Update August 2019. Was ist Cookie Miner? Wie Entfernen von Cookies Miner? Wie man aufhört Cookie Miner aus dem Bergbau cryptocurrencies auf Ihrem Mac?
Cookie Miner ist ein Kryptowährung Bergmann Trojan, die Ihren Mac infiziert und beginnt, Informationen zu stehlen, verfolgen Sie Ihre Aktivität und mir für Krypto. Die Mining-Prozesse können Ihren Mac verlangsamen und machen es stottern und frieren auch und wenn Plätzchen Miner für längere Zeit auf dem Mac bleibt kann es sogar Schaden anrichten, um es CPUs (Prozessor) und GPU (Grafikkarte), was kann es brechen. Lesen Sie diesen Artikel erfahren Sie, wie Cookie-Miner von Ihrem Mac entfernen.

Threat Zusammenfassung
| Name | Cookie Miner |
| Art | Miner Trojaner für Mac OS |
| kurze Beschreibung | Zielt darauf ab, schlittern auf Ihrem Mac leise und führen Sie Trojan und Kryptowährung Mining-Aktivitäten. |
| Symptome | Ihr Mac kann erheblich verlangsamen und Sie können beginnen verschiedene unbekannte Prozesse zu sehen, im Hintergrund läuft. |
| Verteilungsmethode | Via verdächtige Downloads, Virus URLs oder bösartiger E-Mail-Spam. |
| Detection Tool |
Überprüfen Sie, ob Ihr System von Malware betroffen ist
Herunterladen
Combireiniger
|
Benutzererfahrung | Abonnieren Sie unseren Forum Cookie-Miner zu Diskutieren. |

Cookie Miner – Wie habe ich es und was tut sie?
Cookie Miner Malware ist, die die privaten Daten von Nutzern stehlen wollen, und öffnen eine Hintertür auf dem infizierten Macs nach dem Download und auch einen Kryptowährung Bergmann läuft.
Es kann Ihren Computer über die folgenden Methoden infiziert;
- Wenn Sie eine Virus-Datei geöffnet haben, werden an eine E-Mail angehängt, wo es vorgibt legitimes Dokument zu sein.
- Wenn Sie das Virus Datei online heruntergeladen haben, wo es gibt vor, eine App oder ein anderes Programm zu sein.
- Wenn Sie als Folge des Besuchs eine Low-Ruf-Website oder mit Adware auf Ihrem Mac auf eine Virusinfektion URL umgeleitet wurden.
So oder so, einmal wurde es auf Ihrem Computer installiert, Das Cookie Miner kann damit beginnen, die folgenden Tätigkeiten auszuführen:
- Erhalten Sie Ihre Cookies, um Informationen von Chrome und Safari.
- Obtain Benutzernamen und Passwörter auf Ihrem Web-Browser gespeichert.
- Stehlen Sie Ihre Finanzdaten (Kreditkarteninformation).
- Erhalten Sie Nachrichten von Ihrem iPhone und anderen Anrufprotokolldaten, die in Ihrer iTunes gesichert wurden.
- Herunterladen und Installieren von anderen Viren über die Hintertür.
- Führen Sie das Kryptowährung Miner-Programm.
Cookie Miner hat die Fähigkeit, Daten aus den folgenden Kreditkarten zu stehlen:
- Visum.
- AMEX.
- MasterCard.
- Entdecken.
Für die Fernsteuerung, Cookie Miner Virus herunterlädt Empyre, Das ist ein Steuerungsinstrument für Mac, das kann in der Kamera tippen, Mikrofon und Relais Screenshots von Ihrem Desktop und an den Hacker als CheckPoint Forscher schicken Bericht.
Der Krypto-Miner-Programm ein Cookie Miner kann auf eine Münze Bergbau Pool verbinden und es ist Hauptziel ist Ihr Mac mit einem Kryptowährung Mining Pool zu verbinden. Dieser Pool von infizierten Computern soll BitCoin oder andere anonyme cryptocurrencies, indem sie ihre Ressourcen generieren. Also, ohne dass Sie es zu merken, die Gauner Geld von Ihrem Mac leise überbeanspruchend. Das einzige, was es zu verraten ist, dass Ihr Mac wird deutlich langsamer.

