2017 foi um ano de crescente ameaça para o ransomware, seu primeiro ano de grande avanço o encontrou nas primeiras páginas da mídia tradicional, bem como em publicações de TI de alto nível. A rápida ascensão de WannaCry, GoldenEye, NotPetya levou a uma maior apreensão e vigilância de gerentes de TI e proprietários de negócios em todo o planeta.
Sua repentina proeminência é uma proposta de dar água na boca para os cibercriminosos – conseguiu desenvolver sua própria economia: barreira baixa para a entrada, pequeno investimento, altas recompensas, e até mesmo seu próprio modelo de negócios. Uma rede sofisticada completa com cadeias de suprimentos, criadores, distribuidores, mercados, Kits de bricolagem, contratos de afiliados, anúncios e alguns argumentariam sua própria moeda.
Estudos têm mostrado que esse ransomware viu um 2500% subir desde 2016, Com mais 6300 mercados e quase 45000 listas de produtos. As estimativas do valor total de mercado totalizaram quase $1 Bilhão.
ransomware: O Modelo de Negócios
A ascensão do ransomware depende de princípios de negócios bastante simples; notavelmente, fornecimento atendendo a demanda, barreira baixa para a entrada, baixo investimento de capital, escalabilidade fácil, e um grande mercado para atingir.
O ambiente do mundo estava repleto de ameaças cibernéticas como ransomware; muito de sua ascensão deve-se ao avanço da tecnologia e às oportunidades. Agora vivemos em um mundo cada vez mais online, nossos telefones e laptops contêm algumas de nossas informações mais confidenciais e pessoais, Da mesma forma, as empresas costumam manter seus negócios inteiros em servidores sem backups. Todo mundo agora é uma marca, exacerbado frequentemente por segurança frouxa e treinamento insuficiente de funcionários.
Os dias em que o ransomware e os vírus eram apenas para hackers sofisticados já se foram. Ransomware-as-a-Service cuidou disso; Raas é uma solução totalmente pronta para uso que permite que qualquer pessoa participe dessas atividades ilícitas, sem experiência em codificação ou habilidades técnicas, se você pode navegar na dark web, você pode participar de campanhas de ransomware, mesmo sem nenhum investimento de capital.
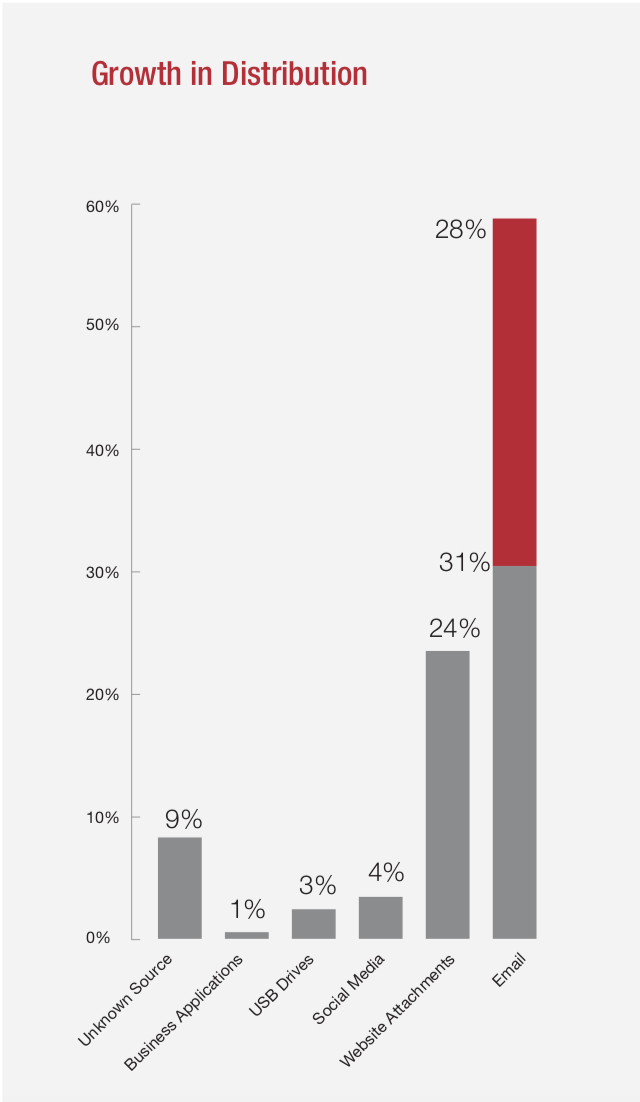
Pode ser enviado gratuitamente: p-mail, que ainda é o meio mais comum de infecção de ransomware, permitiu que criminosos distribuíssem ransomware para 100.000 ou até milhões de pessoas em uma explosão. Também estamos entrando em um mundo em que não apenas todos são uma marca, mas tudo: A IoT pode fazer com que tudo, de carros a geladeiras, seja usado para resgate.
