Cosa è UC Browser? È UC Browser legittimo o una truffa? È UC Browser un adware? Come rimuovere UC Browser PUP dal vostro PC o Mac?
Il PUP Browser UC è una versione del malware di un browser web legittimo e ben noti. E 'costituito da più gruppi di hacker e distribuito su Internet in campagne di distribuzione su larga scala. Questi campioni possono portare a diversi tipi di azioni dannose, compresa la consegna di altre minacce. Anche se il vero UC Browser è installato su un dato sistema si consiglia agli utenti di controllare se non è un malware o un PUP.

Sommario minaccia
| Nome | UC Browser |
| Tipo | Adware, PUP |
| breve descrizione | Si pone come un browser web legittimo e utile. |
| Sintomi | Le vittime possono notare i problemi di prestazioni e possono infettarsi con altri malware. |
| Metodo di distribuzione | Principalmente attraverso siti di download e reti di file sharing. |
| Detection Tool |
Verifica se il tuo sistema è stato interessato da malware
Scarica
Strumento di rimozione malware
|
Esperienza utente | Iscriviti alla nostra Forum per discutere UC Browser. |

PUP Browser UC - Come ho ricevuto E '?
Il UC Browser è un browser web popolare dei quali sono stati fatti molti derivati PUP. Loro sono copie infettate dal virus del software che sono ampiamente distribuite in posa come il programma reale e sicura. Questa è una minaccia molto popolare in quanto vi sono diversi fatti per molti sistemi operativi.
Le infezioni possono essere effettuate utilizzando una varietà di metodi, a causa del fatto che si tratta di uno dei browser più popolari tra le giovani generazioni. Questo ha provocato un aumento delle varianti PUP. Un metodo comune è il coordinamento di campagne di email di phishing che vengono inviati alle vittime. Varie tattiche di ingegneria sociale sono utilizzati al fine di convincerli a installare il PUP Browser UC - un'esperienza di navigazione web ottimizzato, miglioramenti rispetto alle versioni precedenti e ecc.
L'altro metodo popolare è quello di creare siti truffa Internet che mirano ad imitare noto portali di download, motori di ricerca e pagine di destinazione. Essi sono ospitati su simili pagine web dal suono a località famose e possono essere firmati con certificati di sicurezza.
L'installazione del browser può essere innescato da interazioni con i vari vettori payload di cui ci sono due tipi principali - documenti modificati che includono le macro malevoli (di tutti i tipi: documenti di testo, fogli di calcolo, presentazioni e database) e installazione di applicazioni.
L'infezione Browser PUP UC può essere attivato anche tramite l'installazione e l'uso di browser hijacker quali sono i plugin pericolose effettuati per la maggior parte dei browser più diffusi. Essi sono ampiamente utilizzati per reindirizzare gli utenti a una pagina di hacker controllato (di solito un sito di download di atterraggio) o per fornire direttamente il PUP Browser UC ai computer delle vittime. Uno dei luoghi più popolari in cui tali dirottatori si possono trovare sono i plug-in associato repository dove vengono pubblicati con commenti falsi e le credenziali per sviluppatori.

UC Browser PUP - che cosa fa?
il maligno UC Browser versioni PUP possono causare una serie di azioni pericolose sui dispositivi interessati. In molti casi gli utenti non saranno in grado di distinguere tra il legittimo e di un falso e dannoso PUP. In questo caso ci può essere più di un collettivo di hacker invio del UC Browser PUP alle loro vittime designate. Ciò significa che diverse campagne possono essere mescolati e diverse infezioni differenti possono fornire diversi modelli di comportamento.
Tali campioni possono lanciare una sequenza di azioni pericolose che sono governati dagli hacker. Tali infezioni solito iniziano con un i dati di raccolta componente che può essere utilizzato per raccogliere informazioni sugli utenti vittima esponendo così la loro identità. Può anche essere utilizzato per generare un ID univoco infezione che possono differenziare ogni host.
Il UC Browser è stato recentemente trovato per includere un bug nella sua versione stabile, che consente agli hacker di computer per fornire il malware. Questo si trova all'interno del rilascio di Android che mostra che la società dietro di esso ha anche violato le regole del Google Play Store che vieta tale software da caricare nel repository ufficiale. Dato questo storia delle violazioni si raccomanda che gli utenti di tutto UC Browser versioni verificare se sono in esecuzione la versione più recente. E 'allarmante che ciò è dovuto a un difetto di progettazione che può aprire la strada ad altri exploit nelle versioni future che possono ancora rimanere da scoprire.
Molti PUP simili possono utilizzare le informazioni acquisite al fine di by-pass delle applicazioni e dei servizi di sicurezza esistenti che di solito si rivolge programmi anti-virus, firewall, virtual host di macchine e ambienti sandbox.
Quando questi componenti hanno terminato l'esecuzione varie altre azioni pericolose possono avvenire:
- Windows modifica del Registro di sistema - Il motore associato può portare a più modifiche nel registro di Windows. Possono creare stringhe per il PUP stesso e modificare le voci esistenti e cancellarli. Questo porta a problemi gravi di prestazioni, errori imprevisti e perdita di dati.
- infezioni persistenti - Il UC Browser PUP possono essere programmati per modificare importanti file di configurazione che possono bloccare la possibilità agli utenti di menu di avvio di recupero di accesso. Un'ulteriore conseguenza è che questo renderà più manuale guide rimozione inutile.
- rimozione dei dati - Il motore può individuare e rimuovere i dati sensibili, che rende il recupero molto più difficile: backup, ombra copie di volume e punti di ripristino.
- UC Browser Adware Component – UC Browser può aggiungere un componente adware che può caricare un sacco di pop-up e raccogliere dati sui suoi utenti.
- Minacce aggiuntive Deliver - Le versioni pericolose del UC Browser può essere programmato per fornire altre minacce, quelli popolari includono Trojan e minatori criptovaluta.
Come UC Browser campioni PUP sono realizzati da diversi collettivi degli hacker di tutto il mondo le varianti saranno solo continuazione della produzione. Inoltre, il UC Browser Adware possono essere aggiunti. Ogni singolo campioni acquisiti possono avere un modello di comportamento diverso che rende questo prole estremamente pericoloso. Non appena è stata posta su un determinato computer si consiglia una soluzione di qualità anti-spyware è utilizzato al fine di assicurare che non è una release dannoso.

Rimuovere UC Browser PUP
Al fine di eliminare completamente UC Browser dal sistema del computer, si consiglia di seguire le istruzioni di rimozione sotto questo articolo. Se le prime due fasi di rimozione manuale non sembrano al lavoro e si vede ancora UC Browser o programmi, ad essa collegate, suggeriamo che la maggior parte esperti di sicurezza consigliano - per scaricare ed eseguire una scansione del vostro comptuer con un programma anti-malware affidabile. Scaricando questo software non solo di risparmiare tempo, ma sarà rimuovere tutti UC Browser file e programmi ad esso correlati e proteggerà il vostro computer da tali applicazioni intrusive e malware in futuro.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Interrompi i popup push
Come rimuovere UC Browser da Windows.
