
I denne digitale tidsalder, Vi stoler meget på teknologi og pc'er er massivt bruges på daglig basis. Dette behov har skubbet malware forfattere til at kode forskellige typer af malware til at tjene deres interesser. Det er derfor, det er vigtigt at have den viden til at registrere og fjerne sporene af sådanne filer fra din computer.
Før vi begynder
Du skal vide, at situationer kan variere, når ondsindede filer er genstand for fjernelse. Der er skadelige filer af programmer, der ikke venligt generelt, men er ikke malware, og der er programmer, der er malware, installeres direkte på ofrets computer. Vi vil give fjernelse metoder til både, men kraftigste råde brugerne til at sikkerhedskopiere deres data, fordi vi holder ikke noget ansvar for resultatet på grund af hvordan variable er situationen.
Skadelige filer, der ikke Malware
Indirekte skadelige filer af denne type er generelt nemme at fjerne, men de kan frembyde vanskeligheder i nogle situationer så godt. Dette er fordi de kan være skjult i forskellige mapper og kan indstilles til at køre og gendanne sig selv efter sletning hver gang Windows genstarter. Således, før du fjerner disse filer, du nødt til at stoppe dem som aktive Windows Processer.
Trin 1: Stoppe en aktiv proces
1)Højreklik på din Windows-værktøjslinjen, og vælg “Start Jobliste” eller “Task Manager” (Afhænger hvilken Windows-version du kører).
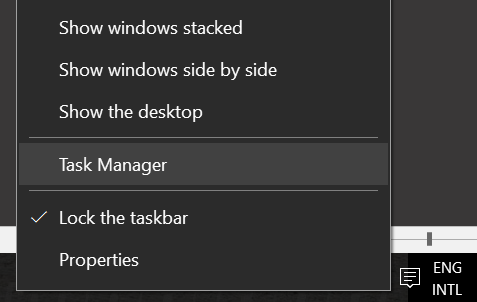
2)Kig efter en mistænkelig proces ved at gå til “Detaljer” fanen din Task Manager.
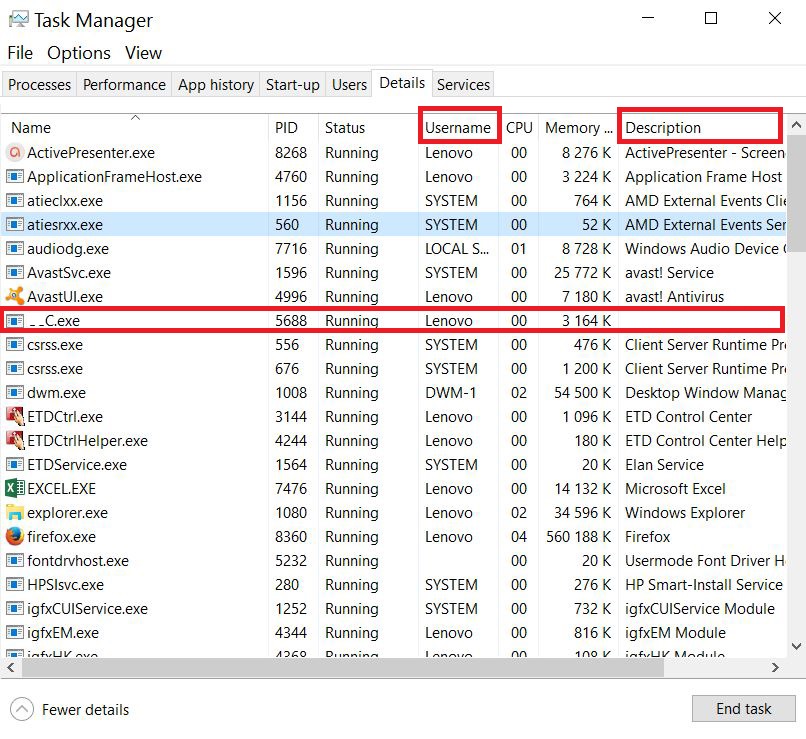
NB. For at finde mistænkelige processer, du skal se primært Beskrivelse og Brugernavn Tabs i den skadelige proces for at identificere det. Desuden, til det, er det stærkt anbefales at henvise med den berygtede Proces Bibliotek som har oplysninger om Windows-processer.
3)Finde placeringen af processen ved højreklikke på den og vælge "Åbn filplacering".
