Le cheval de Troie de vengeance est une arme dangereuse utilisée contre les utilisateurs d'ordinateurs dans le monde entier. Le virus infecte principalement par les installateurs de logiciels infectés. Notre article donne un aperçu de son comportement en fonction des échantillons recueillis et les rapports disponibles, aussi il peut être utile pour tenter de supprimer le virus.

Menace Résumé
| Nom | La revanche de Troie |
| Type | Troyen |
| brève description | Le cheval de Troie Revenge est un virus informatique conçu pour s'infiltrer silencieusement dans les systèmes informatiques. |
| Symptômes | Les victimes peuvent ne présentent aucun symptôme apparent d'infection. |
| Méthode de distribution | Les vulnérabilités de logiciels, Installations Freeware, Forfaits groupés, Scripts et autres. |
| Detection Tool |
Voir si votre système a été affecté par des logiciels malveillants
Télécharger
Malware Removal Tool
|
| Expérience utilisateur | Rejoignez notre Forum pour discuter de la vengeance Trojan. |

Revenge Trojan - Méthodes de distribution
Le cheval de Troie Revenge a été repéré lors d'une récente campagne d'attaque. Un collectif de hackers inconnu est à l'origine des attaques en cours, pour le moment il n'y a aucune information sur leur identité. Les échantillons capturés ont été identifiés comme des logiciels malveillants via l'un des mécanismes d'intrusion les plus courants - documents infectés. Le code d'installation du virus fait partie des macros intégrées dans les documents de charge utile, ils peuvent être de tout l'un des types populaires: des documents texte, feuilles de calcul, des présentations et des bases de données. Une fois qu'ils sont ouverts par les utilisateurs victimes, une invite apparaîtra demandant aux victimes d'activer le contenu. La fenêtre indiquera généralement que cela est nécessaire pour afficher correctement les fichiers.
Ce qui est plus dangereux, c'est que d'autres tactiques similaires peuvent également être utilisées. L'un des cas courants est celui où les pirates intègrent les instructions d'installation du virus dans fichiers de configuration du logiciel. Ils ciblent les applications généralement téléchargées par les utilisateurs finaux, telles que les utilitaires système, suites de créativité, des applications de productivité et de bureau et etc.
Les fichiers de virus eux-mêmes et ces deux types de charges utiles sont généralement propagés par des méthodes qui peuvent infecter des milliers d'utilisateurs à la fois. Il existe plusieurs méthodes telles que les suivantes:
- Email SPAM Messages - Les pirates peuvent créer des e-mails de phishing qui apparaissent comme des notifications envoyées par des services légitimes. Cela se fait en utilisant leur propre mise en page de conception et le contenu du corps du texte. Les faux messages de phishing par e-mail lieront les fichiers dans des liens texte ou des contenus interactifs. Alternativement, ils peuvent être directement joints aux messages.
- Les sites Web malveillants - Une stratégie connexe consiste à créer des pages Web qui imitent des services légitimes, portails de téléchargement, pages d'atterrissage et etc. Ils sont hébergés sur des noms de domaine similaires et, dans certains cas, utilisent des certificats de sécurité volés ou générés par des hackers..
- Sites de partage de fichiers - Les fichiers autonomes et les charges utiles infectées sont largement disponibles sur des réseaux comme BitTorrent où le contenu légitime et pirate est librement partagé entre les utilisateurs d'Internet.
- pirates de navigateur - Des plugins de navigateur Web dangereux peuvent être créés par les criminels qui sont rendus compatibles avec les navigateurs Web les plus populaires et téléchargés dans les référentiels appropriés. Ils sont accompagnés de faux avis d'utilisateurs et d'identifiants de développeur volés ou créés par un pirate afin de faire croire aux victimes que l'extension est sûre.. Leurs descriptions promettent l'ajout de nouvelles fonctionnalités ou d'optimisations de performances.
D'autres tactiques peuvent également être utilisées dans les attaques à venir et les prochaines versions du cheval de Troie Revenge.

Revenge Trojan - Description détaillée
Le cheval de Troie Revenge semble être une création originale qui n'utilise aucun extrait de code des menaces précédentes. Au moment de la rédaction de cet article, il existe des informations sur l'identité du groupe à l'origine des attaques en cours.. Nous supposons que la menace est de nature modulaire et que divers modules peuvent y être ajoutés.