Passo 1: Scansione per UC Browser con SpyHunter Anti-Malware Strumento



Passo 2: Avvia il PC in modalità provvisoria





Passo 3: Disinstallare UC Browser e relativo software da Windows
Passaggi di disinstallazione per Windows 11
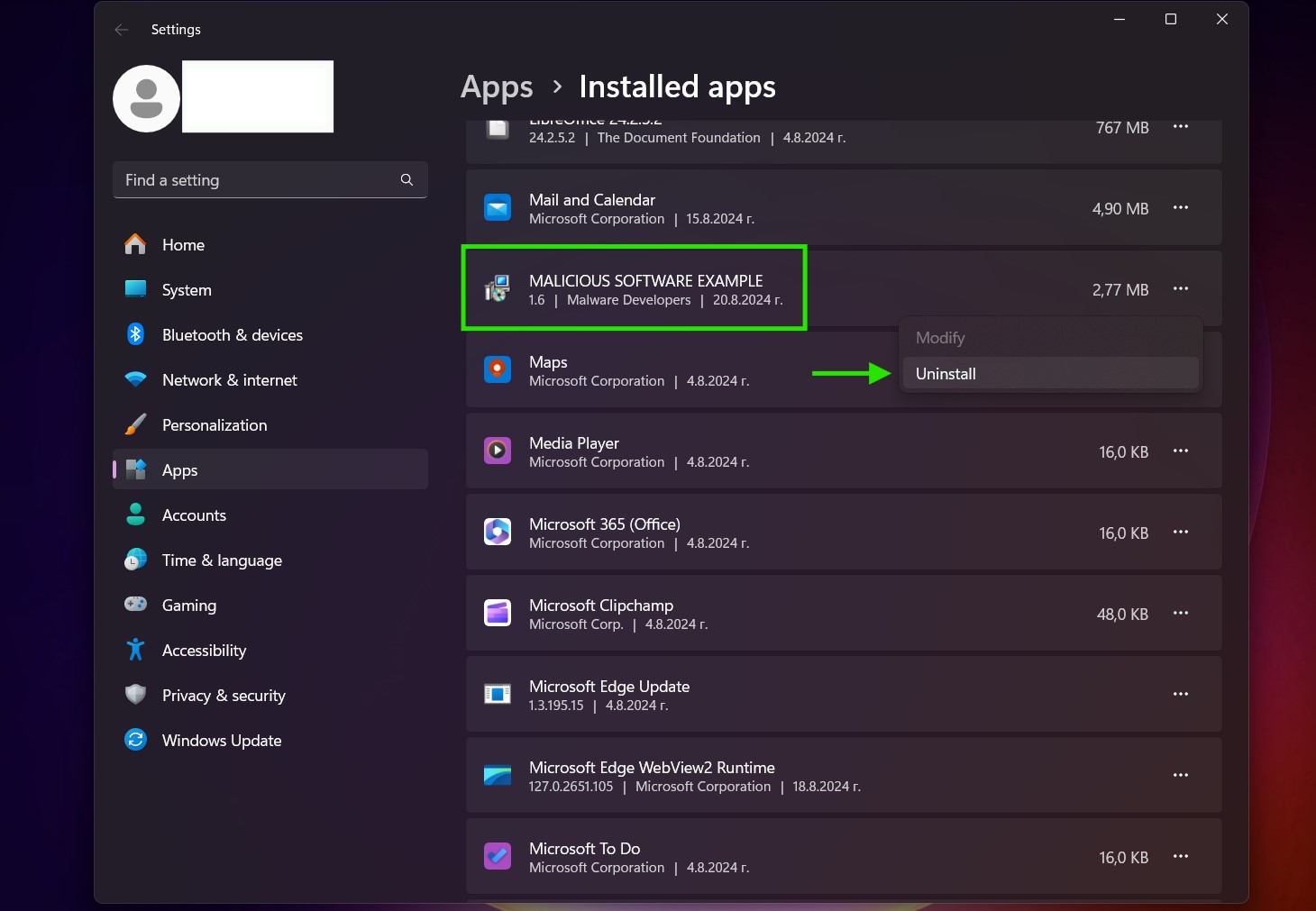
Passaggi di disinstallazione per Windows 10 e versioni precedenti
Ecco un metodo in pochi semplici passi che dovrebbero essere in grado di disinstallare maggior parte dei programmi. Non importa se si utilizza Windows 10, 8, 7, Vista o XP, quei passi otterrà il lavoro fatto. Trascinando il programma o la relativa cartella nel cestino può essere un molto cattiva decisione. Se lo fai, frammenti di programma vengono lasciati, e che possono portare al lavoro instabile del PC, errori con le associazioni di tipo file e altre attività spiacevoli. Il modo corretto per ottenere un programma dal computer è di disinstallarlo. Per fare questo:


 Seguire le istruzioni di cui sopra e vi disinstallare correttamente maggior parte dei programmi.
Seguire le istruzioni di cui sopra e vi disinstallare correttamente maggior parte dei programmi.
Passo 4: Pulisci tutti i registri, Created by UC Browser on Your PC.
I registri di solito mirati di macchine Windows sono i seguenti:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
È possibile accedere aprendo l'editor del registro di Windows e l'eliminazione di tutti i valori, creato da UC Browser lì. Questo può accadere seguendo la procedura sotto:


 Mancia: Per trovare un valore virus creato, è possibile fare clic destro su di esso e fare clic su "Modificare" per vedere quale file è impostato per funzionare. Se questa è la posizione file del virus, rimuovere il valore.
Mancia: Per trovare un valore virus creato, è possibile fare clic destro su di esso e fare clic su "Modificare" per vedere quale file è impostato per funzionare. Se questa è la posizione file del virus, rimuovere il valore.
Guida alla rimozione dei video per UC Browser (Windows).
Sbarazzati di UC Browser da Mac OS X.
Passo 1: Disinstalla UC Browser e rimuovi file e oggetti correlati
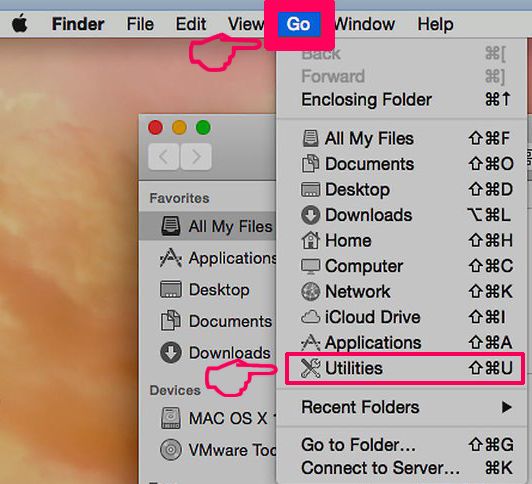
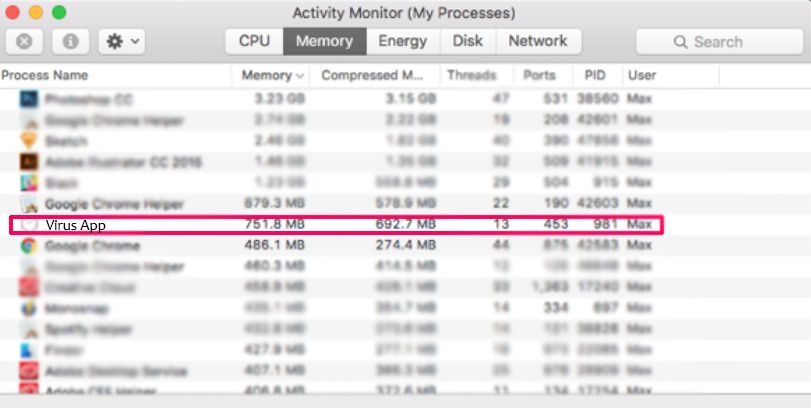
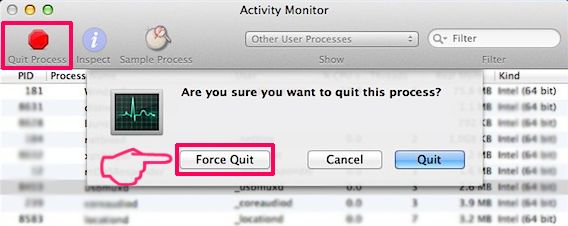
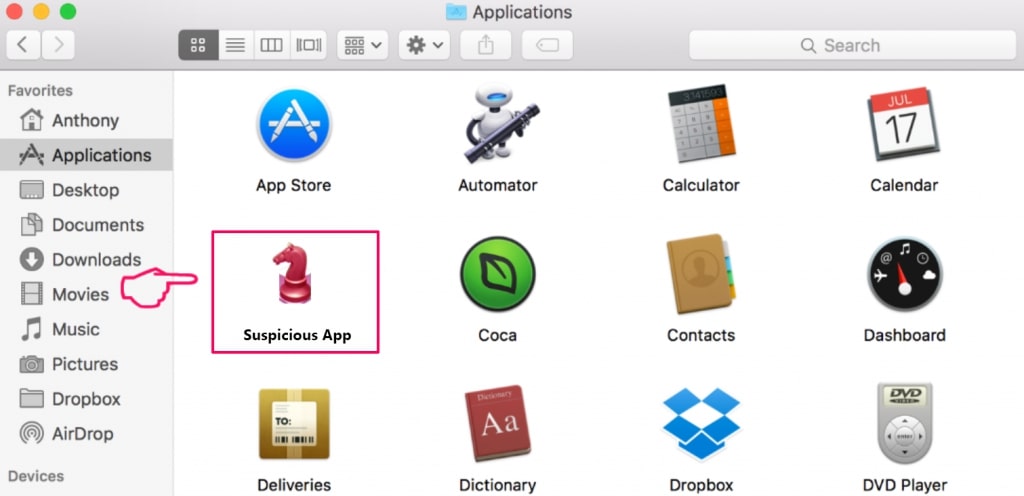
Il Mac ti mostrerà un elenco di elementi che si avvia automaticamente quando si accede. Cercare eventuali applicazioni sospette identici o simili a UC Browser. Controllare l'applicazione che si desidera interrompere l'esecuzione automatica e quindi selezionare sul Meno ("-") icona per nasconderlo.
- Vai a mirino.
- Nella barra di ricerca digitare il nome della app che si desidera rimuovere.
- Al di sopra della barra di ricerca cambiare i due menu a tendina per "File di sistema" e "Sono inclusi" in modo che è possibile vedere tutti i file associati con l'applicazione che si desidera rimuovere. Tenete a mente che alcuni dei file non possono essere correlati al app in modo da essere molto attenti che i file si elimina.
- Se tutti i file sono correlati, tenere il ⌘ + A per selezionare loro e poi li di auto "Trash".