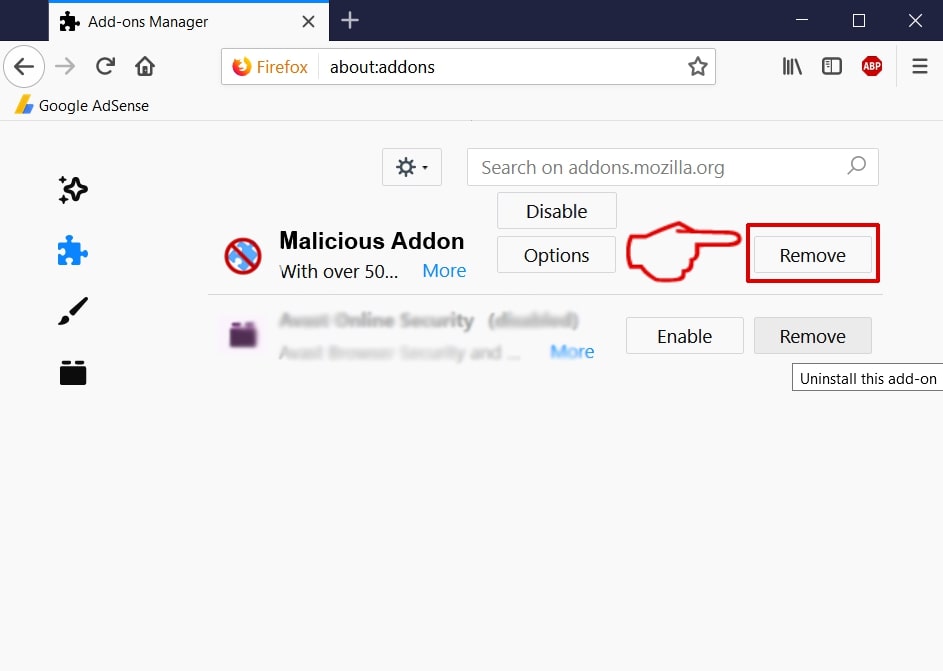
Entfernen Sie Cookie-Miner Trojan von Ihrem Mac
Um diese Malware von Ihrem Mac zu entfernen, Wir empfehlen dringend, dass Sie die Anweisungen in diesem Artikel lesen. Sie wurden mit dem alleinigen Zweck, damit Sie diesen Virus von Ihrem Mac Schritt effektiv Schritt löschen gemacht. Für maximale Wirksamkeit, Wir empfehlen dringend, dass Sie einen Scan Ihres Mac mit einem professionellen Malware Cleaner für Mac herunterladen und ausführen. Eine solche Software soll automatisch alle Objekte auf dem Mac erkennen und löschen Sie sie dann gründlich.
Schritte zur Vorbereitung vor dem Entfernen:
Vor dem Starten Sie die folgenden Schritte folgen, darauf hingewiesen werden, dass Sie sollten zunächst die folgenden Vorbereitungen tun:
- Sichern Sie Ihre Dateien, falls das Schlimmste passiert.
- Achten Sie darauf, ein Gerät mit dieser Anleitung auf standy haben.
- Bewaffnen Sie sich mit Geduld.
- 1. Suchen Sie nach Mac-Malware
- 2. Deinstallieren Sie riskante Apps
- 3. Bereinigen Sie Ihre Browser
Schritt 1: Suchen Sie nach Cookie Miner-Dateien und entfernen Sie sie von Ihrem Mac
Wenn Sie mit Problemen konfrontiert, auf Ihrem Mac als Folge unerwünschten Skripte und Programme wie Cookie-Miner, der empfohlene Weg, um die Bedrohung zu beseitigen ist durch ein Anti-Malware-Programm. SpyHunter für Mac bietet erweiterte Sicherheitsfunktionen sowie andere Module, die die Sicherheit Ihres Mac verbessern und ihn in Zukunft schützen.
