Este artigo irá ajudá-lo a remover .garrantydecrypt Ransomware. Siga as instruções de remoção ransomware fornecidas no final do artigo.
.Garrantydecrypt Files Virus é aquele que criptografa seus dados e exige dinheiro como resgate para obtê-lo restaurado. Arquivos receberá o .qweuirtksd extensão como um secundário, sem quaisquer alterações feitas ao nome original de um arquivo criptografado. o .Garrantydecrypt Files Virus vai deixar instruções ransomware dentro de um arquivo de texto. Continue a ler o artigo e ver como você poderia tentar recuperar potencialmente alguns de seus arquivos bloqueados e dados.

Resumo ameaça
| Nome | .garrantydecrypt ransomware |
| Tipo | ransomware, Cryptovirus |
| Pequena descrição | O ransomware criptografa arquivos, colocando o .garrantydecrypt extensão em seu sistema de computador e exige um resgate a ser pago aos supostamente recuperá-los. |
| Os sintomas | O ransomware irá criptografar seus arquivos e deixar uma nota de resgate com instruções de pagamento. |
| distribuição Método | Os e-mails de spam, Anexos de e-mail |
| Ferramenta de detecção |
Veja se o seu sistema foi afetado por malware
Baixar
Remoção de Malware Ferramenta
|
Experiência de usuário | Participe do nosso Fórum para discutir o ransomware .garrantydecrypt. |
| Ferramenta de recuperação de dados | Windows Data Recovery por Stellar Phoenix Aviso prévio! Este produto verifica seus setores de unidade para recuperar arquivos perdidos e não pode recuperar 100% dos arquivos criptografados, mas apenas alguns deles, dependendo da situação e se você tem ou não reformatado a unidade. |

.garrantydecrypt Ransomware - atualização de janeiro 2019
Em janeiro 2019 uma nova campanha de ataque foi detectada com uma versão ligeiramente diferente da nota de ransomware. Uma análise de segurança ainda não está disponível para essas amostras e nenhuma infecção em grande escala foi relatada. Isso nos dá razões para acreditar que as alterações feitas são possivelmente apenas da nota e que nenhum outro componente avançado foi adicionado.

.garrantydecrypt Ransomware - atualização de dezembro 2018
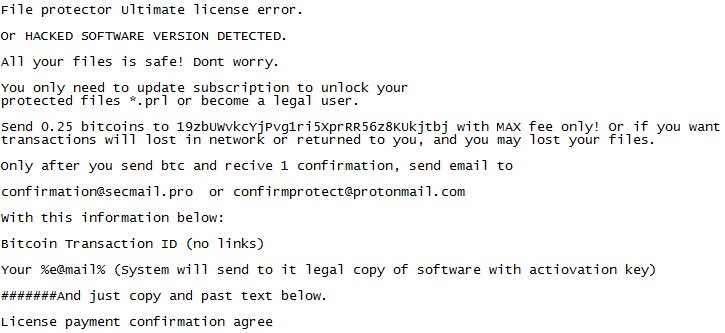
.garrantydecrypt Ransomware tem uma nova atualização em dezembro 2018. Parece que há uma nova variante GarrantyDecrypt Ransomware que tem a seguinte nota de resgate:
A nota de resgate indica que os fabricantes de ransomware querem 0.25 Bitcoin como soma de resgate.

.garrantydecrypt Ransomware - Táticas de distribuição
O .garrantydecrypt Ransomware pode ser entregue usando as táticas mais populares, assim como outros vírus comuns. Uma das estratégias mais eficazes é coordenar um campanha de phishing em massa usando mensagens de e-mail. Eles são enviados em massa para os destinos pretendidos e são projetados para se parecerem com notificações regulares enviadas por empresas ou serviços legítimos da Internet que eles possam usar.