L'instance de cheval de Troie Revenge capturée semble lancer un moteur principal qui se connecte à un serveur contrôlé par un pirate informatique et permet aux opérateurs criminels d'espionner les victimes.. Grâce à cette connexion sécurisée, ils ont la possibilité de prendre le contrôle des machines concernées, voler leurs données et mener toutes sortes d'actions malveillantes.
Un script basé sur PowerShell est lancé, ce qui permet d'ajouter toutes sortes de composants. Les chevaux de Troie tels que celui-ci incluent généralement tous un certain ensemble de modèles de comportement courants. Une liste d'entre eux est le suivant:
- Récupération de l'information - Le moteur peut être programmé pour extraire des informations sensibles qui peuvent être utilisées pour générer un identifiant unique spécifique à chaque ordinateur individuel. Ceci est fait par un algorithme qui prend ses paramètres d'entrée à partir d'ensembles de données tels que la liste des pièces des composants matériels installés, paramètres utilisateur, préférences régionales et autres mesures connexes. L'autre mécanisme dangereux utilisé par les chevaux de Troie est l'exposition d'informations personnelles qui se fait en programmant les chaînes pour rechercher des chaînes qui contiennent directement révéler les victimes. Les plus communs incluent leur nom, adresse, numéro de téléphone, intérêts et les informations d'identification de compte stockées. Si le cheval de Troie interagit avec Windows Volume Manager, il peut également rechercher les périphériques de stockage amovibles et les partages réseau disponibles. Les ensembles de données obtenus peuvent être utilisés pour divers crimes, y compris le vol d'identité, chantage et d'abus financier.
- Modification des options de démarrage - Un mécanisme populaire qui fait partie de la plupart des chevaux de Troie, éventuellement y compris les futures variantes du cheval de Troie Revenge, est la possibilité de modifier les options de démarrage et les fichiers de configuration qui le configureront pour démarrer automatiquement une fois que l'ordinateur est allumé. Cela peut également désactiver la plupart des guides de récupération manuelle de l'utilisateur car ils dépendent de l'accès aux menus de démarrage de récupération.
- Les modifications du Registre Windows - Le module Trojan est capable d'accéder aux enregistrements du Registre non seulement pour créer des chaînes pour lui-même mais aussi pour modifier celles existantes. Si les valeurs utilisées par le système d'exploitation sont affectées, les utilisateurs victimes ne pourront pas accéder à certains services et peuvent rencontrer de graves problèmes de performances.. Les modifications apportées aux chaînes utilisées par des applications tierces peuvent entraîner des erreurs inattendues.
- Suppression des données sensibles - Le moteur peut être programmé pour localiser et supprimer les fichiers sensibles qui peuvent sérieusement perturber la procédure de récupération habituelle. Cela se fait en ciblant les points de restauration du système, sauvegardes, Clichés instantanés de volume et etc. Dans ce cas, les victimes devront associer un utilitaire anti-spyware de qualité professionnelle et un programme de récupération de données..
- Livraison des charges utiles supplémentaires - Le cheval de Troie Revenge peut être invité à insérer d'autres menaces malveillantes sur les machines compromises.
Les campagnes de chevaux de Troie Future Revenge peuvent être invitées à effectuer d'autres actions telles que configurées par les pirates.

Supprimer Revenge Trojan
Si votre ordinateur a été infecté par le La revanche de Troie, vous devriez avoir un peu d'expérience dans l'élimination des logiciels malveillants. Vous devriez vous débarrasser de ce cheval de Troie le plus rapidement possible avant qu'il puisse avoir la chance de se propager plus loin et infecter d'autres ordinateurs. Vous devez supprimer le cheval de Troie et suivez les instructions étape par étape ci-dessous.
Note! Votre système informatique peut être affecté par La revanche de Troie et d'autres menaces.
Analysez votre PC avec SpyHunter
SpyHunter est un puissant outil de suppression des logiciels malveillants conçus pour aider les utilisateurs avec le système analyse approfondie de la sécurité, détection et élimination des La revanche de Troie.
Gardez à l'esprit, que le scanner SpyHunter est seulement pour la détection des logiciels malveillants. Si SpyHunter détecte les logiciels malveillants sur votre PC, vous devrez acheter outil de suppression des logiciels malveillants SpyHunter pour supprimer les menaces de logiciels malveillants. Lis notre SpyHunter 5 examen. Cliquez sur les liens correspondants pour vérifier SpyHunter de CLUF, politique de confidentialité et Critères d'évaluation des menaces.