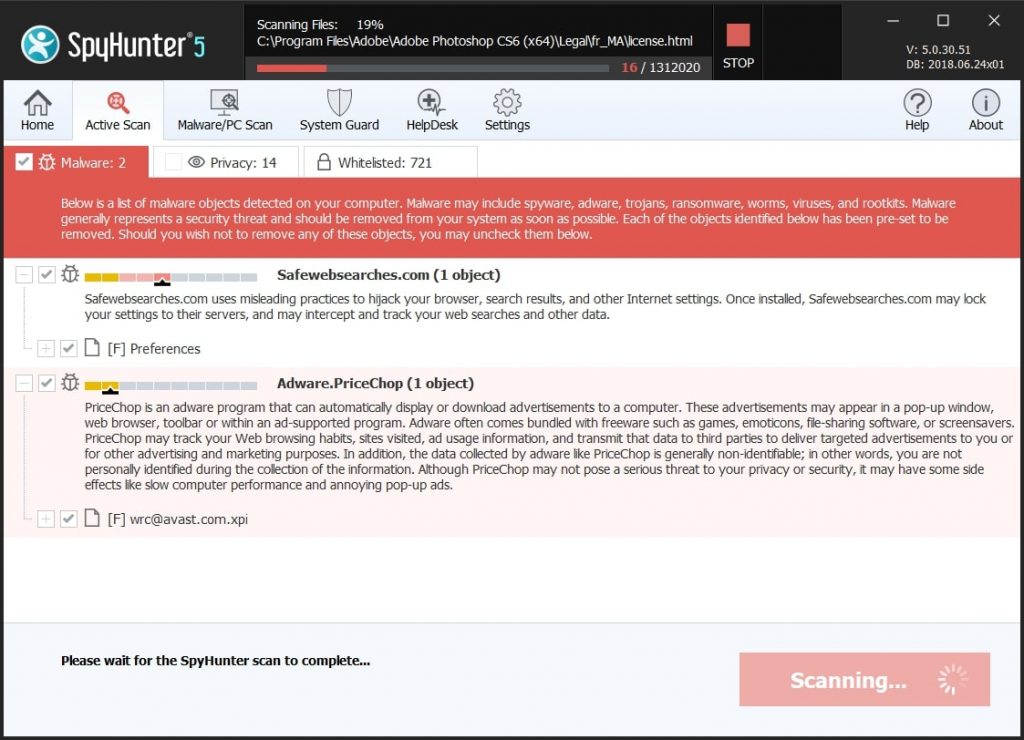
Schnelle und einfache Anleitung zum Entfernen von Mac-Malware-Videos
Bonusschritt: So machen Sie Ihren Mac schneller?
Mac-Rechner unterhalten wahrscheinlich das schnellste Betriebssystem auf dem Markt. Noch, Macs werden manchmal langsam und träge. Die folgende Videoanleitung untersucht alle möglichen Probleme, die dazu führen können, dass Ihr Mac langsamer als gewöhnlich ist, sowie alle Schritte, die Ihnen helfen können, Ihren Mac zu beschleunigen.
Schritt 2: Deinstallieren Sie Cookie Miner und entfernen Sie zugehörige Dateien und Objekte
1. hit the ⇧ + ⌘ + U Tasten zum Öffnen von Dienstprogrammen. Eine andere Möglichkeit besteht darin, auf „Los“ zu klicken und dann auf „Dienstprogramme“ zu klicken., wie das Bild unten zeigt:
2. Suchen Sie den Aktivitätsmonitor und doppelklicken Sie darauf:
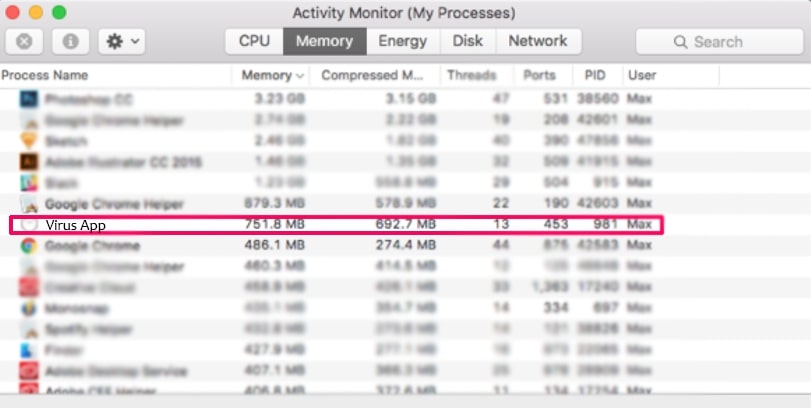
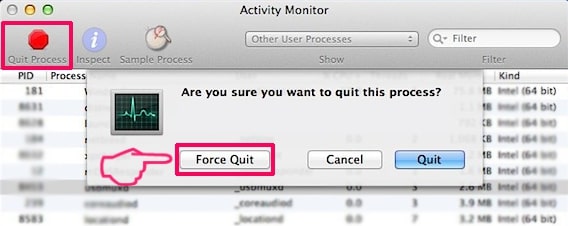
3. Im Activity Monitor sucht verdächtige Prozesse, gehören, oder in Verbindung mit Cookie-Miner:
4. Klicken Sie auf die "Gehen" Taste erneut, aber diesmal wählen Sie Anwendungen. Eine andere Möglichkeit ist mit den ⇧+⌘+A Tasten.
