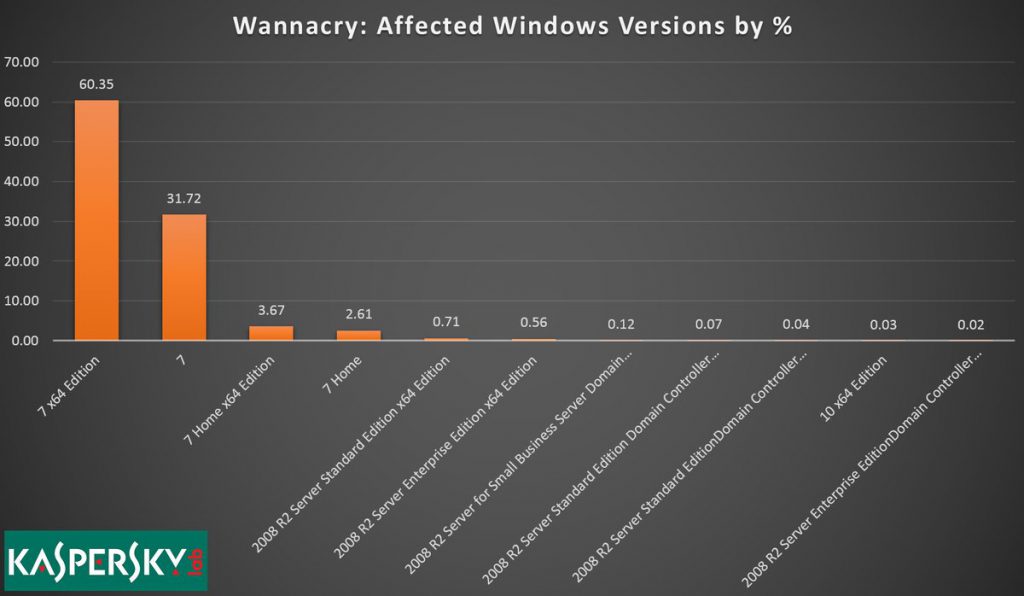
As estatísticas da Kaspersky Lab indicam que o WannaCry ataca no Windows 7 representaram 98% do número total de infecções. Mais particularmente, sobre 60% dos sistemas atacados pelo WannaCry estavam executando a versão de 64 bits do Windows 7, enquanto que 32% das vítimas estavam na versão de 32 bits do sistema operacional. Esta notícia não é surpreendente porque o Windows 7 ainda é o sistema operacional de desktop preferido, com uma participação de mercado próxima de 50%.
janelas 7: Taxas mais altas de infecção de ransomware WannaCry
O que é paradoxal aqui é que o Windows 7 deveria estar protegido contra a campanha de ransomware WannaCry porque a Microsoft lançou patches para interromper a infecção em março deste ano. Mas como acabou - não foi, e foi massivamente atingido.
A popularidade do sistema operacional quase significa que aproximadamente 1 no 2 as máquinas ainda estão no Windows 7, ilustrando facilmente as altas taxas de infecção. Infelizmente, ainda é um sistema operacional muito pirateado, o que significa que milhões de usuários estão executando software pirata, particularmente em países como Rússia e China. Escusado será dizer, executar cópias do sistema operacional que não sejam originais é muito perigoso - na maioria dos casos, elas não podem ser atualizadas porque os usuários interromperam as atualizações para evitar que a cópia verifique as chaves de produto originais.
Mesmo que o Windows 7 será suportado até janeiro 2020, os usuários que o executam podem querer começar a pensar em migrar para uma versão mais recente, especialistas em segurança aconselham. Obter as atualizações de segurança mais recentes o mais rápido possível também é crucial para a segurança contra ataques como o WannaCry.
“oops, seus arquivos importantes são criptografados”É o que as vítimas do WannaCry veem depois que seus computadores são infectados. Uma vez que isso aconteceu, a infecção do ransomware começa a anexar algoritmos de criptografia para tornar os documentos nos computadores afetados não legíveis. Então, !Por favor Read Me!.O arquivo txt é descartado no alvo com o objetivo de fazer com que as vítimas baixem um descriptografador de uma conta de caixa de depósito. Finalmente, as demandas de ransomware 300$ no pagamento BTC para obter os dados de volta.