Pour supprimer Revenge Trojan Suivez ces étapes:
Utilisez SpyHunter pour rechercher les programmes malveillants et indésirables
Preparation before removing Revenge Trojan.
Avant de commencer le processus de suppression réelle, nous vous recommandons d'effectuer les étapes de préparation suivantes.
- Assurez-vous que vous avez ces instructions toujours ouvert et devant vos yeux.
- Faites une sauvegarde de tous vos fichiers, même si elles pourraient être endommagées. Vous devez sauvegarder vos données avec une solution de sauvegarde en nuage et assurer vos fichiers contre tout type de perte, même des menaces les plus graves.
- Soyez patient car cela pourrait prendre un certain temps.
- Rechercher les logiciels malveillants
- Réparer les registres
- Supprimer les fichiers de virus
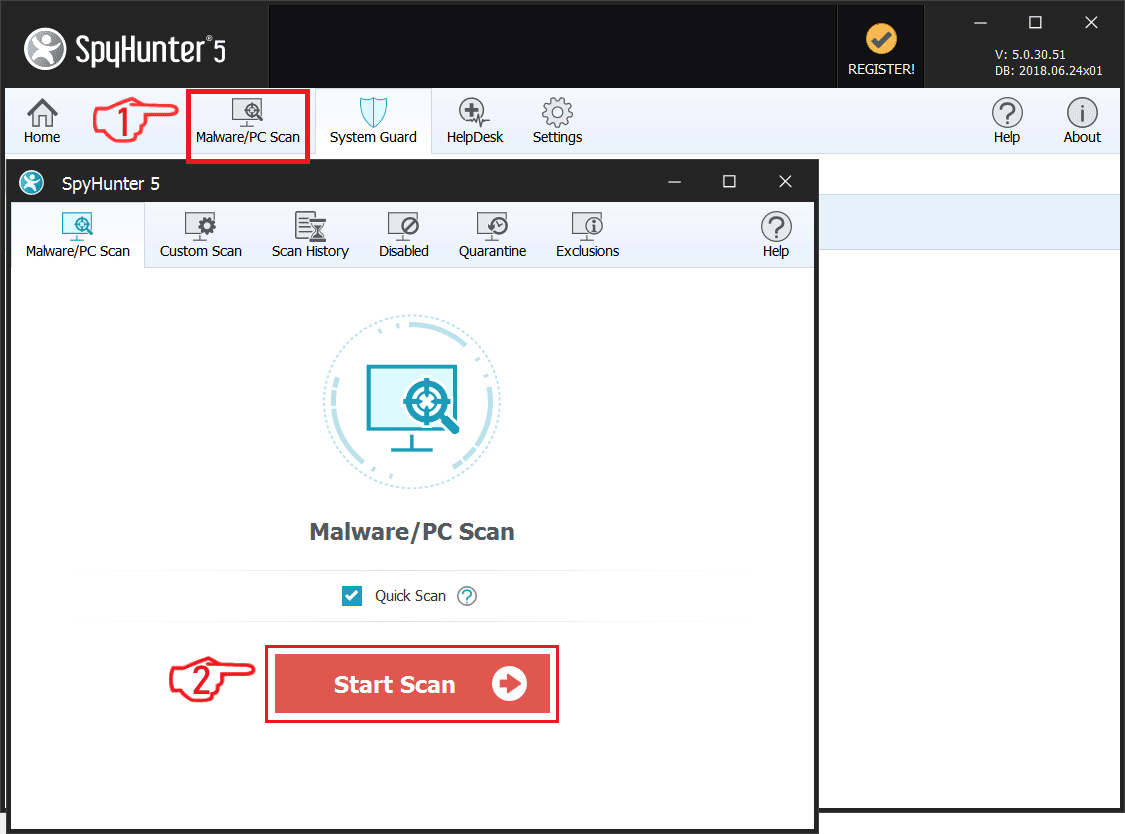
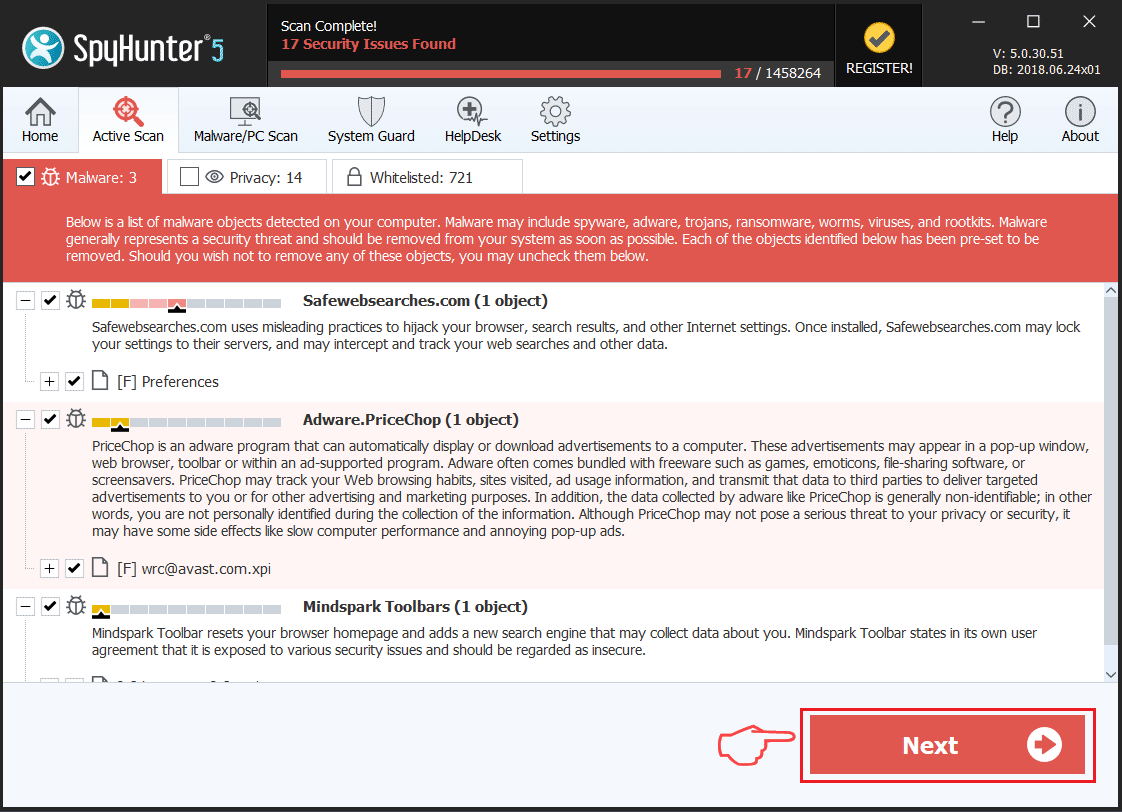
Étape 1: Rechercher un cheval de Troie Revenge avec SpyHunter Anti-Malware Tool



Étape 2: Nettoyer les registres, créé par Revenge Trojan sur votre ordinateur.
