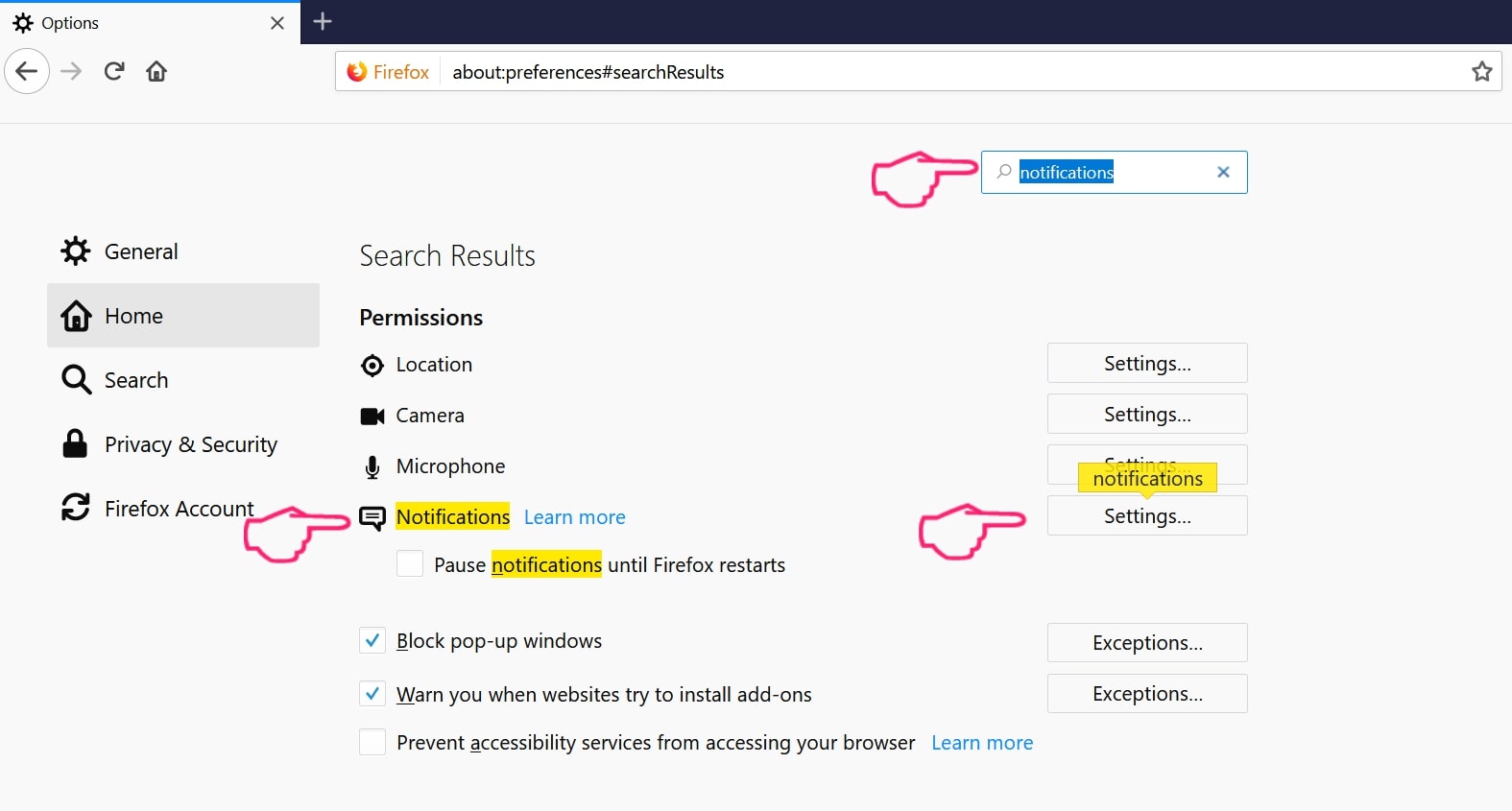
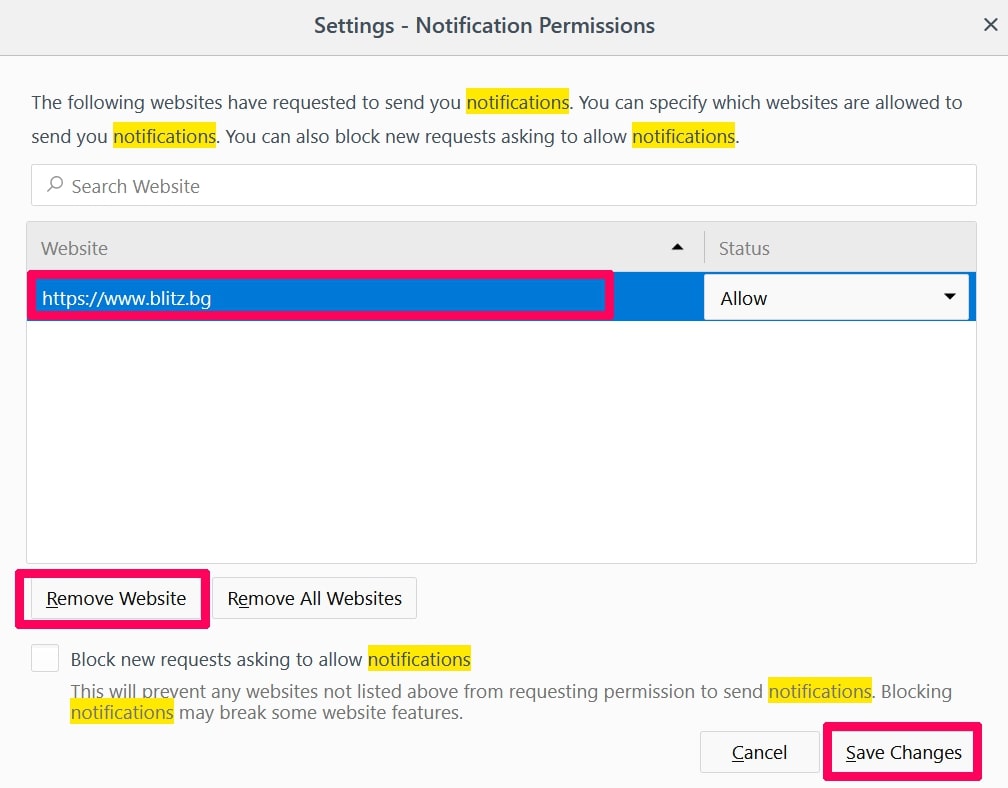
Degrau 3: Clique em “Remover” em qualquer site para o qual deseja que as notificações desapareçam