 O malware bancário está evoluindo e se transformando em uma das maiores ameaças na cena do malware, apesar do internacional, esforços colaborativos em nome de policiais e especialistas em crimes cibernéticos. Um novo relatório lançado pela Dell Secure Works Counter Threat Unit (CTU) ilustra perfeitamente o crescimento do malware bancário, e, particularmente, botnets bancários.
O malware bancário está evoluindo e se transformando em uma das maiores ameaças na cena do malware, apesar do internacional, esforços colaborativos em nome de policiais e especialistas em crimes cibernéticos. Um novo relatório lançado pela Dell Secure Works Counter Threat Unit (CTU) ilustra perfeitamente o crescimento do malware bancário, e, particularmente, botnets bancários.
O relatório se concentra em 2015 e fornece detalhes, análise aprofundada sobre a estrutura de botnet bancária quase impecável, e o surgimento de botnets como serviço e botnets móveis.
Botnets-as-a-service e botnets móveis entraram no mercado
Este modelo (botnet-as-a-service) ganhou popularidade em todo 2015, com mais agentes de malware alugando subconjuntos de seus botnets para outras operações maliciosas, como:
- DDoS (Negação de serviço distribuída) ataques;
- Fraude de clique;
- Mineração de criptomoeda;
- Ataques direcionados.
Mais sobre Trojans móveis
além do que, além do mais, botnets móveis também mostraram uso aumentado para uma série de atividades maliciosas, incluindo DDoS, fraude do clique, e ataques de falsificação de identidade. Não obstante, de acordo com a pesquisa, a demanda pelo serviço 'regular' de botnet como um kit é ainda maior, simplesmente porque dá aos criminosos cibernéticos a chance de controlar e monitorar totalmente a operação do malware.
bancários Botnets 2015: Velho versus Novo
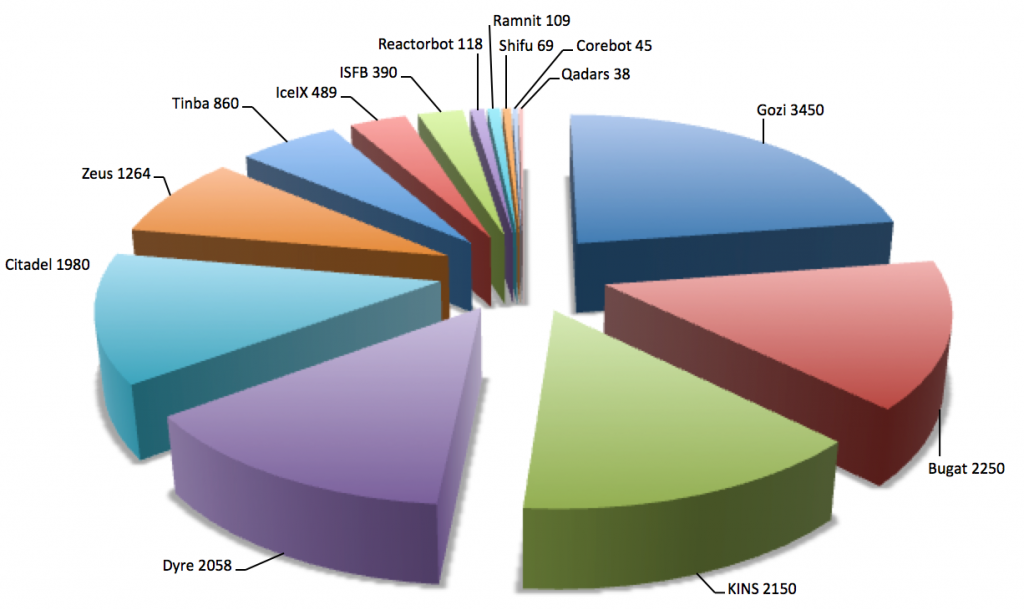
image Source: https://www.secureworks.com
Os pesquisadores observaram que vários botnets de 2014 continuou a funcionar. Contudo, novas adições entraram na infraestrutura de botnet:
- Shifu
- Corebot
- Reactorbot
2015 também viu um aumento na atividade de vários outros botnets, como Qadars, Tinba, Gozi Neverquest. No geral, botnets bancários mostraram uma atividade sem precedentes ao longo do ano passado, com o reaparecimento de Ramnit e Bugat depois de serem derrubados em 2014.
Felizmente, as operações de remoção do botnet não pararam, apesar da resiliência dos cibercriminosos. No ano passado, testemunhou uma maior colaboração entre as autoridades policiais e fornecedores de segurança, todos lutando para confiscar servidores e infraestruturas de botnets. Apenas um sucesso, Contudo, foi gravado, e foi o sucesso da derrubada do infame Dyre, depois que autoridades russas invadiram os escritórios de uma distribuidora de filmes localizada em Moscou.
bancários Botnets 2015: Recursos
Os botnets bancários geralmente são sofisticados em estrutura e implementam vários recursos. Mesmo que os botnets normalmente visem obter informações financeiras e usar sistemas comprometidos para obter ganhos financeiros, eles também visam informações pessoais. As credenciais de e-mail são frequentemente coletadas em operações baseadas em botnet. Ao longo 2015, botnets bancários alcançaram um novo ponto alto; a maioria deles foram observados para integrar comando de backup e soluções de controle via backup DGA (algoritmo de geração de domínio).
além do que, além do mais, a maioria dos botnets agora usa roteadores comprometidos como servidores proxy para ocultar os servidores reais de comando e controle, aproveite as redes p2p para contornar o monitoramento, e, não surpreendentemente, use Tor e I2P para resistir à divulgação.
bancários Botnets 2015: Alvos
Instituições financeiras e bancos continuaram a ser um alvo principal para botnets bancários. Contudo, criminosos mostraram interesse em finanças corporativas e serviços de folha de pagamento e organizações de negociação de ações, situado principalmente em regiões desenvolvidas com residentes ricos. Os pesquisadores observaram atores de malware visando países com proteção de conta fraca e dificuldades em transações internacionais. Curiosamente, criminosos também estavam interessados em países que exigiam interferência local em termos de lavagem de dinheiro. Em outras palavras, alvos primários para 2015 eram bancos e várias instituições financeiras na região da Ásia-Pacífico, o Oriente Médio, e Europa Oriental.
Mais sobre Banking Malware
Botnets bancários entregando ransomware
2015 viu uma reviravolta interessante - observou-se que botnets bancários entregavam não apenas Trojans bancários, mas também peças de ransomware. A equipe CTU da Dell explica a mudança com a necessidade cada vez maior de grupos organizados de crimes cibernéticos encontrarem novas maneiras de roubar dinheiro de suas vítimas. Essa explicação simples também ilustra a intensidade em malware móvel e botnet-as-a-service.
Dê uma olhada em Relatório da Dell CTU.