Uma abordagem semelhante é a construção de locais controlado por hackers que são projetados para aparecer como portais de Internet conhecidos ou sites de fornecedores oficiais de aplicativos conhecidos. Esses dois métodos estão entre os principais usados para implantar portadores de carga útil infectados. Existem dois tipos principais que são os mais frequentes:
- Os documentos maliciosos - Os hackers podem criar cópias perigosas de todos os tipos de documentos populares: apresentações, Planilhas, bancos de dados e arquivos de texto. Sempre que forem abertos pelas vítimas, uma caixa de mensagem aparecerá solicitando aos usuários que habilitem os scripts integrados. Sempre que forem executados, o .garrantydecrypt Ransomware começará.
- Pacotes de aplicativos - Os operadores por trás do vírus podem incorporar o código perigoso em instaladores de software direcionados aos instalados com mais frequência: suites criatividade, aplicações de produtividade e utilitários do sistema. Sempre que forem instalados nos hosts alvo, a infecção por vírus também será iniciada.
Um método adicional usado para espalhar essas cargas úteis é o uso de redes de compartilhamento de arquivos como o BitTorrent, onde tais conteúdos são frequentemente enviados. Os hackers podem distribuir o vírus em todas as suas formas e a taxa de sucesso geralmente é alta, pois são uma plataforma muito comum para espalhar esses arquivos.
Em casos avançados, o .garrantydecrypt Ransomware também pode infectar ameaças por meio de extensões do navegador web maliciosas. Eles são criados pelos operadores para oferecer suporte aos navegadores mais populares e são carregados em seus vários repositórios com descrições elaboradas que prometem melhorias e adições de recursos. Quando instalados pelos usuários, eles executam as instruções integradas que geralmente modificam as configurações para redirecionar as vítimas a um site controlado por hacker. Depois de concluído, o .garrantydecrypt Ransomware será carregado nos computadores das vítimas.

.garrantydecrypt Ransomware - Descrição detalhada
As amostras .garrantydecrypt Ransomware capturadas pelos pesquisadores de segurança parecem ser as primeiras versões de teste. Isso leva a várias hipóteses possíveis sobre a origem das infecções. O primeiro é que os operadores por trás dele são desenvolvedores. Isso significa que o coletivo pode decidir por si quais recursos adicionar e implementá-los nas campanhas futuras. A outra hipótese é que os hackers responsáveis pelo lançamento da campanha o compraram dos mercados de hackers clandestinos.
Presumimos que versões futuras dele irão lançar uma série de ações contra os sistemas de destino. Muitos deles começam infecções lançando um módulo de colheita de dados. É usado para extrair strings usando um método automatizado que procura por informações específicas que são consideradas úteis para os controladores. O primeiro grupo de dados coletados pode expor a identidade dos usuários - as informações incluem strings como seu nome, endereço, senhas armazenadas e etc. A outra coleção é útil ao construir o ID de infecção exclusivo. É baseado em um relatório gerado dos componentes de hardware instalados, variáveis de ambiente do sistema operacional e etc.
Quando esta etapa for concluída, os dados extraídos podem ser processados por outro componente chamado proteção discrição. Ele procura assinaturas de software de segurança, como mecanismos antivírus, ambientes de sandbox e hosts de máquinas virtuais. Quando esses dois módulos forem executados, o mecanismo de vírus terá controle total sobre a máquina infectada. Isso permitirá que ele inicie vários processos, obter privilégios administrativos e também se conectar a processos do sistema e aplicativos de terceiros.
As próximas etapas são mudar o Valores do Registro do Windows pertencentes ao sistema operacional e aos aplicativos instalados pelo usuário. Modificações nos valores do Registro pertencentes ao próprio sistema podem levar a graves problemas de desempenho, problemas ao lançar certos serviços e etc. Quando os aplicativos instalados pelo usuário são afetados, isso pode afetar sua funcionalidade normal ou levar a erros inesperados.
Se configurado assim, isso também pode levar a um estado persistente de execução. Irá definir o motor de vírus para iniciar automaticamente sempre que o computador for ligado. Na maioria das situações, isso também irá desativar o menu de inicialização de recuperação e outros serviços que são iniciados no momento da inicialização. Esteja ciente de que esta etapa também contesta algumas instruções de recuperação manual do usuário.