e clique em “Salvar alterações”
Parar notificações push no Opera
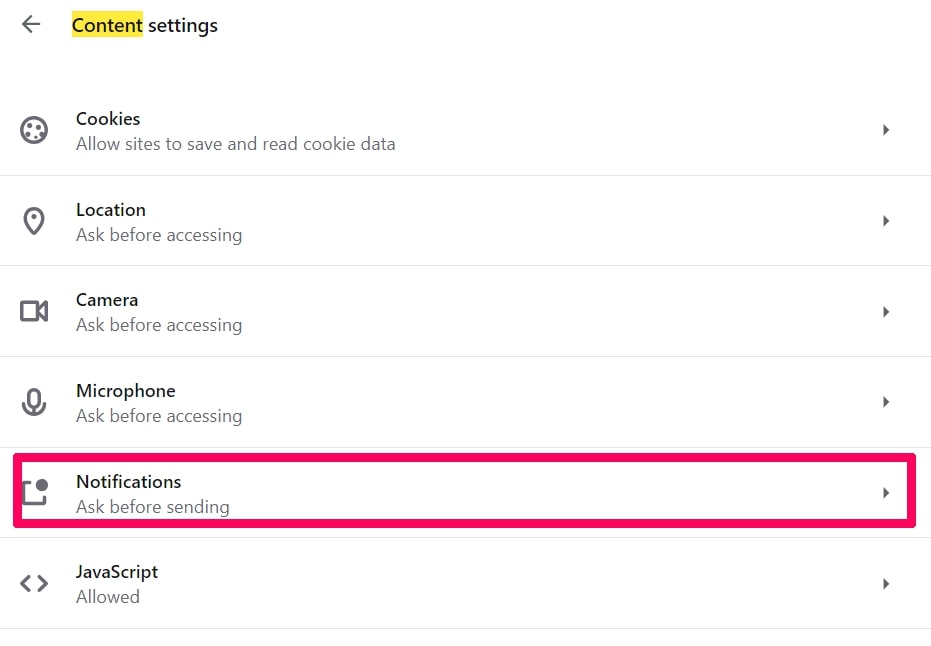
Degrau 1: Na ópera, pressione ALT + P para ir para Configurações.