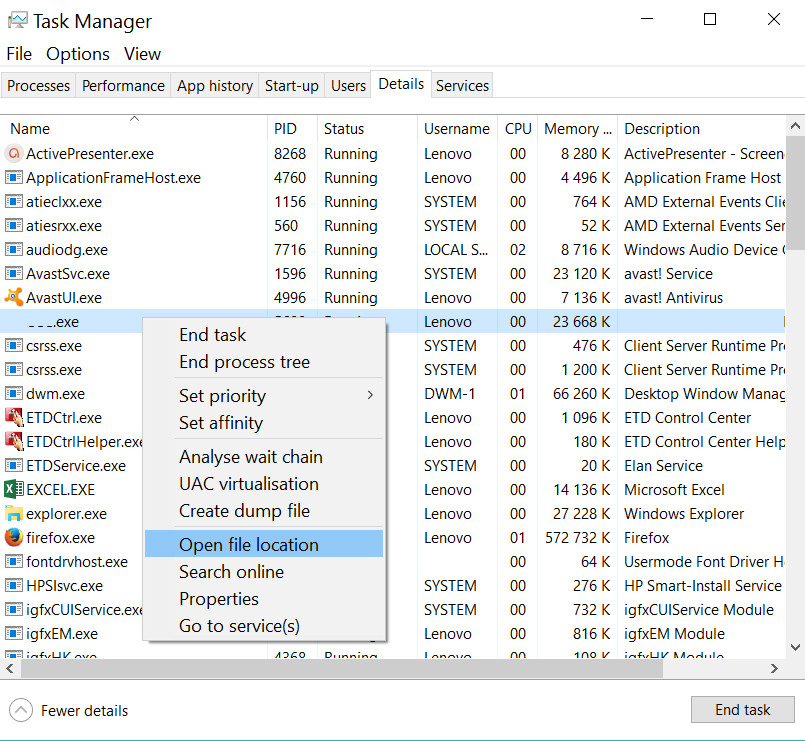
4)Endelig, stoppe processen ved igen højreklikke det i Task-manager og vælge "Afslut proces."
5)Slet alle associerede filer i mappen. Hvis nogle filer ikke kan slettes, bruge en af metoderne i Slet Doctor - gratis software, der kan slette en fil i Windows.
Skadelige filer, der Malware
For ondsindede filer, situationen kan temmelig kompliceret. Første, du har brug for at vide, hvad du har at gøre med. Er malware en orm, og virus, ransomware eller en trojansk hest? Whatever the case may be, er det vigtigt at vide, at malware bruger lusket taktik for at være skjult på dit system.
En af den taktik, der bruges af malware er at maskere sig som legitime Windows processer eller programmer, der er godt kendt. De processer, der ofte efterlignede er:
- svchost.exe
- System.Exe
- notepad.exe
- Explorer.exe
- Winlogon.exe
- WindowsUpdate.exe
Endvidere, malware kan indsætte skadelig kode i legitime Windows Processer til at oprette exploits eller stoppe forsvar. Nogle malware moduler kan endda have evnen til at skjule proces, som om det var aldrig der fra Windows Task Manager.
Den malware bruger normalt følgende mapper til at droppe sine skadelige filer:
- %Bruger%
- %Brugere%
- %AppData%
- %Roaming%
- %System%
- %System32%
- %Temp%
- %Lokal%
Da forskellige malware kan have evnen til at oprette forbindelse til aktive værter og skabe mere end en ondsindet proces eller migrere en proces, når det er blevet opdaget, Vi kan varmt anbefale at bruge et avanceret anti-malware værktøj til at scanne efter og fjerne alle skadelige objekter, der er forbundet.
At korrekt og effektivt scanne din computer, det første skridt er at isolere malware ved at stoppe internetforbindelsen. Derefter, er det tilrådeligt at hente anti-malware-software fra en ren enhed.
SpyHunter scanner vil kun afsløre truslen. Hvis du ønsker, at truslen skal fjernes automatisk, du nødt til at købe den fulde version af anti-malware værktøj.Læs mere om SpyHunter Anti-Malware værktøj / Sådan fjernes SpyHunter
Det er stærkt foretrukket at anvende en offline installatør med de seneste opdateringer allerede er installeret, fordi du bliver nødt til at opdatere anti-malware værktøj senere. Når du har installeret anti-malware værktøj, starte din PC i fejlsikret tilstand. Hvis det ikke har opdateret, starte den op i fejlsikret tilstand med netværk. For mere information om, hvordan til at starte i fejlsikret tilstand, henvises til senere nævnte tutorial.