Para tornar ainda mais difícil as infecções, remover o mecanismo malicioso pertencente ao .garrantydecrypt Ransomware pode excluir dados do sistema como as cópias Shadow Volume, backups e pontos de restauração. Eles podem ser recuperados apenas usando uma solução de recuperação de dados de qualidade, consulte nossas instruções para obter mais informações sobre como conseguir isso.
Outro efeito da instalação ransomare é sua capacidade de instalar outras cargas úteis. Isso é feito porque o ransomware já penetrou na segurança da máquina infectada e serve como um complexo conta-gotas de carga útil. Isso permite que ele manipule o sistema de uma forma que torna muito difícil remover todas as infecções. Uma instância muito perigosa é a entrega de um vírus cavalo de tróia pois vai estabelecer uma conexão com o servidor controlado por hacker. Permite que os operadores espiem os usuários em tempo real, assumir o controle de suas máquinas e sequestrar suas informações.

.garrantydecrypt Ransomware - Processo de criptografia

O mecanismo de ransomware será iniciado assim que todos os módulos anteriores forem concluídos. Os arquivos de amostra que foram capturados na campanha ativa mostram que ela não usa as cifras típicas, mas sim uma chave privada RSA-348 aleatória. Durante o processamento do arquivo, vários métodos são usados para criptografar os dados do usuário. Os próprios dados são criptografados de acordo com uma lista embutida de extensões de tipo de arquivo de destino. Um exemplo tem como alvo os seguintes dados:
- Bases de dados
- arquivo
- backups
- Música
- vídeos
- documentos
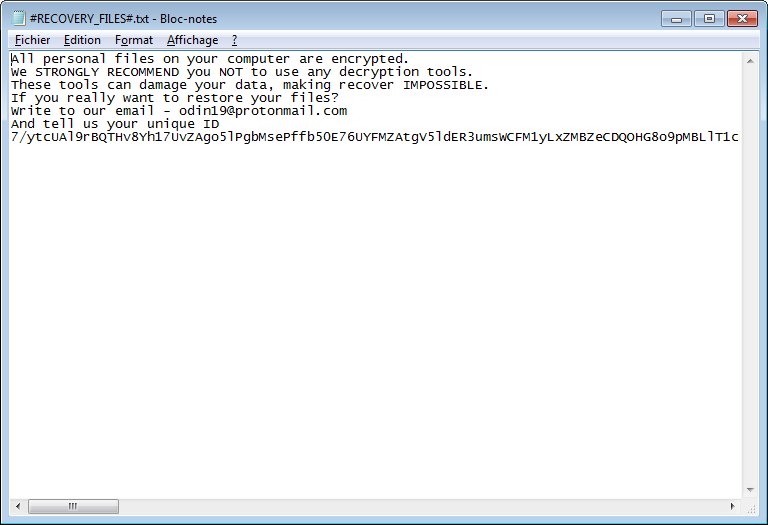
Os arquivos afetados são renomeados com a extensão .garrantydecrypt. Para chantagear os usuários da vítima a pagar uma taxa de descriptografia, o vírus irá gerar automaticamente uma nota de ransomware em um arquivo chamado #RECOVERY_FILES # .txt. Ele lê a seguinte:
Todos os seus arquivos foram criptografadas
Você realmente quer restaurar seus arquivos?
Escreva para o nosso e-mail – garrantydecrypt@airmail.cc
e diga-nos a sua identificação única
[editados 0x200 bytes de base64]

Remova arquivos .garrantydecrypt Cryptovirus e restaure dados criptografados
Se o seu sistema de computador foi infectado com o .Arquivos garrantydecrypt vírus ransomware, você deve ter um pouco de experiência na remoção de malware. Você deve se livrar deste ransomware o mais rápido possível antes que ele possa ter a chance de se espalhar ainda mais e infectar outros computadores. Você deve remover o ransomware e siga o passo-a-passo guia de instruções fornecido abaixo.
