Opdatering August 2019. Hvad er Cookie Miner? Sådan fjernes Cookie Miner? Hvordan man kan stoppe Cookie Miner fra minedrift cryptocurrencies på din Mac?
Cookie Miner er en cryptocurrency minearbejder trojansk hest, der inficerer din Mac og begynder at stjæle oplysninger, spore din aktivitet og mine for krypto. De minedrift processer kan bremse din Mac og gøre det endnu stamme og fryse, og hvis Cookie Miner forbliver i længere tid på din Mac, kan det endda forårsage skade på det CPU (Processor) og GPU (grafikkort), som kan bryde det ned. Læs denne artikel for at lære, hvordan du fjerner Cookie Miner fra din Mac.

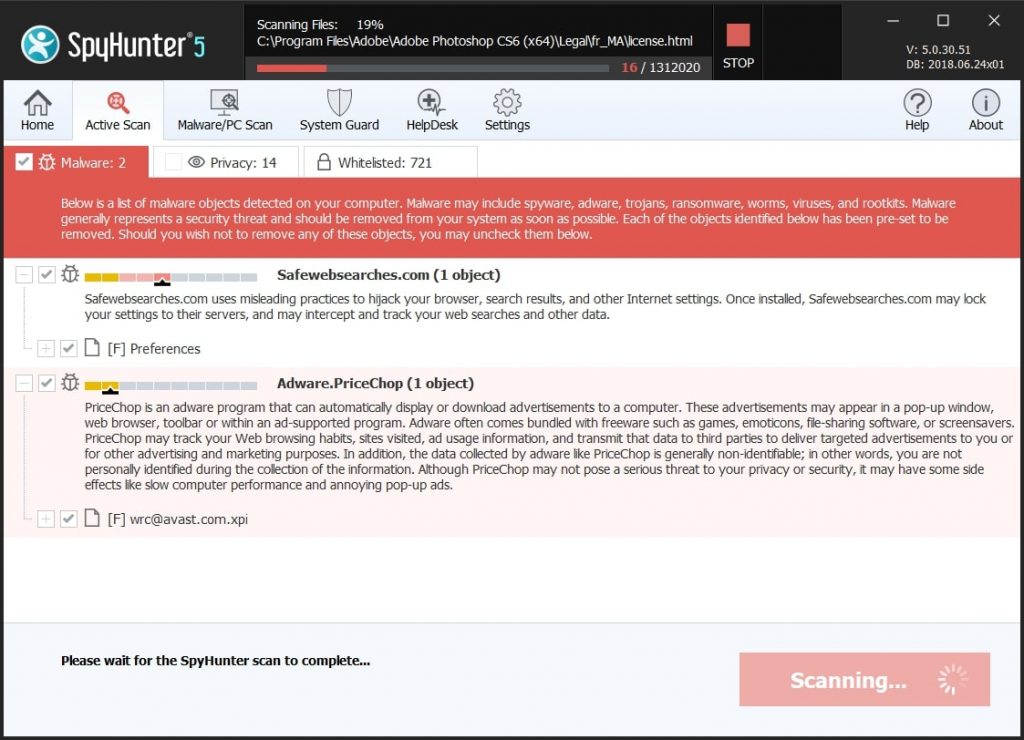
Trussel Summary
| Navn | Cookie Miner |
| Type | Miner Trojan for Mac OS |
| Kort beskrivelse | Har til formål at sno sig på din Mac lydløst og udføre Trojan og Cryptocurrency Minedrift. |
| Symptomer | Din Mac kan falde væsentligt, og du kan begynde at se flere forskellige ukendte processer, der kører i baggrunden. |
| Distributionsmetode | Via mistænkelige downloads, virus URL'er eller ondsindet e-mail-spam. |
| Værktøj Detection |
Se, om dit system er blevet påvirket af malware
Hent
Combo Cleaner
|
Brugererfaring | Tilmeld dig vores forum at diskutere Cookie Miner. |

Cookie Miner – Hvordan klarede jeg mig det, og hvad betyder det gøre?
cookie Miner er malware, der har til formål at stjæle private data af brugere og åbne en bagdør på de inficerede Macs hvorefter downloads og også kører en cryptocurrency minearbejder.
Det kan inficere din computer via følgende metoder;
- Hvis du har åbnet en virus fil, der er knyttet til en e-mail, hvor det foregiver at være legitim dokument.
- Hvis du har hentet virus fil online, hvor det foregiver at være en app eller et andet program.