Criminosos anônimos: Criminosos sem rosto, utilizando a rede Tor e aproveitando os pagamentos criptográficos pode manter seu anonimato – se você é uma pequena empresa ou indivíduo, as chances de prender o criminoso são mínimas.
De acordo com Carbon Black, o mercado de ransomware cresceu de $250,000 a mais $6,000,000 no ano passado – muito desse crescimento deve-se ao RaaS. Os kits de bricolagem costumam ser um menu de ransomware com preços variados, compilações de ransomware personalizado podem custar até $3,000 mas clones e kits DIY podem custar menos de um dólar.
A Cadeia de Suprimentos de Ransomware
Criação: Este é o centro nervoso, onde a sofisticação e o conhecimento real entram. Os autores e programadores desenvolvem programas de ransomware que podem ser colocados nos mercados, vendido, ou aproveitado pelo software RaaS.
Distribuição: Pode ser uma venda direta ou locais em plataformas RaaS. Na distribuição, os autores receberão uma parte dos resgates OU serão pagos adiantado. O custo depende de quão personalizado é o código, isso geralmente se correlaciona com sua capacidade de passar despercebido por antivírus e filtros de spam. Os distribuidores também podem comprar “ações” em uma campanha, onde os rendimentos são divididos dependendo do investimento. Os próprios vírus são geralmente enviados como "pulverizar e rezar’ listas de e-mail de spam ou hacks especificamente direcionados que exploram vulnerabilidades.
Encryption: Geralmente, existem dois tipos de criptografia de ransomware, o primeiro é o chamado ransomware locker e o segundo é criptográfico.
O armário é a forma mais antiga de ransomware, que interrompe a interação do usuário com um computador, geralmente dentro do navegador. Essas peças de ransomware costumam imitar agências governamentais, usando táticas de engenharia social para coagir dinheiro de usuários assustados.