Les registres généralement ciblés des machines Windows sont les suivantes:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Vous pouvez y accéder en ouvrant l'éditeur de Registre Windows et la suppression de toutes les valeurs, créé par Revenge Trojan là-bas. Cela peut se produire en suivant les étapes ci-dessous:


 Pointe: Pour trouver une valeur créée virus, vous pouvez faire un clic droit dessus et cliquez "Modifier" pour voir quel fichier il est configuré pour exécuter. Si cela est l'emplacement du fichier de virus, supprimer la valeur.
Pointe: Pour trouver une valeur créée virus, vous pouvez faire un clic droit dessus et cliquez "Modifier" pour voir quel fichier il est configuré pour exécuter. Si cela est l'emplacement du fichier de virus, supprimer la valeur.Étape 3: Find virus files created by Revenge Trojan on your PC.
1.Pour Windows 8, 8.1 et 10.
Pour les plus récents systèmes d'exploitation Windows
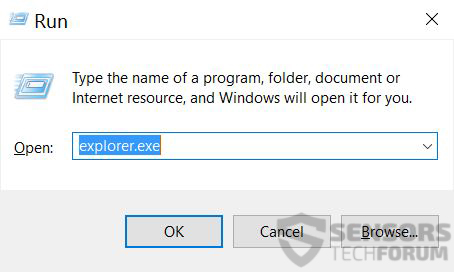
1: Sur votre clavier, pressez la + R et écrire explorer.exe dans le Courir zone de texte et puis cliquez sur le D'accord bouton.