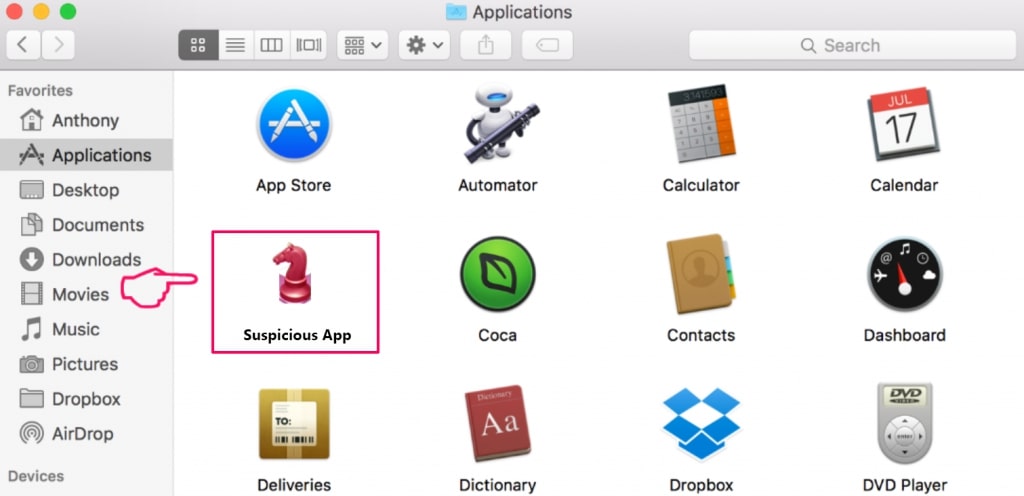
5. Im Menü Anwendungen, sucht jede verdächtige App oder eine App mit einem Namen, ähnlich oder identisch mit Cookie-Miner. Wenn Sie es finden, Klicken Sie mit der rechten Maustaste auf die App und wählen Sie "In den Papierkorb verschieben".
6. Wählen Accounts, Danach klicken Sie auf die Login Artikel Vorliebe. Ihr Mac zeigt Ihnen dann eine Liste der Elemente, die automatisch gestartet werden, wenn Sie sich einloggen. Suchen Sie nach verdächtigen Anwendungen identisch oder ähnlich Plätzchen Miner. Aktivieren Sie die App, deren automatische Ausführung Sie beenden möchten, und wählen Sie dann auf aus Minus („-“) Symbol, um es zu verstecken.
7. Entfernen Sie alle verbleibenden Dateien, die möglicherweise mit dieser Bedrohung zusammenhängen, manuell, indem Sie die folgenden Teilschritte ausführen:
- Gehe zu Finder.
- In der Suchleiste den Namen der Anwendung, die Sie entfernen möchten,.
- Oberhalb der Suchleiste ändern, um die zwei Drop-Down-Menüs "Systemdateien" und "Sind inklusive" so dass Sie alle Dateien im Zusammenhang mit der Anwendung sehen können, das Sie entfernen möchten. Beachten Sie, dass einige der Dateien nicht in der App in Beziehung gesetzt werden kann, so sehr vorsichtig sein, welche Dateien Sie löschen.
- Wenn alle Dateien sind verwandte, halte das ⌘ + A Tasten, um sie auszuwählen und fahren sie dann zu "Müll".