Nel caso in cui non è possibile rimuovere UC Browser via Passo 1 sopra:
Nel caso in cui non è possibile trovare i file dei virus e gli oggetti nelle applicazioni o altri luoghi che abbiamo sopra riportati, si può cercare manualmente per loro nelle Biblioteche del Mac. Ma prima di fare questo, si prega di leggere il disclaimer qui sotto:
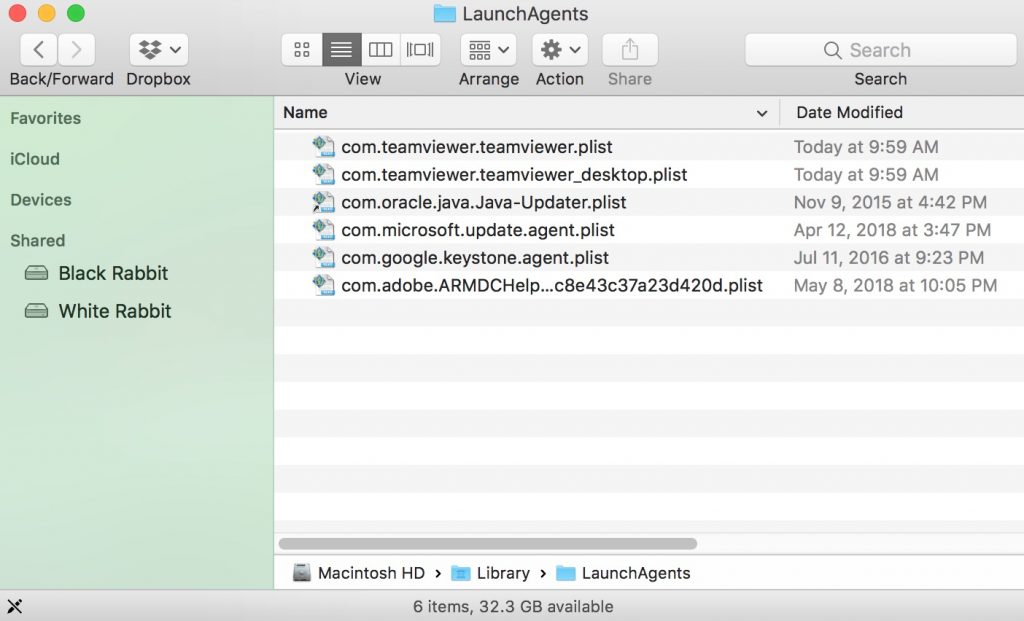
Puoi ripetere la stessa procedura con il seguente altro Biblioteca directory:
→ ~ / Library / LaunchAgents
/Library / LaunchDaemons
Mancia: ~ è lì apposta, perché porta a più LaunchAgents.
Passo 2: Cerca e rimuovi i file del browser UC dal tuo Mac
Quando si trovano ad affrontare problemi sul vostro Mac come un risultato di script indesiderati e programmi come UC Browser, il modo consigliato di eliminare la minaccia è quello di utilizzare un programma anti-malware. SpyHunter per Mac offre funzionalità di sicurezza avanzate insieme ad altri moduli che miglioreranno la sicurezza del tuo Mac e la proteggeranno in futuro.
Guida alla rimozione dei video per UC Browser (Mac)
Rimuovere UC Browser da Google Chrome.
Passo 1: Avvia Google Chrome e apri il menu a discesa
Passo 2: Spostare il cursore sopra "Strumenti" e poi dal menu esteso scegliere "Estensioni"
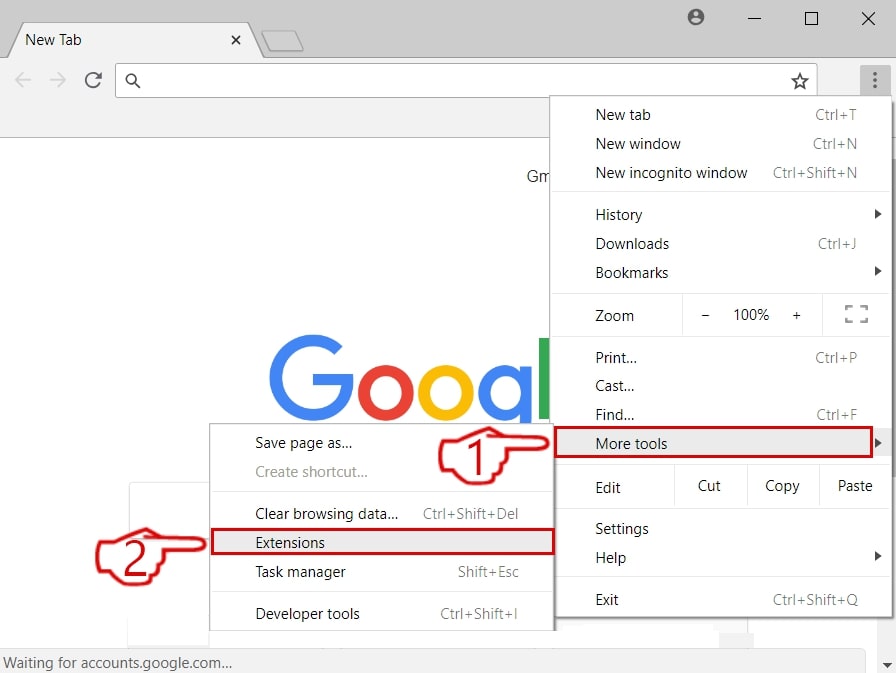
Passo 3: Dal aperto "Estensioni" menu di individuare l'estensione indesiderata e fare clic sul suo "Rimuovere" pulsante.
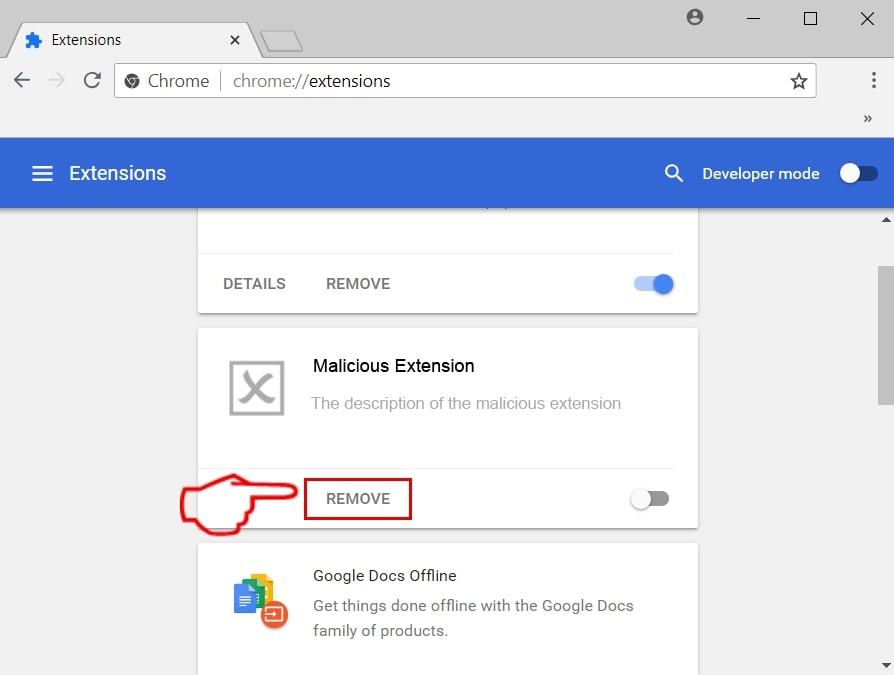
Passo 4: Dopo l'estensione viene rimossa, riavviare Google Chrome chiudendo dal rosso "X" pulsante in alto a destra e iniziare di nuovo.
Cancella UC Browser da Mozilla Firefox.
Passo 1: Avviare Mozilla Firefox. Aprire la finestra del menu:
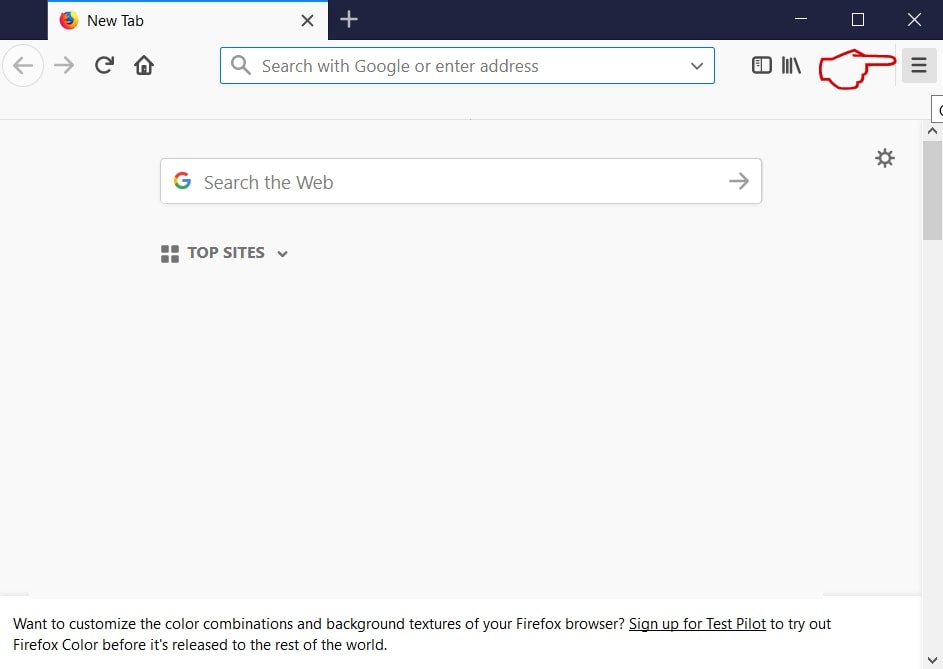
Passo 2: Selezionare il "Componenti aggiuntivi" icona dal menu.