1. Boot din pc i fejlsikret tilstand for at isolere og fjerne skadelig software
1. Boot din PC i fejlsikret tilstand
 1. For Windows 7, XP og Vista.
1. For Windows 7, XP og Vista. 2. For Windows 8, 8.1 og 10.
2. For Windows 8, 8.1 og 10.
I Windows XP, Vista, 7 systemer:
1. Fjern alle cd'er og dvd'er, og derefter Genstart pc'en fra “Start” menu.
2. Vælg en af de to muligheder, der nedenfor:
– For pc'er med et enkelt operativsystem: Tryk “F8” gentagne gange efter den første boot-skærmen dukker op i løbet af genstart af din computer. I tilfælde af Windows-logoet vises på skærmen, du er nødt til at gentage den samme opgave igen.

– For pc'er med flere operativsystemer: Тhe piletasterne vil hjælpe dig med at vælge det operativsystem, du foretrækker at starte i Fejlsikret tilstand. Tryk “F8” lige som beskrevet for et enkelt operativsystem.
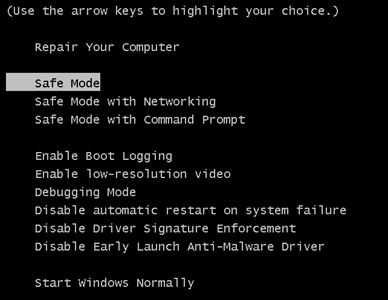
3. Som “Avancerede startindstillinger” vises, vælg Fejlsikret tilstand ønskede indstilling ved hjælp af piletasterne. Som du gøre dit valg, presse “Indtast“.
4. Log på computeren ved hjælp af din administratorkonto
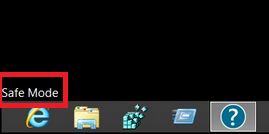
Mens computeren er i fejlsikret tilstand, ordene “Fejlsikret tilstand” vises i alle fire hjørner af skærmen.
Trin 1: Åbn Start Menu
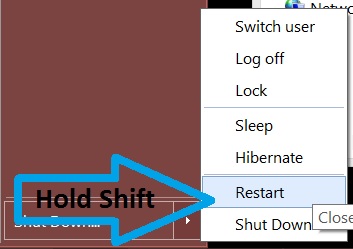
Trin 2: Mens holde Shift knap, Klik på Magt og klik derefter på Genstart.
Trin 3: Efter genstart, den aftermentioned menuen vises. Derfra skal du vælge Fejlfinde.
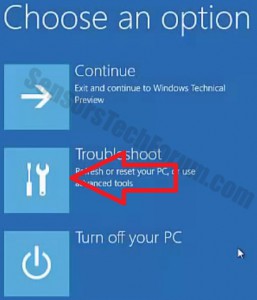
Trin 4: Du vil se Fejlfinde menu. Fra denne menu kan du vælge Avancerede indstillinger.
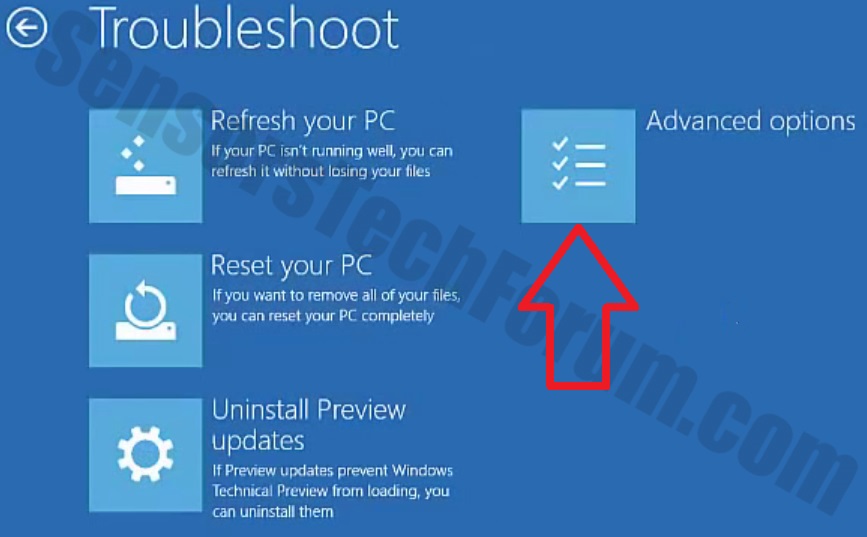
Trin 5: Efter Avancerede indstillinger menu vises, Klik på Startup Indstillinger.