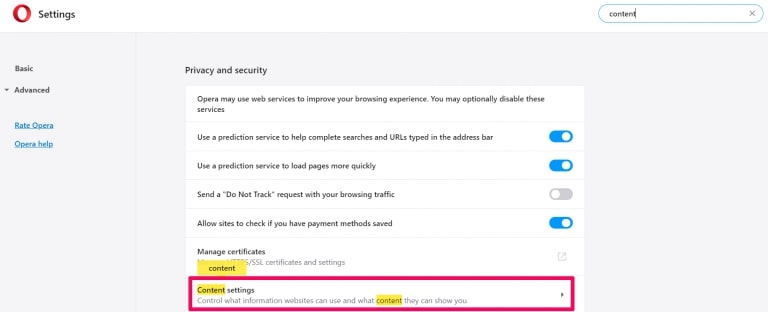
Degrau 2: Na pesquisa de configuração, digite “Conteúdo” para ir para Configurações de Conteúdo.
Degrau 3: Abrir notificações:
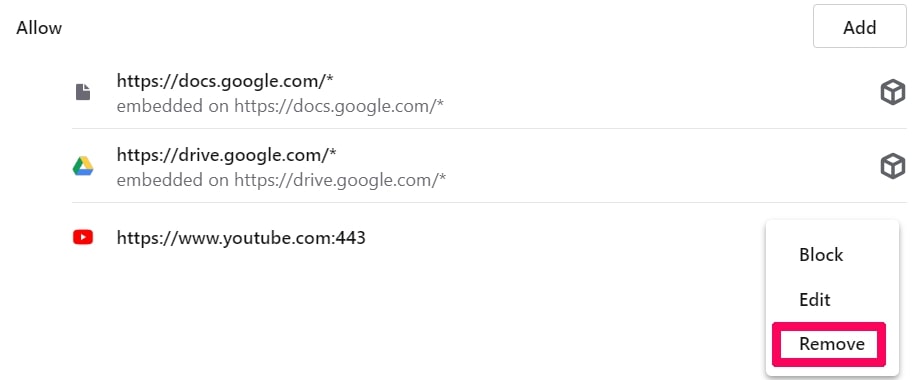
Degrau 4: Faça o mesmo que você fez com o Google Chrome (explicado abaixo):
Elimine notificações push no Safari
Degrau 1: Abra as preferências do Safari.
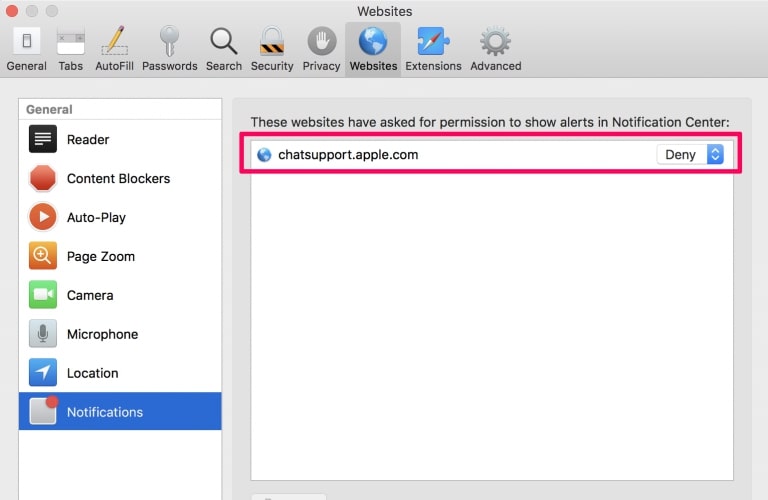
Degrau 2: Escolha o domínio de onde você gosta de push pop-ups e mude para "Negar" de "Permitir".
kshowonline.stream-FAQ
What Is kshowonline.stream?
The kshowonline.stream threat is adware or vírus redirecionar navegador.
Pode tornar o seu computador significativamente lento e exibir anúncios. A ideia principal é que suas informações provavelmente sejam roubadas ou mais anúncios sejam exibidos em seu dispositivo.
Os criadores de tais aplicativos indesejados trabalham com esquemas de pagamento por clique para fazer seu computador visitar tipos de sites arriscados ou diferentes que podem gerar fundos para eles. É por isso que eles nem se importam com os tipos de sites que aparecem nos anúncios. Isso torna o software indesejado indiretamente arriscado para o seu sistema operacional.
What Are the Symptoms of kshowonline.stream?