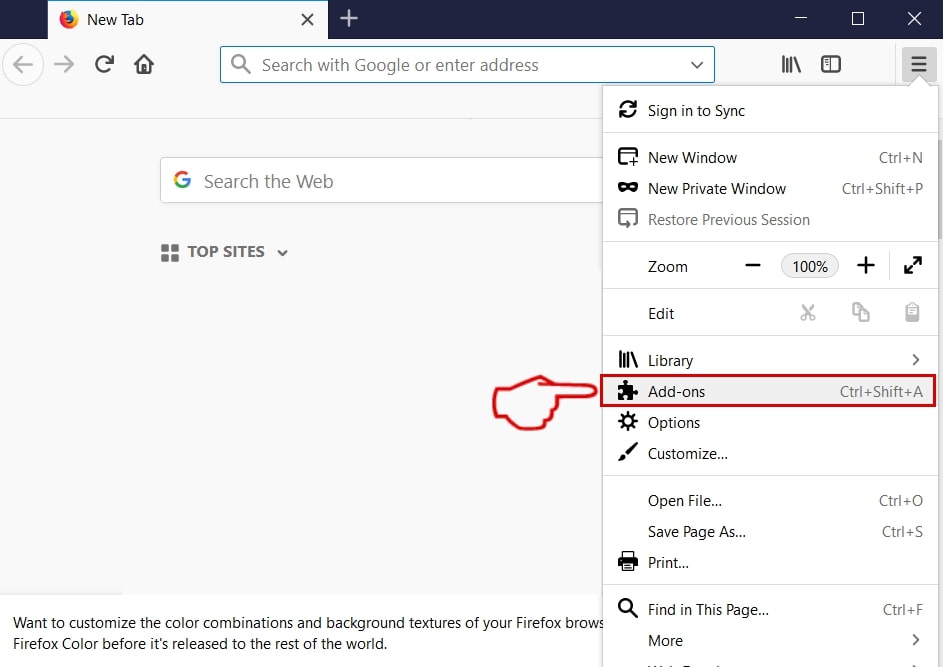
Passo 3: Selezionare l'estensione indesiderata e fare clic su "Rimuovere"

Passo 4: Dopo l'estensione viene rimossa, riavviare Mozilla Firefox chiudendo dal rosso "X" pulsante in alto a destra e iniziare di nuovo.
Disinstalla UC Browser da Microsoft Edge.
Passo 1: Avviare il browser Edge.
Passo 2: Apri il menu a tendina facendo clic sull'icona nell'angolo in alto a destra.
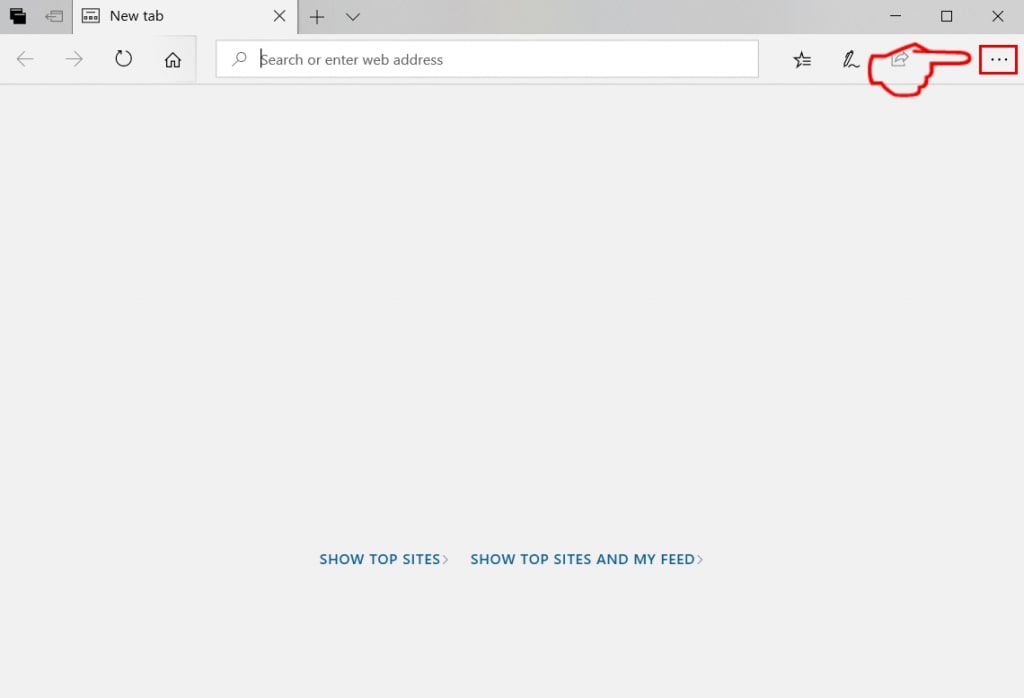
Passo 3: Dal menu a discesa selezionare "Estensioni".
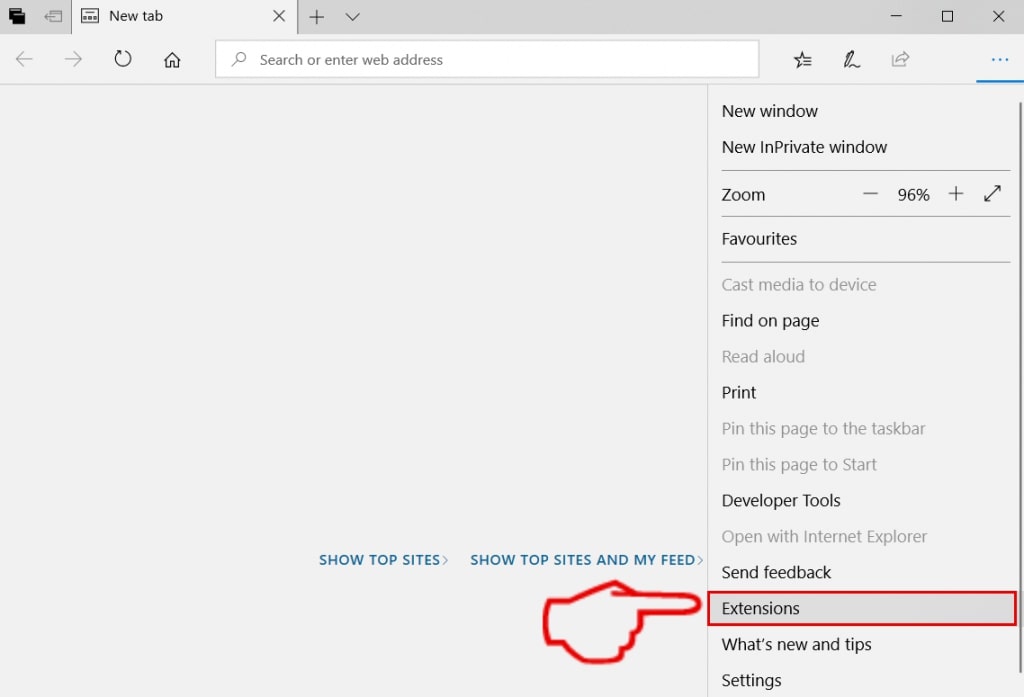
Passo 4: Scegli l'estensione dannosa sospetta che desideri rimuovere, quindi fai clic sull'icona a forma di ingranaggio.
