Un equipo de investigadores presentó un software malicioso concepto llamada la red de bots BlackIoT que se puede utilizar en dispositivos selectivos contra ataques de IO en una escala mundial. Los detalles sobre la amenaza están disponibles en una presentación principal presentada en una conferencia de seguridad..
Los investigadores proponen que el concepto de botnet BlackIoT puede ser un arma devastadora
Un grupo de investigadores presentó un nuevo concepto de malware en la Simposio de seguridad de Usenix esta semana llamada botnet BlackIoT. Es una ofensiva teórica que aún no está disponible como código ejecutable que pueda usarse en ataques del mundo real.. Una de las razones propuestas para crear el modelo teórico es el vasto despliegue de dispositivos IoT tanto por parte de los usuarios finales como en entornos empresariales que sirven para diversos propósitos.. Hay tres tipos de ataques distintos que se describen en la sinopsis y brindan información sobre cómo se puede implementar en un intento de intrusión.. Van desde ataques básicos (manipular configuraciones individuales) a modificaciones de dispositivos más complejas.
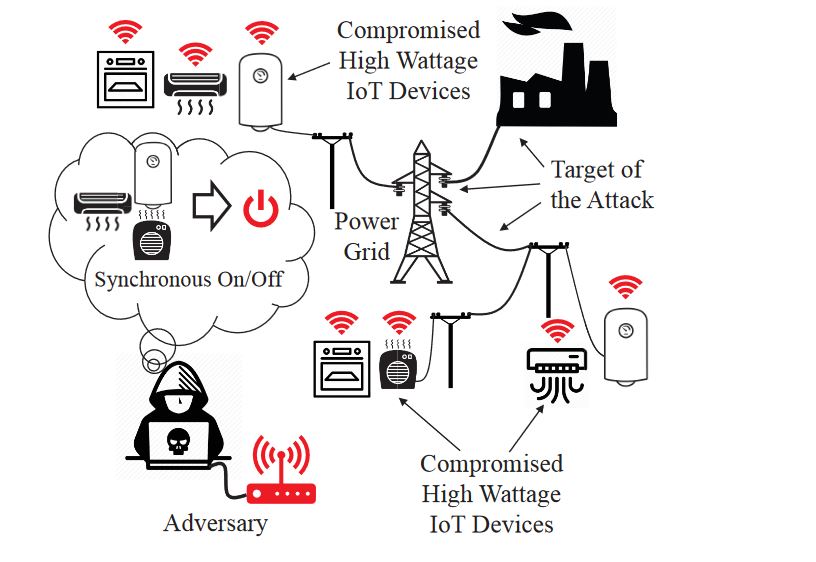
Una característica importante del modelo BlackIoT es que su uso puede dirigirse a la infraestructura crítica., Los sistemas de ejemplo que pueden manipularse incluyen sistemas de redes eléctricas y control de agua.. La botnet BlackIoT también puede desencadenar un ataque de red a los dispositivos de los consumidores, provocando un aumento repentino en el consumo de energía. Este ataque indirecto se basa en un modelo de sabotaje que es otro enfoque teórico para causar daños generalizados.. Se han realizado varias simulaciones que demuestran que si se implementan en un escenario del mundo real, el daño inminente sería digno de preparar defensas adecuadas..
Hay varios factores que se requieren para acumular la energía necesaria para eliminar redes completas de dispositivos IoT.: una gran cantidad de hosts infectados que pueden aprovechar la botnet maliciosa. Para una mayor eficiencia, los anfitriones deben estar ubicados en la misma área geográfica.. Otro conjunto de factores incluye el hecho de que llevaría algún tiempo (para ciertos equipos de IoT) para derribarlos. La seguridad de red adaptable puede bloquear dichos intentos automáticamente si se configura correctamente.
El descrito dentro del ataque se llama Manipulación de la demanda a través de IoT abreviado a MadIoT. Usando las simulaciones, los ataques pueden resultar tanto en cortes locales como en apagones a gran escala.. Un efecto alternativo es el aumento de los costos operativos de una red eléctrica que puede impulsar los gastos en el mercado eléctrico..
El trabajo de investigación se puede descargar desde Esta dirección.