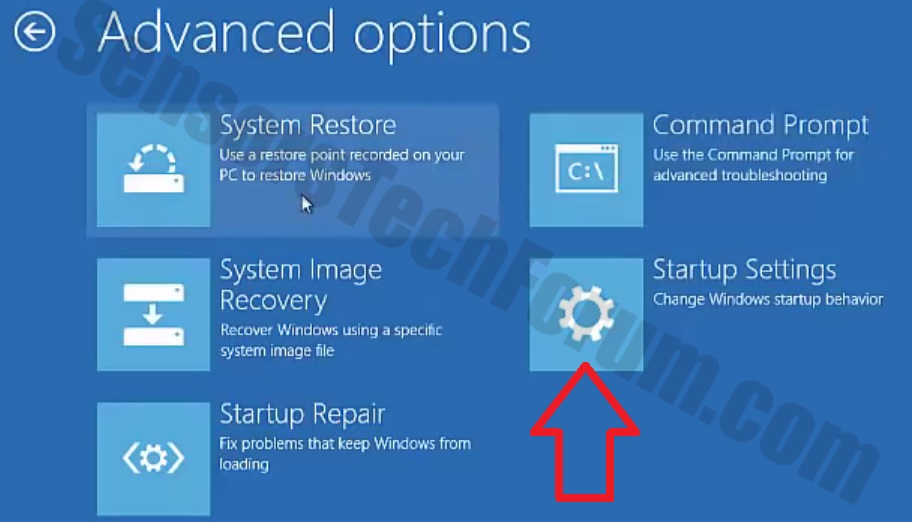
Trin 6: Klik på Genstart.

Trin 7: En menu vises ved genstart. Du bør vælge Fejlsikret tilstand ved at trykke på dens tilsvarende nummer og maskinen genstarter.
2. Fjern Skadelig software med SpyHunter Anti-Malware værktøj
2. Fjern Skadelig software med SpyHunter Anti-Malware værktøj
 1. Installer SpyHunter at scanne efter og fjerne skadelig software.
1. Installer SpyHunter at scanne efter og fjerne skadelig software. 2. Scan med SpyHunter at opdage og fjerne skadelig software.
2. Scan med SpyHunter at opdage og fjerne skadelig software.
Trin 1:Klik på “Hent” knappen for at gå videre til SpyHunter download side.

Det anbefales stærkt at køre en scanning, før du køber den fulde version af softwaren for at sikre, at den nuværende version af malware kan påvises ved SpyHunter.
Trin 2: Guide dig selv ved download vejledningen for hver browser.
Trin 3: Når du har installeret SpyHunter, vente på, at automatisk opdatere.
Trin 1: Efter opdateringen er færdig, klik på 'Scan computer nu’ knap.
