Hævn Trojan er et farligt våben brugt mod computerbrugere over hele verden. Det inficerer primært via inficerede software installatører. Vores artikel giver et overblik over sin adfærd i overensstemmelse med de indsamlede prøver og tilgængelige rapporter, også det kan være nyttigt i forsøget på at fjerne virus.

Trussel Summary
| Navn | Revenge Trojan |
| Type | Trojan |
| Kort beskrivelse | The Revenge Trojan er en computervirus, der er designet til lydløst at infiltrere computersystemer. |
| Symptomer | Ofrene kan ikke opleve nogen synlige symptomer på infektion. |
| Distributionsmetode | Software Sårbarheder, Freeware installationer, Bundtede pakker, Scripts og andre. |
| Værktøj Detection |
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
| Brugererfaring | Tilmeld dig vores forum at diskutere hævn Trojan. |

Hævn Trojan - Distributionsmetoder
Hævn Trojan er blevet opdaget i en nylig angrebskampagne. Et ukendt hackerkollektiv står bag de igangværende angreb, i øjeblikket er der ingen oplysninger om deres identitet. De fangede prøver blev identificeret som malware gennem en af de mest almindelige indtrængningsmekanismer - inficerede dokumenter. Virusinstallationskoden er lavet som en del af makroer, der er integreret i nyttelastdokumenterne, de kan være af en hvilken som helst af de populære typer: tekstdokumenter, regneark, præsentationer og databaser. Når de er åbnet af offerbrugerne, vises der en prompt, der beder ofrene om at aktivere indholdet. Vinduet angiver normalt, at dette er påkrævet for at se filerne korrekt.
Hvad der er farligere er, at andre lignende taktikker også kan anvendes. Et af de almindelige tilfælde er, når hackerne integrerer instruktionerne om virusinstallation i softwareopsætningsfiler. De er målrettet mod applikationer, der populært downloades af slutbrugere såsom systemværktøjer, kreativitet suiter, produktivitet og kontor apps og etc.
Både selve virusfilerne og disse to nyttelasttyper spredes normalt gennem metoder, der kan inficere tusindvis af brugere på én gang. Der er flere metoder, såsom følgende:
- E-mail-spam-meddelelser - Hackerne kan lave phishing-e-mails, der ser ud til, at meddelelser sendes af legitime tjenester. Dette gøres ved hjælp af deres eget designlayout og teksttekstindhold. De falske e-mail-phishing-meddelelser knytter filerne i tekstlink eller interaktivt indhold. Alternativt kan de knyttes direkte til meddelelserne.
- Ondsindede websteder - En relateret strategi er at oprette websider, der efterligner legitime tjenester, download-portaler, destinationssider og etc. De er hostet på lignende lydende domænenavne og i nogle tilfælde ved hjælp af stjålne eller hacker-genererede sikkerhedscertifikater.
- Fildelingswebsteder - Både de uafhængige filer og inficerede nyttelast er vidt tilgængelige på netværk som BitTorrent, hvor både legitimt og piratindhold deles frit på tværs af internetbrugere.
- Browser Hijackers - Farlige webbrowser-plugins kan laves af de kriminelle, der gøres kompatible med de mest populære webbrowsere og uploades til de relevante arkiver. De ledsages af falske brugeranmeldelser og stjålne eller hackerfremstillede udvikleroplysninger for at forvirre ofrene til at tro, at udvidelsen er sikker. Deres beskrivelser vil love tilføjelsen af nye funktioner eller ydeevneoptimeringer.
Andre taktikker kan desuden bruges i kommende angreb og kommende versioner af Revenge Trojan.

Revenge Trojan - Detaljeret beskrivelse
Revenge Trojan ser ud til at være en original oprettelse, der ikke bruger nogen kodestykker fra tidligere trusler. På dette tidspunkt, hvor denne artikel skrives, er der information om identiteten af gruppen bag de igangværende angreb. Vi antager, at truslen er modulopbygget og at forskellige moduler kan tilføjes til den.