- Degrau 1
- Degrau 2
- Degrau 3
- Degrau 4
- Degrau 5
Degrau 1: Verifique se há ransomware .garrantydecrypt com a ferramenta Anti-Malware SpyHunter



Remoção automática de ransomware - Guia de Vídeo
Degrau 2: Uninstall .garrantydecrypt ransomware and related malware from Windows
Aqui é um método em alguns passos simples que deve ser capaz de desinstalar a maioria dos programas. Não importa se você estiver usando o Windows 10, 8, 7, Vista ou XP, esses passos vai começar o trabalho feito. Arrastando o programa ou a sua pasta para a lixeira pode ser um muito má decisão. Se você fizer isso, pedaços e peças do programa são deixados para trás, e que pode levar a um trabalho instável do seu PC, erros com as associações de tipo de arquivo e outras atividades desagradáveis. A maneira correta de obter um programa fora de seu computador é para desinstalá-lo. Fazer isso:


 Siga as instruções acima e você excluirá com sucesso a maioria dos programas maliciosos e indesejados.
Siga as instruções acima e você excluirá com sucesso a maioria dos programas maliciosos e indesejados.
Degrau 3: Limpe quaisquer registros, criado por .garrantydecrypt ransomware no seu computador.
Os registros normalmente alvo de máquinas Windows são os seguintes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Você pode acessá-los abrindo o editor de registro do Windows e excluir quaisquer valores, criado por .garrantydecrypt ransomware lá. Isso pode acontecer, seguindo os passos abaixo:


 Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Gorjeta: Para encontrar um valor criado-vírus, você pode botão direito do mouse sobre ela e clique "Modificar" para ver qual arquivo é definido para ser executado. Se este é o local do arquivo de vírus, remover o valor.
Antes de começar "Degrau 4", por favor Arrancar de novo para o modo Normal, no caso em que você está no Modo de Segurança.
Isto irá permitir-lhe instalar e uso SpyHunter 5 com sucesso.