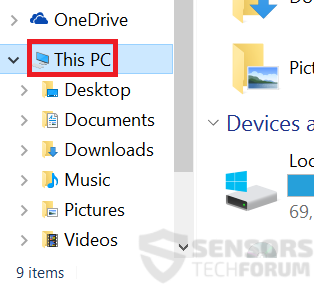
2: Cliquer sur votre PC dans la barre d'accès rapide. Cela est généralement une icône avec un moniteur et son nom est soit "Mon ordinateur", "Mon PC" ou "Ce PC" ou ce que vous avez nommé il.

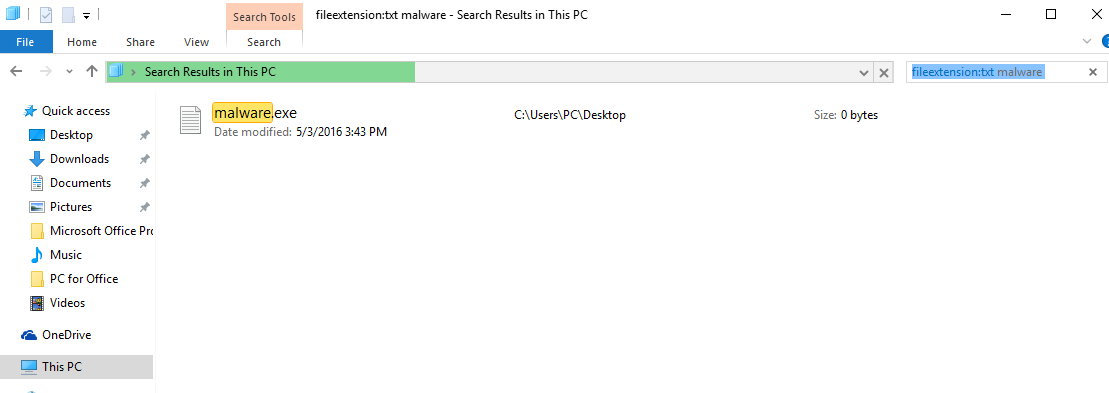
3: Accédez au champ de recherche en haut à droite de l'écran de votre PC et tapez "extension de fichier:" et après quoi tapez l'extension de fichier. Si vous êtes à la recherche pour les exécutables malveillants, Un exemple peut être "extension de fichier:exe". Après avoir fait cela, laisser un espace et tapez le nom de fichier que vous croyez que le malware a créé. Voici comment cela peut apparaître si votre fichier a été trouvé:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.Pour Windows XP, Vue, et 7.
Pour plus anciens systèmes d'exploitation Windows
Dans les anciens systèmes d'exploitation Windows, l'approche conventionnelle devrait être la plus efficace:
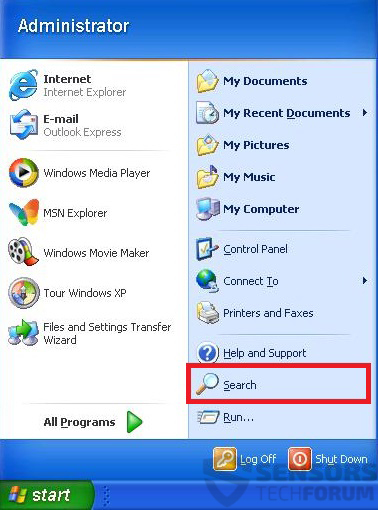
1: Cliquez sur le Le menu Démarrer icône (habituellement sur votre inférieur gauche) puis choisissez le Recherche préférence.

2: Après la fenêtre de recherche apparaît, choisir Options avancées de la boîte assistant de recherche. Une autre façon est en cliquant sur Tous les fichiers et dossiers.

3: Après ce type le nom du fichier que vous recherchez et cliquez sur le bouton Rechercher. Cela peut prendre un certain temps, après quoi les résultats apparaîtront. Si vous avez trouvé le fichier malveillant, vous pouvez copier ou ouvrir son emplacement par clic-droit dessus.
Maintenant, vous devriez être en mesure de découvrir tous les fichiers sur Windows aussi longtemps qu'il est sur votre disque dur et ne soit pas cachée par l'intermédiaire d'un logiciel spécial.
Revenge Trojan FAQ
What Does Revenge Trojan Trojan Do?