Den erobrede Revenge Trojan-forekomst ser ud til at starte en hovedmotor, der forbinder til en hackerstyret server og giver de kriminelle operatører mulighed for at spionere på ofrene. Gennem denne sikre forbindelse har de evnen til at overtage kontrollen med de berørte maskiner, stjæle deres data og udføre alle mulige ondsindede handlinger.
Et PowerShell-baseret script lanceres, der giver mulighed for at tilføje alle mulige komponenter. Trojanske heste som denne inkluderer normalt et bestemt sæt almindelige adfærdsmønstre. En liste af dem er følgende:
- Informationssøgning - Motoren kan programmeres til at udtrække følsomme oplysninger, der kan bruges til at generere et unikt ID, der er specifikt for hver enkelt computer. Dette gøres ved hjælp af en algoritme, der tager sine inputparametre fra datasæt, såsom delelisten over de installerede hardwarekomponenter, brugerindstillinger, regionale præferencer og andre relaterede metrics. Den anden farlige mekaniker, der anvendes af trojanske heste, er eksponering af personlig information, som gøres ved at programmere strengene til at lede efter strenge, der direkte afslører ofrene. Almindelige inkluderer deres navn, adresse, telefonnummer, interesser og eventuelle gemte kontooplysninger. Hvis Trojan interagerer med Windows Volume Manager, kan den også søge i de flytbare lagerenheder og tilgængelige netværksdele. De opnåede datasæt kan bruges til forskellige forbrydelser, herunder identitetstyveri, afpresning og økonomisk udnyttelse.
- Boot Options Ændring - En populær mekanisme, der er en del af de fleste trojanske heste, muligvis inklusive fremtidige Revenge Trojan-varianter, er evnen til at ændre bootindstillinger og konfigurationsfiler, der indstiller den til automatisk at starte, når computeren er tændt. Dette kan også deaktivere de fleste manuelle brugergendannelsesguider, da de er afhængige af adgang til opstartsmenuer til gendannelse.
- Windows Registry Ændringer - Trojan-modulet er i stand til at få adgang til registreringsdatabaseoptegnelserne ikke kun for at oprette strenge for sig selv, men også for at ændre eksisterende. Hvis værdier, der bruges af operativsystemet, påvirkes, er offerbrugerne ikke i stand til at få adgang til visse tjenester og kan opleve alvorlige ydeevneproblemer. Ændringer i strenge, der bruges af tredjepartsapplikationer, kan føre til uventede fejl.
- Fjernelse af følsomme data - Motoren kan programmeres til at finde og slette følsomme filer, der alvorligt kan forstyrre den sædvanlige gendannelsesprocedure. Dette gøres ved at målrette mod systemgendannelsespunkter, Backups, Shadow Volume Kopier og etc. I dette tilfælde er ofrene nødt til at se en kombination af et anti-spywareprogram af professionel kvalitet og datagendannelsesprogram.
- Yderligere Payloads Levering - Revenge Trojan kan instrueres i at indsætte andre ondsindede trusler på de kompromitterede maskiner.
Future Revenge Trojan-kampagner kan instrueres i at udføre andre handlinger som konfigureret af hackerne.

Fjern Revenge Trojan
Hvis din computer-system fik inficeret med Revenge Trojan, du skal have lidt erfaring med at fjerne malware. Du bør slippe af med denne trojanske så hurtigt som muligt, før det kan få mulighed for at sprede sig yderligere og inficere andre computere. Du bør fjerne den trojanske og følg trin-for-trin instruktioner guide leveres nedenfor.
Note! Dit computersystem kan blive påvirket af Revenge Trojan og andre trusler.
Scan din pc med SpyHunter
SpyHunter er en kraftfuld malware fjernelse værktøj designet til at hjælpe brugerne med dybdegående systemets sikkerhed analyse, detektering og fjernelse af Revenge Trojan.
Husk, at SpyHunter scanner er kun for malware afsløring. Hvis SpyHunter registrerer malware på din pc, du bliver nødt til at købe SpyHunter har malware fjernelse værktøj til at fjerne malware trusler. Læs vores SpyHunter 5 bedømmelse. Klik på de tilsvarende links til at kontrollere SpyHunter s EULA, Fortrolighedspolitik og Kriterier trusselsvurdering.