- Hvis du er blevet omdirigeret til en virusinfektion webadresse som et resultat af at besøge en lav-ry websted eller har adware på din Mac.
Enten måde, når den er blevet installeret på din computer, Cookie Miner kan begynde at udføre følgende aktiviteter:
- Få dine cookies oplysninger fra Chrome og Safari.
- Anskaf brugernavne og passwords gemt på din web-browsere.
- Stjæl din økonomiske data (Kreditkortoplysninger).
- Få meddelelser fra din iPhone og andre opkald logdata, der blev bakket op i dine iTunes.
- Download og installer andre vira via bagdøren.
- Kør cryptocurrency minearbejder programmet.
Cookie Miner har evnen til at stjæle data fra følgende kreditkort:
- Visum.
- AMEX.
- Mastercard.
- Opdage.
Til fjernbetjening, Cookie Miner virus vil hente Empyre, der er en kontrol værktøj til Mac, der kan indpasses i dit kamera, mikrofon og relæ screenshots fra dit skrivebord og sende dem til hackere som CheckPoint forskere rapport.
Den krypto minearbejder program Cookie Miner kan forbinde til en mønt minedrift pulje, og det er vigtigste mål er at forbinde din Mac til en cryptocurrency minedrift pulje. Denne pulje af inficerede computere har til formål at generere Bitcoin eller andre anonyme cryptocurrencies ved at bruge deres ressourcer. Så uden at du mærker, skurke tjene penge ved overusing din Mac lydløst. Det eneste, der giver den væk, er, at din Mac bliver betydeligt langsommere.

Fjern Cookie Miner Trojan fra din Mac
For at fjerne denne malware fra din Mac, Vi anbefaler kraftigt, at du læser anvisningerne i denne artikel. De er blevet lavet med det ene formål at hjælpe dig med at slette denne virus fra din Mac effektivt trin for trin. For maksimal effektivitet, vi på det kraftigste anbefale, at du henter og kører en scanning af din Mac med en professionel malware renere for mac. Sådan software er at automatisk at registrere alle objekter på din Mac og slette dem grundigt.
Trin til at forberede før fjernelse:
Inden du begynder at følge nedenstående trin, tilrådes, at du først skal gøre følgende forberedelser:
- Backup dine filer i tilfælde det værste sker.
- Sørg for at have en enhed med disse instruktioner om standy.
- Arm dig selv med tålmodighed.
- 1. Scan efter Mac Malware
- 2. Afinstaller Risky Apps
- 3. Rens dine browsere
Trin 1: Scan for and remove Cookie Miner files from your Mac
Når du står over for problemer på din Mac som følge af uønskede scripts og programmer såsom Cookie Miner, den anbefalede måde at eliminere truslen er ved hjælp af en anti-malware program. SpyHunter til Mac tilbyder avancerede sikkerhedsfunktioner sammen med andre moduler, der forbedrer din Mac's sikkerhed og beskytter den i fremtiden.
Hurtig og nem Mac Malware Video Removal Guide
Bonustrin: Sådan får du din Mac til at køre hurtigere?
Mac-maskiner opretholder nok det hurtigste operativsystem der findes. Stadig, Mac'er bliver nogle gange langsomme og træge. Videoguiden nedenfor undersøger alle de mulige problemer, der kan føre til, at din Mac er langsommere end normalt, samt alle de trin, der kan hjælpe dig med at fremskynde din Mac.
