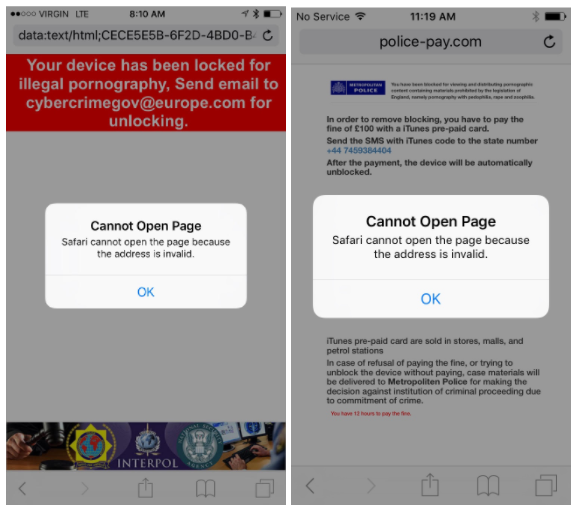
As tentativas de scareware de ransomware baseadas nos usuários que visualizam conteúdo adulto não são algo novo, mas costumam ter sucesso. Uma nova campanha desse tipo foi detectada recentemente por pesquisadores da Lookout no navegador iOS Mobile Safari, extorquir dinheiro de usuários que visualizaram conteúdo obsceno em seus dispositivos. Felizmente, a vulnerabilidade que levou aos ataques foi corrigida no patch do iOS de segunda-feira.
Como foi feita a campanha?
o ransomware / campanha de scareware foi construída em uma vulnerabilidade que envolvia a maneira como o Safari exibia pop-ups JavaScript. Os invasores exploraram o manuseio dessas caixas de diálogo pop-up no Mobile Safari, impedindo o usuário de usar o navegador. Durante esse tempo, uma ameaça (daí o nome scareware desta tática) mensagem seria exibida para forçar a vítima a pagar. A vítima seria bloqueada até que o resgate fosse pago na forma de um vale-presente do iTunes.
relacionado: Como bloquear Activation iOS da Bypass Apple em iPhone e iPad
Contudo, Como explicado por Lookout:
Um usuário experiente pode restaurar a funcionalidade do Mobile Safari limpando o cache do navegador por meio das configurações do iOS - o ataque não criptografa nenhum dado e o mantém como resgate. Seu objetivo é assustar a vítima para que pague para desbloquear o navegador antes que ela perceba que não precisa pagar o resgate para recuperar dados ou acessar o navegador.
Felizmente, a superfície de ataque foi totalmente erradicada com o iOS 10.3 remendo. O patch mudou a maneira como o Mobile Safari lida com as caixas de diálogo pop-up do site, “tornando-os por guia em vez de assumir todo o aplicativo”.
O ataque foi originalmente relatado ao suporte da Lookout por um dos usuários da empresa executando o iOS 10.2. O usuário disse que perdeu o controle sobre seu navegador depois de visitar um site. Pesquisadores dizem que ataques baseados neste código parecem ter sido desenvolvidos para versões mais antigas do iOS, como iOS 8. Contudo, a exploração de diálogos pop-up ainda era possível até o iOS 10.3.
além do que, além do mais, é muito provável que os golpistas por trás dessa campanha de scareware tenham comprado uma grande quantidade de domínios na tentativa de capturar vítimas em potencial que procuram conteúdo explícito.