For at fjerne Revenge Trojan følge disse trin:
Brug SpyHunter at scanne for malware og uønskede programmer
Preparation before removing Revenge Trojan.
, Før den egentlige fjernelse proces, Vi anbefaler, at du gør følgende forberedelse trin.
- Sørg for at have disse instruktioner altid åben og foran dine øjne.
- Gør en sikkerhedskopi af alle dine filer, selv om de kunne blive beskadiget. Du bør sikkerhedskopiere dine data med en sky backup-løsning og forsikre dine filer mod enhver form for tab, selv fra de mest alvorlige trusler.
- Vær tålmodig, da det kan tage et stykke tid.
- Scan for malware
- Rette registre
- Fjern virusfiler
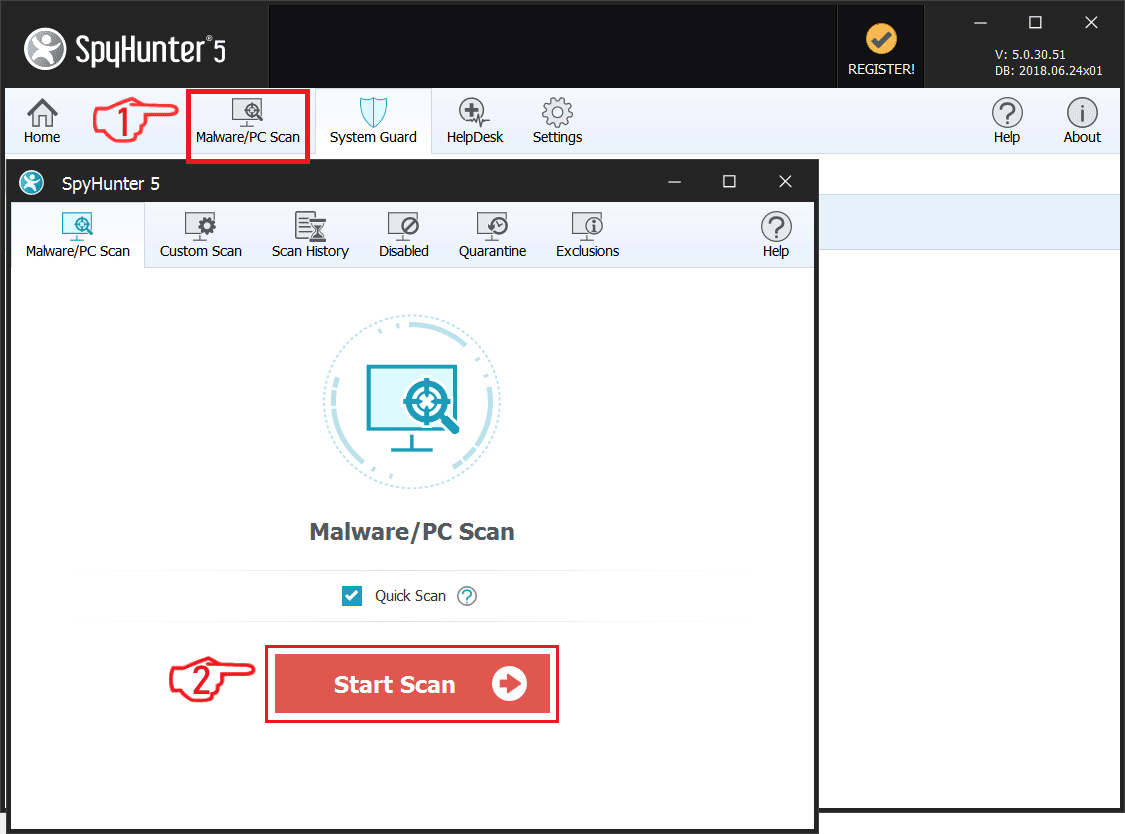
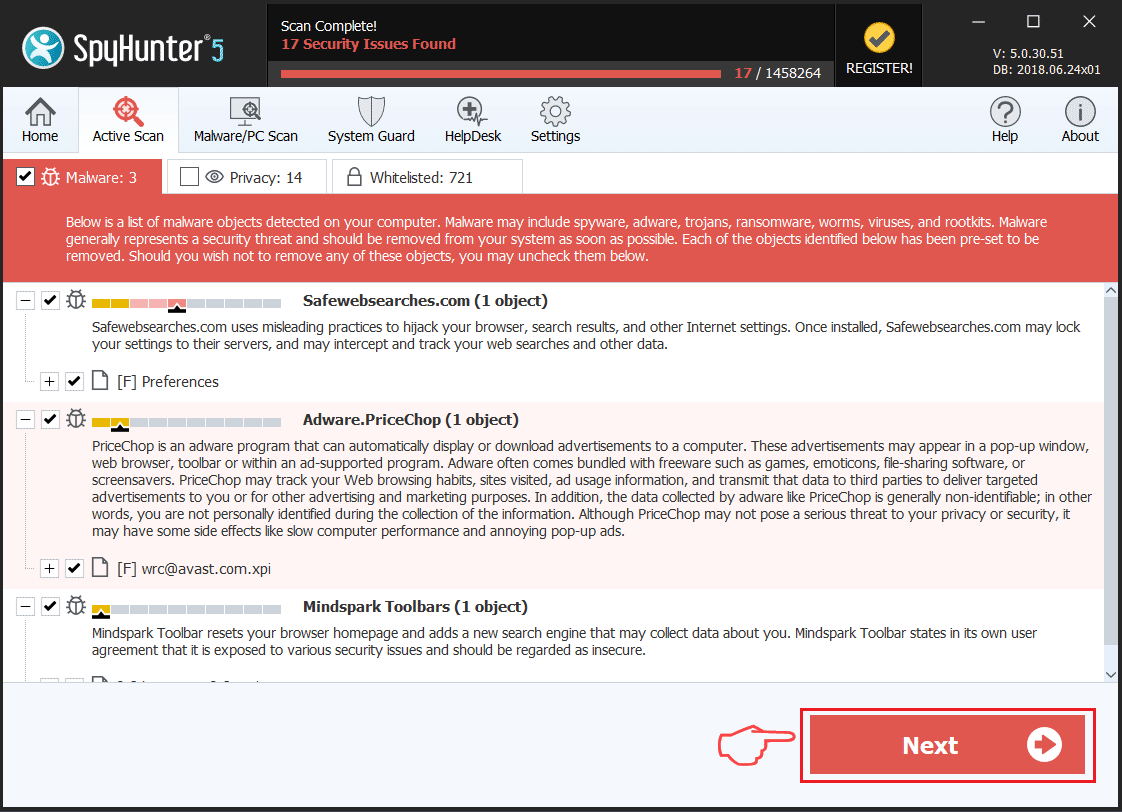
Trin 1: Scan for Revenge Trojan med SpyHunter Anti-Malware-værktøj



Trin 2: Rens eventuelle registre, oprettet af Revenge Trojan på din computer.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, oprettet af Revenge Trojan der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.Trin 3: Find virus files created by Revenge Trojan on your PC.
1.For Windows 8, 8.1 og 10.
For Nyere Windows-operativsystemer
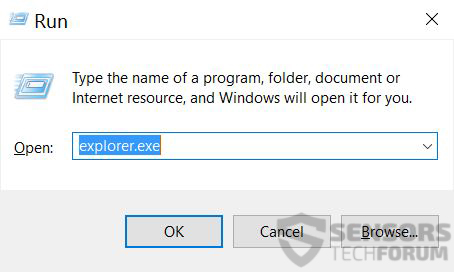
1: På dit tastatur tryk + R og skrive explorer.exe i Løbe tekstboks og derefter klikke på Ok knap.