Für den Fall, können Sie nicht entfernen Cookie-Miner über Schritt 1 über:
Für den Fall, können Sie nicht die Virus-Dateien und Objekten in Ihren Anwendungen oder an anderen Orten finden wir oben gezeigt haben, Sie können in den Bibliotheken Ihres Mac für sie manuell suchen. Doch bevor dies zu tun, bitte den Disclaimer unten lesen:
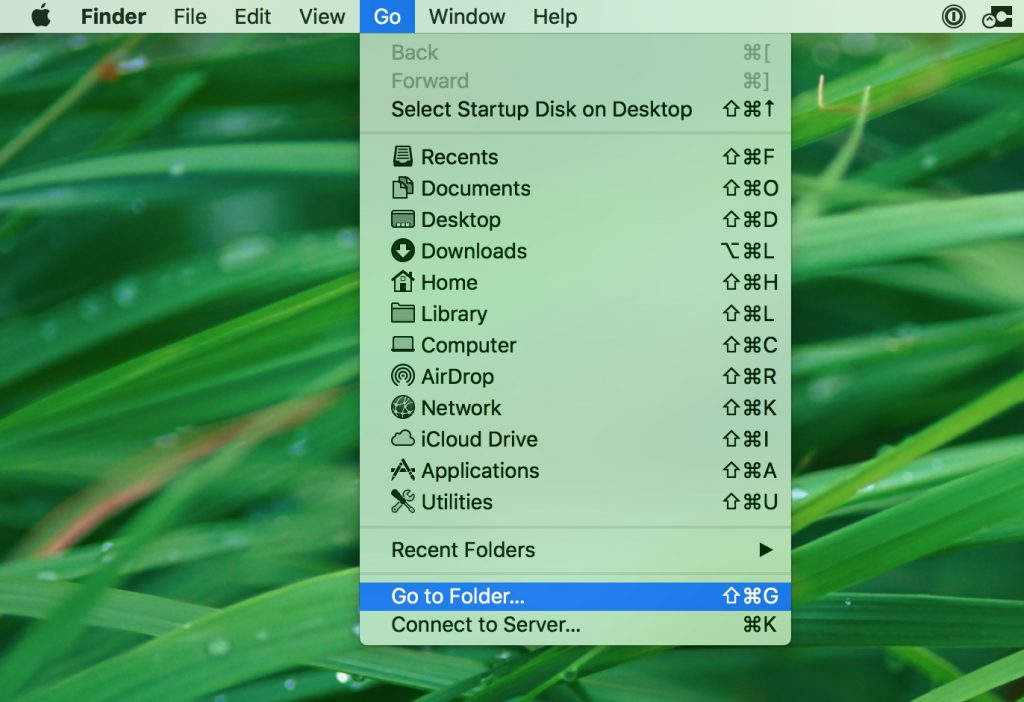
1. Klicke auf "Gehen" und dann "Gehe zum Ordner" wie gezeigt unter:
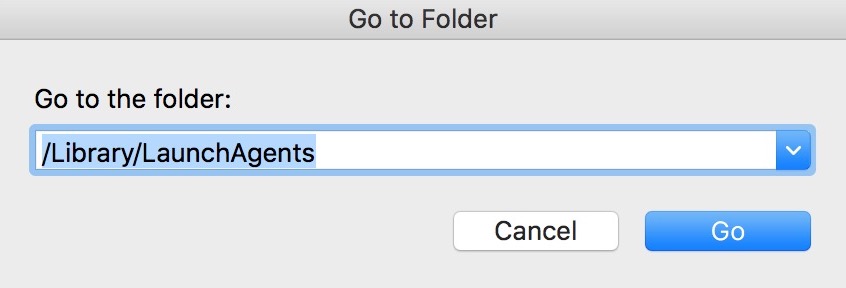
2. Eintippen "/Library / LauchAgents /" und klicke auf Ok:
3. Löschen Sie alle die Virus-Dateien, die ähnlich oder die gleichen Namen wie Cookie-Miner haben. Wenn Sie glauben, dass es keine solche Datei, lösche nichts.