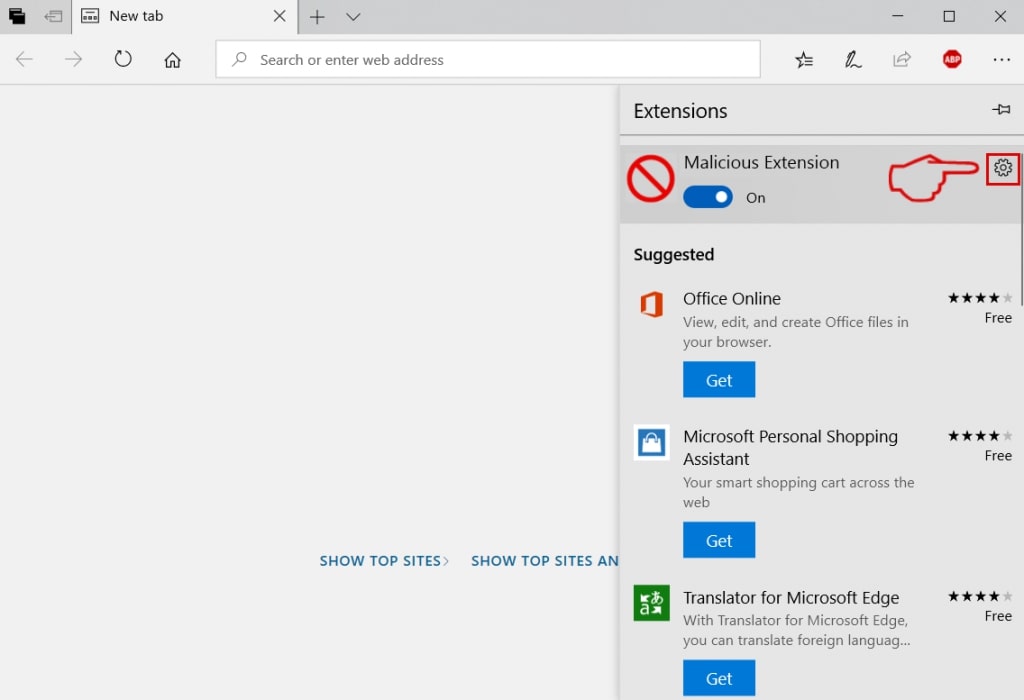
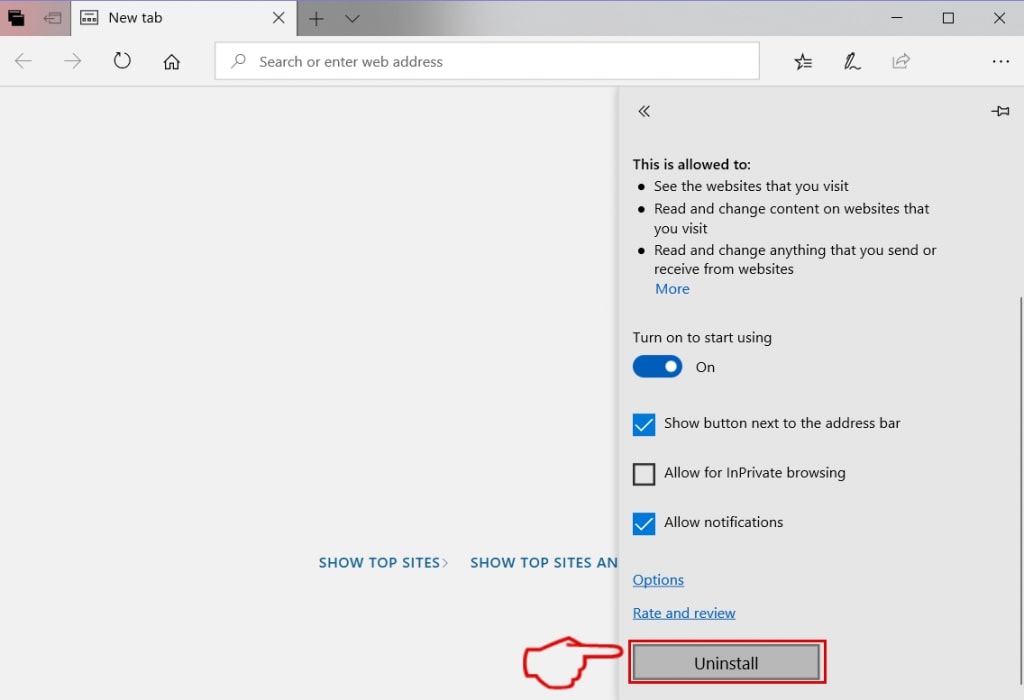
Passo 5: Rimuovere l'estensione dannosa scorrendo verso il basso e quindi facendo clic su Disinstalla.
Rimuovi UC Browser da Safari
Passo 1: Avvia l'app Safari.
Passo 2: Dopo avere posizionato il cursore del mouse nella parte superiore dello schermo, fai clic sul testo di Safari per aprire il suo menu a discesa.
Passo 3: Dal menu, clicca su "Preferenze".
Passo 4: Dopo di che, seleziona la scheda "Estensioni".
Passo 5: Fare clic una volta sulla estensione che si desidera rimuovere.
Passo 6: Fare clic su "Disinstalla".
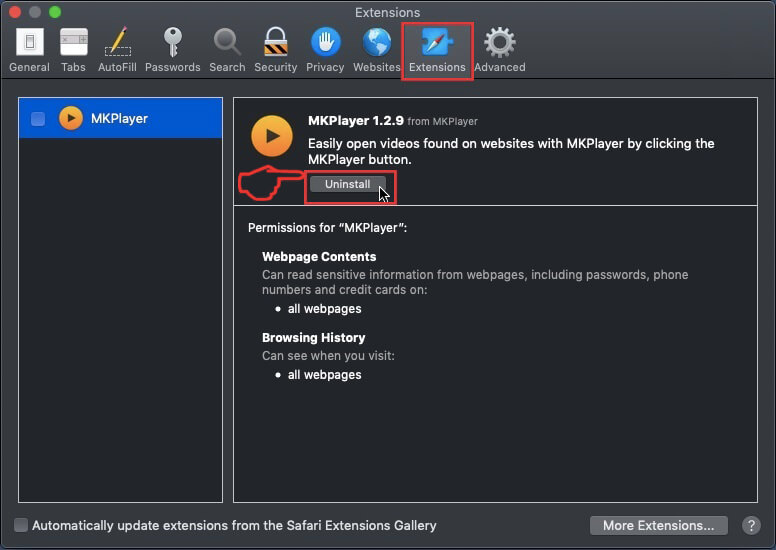
Una finestra pop-up che chiede conferma per disinstallare l'estensione. Selezionare 'Uninstall' di nuovo, e il browser UC sarà rimosso.
Elimina UC Browser da Internet Explorer.
Passo 1: Avviare Internet Explorer.
Passo 2: Fare clic sull'icona a forma di ingranaggio denominata "Strumenti" per aprire il menu a discesa e selezionare "Gestisci componenti aggiuntivi"
Passo 3: Nella finestra "Gestisci componenti aggiuntivi".
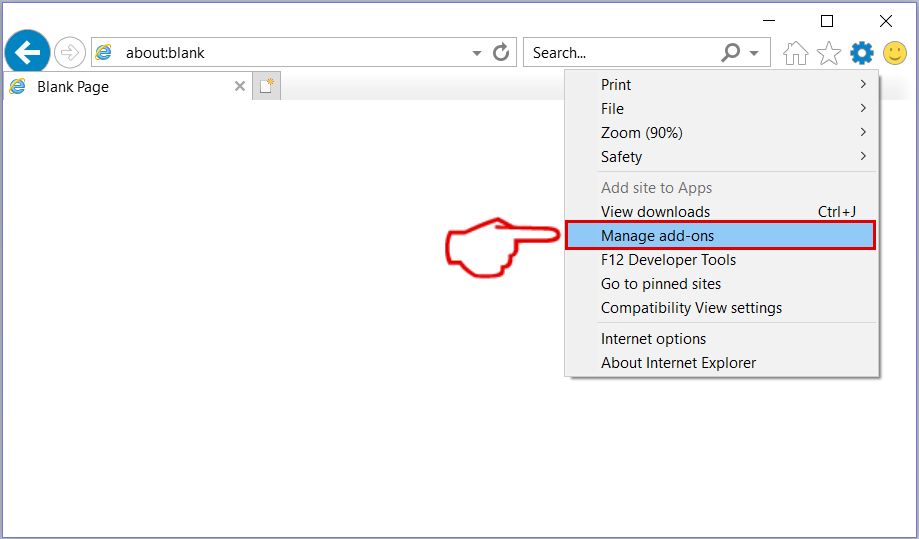
Passo 4: Seleziona l'estensione che desideri rimuovere, quindi fai clic su "Disabilita". Una finestra pop-up apparirà per informarvi che si sta per disattivare l'estensione selezionata, e alcuni altri componenti aggiuntivi potrebbero essere disattivate pure. Lasciare tutte le caselle selezionate, e fai clic su "Disabilita".
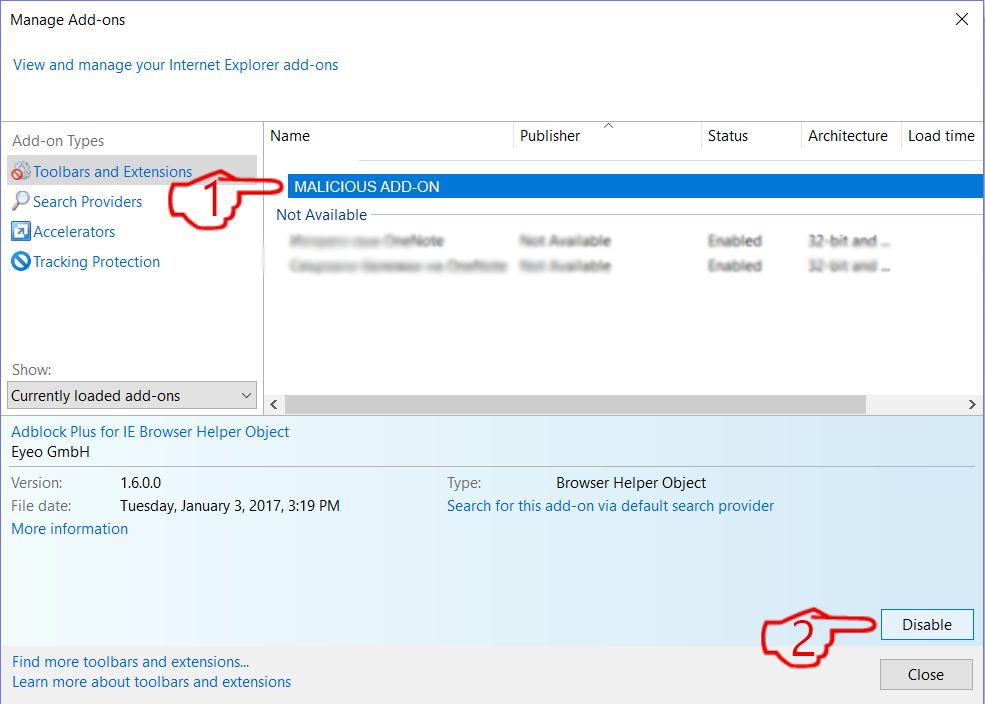
Passo 5: Dopo l'estensione indesiderato è stato rimosso, riavvia Internet Explorer chiudendolo dal pulsante rosso "X" situato nell'angolo in alto a destra e riavvialo.