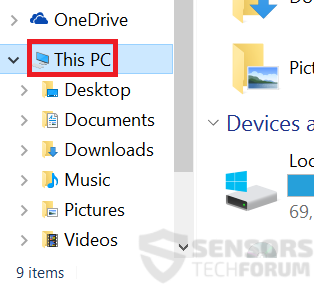
2: Klik på din pc fra hurtig adgang bar. Dette er normalt et ikon med en skærm og dets navn er enten "Min computer", "Min PC" eller "Denne PC" eller hvad du har navngivet det.

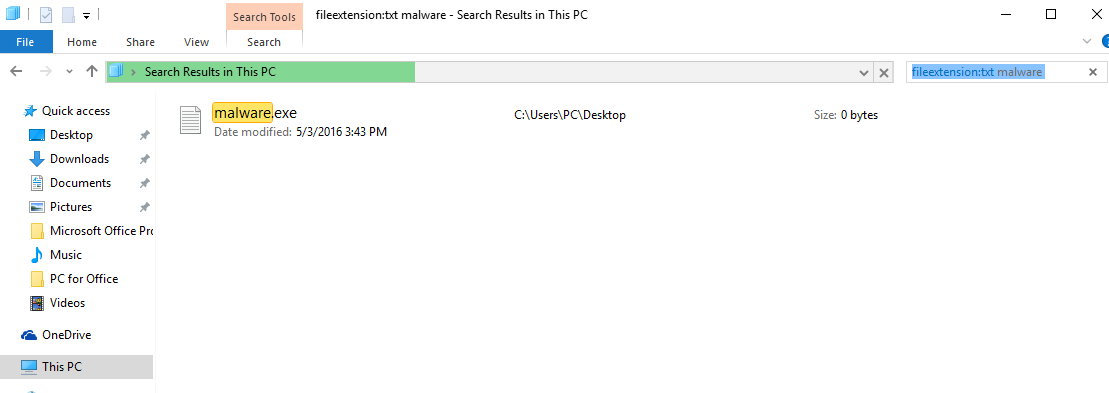
3: Naviger til søgefeltet øverst til højre på din pc's skærm og type "fileextension:" og hvorefter skrive filtypen. Hvis du er på udkig efter ondsindede eksekverbare, et eksempel kan være "fileextension:exe". Efter at gøre det, efterlade et mellemrum og skriv filnavnet du mener malware har skabt. Her er, hvordan det kan se ud, hvis der er fundet din fil:

NB. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.I Windows XP, Vista, og 7.
For ældre Windows-operativsystemer
I ældre Windows OS bør den konventionelle tilgang være den effektive:
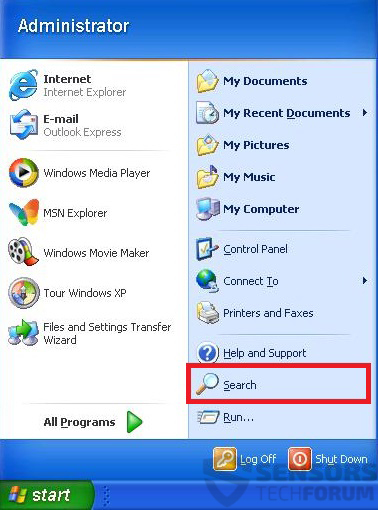
1: Klik på Start Menu ikon (normalt på din nederste venstre) og vælg derefter Søg præference.

2: Efter søgningen vises, vælge Flere avancerede indstillinger fra søgningen assistent boksen. En anden måde er ved at klikke på Alle filer og mapper.

3: Efter denne type navnet på den fil, du søger, og klik på knappen Søg. Dette kan tage noget tid, hvorefter resultater vises. Hvis du har fundet den skadelig fil, du må kopiere eller åbne sin placering ved højreklikke på det.
Nu skulle du være i stand til at opdage en fil på Windows, så længe det er på din harddisk og ikke skjult via speciel software.
Revenge Trojan FAQ
What Does Revenge Trojan Trojan Do?
The Revenge Trojan Trojan er et ondsindet computerprogram designet til at forstyrre, skade, eller få uautoriseret adgang til et computersystem.
