Persoonlijke veiligheid begint meestal met het apparaat. Hoe meer onveilige apparaten zijn die er zijn, des te beter is het mechanisme achter datalekken en malware-infecties. Dus, als je wilt veilig en gezond te zijn, te beginnen met het apparaat.
Apparaatbeveiliging en besturingssystemen
Het besturingssysteem van Microsoft heeft een behoorlijk aandeel van de gebruikersmarkt. Misschien is dat een van de redenen van Windows in de weg van cyberaanvallen die vaak. Of misschien de intensiteit van de succesvolle aanvallen op Windows is te wijten aan een verouderde versie van het OS?
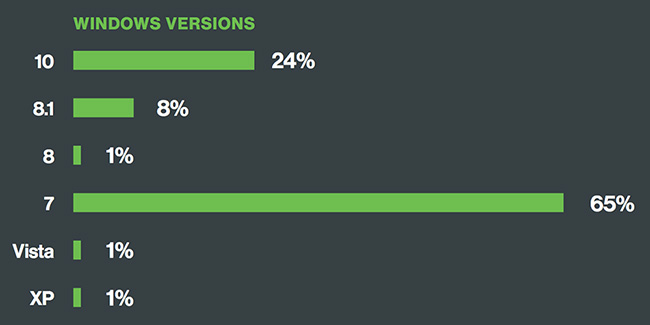
Om deze en andere vragen te beantwoorden of alleen omwille van de analyse, Duo Beveiliging onderzocht meer dan twee miljoen apparaten, meer dan de helft van die werden uitgevoerd op een versie van Windows.
Onderzoekers ontdekten dat 65 procent van de Windows-apparaten werden uitgevoerd op Windows 7, dat gevoelig is voor meer dan 600 beveiligingsproblemen.
Dit is niet het ergste. Tienduizenden machines zijn nog steeds Windows XP. Windows XP werd uitgebracht in 2001. Dit feit alleen al betekent dat meerdere aanval scenario's letterlijk door honderden kwetsbaarheden ter beschikking gesteld. Veel van deze tekortkomingen van cruciaal karakter.
Er zijn vele redenen waarom een bedrijf een oudere OS zou verkiezen boven een onlangs vrijgegeven één
De meest voor de hand liggende reden is de kosten en de tijd die nodig is om elke computer en software bij te werken in een organisatie. In sommige gevallen, de software van het bedrijf wordt uitgevoerd mogelijk niet overeen met latere besturingssystemen en omgevingen, als toegelicht door Ajay Arora, CEO van Vera.
De deskundige is ook van mening dat als bedrijven blijven Windows kiezen 7 meer dan latere Windows-versies, ze nodig hebben om beveiligingssoftware die de ontbrekende functies, zoals standaard disk encryptie dekt overwegen. "Het komt neer op, de besteding van het geld aan de onderliggende probleem van het gebruik van een besturingssysteem met een zwakkere beveiliging aan te pakken, het uitgeven van geld aan de besturingssystemen werken, of de besteding van het geld om het ding die u probeert te beschermen in de eerste plaats veilig te stellen; de gegevens zelf,”Arora zegt.
Het grootste probleem echter is de doorlopende verspreiding van nieuwe kwetsbaarheden. Onlangs, Google's Threat Analysis Group bekendgemaakt een set van zero-day fouten in Adobe Flash en Microsoft Windows-kernel. Deze set van gebreken is al in het wild misbruik tegen de Chrome-browser.
Adobe waren in staat om snel te werken Flash tegen de CVE-2016-7855
Helaas, de Windows-kernel bug is nog steeds ongepatchte. In een post van 31 oktober, Neel Mehta en Billy Leonard uit het Threat Analysis Group zeggen dat:
Na 7 dagen, per onze gepubliceerde beleid voor het actief uitgebuit kritieke kwetsbaarheden, we zijn vandaag de dag zij het bestaan van een resterende kritieke kwetsbaarheid in Windows waarvoor geen adviserende of fix nog is vrijgegeven. Deze kwetsbaarheid is bijzonder ernstig, omdat we weten dat het actief wordt uitgebuit.
De Windows-kwetsbaarheid is een lokale escalatie van bevoegdheden in de Windows-kernel die kan worden gebruikt als een beveiligingssandbox escape. Het kan worden geactiveerd via de win32k.sys system call NtSetWindowLongPtr() voor de index GWLP_ID op een venster handgreep met GWL_STYLE ingesteld op WS_CHILD. De sandbox van Chrome blokken win32k.sys systeem belt met behulp van de Win32 lockdown mitigatie op Windows 10, die misbruik van dit zandbak ontsnapping kwetsbaarheid voorkomt.
Wat zijn enkele goede beveiligingstips?
Duo security onderzoekers adviseren de volgende, en wij zijn het eens:
- Gebruik moderne browser platforms die veiliger zijn of ga voor browsers die vaker en automatisch worden bijgewerkt;
- Onderschat nooit de kracht van beveiligingsupdates en hulpdiensten flarden;
- Overweeg het gebruik van het apparaat versleuteling, wachtwoorden en vingerafdruk ID;
- Overweeg het gebruik van een twee-factor authenticatie oplossing voor systemen en gegevens te beschermen;
- Schakel Java en te voorkomen dat Flash automatisch worden uitgevoerd op de corporate apparaten;
- Deze praktijk moet gaan voor het bezit van gebruikers apparaten via toegang tot het beleid en de controles eindpunt.