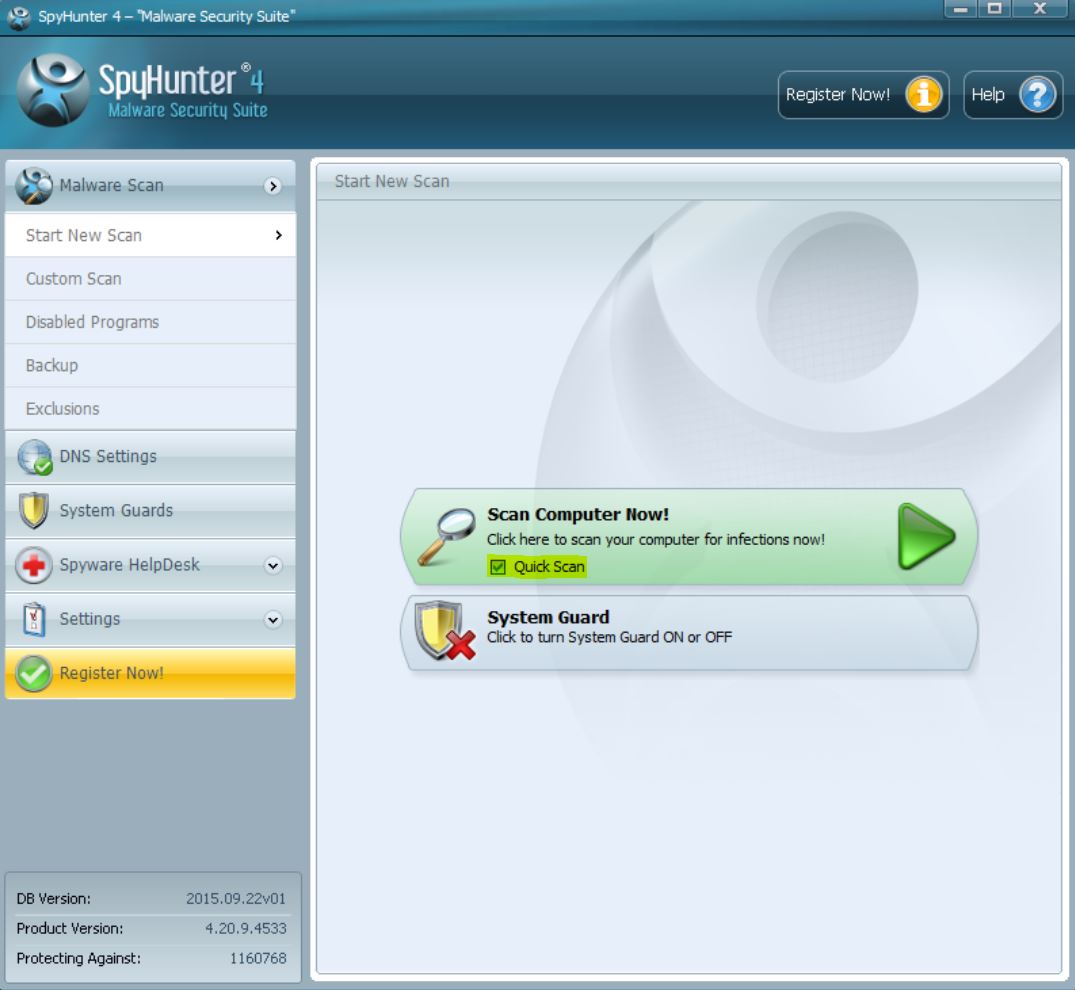
Trin 2: Efter SpyHunter har færdig med at scanne din pc for enhver skadelig software filer, klik på 'Fix Trusler’ for at fjerne dem automatisk og permanent.
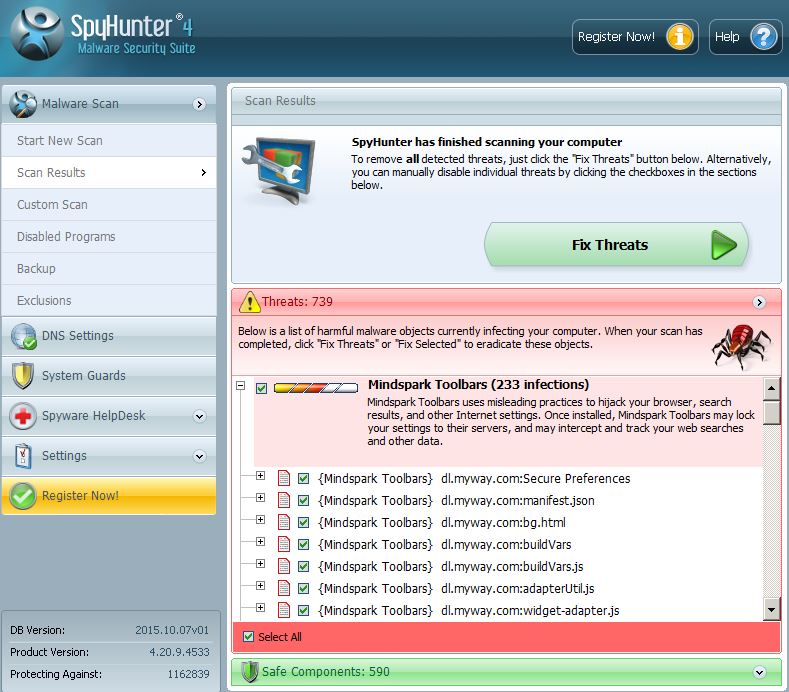
Trin 3: Når indtrængen på din pc er blevet fjernet, Det anbefales stærkt at genstarte den.