Degrau 4: Inicialize seu PC no modo de segurança para isolar e remover .garrantydecrypt ransomware





Degrau 5: Tente restaurar arquivos criptografados por .garrantydecrypt ransomware.
Método 1: Use o STOP Decrypter da Emsisoft.
Nem todas as variantes deste ransomware pode ser descriptografado gratuitamente, mas nós adicionamos o decryptor utilizado por pesquisadores que é frequentemente atualizado com as variantes que se tornam, eventualmente descriptografado. Você pode tentar e descriptografar seus arquivos usando as instruções abaixo, mas se eles não funcionam, então, infelizmente, a sua variante do vírus ransomware não é decryptable.
Siga as instruções abaixo para usar o decrypter Emsisoft e descriptografar os arquivos de graça. Você pode baixar a ferramenta de decodificação Emsisoft ligados aqui e depois seguir os passos apresentados abaixo:
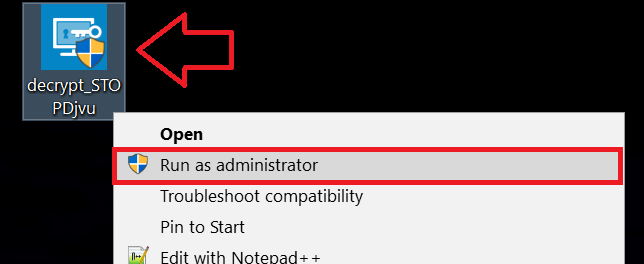
1 Botão direito do mouse na decrypter e clique em Executar como administrador como mostrado abaixo:
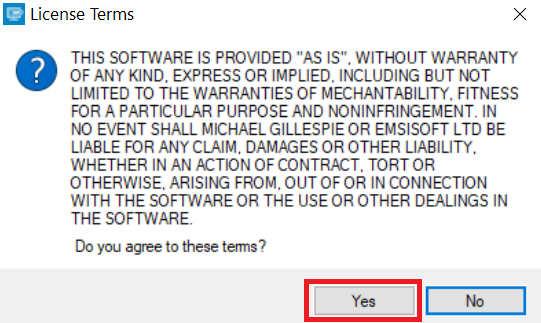
2. Concordo com os termos de licença:
3. Clique em "Adicionar pasta" e em seguida, adicione as pastas onde deseja que os arquivos descriptografado como debaixo mostrado:
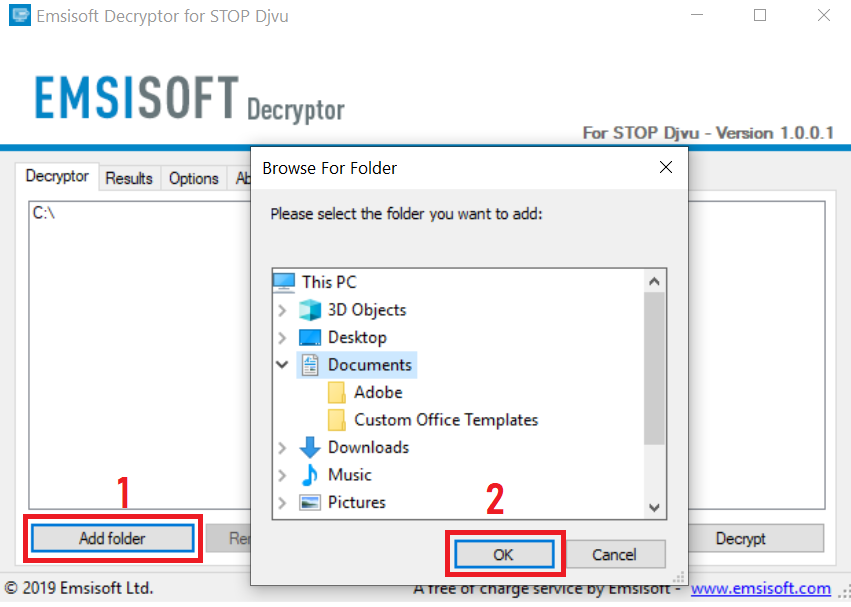
4. Clique em "Decrypt" e esperar por seus arquivos para ser decodificado.
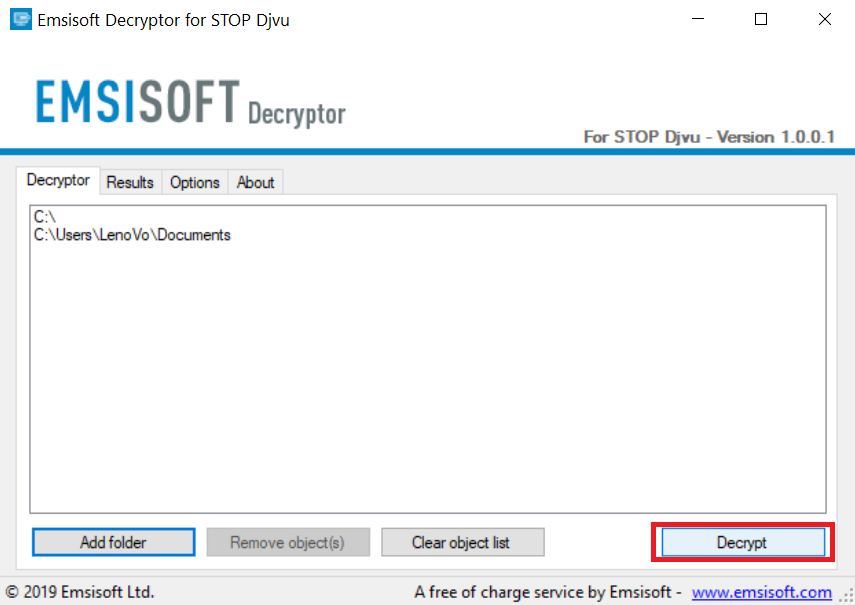
Nota: Crédito para o decryptor vai para pesquisadores Emsisoft que fizeram a descoberta com este vírus.
Método 2: Use software de recuperação de dados
As infecções de ransomware e o ransomware .garrantydecrypt visam criptografar seus arquivos usando um algoritmo de criptografia que pode ser muito difícil de descriptografar. É por isso que sugeriram um método de recuperação de dados que podem ajudá-lo a ir descriptografia torno direta e tentar restaurar seus arquivos. Tenha em mente que este método pode não ser 100% eficaz, mas também pode ajudá-lo um pouco ou muito em situações diferentes.