The Revenge Trojan Troyen est un programme informatique malveillant conçu pour perturber, dommage, ou obtenir un accès non autorisé à un système informatique. Il peut être utilisé pour voler des données sensibles, prendre le contrôle d'un système, ou lancer d'autres activités malveillantes.
Les chevaux de Troie peuvent-ils voler des mots de passe?
Oui, Les chevaux de Troie, like Revenge Trojan, peut voler des mots de passe. Ces programmes malveillants are designed to gain access to a user's computer, espionner les victimes et voler des informations sensibles telles que des coordonnées bancaires et des mots de passe.
Can Revenge Trojan Trojan Hide Itself?
Oui, ça peut. Un cheval de Troie peut utiliser diverses techniques pour se masquer, y compris les rootkits, chiffrement, et obfuscation, se cacher des scanners de sécurité et échapper à la détection.
Un cheval de Troie peut-il être supprimé par réinitialisation d'usine?
Oui, un cheval de Troie peut être supprimé en réinitialisant votre appareil aux paramètres d'usine. C'est parce qu'il restaurera l'appareil à son état d'origine, éliminant tout logiciel malveillant qui aurait pu être installé. Gardez à l’esprit qu’il existe des chevaux de Troie plus sophistiqués qui laissent des portes dérobées et réinfectent même après une réinitialisation d’usine.
Can Revenge Trojan Trojan Infect WiFi?
Oui, il est possible qu'un cheval de Troie infecte les réseaux WiFi. Lorsqu'un utilisateur se connecte au réseau infecté, le cheval de Troie peut se propager à d'autres appareils connectés et accéder à des informations sensibles sur le réseau.
Les chevaux de Troie peuvent-ils être supprimés?
Oui, Les chevaux de Troie peuvent être supprimés. Cela se fait généralement en exécutant un puissant programme antivirus ou anti-malware conçu pour détecter et supprimer les fichiers malveillants.. Dans certains cas,, la suppression manuelle du cheval de Troie peut également être nécessaire.
Les chevaux de Troie peuvent-ils voler des fichiers?
Oui, Les chevaux de Troie peuvent voler des fichiers s'ils sont installés sur un ordinateur. Cela se fait en permettant au auteur de logiciels malveillants ou utilisateur pour accéder à l'ordinateur et ensuite voler les fichiers qui y sont stockés.
Quel anti-malware peut supprimer les chevaux de Troie?
Les programmes anti-malware tels que SpyHunter sont capables de rechercher et de supprimer les chevaux de Troie de votre ordinateur. Il est important de maintenir votre anti-malware à jour et d'analyser régulièrement votre système à la recherche de tout logiciel malveillant..
Les chevaux de Troie peuvent-ils infecter l'USB?
Oui, Les chevaux de Troie peuvent infecter USB dispositifs. Chevaux de Troie USB se propagent généralement par le biais de fichiers malveillants téléchargés sur Internet ou partagés par e-mail, allowing the hacker to gain access to a user's confidential data.
About the Revenge Trojan Research
Le contenu que nous publions sur SensorsTechForum.com, this Revenge Trojan how-to removal guide included, est le résultat de recherches approfondies, le travail acharné et le dévouement de notre équipe pour vous aider à éliminer le problème spécifique du cheval de Troie.
How did we conduct the research on Revenge Trojan?
Veuillez noter que notre recherche est basée sur une enquête indépendante. Nous sommes en contact avec des chercheurs indépendants en sécurité, grâce auquel nous recevons des mises à jour quotidiennes sur les dernières définitions de logiciels malveillants, y compris les différents types de chevaux de Troie (détourné, downloader, infostealer, rançon, etc)
En outre, the research behind the Revenge Trojan threat is backed with VirusTotal.
Pour mieux comprendre la menace posée par les chevaux de Troie, veuillez vous référer aux articles suivants qui fournissent des détails bien informés.


 1. Pour Windows XP, Vista et 7.
1. Pour Windows XP, Vista et 7. 2. Pour Windows 8, 8.1 et 10.
2. Pour Windows 8, 8.1 et 10. Correction des entrées de registre créées par des logiciels malveillants et potentiellement indésirables sur votre PC.
Correction des entrées de registre créées par des logiciels malveillants et potentiellement indésirables sur votre PC.