Rimuovi le notifiche push dai tuoi browser
Disattiva le notifiche push da Google Chrome
Per disabilitare eventuali notifiche push dal browser Google Chrome, si prega di seguire i passi di seguito:
Passo 1: Vai a Impostazioni in Chrome.
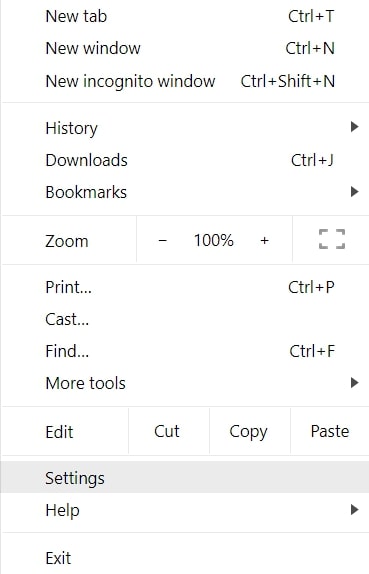
Passo 2: In Impostazioni, selezionare “Impostazioni avanzate":
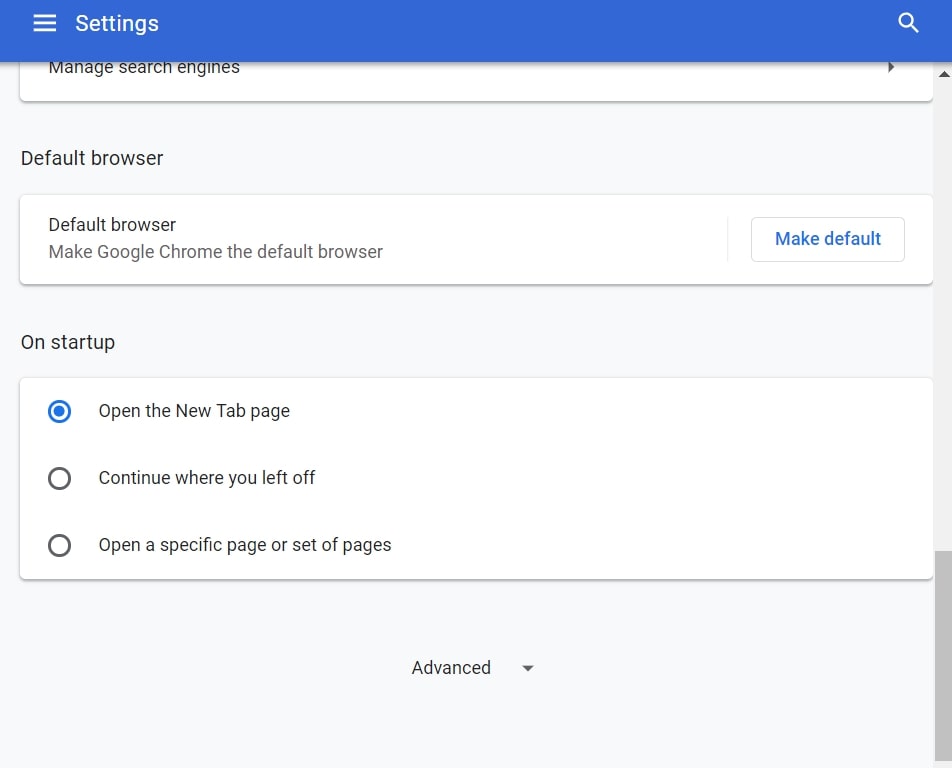
Passo 3: Fare clic su "Le impostazioni del contenuto":
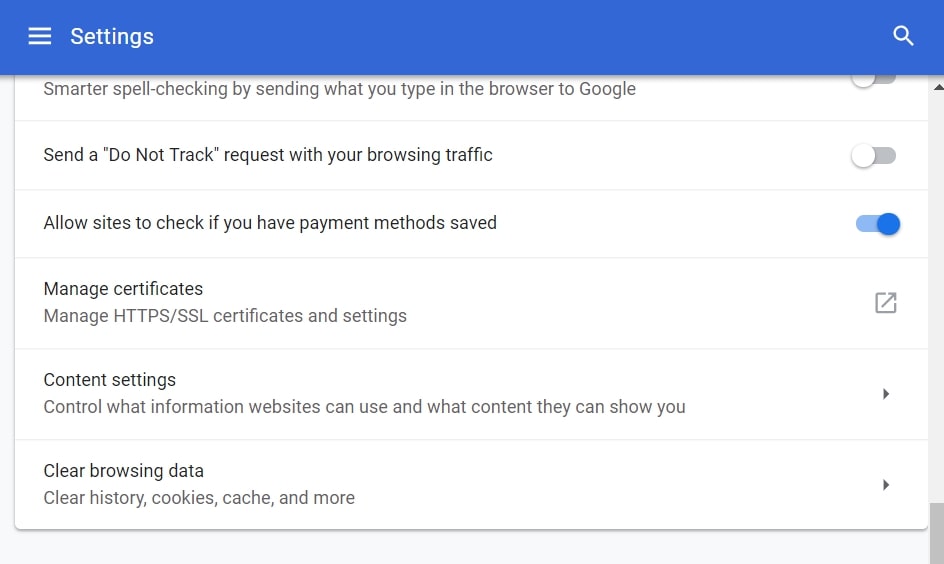
Passo 4: Aperto "notifiche":
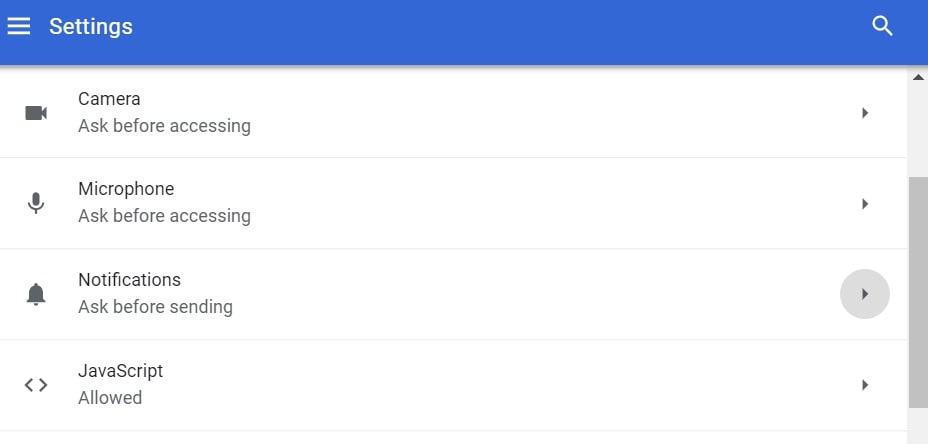
Passo 5: Fare clic sui tre punti e scegliere Blocca, Modificare o rimuovere le opzioni:

Rimuovere le notifiche push su Firefox
Passo 1: Vai a Opzioni di Firefox.