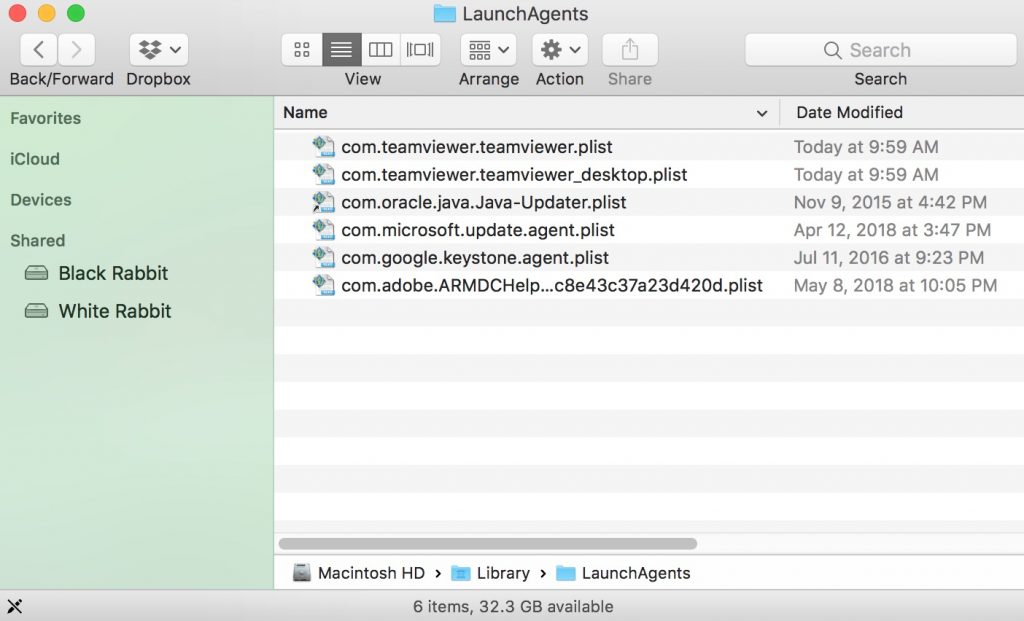
Sie können die gleiche Prozedur mit den folgenden anderen Bibliothek Verzeichnisse wiederholen:
→ ~ / Library / Launchagents
/Library / LaunchDaemons
Spitze: ~ ist es absichtlich, denn es führt mehr LaunchAgents- zu.
Schritt 3: Entfernen Sie Cookie Miner-bezogene Erweiterungen aus Safari / Chrom / Firefox
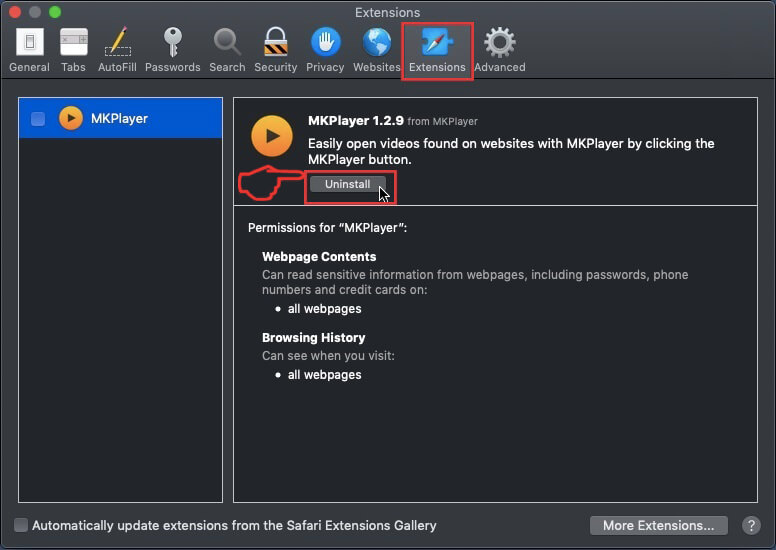
Cookie Miner-FAQ
Was ist Cookie Miner auf Ihrem Mac??
Die Cookie-Miner-Bedrohung ist wahrscheinlich eine potenziell unerwünschte App. Es besteht auch die Möglichkeit, dass es damit zusammenhängt Mac Malware. Wenn dem so ist, Solche Apps neigen dazu, Ihren Mac erheblich zu verlangsamen und Werbung anzuzeigen. Sie können auch Cookies und andere Tracker verwenden, um Browserinformationen von den auf Ihrem Mac installierten Webbrowsern abzurufen.
Können Macs Viren bekommen??
Ja. So viel wie jedes andere Gerät, Apple-Computer bekommen Malware. Apple-Geräte sind möglicherweise kein häufiges Ziel von Malware Autoren, Aber seien Sie versichert, dass fast alle Apple-Geräte mit einer Bedrohung infiziert werden können.
Welche Arten von Mac-Bedrohungen gibt es??