Existem vários sintomas a serem observados quando esta ameaça específica e também aplicativos indesejados em geral estão ativos:
Sintoma #1: Seu computador pode ficar lento e ter baixo desempenho em geral.
Sintoma #2: Você tem barras de ferramentas, add-ons ou extensões em seus navegadores da web que você não se lembra de ter adicionado.
Sintoma #3: Você vê todos os tipos de anúncios, como resultados de pesquisa com anúncios, pop-ups e redirecionamentos para aparecerem aleatoriamente.
Sintoma #4: Você vê os aplicativos instalados no seu Mac sendo executados automaticamente e não se lembra de instalá-los.
Sintoma #5: Você vê processos suspeitos em execução no Gerenciador de Tarefas.
Se você ver um ou mais desses sintomas, então os especialistas em segurança recomendam que você verifique se há vírus no seu computador.
Que tipos de programas indesejados existem?
De acordo com a maioria dos pesquisadores de malware e especialistas em segurança cibernética, as ameaças que atualmente podem afetar o seu dispositivo podem ser software antivírus desonesto, adware, seqüestradores de navegador, clickers, otimizadores falsos e quaisquer formas de PUPs.
O que fazer se eu tiver um "vírus" like kshowonline.stream?
Com algumas ações simples. Em primeiro lugar, é imperativo que você siga estas etapas:
Degrau 1: Encontre um computador seguro e conecte-o a outra rede, não aquele em que seu Mac foi infectado.
Degrau 2: Alterar todas as suas senhas, a partir de suas senhas de e-mail.
Degrau 3: Habilitar autenticação de dois fatores para proteção de suas contas importantes.
Degrau 4: Ligue para o seu banco para mude os detalhes do seu cartão de crédito (codigo secreto, etc.) se você salvou seu cartão de crédito para compras on-line ou realizou atividades on-line com seu cartão.
Degrau 5: Tenha certeza de ligue para o seu ISP (Provedor de Internet ou operadora) e peça a eles que alterem seu endereço IP.
Degrau 6: Mude o seu Senha do wifi.
Degrau 7: (Opcional): Certifique-se de verificar todos os dispositivos conectados à sua rede em busca de vírus e repita essas etapas para eles se eles forem afetados.
Degrau 8: Instale o anti-malware software com proteção em tempo real em todos os dispositivos que você possui.
Degrau 9: Tente não baixar software de sites que você não conhece e fique longe de sites de baixa reputação em geral.
Se você seguir essas recomendações, sua rede e todos os dispositivos se tornarão significativamente mais seguros contra quaisquer ameaças ou software invasor de informações e também estarão livres de vírus e protegidos no futuro.
How Does kshowonline.stream Work?
Uma vez instalado, kshowonline.stream can coletar dados utilização rastreadores. Esses dados são sobre seus hábitos de navegação na web, como os sites que você visita e os termos de pesquisa que você usa. Em seguida, é usado para direcionar anúncios ou vender suas informações a terceiros.
kshowonline.stream can also baixe outro software malicioso em seu computador, como vírus e spyware, que pode ser usado para roubar suas informações pessoais e exibir anúncios arriscados, que pode redirecionar para sites de vírus ou fraudes.
Is kshowonline.stream Malware?
A verdade é que os filhotes (adware, seqüestradores de navegador) não são vírus, mas pode ser tão perigoso pois eles podem mostrar e redirecioná-lo para sites de malware e páginas fraudulentas.
Muitos especialistas em segurança classificam programas potencialmente indesejados como malware. Isso ocorre devido aos efeitos indesejados que os PUPs podem causar, como exibir anúncios intrusivos e coletar dados do usuário sem o conhecimento ou consentimento do usuário.
About the kshowonline.stream Research
O conteúdo que publicamos em SensorsTechForum.com, this kshowonline.stream how-to removal guide included, é o resultado de uma extensa pesquisa, trabalho árduo e a dedicação de nossa equipe para ajudá-lo a remover o específico, problema relacionado ao adware, e restaure seu navegador e sistema de computador.
How did we conduct the research on kshowonline.stream?
Observe que nossa pesquisa é baseada em investigações independentes. Estamos em contato com pesquisadores de segurança independentes, graças ao qual recebemos atualizações diárias sobre o malware mais recente, adware, e definições de sequestrador de navegador.
além disso, the research behind the kshowonline.stream threat is backed with VirusTotal.
Para entender melhor esta ameaça online, por favor, consulte os seguintes artigos que fornecem detalhes conhecedores.