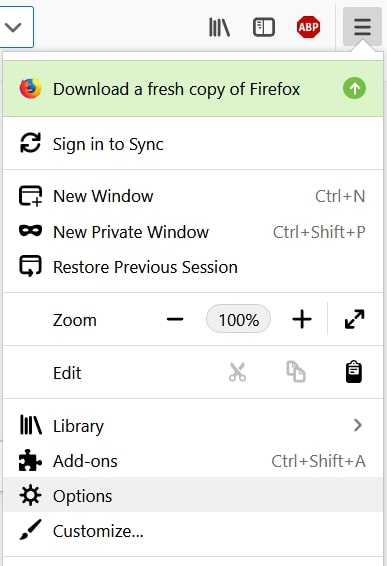
Passo 2: Vai alle impostazioni", digitare "notifiche" nella barra di ricerca e fare clic "Impostazioni":
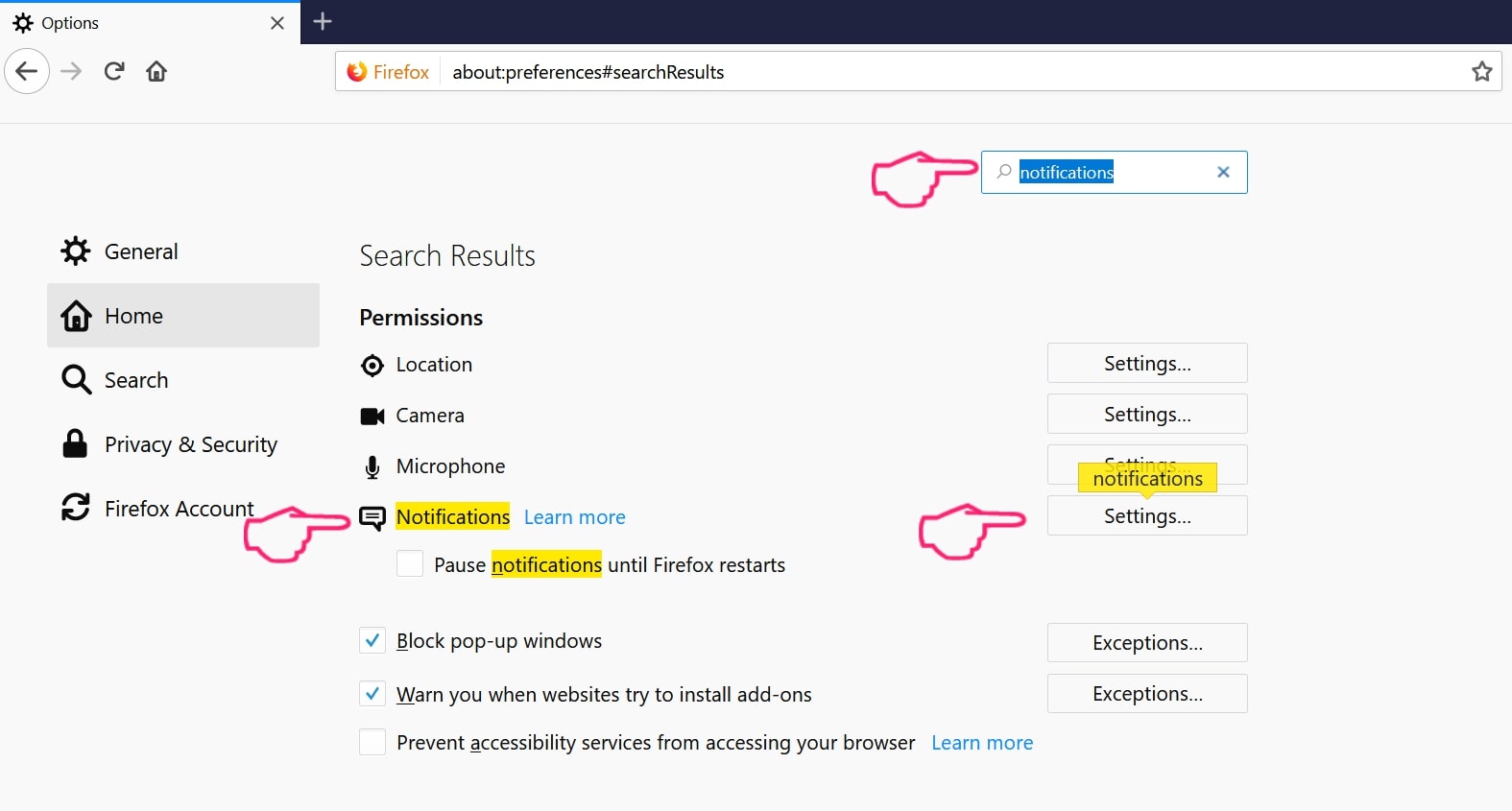
Passo 3: Fai clic su "Rimuovi" su qualsiasi sito in cui desideri che le notifiche vengano eliminate e fai clic su "Salva modifiche"
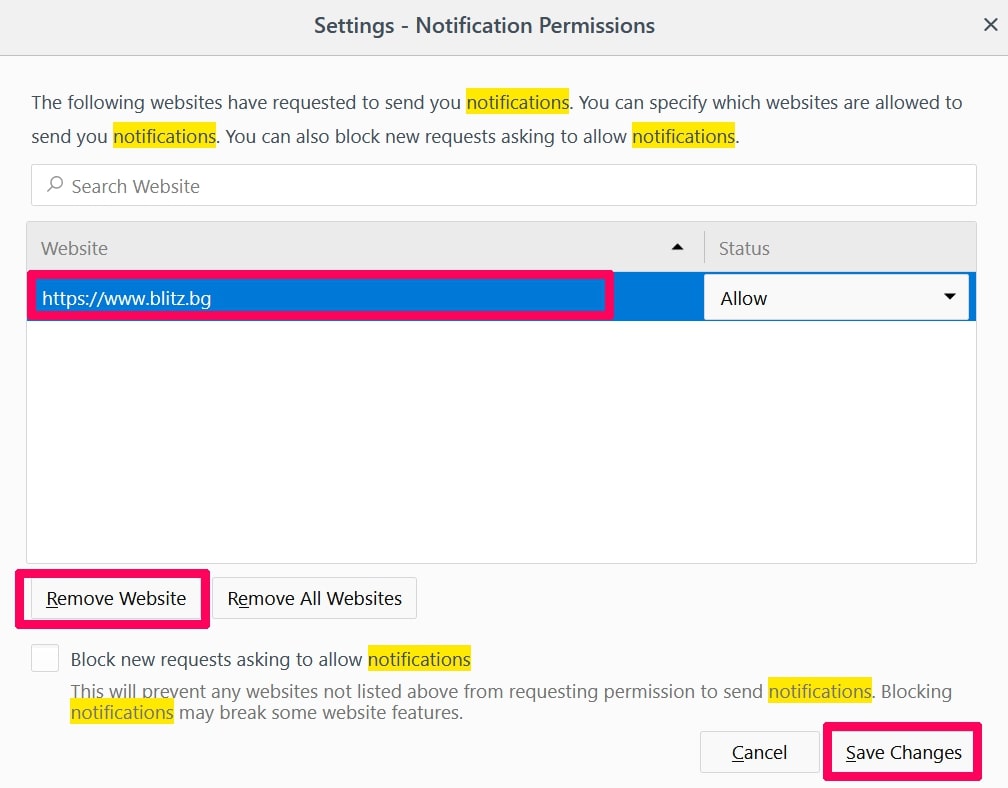
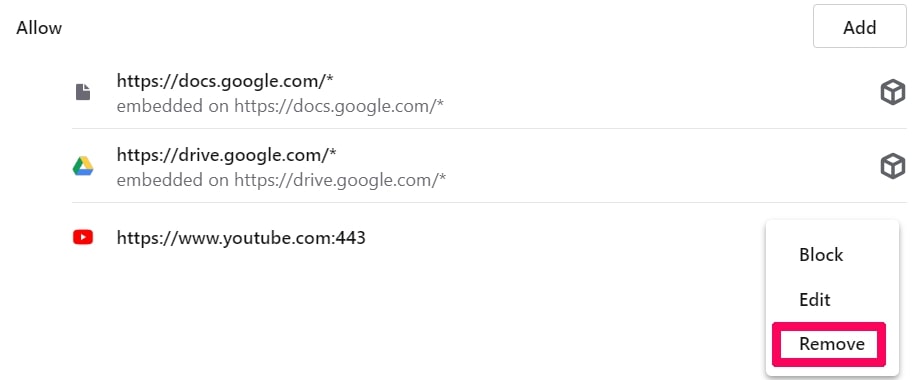
Interrompi le notifiche push su Opera
Passo 1: In Opera, stampa ALT + P per andare su Impostazioni.
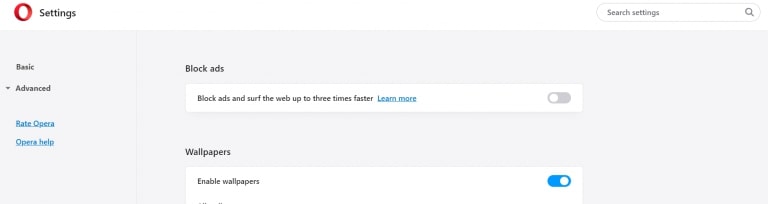
Passo 2: In Setting search, digitare "Contenuto" per accedere alle impostazioni del contenuto.