Trin 2: Uninstall Cookie Miner and remove related files and objects
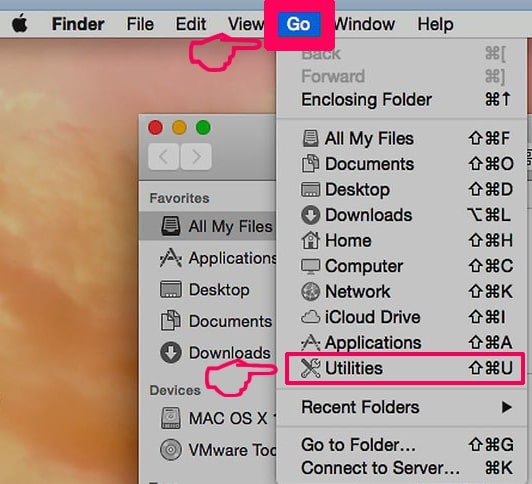
1. ramte ⇧ + ⌘ + U nøgler til at åbne Utilities. En anden måde er at klikke på "Go" og derefter klikke på "Utilities", ligesom på billedet nedenfor viser:
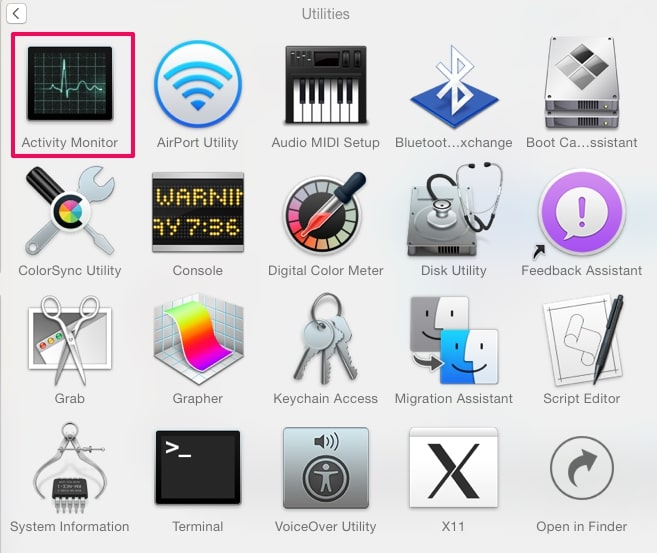
2. Find Activity Monitor og dobbeltklik på den:
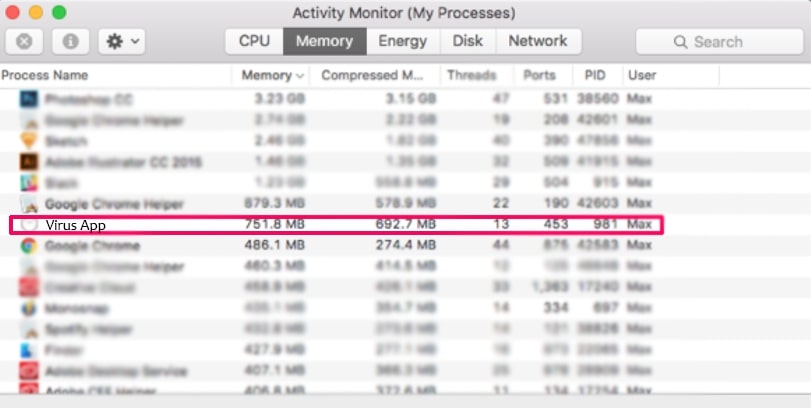
3. I Aktivitetsovervågning kigge efter eventuelle mistænkelige processer, tilhører eller relateret til Cookie Miner:
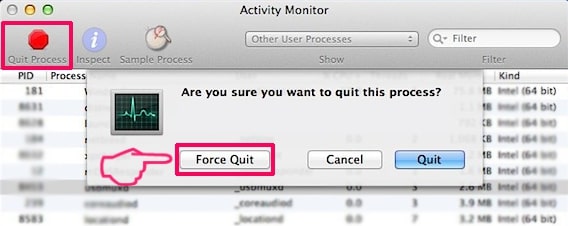
4. Klik på "Gå" knappen igen, men denne gang skal du vælge Programmer. En anden måde er med knapperne ⇧+⌘+A.
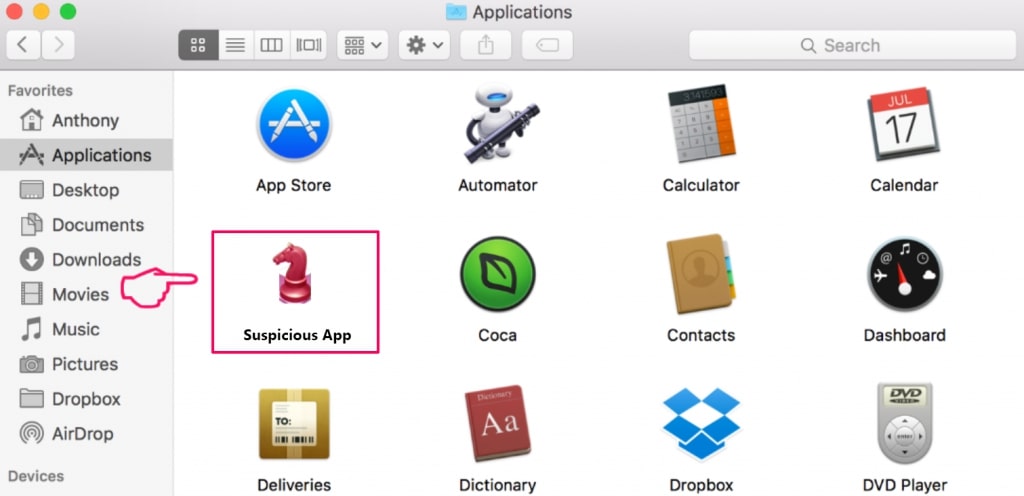
5. I menuen Applikationer, ser for enhver mistænkelig app eller en app med et navn, identisk med eller ligner Cookie Miner. Hvis du finder det, højreklik på appen og vælg "Flyt til papirkurven".
