A group of researchers presented a concept malware called the BlackIoT botnet which can be used in targeted attacks against IoT devices on a global scale. Details about the threat are available in a keynote presentation presented at a security conference.
Researchers Propose That the Concept BlackIoT Botnet Can Be a Devastating Weapon
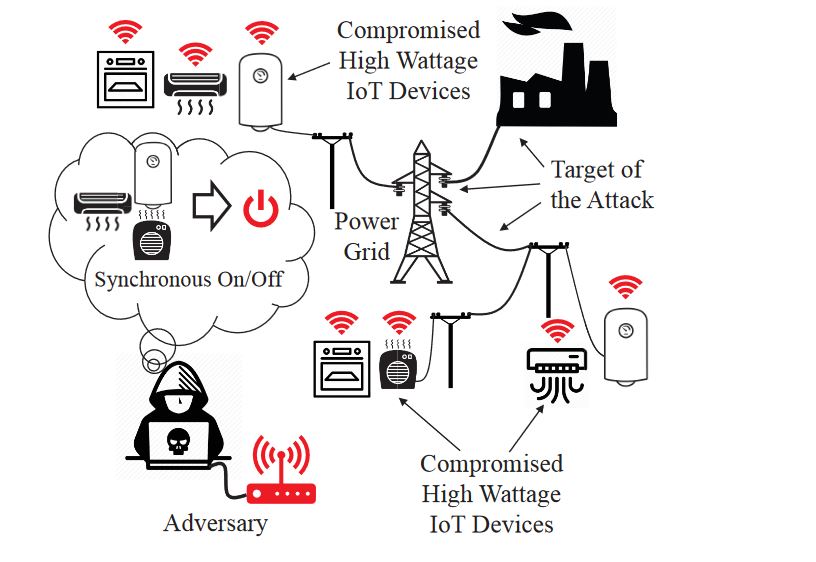
A group of researchers presented a new concept malware at the Usenix Security Symposium this week called the BlackIoT botnet. It is a theoretical offensive that is still not available as an executable code that can be used in real-world attacks. One of the proposed reasons for creating the theoretical model is the vast deployment of IoT devices both by end users and in business environments serving various purposes. There are three distinct attack types that are described in the synopsis giving information on how it can be implemented in an intrusion attempt. They range from basic attacks (manipulating single settings) to more complex device modifications.
An important characteristic of the BlackIoT model is that its use can be targeted against critical infrastructure, example systems that can be manipulated include power grid systems and water control. The BlackIoT botnet can also trigger a network attack on consumer devices thereby triggering a sudden increase in power consumption. This indirect attack is based on a sabotage model that is another theoretical approach in causing widespread damage. Several simulations have been made proving that if implemented in a real-world scenario the impending damage would be worthy of preparing adequate defenses.
There are several factors that are required in order to amass the required power to take out whole networks of IoT devices: a large number of infected hosts that can leverage the malicious botnet. For higher efficiency the hosts should be located in the same geographic area. Another set of factors include the fact that it would take some time (for certain IoT equipment) to take them down. Adaptive network security can block such attempts automatically if configured properly.
The described within attack is called Manipulation of demand via IoT shortened to MadIoT. Using the simulations the attacks can result both in local outages and large-scale blackouts. An alternative effect is the increase of operating costs of a power grid which can drive the expenses in the electricity market.
The research paper can be downloaded from this address.