3. Sikkerhedskopiere dine data for at sikre den mod infektioner og kryptering af skadelig software i fremtiden
3. Sikkerhedskopiere dine data for at sikre den mod angreb i fremtiden
Sikkerhed ingeniører anbefaler, at du sikkerhedskopiere dine filer med det samme, helst på en ekstern hukommelse luftfartsselskab for at være i stand til at gendanne dem. For at beskytte dig selv fra Farlig Software (For Windows-brugere) Følg disse enkle trin:
 1. For Windows 7 og tidligere
1. For Windows 7 og tidligere 1. For Windows 8, 8.1 og 10
1. For Windows 8, 8.1 og 10 1. Aktivering af Windows Defense Feature (Tidligere versioner)
1. Aktivering af Windows Defense Feature (Tidligere versioner)
1-Tryk
Windows-knap + R
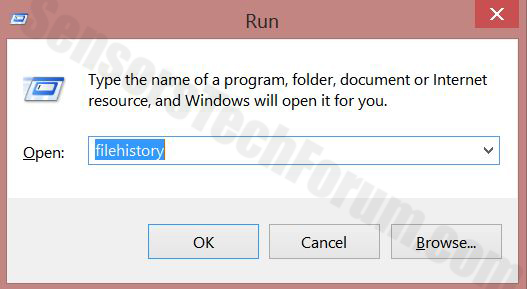
2-I det vindue typen
'Filehistory' og tryk på
Indtast
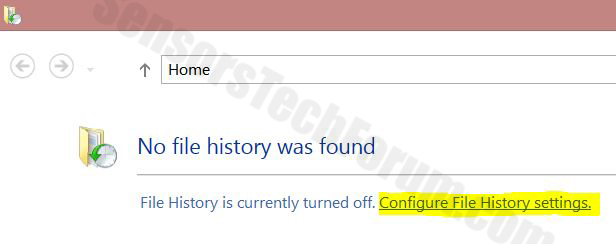
3-En File History vindue vises. Klik på
'Konfigurer fil historik indstillinger'
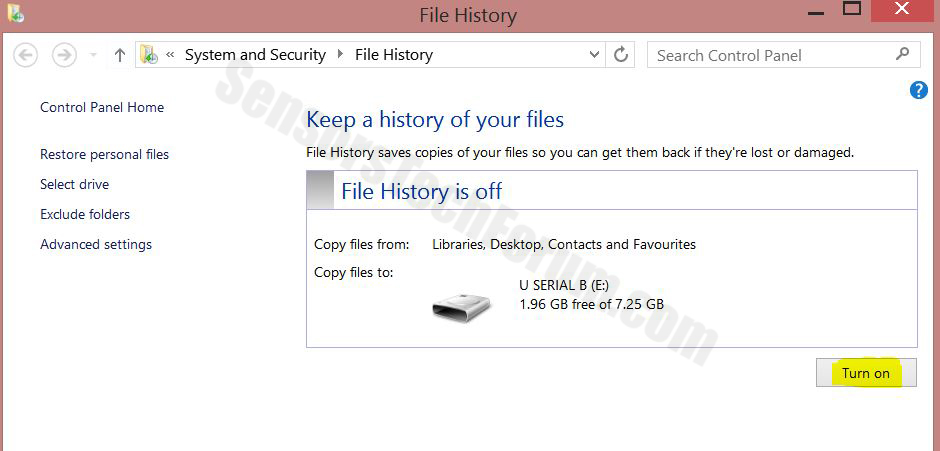
4-Konfigurationsmenuen for File History vises. Klik på 'Turn On'. Efter dens på, klik på Vælg drev for at vælge backup-drev. Det anbefales at vælge en ekstern harddisk, SSD eller en USB-nøgle, hvis hukommelseskapacitet er svarer til størrelsen på de filer, du ønsker at tage backup.