6. Vælg Konti, hvorefter du klikke på Log ind-emner præference. Din Mac vil så vise dig en liste over emner, starte automatisk når du logger ind. Kig efter eventuelle mistænkelige apps identiske eller lignende til Cookie Miner. Marker den app, du vil stoppe med at køre automatisk, og vælg derefter på Minus ("-") ikonet for at skjule det.
7. Fjern eventuelle resterende filer, der kan være relateret til denne trussel, manuelt ved at følge undertrinene nedenfor:
- Gå til Finder.
- I søgefeltet skriv navnet på den app, du vil fjerne.
- Over søgefeltet ændre to rullemenuerne til "System Files" og "Er Inkluderet" så du kan se alle de filer, der er forbundet med det program, du vil fjerne. Husk på, at nogle af filerne kan ikke være relateret til den app, så være meget forsigtig, hvilke filer du sletter.
- Hvis alle filerne er relateret, hold ⌘ + A knapperne til at vælge dem og derefter køre dem til "Affald".
I tilfælde af at du ikke fjerne Cookie Miner via Trin 1 over:
I tilfælde af at du ikke finde virus filer og objekter i dine programmer eller andre steder, vi har vist ovenfor, kan du manuelt søge efter dem i bibliotekerne i din Mac. Men før du gør dette, læs den fulde ansvarsfraskrivelse nedenfor:
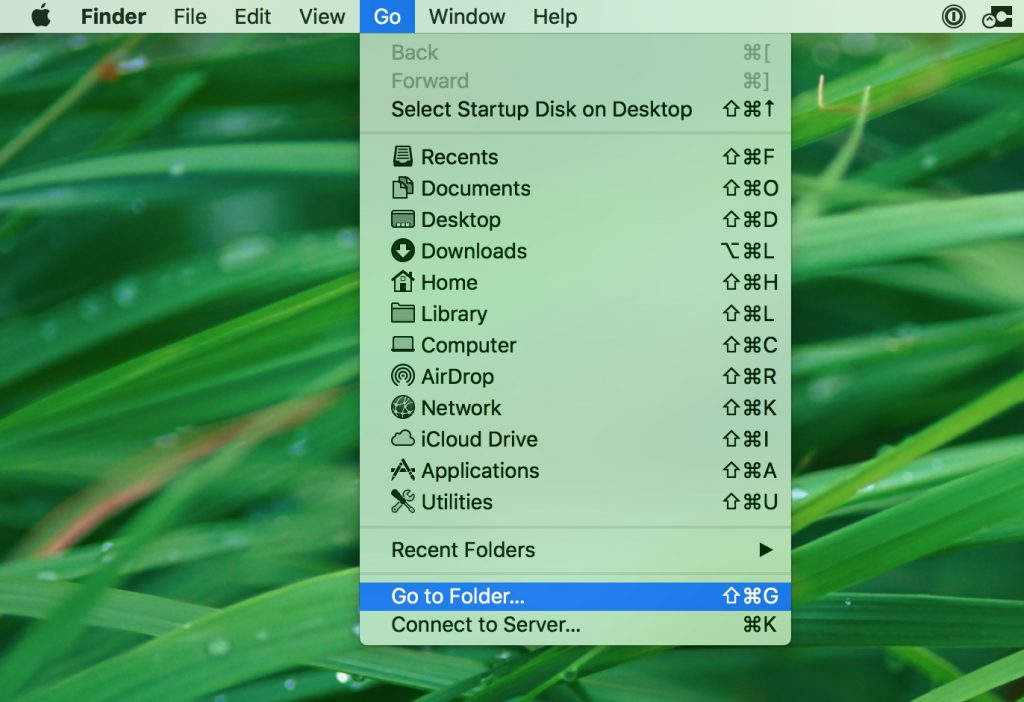
1. Klik på "Gå" og så "Gå til mappe" som vist nedenunder:
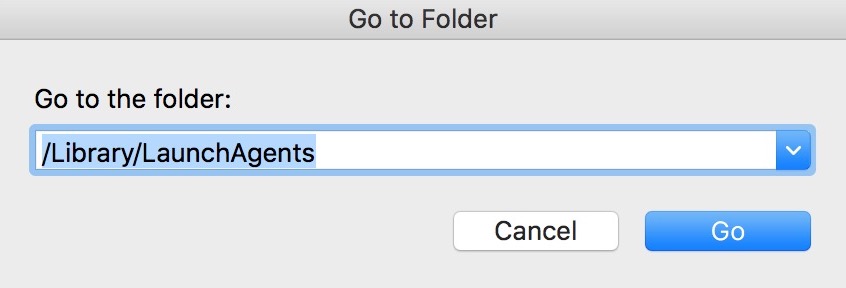
2. Indtaste "/Bibliotek / LauchAgents /" og klik på OK:
3. Slet alle de virus filer, der har lignende eller det samme navn som Cookie Miner. Hvis du mener, der er ingen sådan fil, skal du ikke slette noget.