Basta clicar no link e nos menus do site na parte superior, escolher Recuperação de dados - Assistente de Recuperação de Dados para Windows ou Mac (dependendo do seu SO), e depois baixe e execute a ferramenta.
.garrantydecrypt ransomware-FAQ
What is .garrantydecrypt ransomware Ransomware?
.Garrantydecrypt ransomware é um ransomware infecção - o software malicioso que entra no computador silenciosamente e bloqueia o acesso ao próprio computador ou criptografa seus arquivos.
Muitos vírus ransomware usam algoritmos de criptografia sofisticados para tornar seus arquivos inacessíveis. O objetivo das infecções por ransomware é exigir que você pague um pagamento por resgate para ter acesso aos seus arquivos de volta.
What Does .garrantydecrypt ransomware Ransomware Do?
O ransomware em geral é um software malicioso que é projetado para bloquear o acesso ao seu computador ou arquivos até que um resgate seja pago.
Os vírus ransomware também podem danificar seu sistema, corromper dados e excluir arquivos, resultando na perda permanente de arquivos importantes.
How Does .garrantydecrypt ransomware Infect?
De várias maneiras ... garrantydecrypt ransomware O ransomware infecta computadores sendo enviado através de e-mails de phishing, contendo anexo de vírus. Esse anexo geralmente é mascarado como um documento importante, gostar uma fatura, documento bancário ou até mesmo uma passagem de avião e parece muito convincente para os usuários.
Another way you may become a victim of .garrantydecrypt ransomware is if you baixe um instalador falso, crack ou patch de um site de baixa reputação ou se você clicar em um link de vírus. Muitos usuários relatam ter recebido uma infecção por ransomware baixando torrents.
How to Open ..garrantydecrypt ransomware files?
Vocês can't sem um descriptografador. Neste ponto, a ..garrantydecrypt ransomware arquivos são criptografado. Você só pode abri-los depois de descriptografados usando uma chave de descriptografia específica para o algoritmo específico.
O que fazer se um descriptografador não funcionar?
Não entre em pânico, e faça backup dos arquivos. Se um decodificador não decifrar seu ..garrantydecrypt ransomware arquivos com sucesso, então não se desespere, porque esse vírus ainda é novo.
posso restaurar "..garrantydecrypt ransomware" arquivos?
sim, às vezes os arquivos podem ser restaurados. Sugerimos vários métodos de recuperação de arquivos isso poderia funcionar se você quiser restaurar ..garrantydecrypt ransomware arquivos.
Esses métodos não são de forma alguma 100% garantido que você será capaz de recuperar seus arquivos. Mas se você tiver um backup, suas chances de sucesso são muito maiores.
How To Get Rid of .garrantydecrypt ransomware Virus?
A maneira mais segura e eficiente de remover esta infecção por ransomware é o uso de um programa anti-malware profissional.
Ele irá procurar e localizar .garrantydecrypt ransomware ransomware e, em seguida, removê-lo sem causar nenhum dano adicional aos seus arquivos importantes ..garrantydecrypt ransomware.
Posso denunciar ransomware às autoridades?
Caso seu computador tenha sido infectado por uma infecção de ransomware, você pode denunciá-lo aos departamentos de polícia locais. Ele pode ajudar as autoridades em todo o mundo a rastrear e determinar os autores do vírus que infectou seu computador.
Abaixo, preparamos uma lista com sites governamentais, onde você pode registrar uma denúncia caso seja vítima de um cibercrime:
Autoridades de segurança cibernética, responsável por lidar com relatórios de ataque de ransomware em diferentes regiões em todo o mundo:
Alemanha - Portal oficial da polícia alemã
Estados Unidos - IC3 Internet Crime Complaint Center
Reino Unido - Polícia de Fraude de Ação
França - Ministro do interior
Itália - Polícia Estadual
Espanha - Policia Nacional
Países Baixos - Aplicação da lei
Polônia - Polícia
Portugal - Polícia Judiciária
Grécia - Unidade de crime cibernético (Polícia Helênica)
Índia - Polícia de Mumbai - Célula de investigação do CyberCrime
Austrália - Centro de crime de alta tecnologia australiano
Os relatórios podem ser respondidos em prazos diferentes, dependendo das autoridades locais.