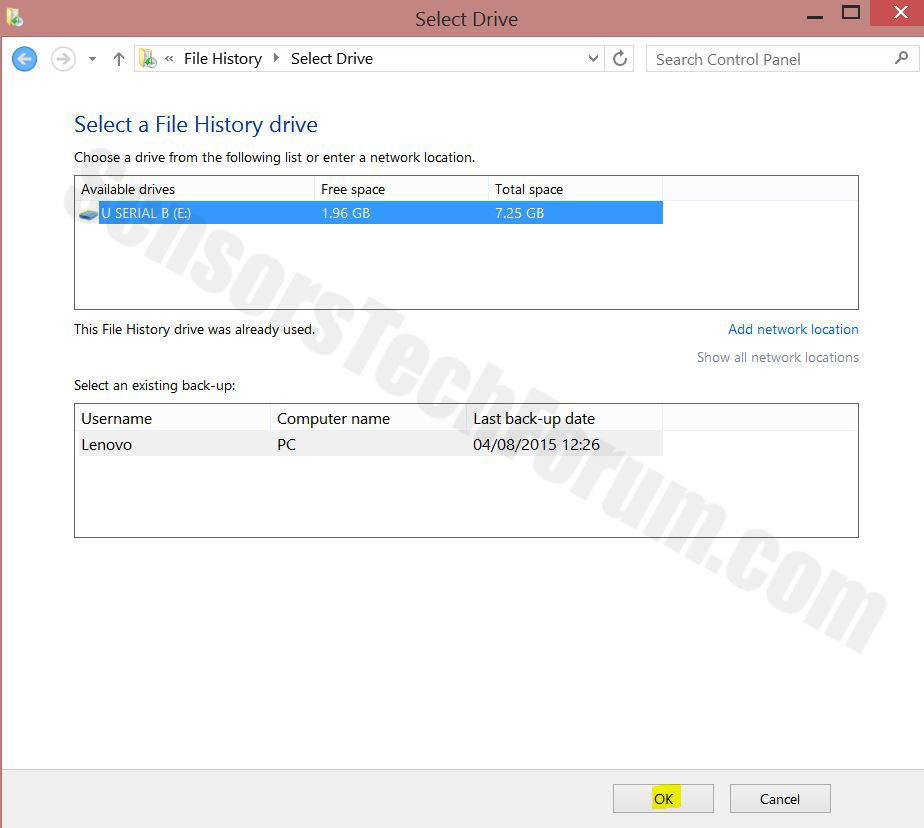
5-Vælg det drev og klik på "OK" for at oprette fil backup og beskytte dig mod
Farlig Software.
Ventsislav er cybersikkerhedsekspert hos SensorsTechForum siden 2015. Han har forsket, tildækning, hjælpe ofre med de nyeste malware-infektioner plus test og gennemgang af software og den nyeste teknologiudvikling. Have uddannet Marketing samt, Ventsislav har også lidenskab for at lære nye skift og innovationer inden for cybersikkerhed, der bliver spiludskiftere. Efter at have studeret Management Chain Management, Netværksadministration og computeradministration af systemapplikationer, han fandt sit rigtige kald inden for cybersecurity-branchen og er en stærk troende på uddannelse af enhver bruger til online sikkerhed og sikkerhed.
Flere indlæg - Websted
Følg mig:

Hent (MAC)
Værktøj til fjernelse af malware
Få en gratis scanner for at se, om din MAC er inficeret.
Brug SpyHunter til at fjerne malware på mindre end 15 minutter.
Nyd en gratis 7-dages prøveperiode med dit kreditkort. Annuller mindst to dage før prøveperioden slutter for at undgå gebyrer. Abonnementsgebyrer varierer efter region og fornys automatisk, medmindre du annullerer i tide. You'll receive a reminder before your next billing, and there's a 30-day money-back guarantee. Læs de fulde vilkår og opdag den gratis fjernelsestjeneste. Read more...
Hent
Værktøj til fjernelse af malware
Få en gratis scanner for at se, om din pc er inficeret.
SpyHunter 5 gratis fjernelse giver dig mulighed, underlagt en 48-timers ventetid, en afhjælpning og fjernelse for fundne resultater. Læs EULA og Fortrolighedspolitik







 1. For Windows 7, XP og Vista.
1. For Windows 7, XP og Vista. 2. For Windows 8, 8.1 og 10.
2. For Windows 8, 8.1 og 10.







 1. Installer SpyHunter at scanne efter og fjerne skadelig software.
1. Installer SpyHunter at scanne efter og fjerne skadelig software.








send mig dit værste malware og jeg er ligeglad med det, hvis jeg ikke har nogen antiviruses program installeret jeg spurgte dig Hvorfor? Ja du har ret, jeg er en Ubuntu bruger …fra, fra, jii!