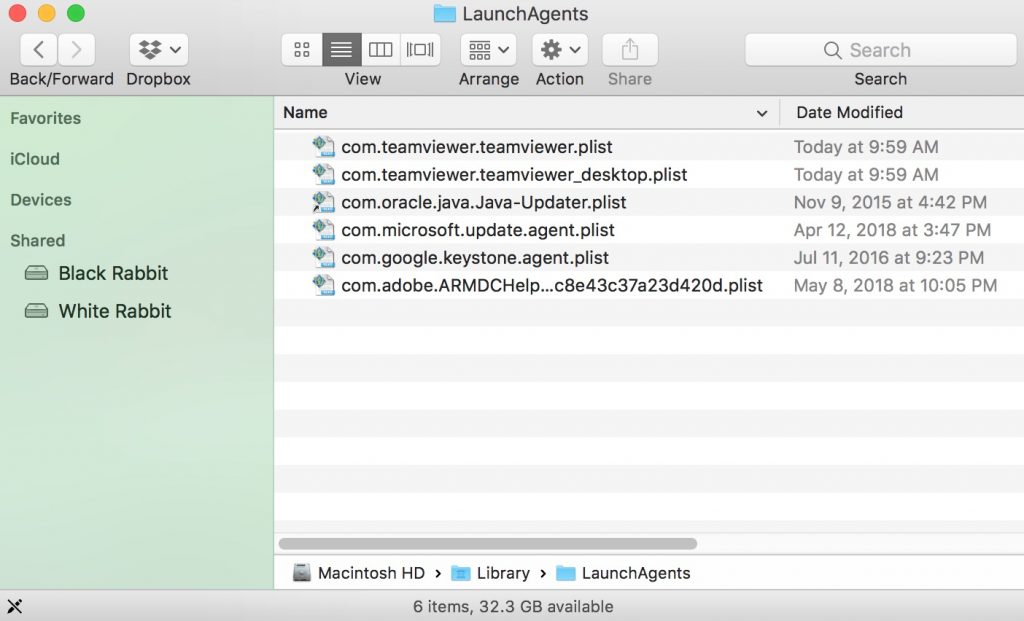
Du kan gentage den samme procedure med følgende andre Bibliotek biblioteker:
→ ~ / Library / LaunchAgents
/Bibliotek / LaunchDaemons
Tip: ~ er der med vilje, fordi det fører til flere LaunchAgents.
Trin 3: Fjern Cookie Miner - relaterede udvidelser fra Safari / Krom / Firefox
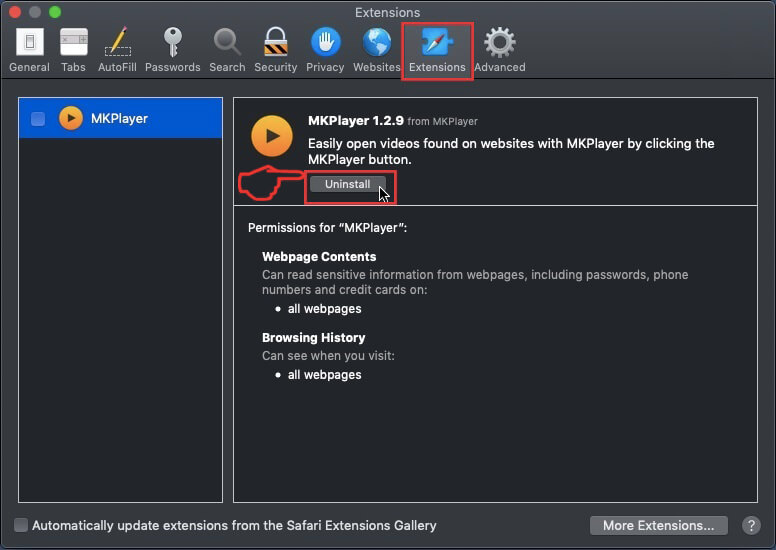
Cookie Miner-FAQ
Hvad er Cookie Miner på din Mac?