Det kan bruges til at stjæle følsomme data, få kontrol over et system, eller starte andre ondsindede aktiviteter.
Kan trojanske heste stjæle adgangskoder?
Ja, Trojans, like Revenge Trojan, kan stjæle adgangskoder. Disse ondsindede programmer are designed to gain access to a user's computer, spionere på ofrene og stjæle følsomme oplysninger såsom bankoplysninger og adgangskoder.
Can Revenge Trojan Trojan Hide Itself?
Ja, det kan. En trojaner kan bruge forskellige teknikker til at maskere sig selv, inklusive rootkits, kryptering, og formørkelse, at gemme sig fra sikkerhedsscannere og undgå registrering.
Kan en trojaner fjernes ved fabriksnulstilling?
Ja, en trojansk hest kan fjernes ved at nulstille din enhed til fabriksindstillinger. Dette skyldes, at det vil gendanne enheden til sin oprindelige tilstand, eliminering af skadelig software, der måtte være blevet installeret. Husk på, at der er mere sofistikerede trojanske heste, der efterlader bagdøre og geninficerer selv efter fabriksnulstilling.
Can Revenge Trojan Trojan Infect WiFi?
Ja, det er muligt for en trojaner at inficere WiFi-netværk. Når en bruger opretter forbindelse til det inficerede netværk, trojaneren kan spredes til andre tilsluttede enheder og kan få adgang til følsomme oplysninger på netværket.
Kan trojanske heste slettes?
Ja, Trojanske heste kan slettes. Dette gøres typisk ved at køre et kraftfuldt anti-virus eller anti-malware program, der er designet til at opdage og fjerne ondsindede filer. I nogle tilfælde, manuel sletning af trojaneren kan også være nødvendig.
Kan trojanske heste stjæle filer?
Ja, Trojanske heste kan stjæle filer, hvis de er installeret på en computer. Dette gøres ved at tillade malware forfatter eller bruger for at få adgang til computeren og derefter stjæle filerne, der er gemt på den.
Hvilken anti-malware kan fjerne trojanske heste?
Anti-malware programmer som f.eks SpyHunter er i stand til at scanne efter og fjerne trojanske heste fra din computer. Det er vigtigt at holde din anti-malware opdateret og regelmæssigt scanne dit system for skadelig software.
Kan trojanske heste inficere USB?
Ja, Trojanske heste kan inficere USB enheder. USB-trojanske heste spredes typisk gennem ondsindede filer downloadet fra internettet eller delt via e-mail, allowing the hacker to gain access to a user's confidential data.
About the Revenge Trojan Research
Indholdet udgiver vi på SensorsTechForum.com, this Revenge Trojan how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed til at hjælpe dig med at fjerne det specifikke trojanske problem.
How did we conduct the research on Revenge Trojan?
Bemærk venligst, at vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om de seneste malware-definitioner, herunder de forskellige typer trojanske heste (bagdør, Downloader, infostealer, løsesum, etc.)
Endvidere, the research behind the Revenge Trojan threat is backed with VirusTotal.
For bedre at forstå truslen fra trojanske heste, Se venligst følgende artikler, som giver kyndige detaljer.













 1. I Windows XP, Vista og 7.
1. I Windows XP, Vista og 7. 2. For Windows 8, 8.1 og 10.
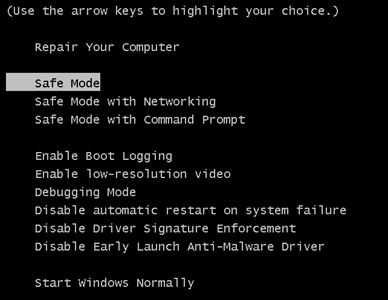
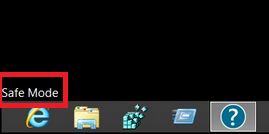
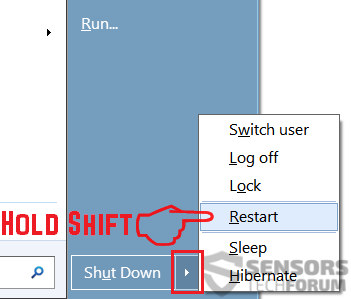
2. For Windows 8, 8.1 og 10. oplysningerne Fix registreringsdatabasen skabt af malware og PUP på din pc.
oplysningerne Fix registreringsdatabasen skabt af malware og PUP på din pc.