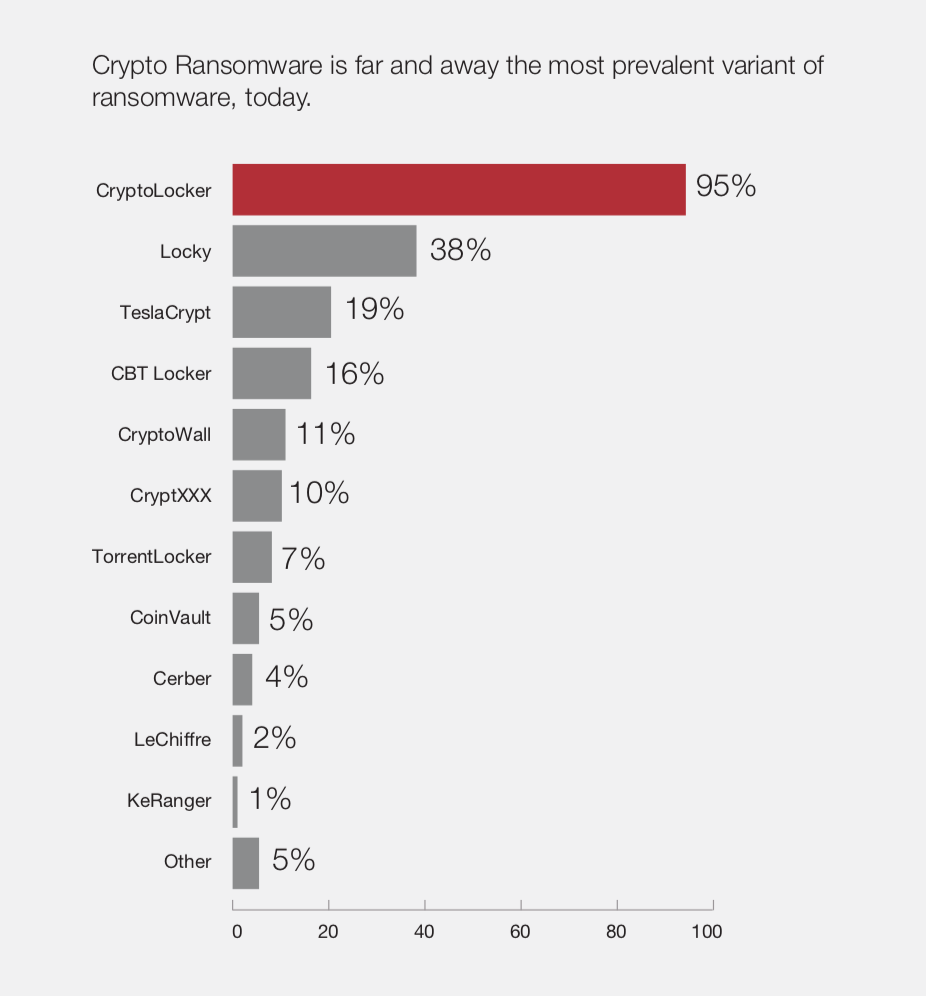
O ransomware criptográfico é a variedade que vemos cada vez mais, isso envolve criptografar informações valiosas armazenadas em computadores, tornando os dados inutilizáveis, a menos que não sejam criptografados. WannaCry e NotPetya eram ambos cripto ransomware.
Forma de pagamento: A parte mais importante do quebra-cabeça do ransomware e alguém pensaria que o mais fácil. Normalmente, uma chave de carteira bitcoin é gerada ou postada em um site, uma maneira fácil de pagamento anônimo. Contudo, nem tudo é fácil Exemplos de chaves de carteira erradas sendo colocadas ou chaves de carteira bloqueadas são comuns. WannaCry, que desenvolveu uma maneira de gerar chaves Bitcoin exclusivas (desbloqueável), tinha um interruptor de eliminação bastante fácil que interrompeu sua propagação.
descriptografia: E ai, o funil está completo – assim que o pagamento for recebido, o código para descriptografar seus arquivos é enviado. Em última análise, porém, pagando o resgate, você está apenas incentivando este tipo de atividade para continuar.
2017 viu um aumento no ransomware em escala, mais dinheiro, mais marcas, mais ataques, e mais perfil. Contudo, muitos dos ataques ainda cometeram erros de novato - esses erros muito provavelmente não serão corrigidos no futuro. A IoT e a estratificação de tudo, de telefones a geladeiras, verão 20.4 bilhões de dispositivos conectado à internet 2020 - apenas aumentando nossa suscetibilidade a ataques.
Nota do editor:
De tempos em tempos, O SensorsTechForum apresenta artigos de convidados de líderes e entusiastas de segurança cibernética e infosec, como este post. As opiniões expressas nestas mensagens de hóspedes, Contudo, são de inteira responsabilidade do autor contribuindo, e podem não refletir as de SensorsTechForum.