Cookie Miner-truslen er sandsynligvis en potentielt uønsket app. Der er også en chance for, at det kan relateres til Mac malware. Hvis ja, sådanne apps har en tendens til at bremse din Mac betydeligt og vise reklamer. De kunne også bruge cookies og andre trackere til at få browserdata fra de installerede webbrowsere på din Mac.
Kan Mac'er få virus?
Ja. Så meget som enhver anden enhed, Apple-computere får malware. Apple-enheder er muligvis ikke et hyppigt mål af malware forfattere, men vær sikker på, at næsten alle Apple-enheder kan blive inficeret med en trussel.
Hvilke typer Mac-trusler er der?
Ifølge de fleste malware-forskere og cybersikkerhedseksperter, den typer af trusler der i øjeblikket kan inficere din Mac, kan være useriøse antivirusprogrammer, adware eller flykaprere (PUP), Trojanske heste, ransomware og crypto-miner malware.
Hvad skal jeg gøre, hvis jeg har en Mac-virus, Like Cookie Miner?
Gå ikke i panik! Du kan let slippe af med de fleste Mac-trusler ved først at isolere dem og derefter fjerne dem. En anbefalet måde at gøre det på er ved at bruge en velrenommeret software til fjernelse af malware der kan tage sig af fjernelsen automatisk for dig.
Der er mange Mac-anti-malware apps derude, som du kan vælge imellem. SpyHunter til Mac er en af de anbefalede Mac-anti-malware-apps, der kan scanne gratis og opdage vira. Dette sparer tid til manuel fjernelse, som du ellers skulle gøre.
How to Secure My Data from Cookie Miner?
Med få enkle handlinger. Først og fremmest, det er bydende nødvendigt, at du følger disse trin:
Trin 1: Find en sikker computer og tilslut det til et andet netværk, ikke den, som din Mac blev inficeret i.
Trin 2: Skift alle dine passwords, startende fra dine e-mail-adgangskoder.
Trin 3: Aktiver to-faktor-autentificering til beskyttelse af dine vigtige konti.
Trin 4: Ring til din bank til ændre dine kreditkortoplysninger (hemmelig kode, etc.) hvis du har gemt dit kreditkort til online shopping eller har foretaget onlineaktiviteter med dit kort.
Trin 5: Sørg for at ring til din internetudbyder (Internetudbyder eller operatør) og bed dem om at ændre din IP-adresse.
Trin 6: Skift din Wi-Fi-adgangskode.
Trin 7: (Valgfri): Sørg for at scanne alle enheder, der er tilsluttet dit netværk for vira, og gentag disse trin for dem, hvis de er berørt.
Trin 8: Installer anti-malware software med realtidsbeskyttelse på alle enheder, du har.
Trin 9: Prøv ikke at downloade software fra websteder, du ikke ved noget om, og hold dig væk fra websteder med lav omdømme i almindelighed.
Hvis du følger disse henstillinger, dit netværk og Apple-enheder bliver betydeligt mere sikre mod enhver trussel eller informationsinvasiv software og også være virusfri og beskyttet i fremtiden.
Flere tip, du kan finde på vores MacOS Virus sektion, hvor du også kan stille spørgsmål og kommentere dine Mac-problemer.
About the Cookie Miner Research
Indholdet udgiver vi på SensorsTechForum.com, this Cookie Miner how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed for at hjælpe dig med at fjerne det specifikke macOS-problem.
How did we conduct the research on Cookie Miner?
Bemærk venligst, at vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om de seneste malware-definitioner, herunder de forskellige typer Mac-trusler, især adware og potentielt uønskede apps (tilfreds).
Endvidere, the research behind the Cookie Miner threat is backed with VirusTotal.
For bedre at forstå truslen fra Mac-malware, Se venligst følgende artikler, som giver kyndige detaljer.