Você pode impedir que o ransomware criptografe seus arquivos?
sim, você pode prevenir o ransomware. A melhor maneira de fazer isso é garantir que o sistema do seu computador esteja atualizado com os patches de segurança mais recentes, use um programa anti-malware confiável e firewall, faça backup de seus arquivos importantes com frequência, e evite clicar em links maliciosos ou baixando arquivos desconhecidos.
Can .garrantydecrypt ransomware Ransomware Steal Your Data?
sim, na maioria dos casos ransomware roubará suas informações. It is a form of malware that steals data from a user's computer, criptografa isso, e depois exige um resgate para descriptografá-lo.
Em muitos casos, a autores de malware ou invasores ameaçarão excluir os dados ou publicá-lo on-line a menos que o resgate seja pago.
O ransomware pode infectar WiFi?
sim, ransomware pode infectar redes WiFi, como agentes mal-intencionados podem usá-lo para obter o controle da rede, roubar dados confidenciais, e bloquear usuários. Se um ataque de ransomware for bem-sucedido, pode levar a uma perda de serviço e/ou dados, e em alguns casos, perdas financeiras.
Devo Pagar Ransomware?
Não, você não deve pagar extorsionários de ransomware. Pagá-los apenas incentiva os criminosos e não garante que os arquivos ou dados sejam restaurados. A melhor abordagem é ter um backup seguro de dados importantes e estar atento à segurança em primeiro lugar.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, os hackers ainda podem ter acesso ao seu computador, dados, ou arquivos e pode continuar ameaçando expô-los ou excluí-los, ou mesmo usá-los para cometer crimes cibernéticos. Em alguns casos, eles podem até continuar a exigir pagamentos de resgate adicionais.
Um ataque de ransomware pode ser detectado?
sim, ransomware pode ser detectado. Software antimalware e outras ferramentas de segurança avançadas pode detectar ransomware e alertar o usuário quando está presente em uma máquina.
É importante manter-se atualizado sobre as medidas de segurança mais recentes e manter o software de segurança atualizado para garantir que o ransomware possa ser detectado e evitado.
Os criminosos de ransomware são pegos?
sim, criminosos de ransomware são pegos. Agências de aplicação da lei, como o FBI, A Interpol e outras empresas tiveram sucesso em rastrear e processar criminosos de ransomware nos EUA e em outros países. Como as ameaças de ransomware continuam a aumentar, o mesmo acontece com a atividade de fiscalização.
About the .garrantydecrypt ransomware Research
O conteúdo que publicamos em SensorsTechForum.com, this .garrantydecrypt ransomware how-to removal guide included, é o resultado de uma extensa pesquisa, trabalho árduo e a dedicação de nossa equipe para ajudá-lo a remover o malware específico e restaurar seus arquivos criptografados.
Como conduzimos a pesquisa sobre este ransomware?
Nossa pesquisa é baseada em uma investigação independente. Estamos em contato com pesquisadores de segurança independentes, e como tal, recebemos atualizações diárias sobre as definições de malware e ransomware mais recentes.
além disso, the research behind the .garrantydecrypt ransomware ransomware threat is backed with VirusTotal e a projeto NoMoreRansom.
Para entender melhor a ameaça do ransomware, por favor, consulte os seguintes artigos que fornecem detalhes conhecedores.
Como um site dedicado a fornecer instruções gratuitas de remoção de ransomware e malware desde 2014, A recomendação do SensorsTechForum é preste atenção apenas a fontes confiáveis.
Como reconhecer fontes confiáveis:
- Sempre verifique "Sobre nós" página da web.
- Perfil do criador do conteúdo.
- Certifique-se de que pessoas reais estejam por trás do site e não nomes e perfis falsos.
- Verifique o Facebook, Perfis pessoais no LinkedIn e no Twitter.