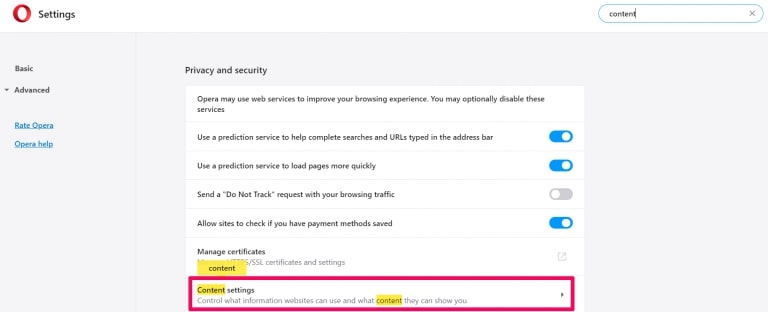
Passo 3: Notifiche aperte:
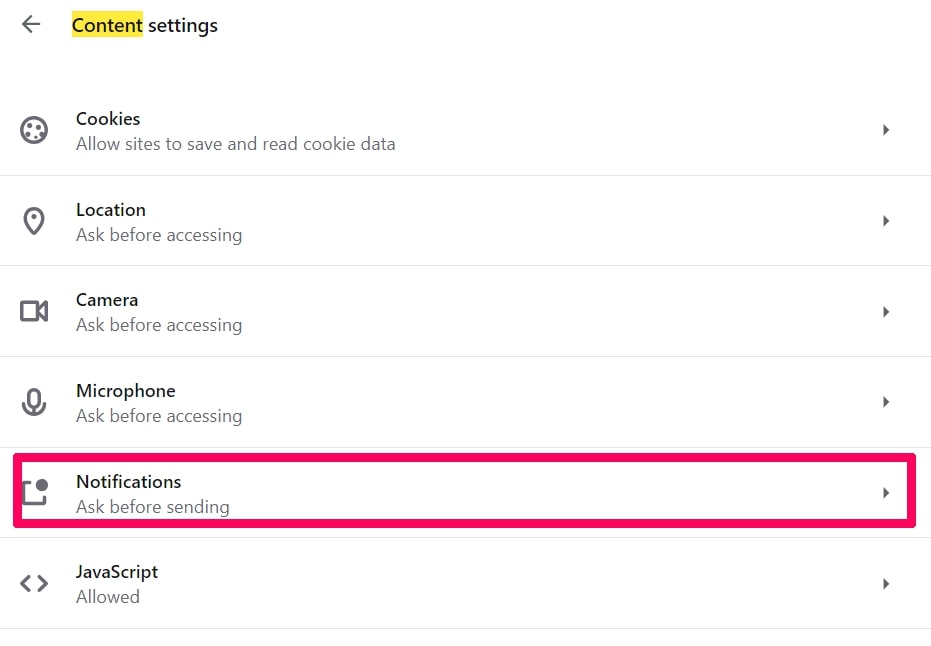
Passo 4: Fai lo stesso che hai fatto con Google Chrome (spiegato di seguito):
Elimina le notifiche push su Safari
Passo 1: Apri le preferenze di Safari.
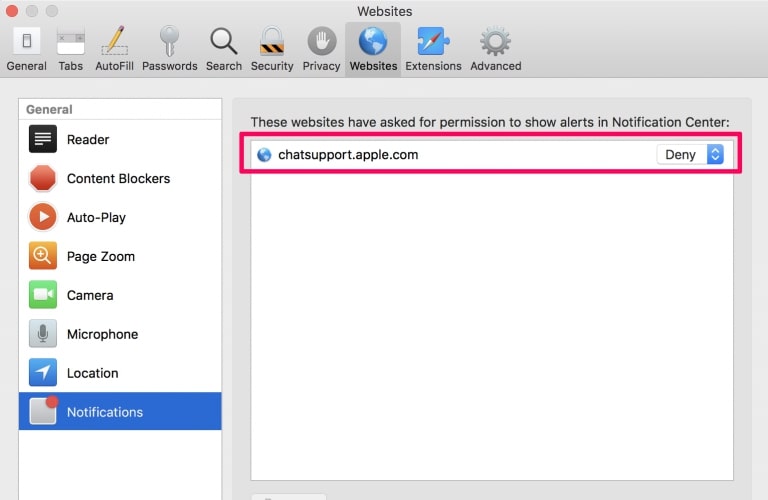
Passo 2: Scegli il dominio da cui ti piacciono i push pop-up e passa a "Negare" da parte di "permettere".
UC Browser-FAQ
What Is UC Browser?
La minaccia UC Browser è adware o virus redirect del browser.
Potrebbe rallentare notevolmente il computer e visualizzare annunci pubblicitari. L'idea principale è che le tue informazioni vengano probabilmente rubate o che più annunci vengano visualizzati sul tuo dispositivo.
I creatori di tali app indesiderate lavorano con schemi pay-per-click per fare in modo che il tuo computer visiti siti Web rischiosi o diversi tipi che potrebbero generare loro fondi. Questo è il motivo per cui non si preoccupano nemmeno dei tipi di siti Web visualizzati negli annunci. Questo rende il loro software indesiderato indirettamente rischioso per il tuo sistema operativo.
What Are the Symptoms of UC Browser?
Ci sono diversi sintomi da cercare quando questa particolare minaccia e anche le app indesiderate in generale sono attive:
Sintomo #1: Il tuo computer potrebbe rallentare e avere scarse prestazioni in generale.
Sintomo #2: Hai delle barre degli strumenti, componenti aggiuntivi o estensioni sui browser Web che non ricordi di aver aggiunto.
Sintomo #3: Vedi tutti i tipi di annunci, come i risultati di ricerca supportati da pubblicità, pop-up e reindirizzamenti per apparire casualmente.
Sintomo #4: Vedi le app installate sul tuo Mac in esecuzione automaticamente e non ricordi di averle installate.
Sintomo #5: Vedi processi sospetti in esecuzione nel tuo Task Manager.
Se vedi uno o più di questi sintomi, quindi gli esperti di sicurezza consigliano di controllare la presenza di virus nel computer.
Quali tipi di programmi indesiderati esistono?
Secondo la maggior parte dei ricercatori di malware ed esperti di sicurezza informatica, le minacce che attualmente possono colpire il tuo dispositivo possono essere software antivirus non autorizzato, adware, browser hijacker, clicker, ottimizzatori falsi e qualsiasi forma di PUP.
Cosa fare se ho un "virus" come UC Browser?
Con poche semplici azioni. Innanzitutto, è imperativo seguire questi passaggi:
Passo 1: Trova un computer sicuro e collegalo a un'altra rete, non quello in cui è stato infettato il tuo Mac.
Passo 2: Cambiare tutte le password, a partire dalle tue password e-mail.
Passo 3: consentire autenticazione a due fattori per la protezione dei tuoi account importanti.
Passo 4: Chiama la tua banca a modificare i dati della carta di credito (codice segreto, eccetera) se hai salvato la tua carta di credito per acquisti online o hai svolto attività online con la tua carta.
Passo 5: Assicurati che chiama il tuo ISP (Provider o operatore Internet) e chiedi loro di cambiare il tuo indirizzo IP.
Passo 6: Cambia il tuo Password Wi-Fi.
Passo 7: (Opzionale): Assicurati di scansionare tutti i dispositivi collegati alla tua rete alla ricerca di virus e ripeti questi passaggi per loro se sono interessati.
Passo 8: Installa anti-malware software con protezione in tempo reale su ogni dispositivo che hai.
Passo 9: Cerca di non scaricare software da siti di cui non sai nulla e stai alla larga siti web di bassa reputazione generalmente.
Se segui questi consigli, la tua rete e tutti i dispositivi diventeranno significativamente più sicuri contro qualsiasi minaccia o software invasivo delle informazioni e saranno privi di virus e protetti anche in futuro.
How Does UC Browser Work?
Una volta installato, UC Browser can raccogliere dati utilizzando tracker. Questi dati riguardano le tue abitudini di navigazione sul web, come i siti web che visiti e i termini di ricerca che utilizzi. Viene quindi utilizzato per indirizzarti con annunci pubblicitari o per vendere le tue informazioni a terzi.
UC Browser can also scaricare altro software dannoso sul tuo computer, come virus e spyware, che può essere utilizzato per rubare le tue informazioni personali e mostrare annunci rischiosi, che potrebbero reindirizzare a siti di virus o truffe.
Is UC Browser Malware?
La verità è che i PUP (adware, browser hijacker) non sono virus, ma potrebbe essere altrettanto pericoloso poiché potrebbero mostrarti e reindirizzarti a siti Web di malware e pagine di truffe.
Molti esperti di sicurezza classificano i programmi potenzialmente indesiderati come malware. Ciò è dovuto agli effetti indesiderati che i PUP possono causare, come la visualizzazione di annunci intrusivi e la raccolta di dati dell'utente senza la conoscenza o il consenso dell'utente.
Informazioni sulla ricerca sul browser UC
I contenuti che pubblichiamo su SensorsTechForum.com, questa guida alla rimozione di UC Browser inclusa, è il risultato di ricerche approfondite, duro lavoro e la dedizione del nostro team per aiutarti a rimuovere lo specifico, problema relativo all'adware, e ripristinare il browser e il sistema informatico.
Come abbiamo condotto la ricerca su UC Browser?
Si prega di notare che la nostra ricerca si basa su un'indagine indipendente. Siamo in contatto con ricercatori di sicurezza indipendenti, grazie al quale riceviamo aggiornamenti quotidiani sugli ultimi malware, adware, e definizioni di browser hijacker.
Inoltre, the research behind the UC Browser threat is backed with VirusTotal.
Per comprendere meglio questa minaccia online, si prega di fare riferimento ai seguenti articoli che forniscono dettagli informati.