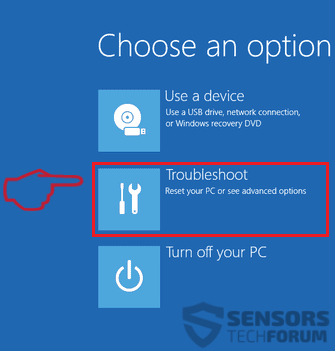
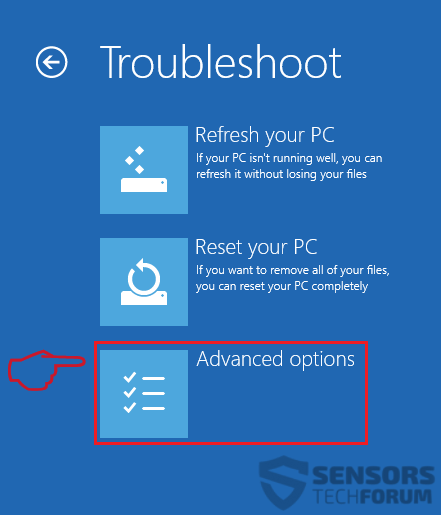
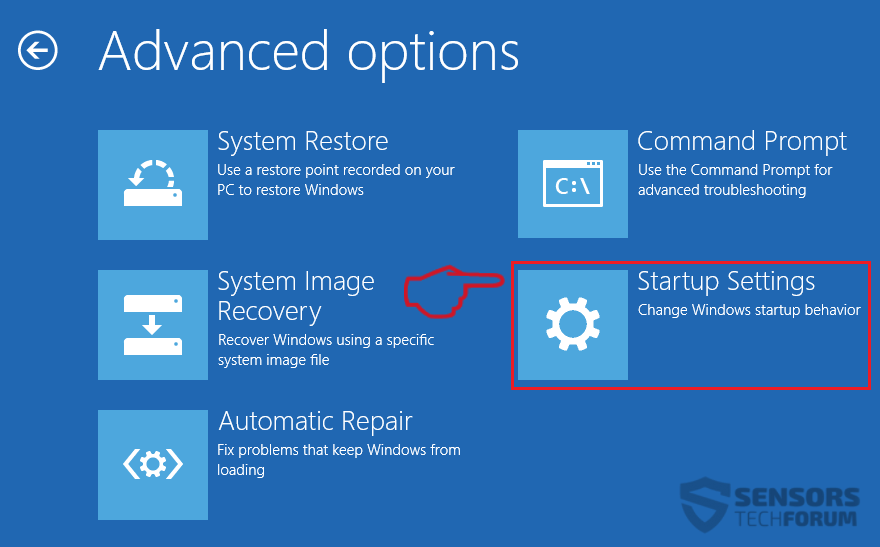
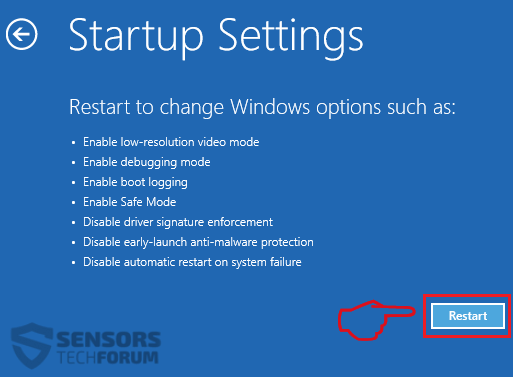
 1. Installer SpyHunter for at scanne efter Revenge Trojan og fjerne dem.
1. Installer SpyHunter for at scanne efter Revenge Trojan og fjerne dem.