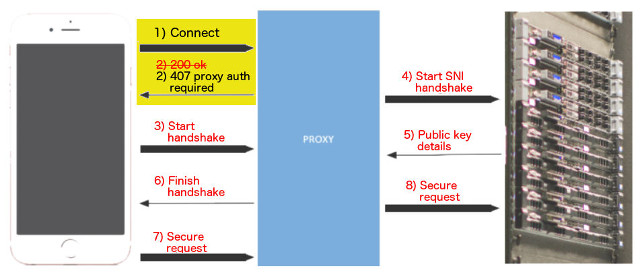
En ny sårbarhed, som kan sætte en række produkter på risiko er blevet netop offentliggjort af sikkerhed forsker Jerry Decime. Han har afsløret chokerende detaljer om fejlen, døbt FalseCONNECT. Ifølge Decime analyse, sårbarheden kan tillade et Man-in-the-Middle-angreb og opfange HTTPS-trafik. Dette skyldtes mangler ved implementeringen af proxy-godkendelsesprocedurer i flere produkter. Mere præcist, der er en fejl i, hvordan specifikke applikationer reagerer på HTTP CONNECT-anmodninger via HTTP / 1.0 407 Proxy-godkendelse Nødvendige svar.
Et dybere kig på sårbarheden FalseCONNECT
Kort sagt:
Der blev begået fejl ved implementeringen af proxy-godkendelse. Dette, på tur, resulterede i adskillige sårbarheder med implementeringerne af “HTTP / 1.0 407 Proxy-godkendelse påkrævet” svar på CONNECT-anmodninger på tværs af en bred vifte af operativsystemer, ansøgninger, og browsere til enhver enhed, der er konfigureret til at bruge en proxy og endda nogle, der ikke var med automatisk proxy-understøttelse aktiveret som standard i Windows.
Det er vigtigt at bemærke, at fejlen kun findes i netværksmiljøer. Det er her, brugerne anvender proxy-forbindelser. Opsætningen er for det meste populær i virksomhedsnetværk, hvor kraftfulde firewalls er sat på plads. Hvis en hacker har adgang til et kompromitteret netværk og kunne lytte til proxytrafik, han kunne også let snuse efter HTTP CONNECT-anmodninger sendt til den lokale proxy.
Når en sådan anmodning er opfanget af en angriber, han kan svare på det i stedet for den rigtige proxyserver. Derefter, angriberen kan udstede en 407 Proxy-godkendelse Nødvendigt svar, hvor brugeren bliver bedt om en adgangskode for at få adgang til en tjeneste.
Hvorfor kaldes sårbarheden FalseCONNECT? Berørte leverandører
HTTP-forbindelsesanmodninger er ukrypteret, og en angriber ved, hvornår målet ønsker at få adgang til følsomme konti. Dette kan ske, selv når tjenesterne er HTTPS.
Hvem er påvirket af FalseCONNECT?
Med forskerens egne ord:
Den værste af disse sårbarheder [er] påvirker Apple, som indtil frigivelsen af iOS 9.3.3 opdatering manifesteret som en komplet fejl i HTTPS-tillid i iOS, alle versioner siden mindst iOS 5.1.1 til OS-tillidskomponenter, Safari, Opera, og applikationer, der bruger WebKit, når du bruger proxyer.
Desuden, forskeren fandt ud af, at WebKit-software er mere sårbar end andre.
Hvad er WebKit?
WebKit er en layoutmotorsoftwarekomponent til gengivelse af websider i webbrowsere. WebKit driver også Apples Safar, og en fork af projektet bruges af Chrom-baserede browsere, som Google Chrome og Opera. US-CERT har advaret om det “WebKit-baserede klienter er sårbare over for yderligere vektorer på grund af det faktum, at HTML-markering og JavaScript gengives af klientens Document Object Model (DOM) i sammenhæng med det oprindeligt anmodede HTTPS-domæne.”
Apple, Microsoft, Oracle og Opera har allerede godkendt deres produkter, der er berørt af fejlen. Andre leverandører beregner stadig risikoen for FalseCONNECT og den indvirkning, det kan have på deres produkter. Listen inkluderer Linux-distroer, Cisco, HP, IBM, Google, Enebær, Nokia, Mozilla, SAP, Sony, etc.
Leverandører kan teste for denne sårbarhed ved hjælp af en opsnappende proxy som The Fiddler. Det understøtter CONNECT-aflytning. Lidt FiddlerScript efter OnBeforeResponse-funktionen er alt, hvad der er brug for, tilføjer forskeren.
Flere oplysninger om denne alvorlige fejl er tilgængelige på FalseConnect's dedikerede side.