Laut den meisten Malware-Forschern und Cyber-Sicherheitsexperten, die Arten von Bedrohungen Bei Viren, die derzeit Ihren Mac infizieren können, kann es sich um betrügerische Antivirenprogramme handeln, Adware oder Entführer (PUPs), Trojanische Pferde, Ransomware und Krypto-Miner-Malware.
Was tun, wenn ich einen Mac-Virus habe?, Like Cookie Miner?
Keine Panik! Sie können die meisten Mac-Bedrohungen leicht beseitigen, indem Sie sie zuerst isolieren und dann entfernen. Ein empfehlenswerter Weg, dies zu tun, ist die Verwendung eines seriösen Anbieters Software zum Entfernen von Schadsoftware Das kann die Entfernung automatisch für Sie erledigen.
Es gibt viele Anti-Malware-Apps für Mac, aus denen Sie auswählen können. SpyHunter für Mac ist eine der empfohlenen Mac-Anti-Malware-Apps, das kann kostenlos scannen und alle Viren erkennen. Dies spart Zeit für das manuelle Entfernen, das Sie sonst durchführen müssten.
How to Secure My Data from Cookie Miner?
Mit wenigen einfachen Aktionen. Zuallererst, Befolgen Sie unbedingt diese Schritte:
Schritt 1: Finden Sie einen sicheren Computer und verbinden Sie es mit einem anderen Netzwerk, nicht der, mit dem Ihr Mac infiziert war.
Schritt 2: Ändern Sie alle Ihre Passwörter, ausgehend von Ihren E-Mail-Passwörtern.
Schritt 3: Aktivieren Zwei-Faktor-Authentifizierung zum Schutz Ihrer wichtigen Konten.
Schritt 4: Rufen Sie Ihre Bank an Ändern Sie Ihre Kreditkartendaten (Geheim Code, usw.) wenn Sie Ihre Kreditkarte für Online-Einkäufe gespeichert oder Online-Aktivitäten mit Ihrer Karte durchgeführt haben.
Schritt 5: Stellen Sie sicher, dass Rufen Sie Ihren ISP an (Internetprovider oder -anbieter) und bitten Sie sie, Ihre IP-Adresse zu ändern.
Schritt 6: Ändere dein WLAN Passwort.
Schritt 7: (Fakultativ): Stellen Sie sicher, dass Sie alle mit Ihrem Netzwerk verbundenen Geräte auf Viren prüfen und diese Schritte wiederholen, wenn sie betroffen sind.
Schritt 8: Installieren Sie Anti-Malware Software mit Echtzeitschutz auf jedem Gerät, das Sie haben.
Schritt 9: Versuchen Sie, keine Software von Websites herunterzuladen, von denen Sie nichts wissen, und halten Sie sich von diesen fern Websites mit geringer Reputation im allgemeinen.
Wenn Sie diesen Empfehlungen folgen, Ihr Netzwerk und Ihre Apple-Geräte werden wesentlich sicherer vor Bedrohungen oder informationsinvasiver Software und auch in Zukunft virenfrei und geschützt.
Weitere Tipps finden Sie auf unserer MacOS-Virus-Bereich, Hier können Sie auch Fragen stellen und Kommentare zu Ihren Mac-Problemen abgeben.
Über die Cookie-Miner-Forschung
Die Inhalte, die wir auf SensorsTechForum.com veröffentlichen, Diese Anleitung zum Entfernen von Cookie Miner ist enthalten, ist das Ergebnis umfangreicher Recherchen, harte Arbeit und die Hingabe unseres Teams, um Ihnen bei der Behebung des spezifischen macOS-Problems zu helfen.
Wie haben wir die Recherche zu Cookie Miner durchgeführt??
Bitte beachten Sie, dass unsere Forschung auf einer unabhängigen Untersuchung basiert. Wir stehen in Kontakt mit unabhängigen Sicherheitsforschern, Dank dessen erhalten wir täglich Updates zu den neuesten Malware-Definitionen, einschließlich der verschiedenen Arten von Mac-Bedrohungen, insbesondere Adware und potenziell unerwünschte Apps (zufrieden).
Weiter, die Forschung hinter der Cookie-Miner-Bedrohung wird unterstützt Virustotal.
Um die Bedrohung durch Mac-Malware besser zu verstehen, Bitte lesen Sie die folgenden Artikel, die sachkundige Details bieten.