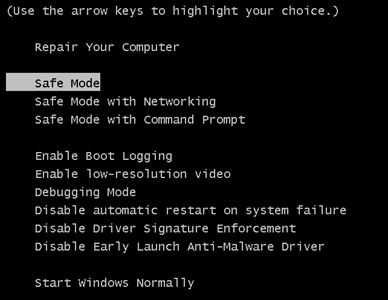
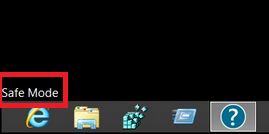
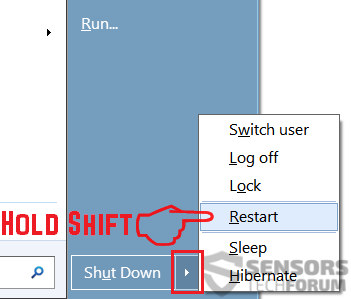
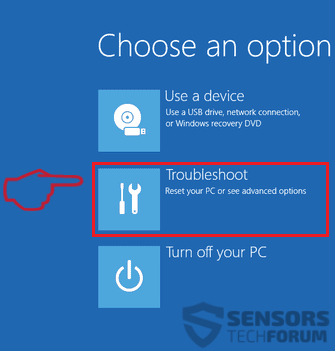
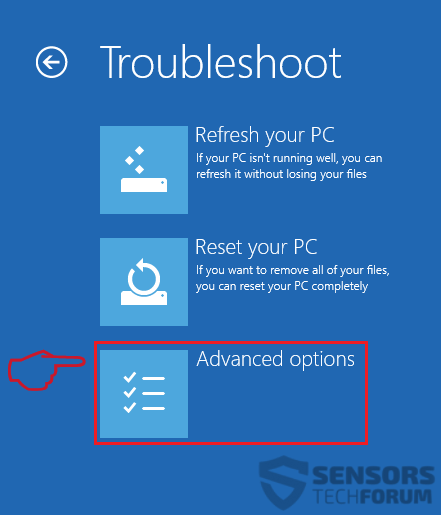
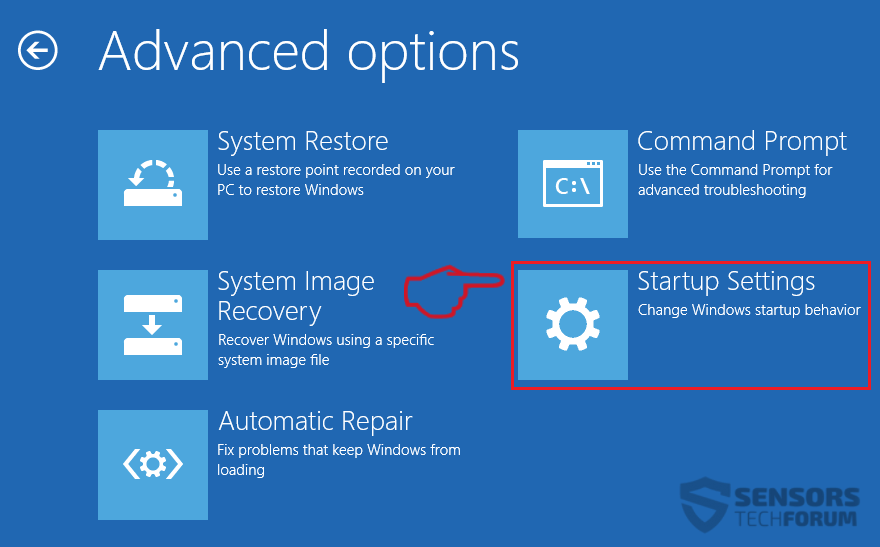
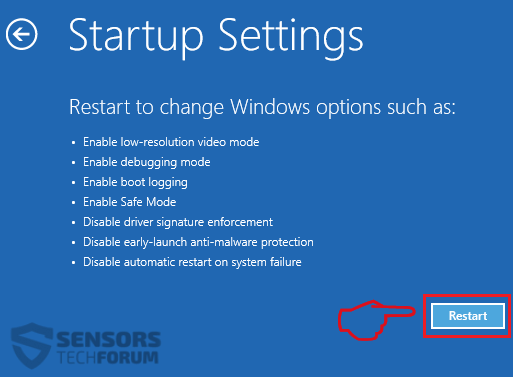
 1. Installez SpyHunter pour rechercher le cheval de Troie Revenge et supprimez-les.
1. Installez SpyHunter pour rechercher le cheval de Troie Revenge et supprimez-les.