 Denne artikel er blevet oprettet for at hjælpe dig med at forklare hvad er det Vega Infostealer malware og hvordan du fjerner denne trussel helt fra din computer.
Denne artikel er blevet oprettet for at hjælpe dig med at forklare hvad er det Vega Infostealer malware og hvordan du fjerner denne trussel helt fra din computer.
Den Vega Stealer malware er den type virus, hvis primære formål er at sno ind på din computer, mens de resterende uopdaget og stjæle vigtige informationer fra det. Den Vega Info stjæler kan også udføre andre spyware og ondsindede aktiviteter og endda gå så langt som til at downloade malware direkte på din computer. Hvis du ser nogen tegn på det Vega Stealer bosiddende i din computer, anbefaler vi dig at læse denne artikel for at lære at tage de nødvendige skridt til at fjerne denne malware fra din computer.

Trussel Summary
| Navn | Vega Infostealer |
| Type | Trojan Horse |
| Kort beskrivelse | Har til formål at stjæle oplysninger stjæle malware og derefter bruge den til at indsamle data fra computeren og sende den til cyber-kriminelle. |
| Symptomer | Din browser kan begynde at udføre forskellige forskellige typer af . |
| Distributionsmetode | Medfølgende downloads. Websider, der kan annoncere det. |
| Værktøj Detection |
Se, om dit system er blevet påvirket af malware
Hent
Værktøj til fjernelse af malware
|
Brugererfaring | Tilmeld dig vores forum at diskutere Vega Infostealer. |

Vega Stealer Malware - Hvordan virker det inficere
Den primære metode til infektion, som anvendes af Vega Info stjæler svarer til, hvad løbet 80% af malware gør for at inficere computere, og det er at sno ondsindede e-mails med vedhæftede filer indlejret i spam-mails. Disse e-mails med vedhæftede filer har den ene og eneste formål er at narre dig til at åbne e-mails med vedhæftede filer indlejret i dem. Disse e-mails med vedhæftede filer til formål at overbevise brugerne til at downloade den vedhæftede fil ved hjælp store virksomheder som påskud, for eksempel:
Den vedhæftede fil er ofte portrætteret som et vigtigt dokument, ligesom en faktura, Kvittering, online ordrebekræftelse og andre lignende sådan.
Disse typer af dokumenter som regel kan være JavaScript typer af filer, vbs scripts og eksekverbare filer, men den mest moderne måde at inficere ofre er via Microsoft Office-dokumenter, der kan indeholde skadelige makroer indlejret i dem:
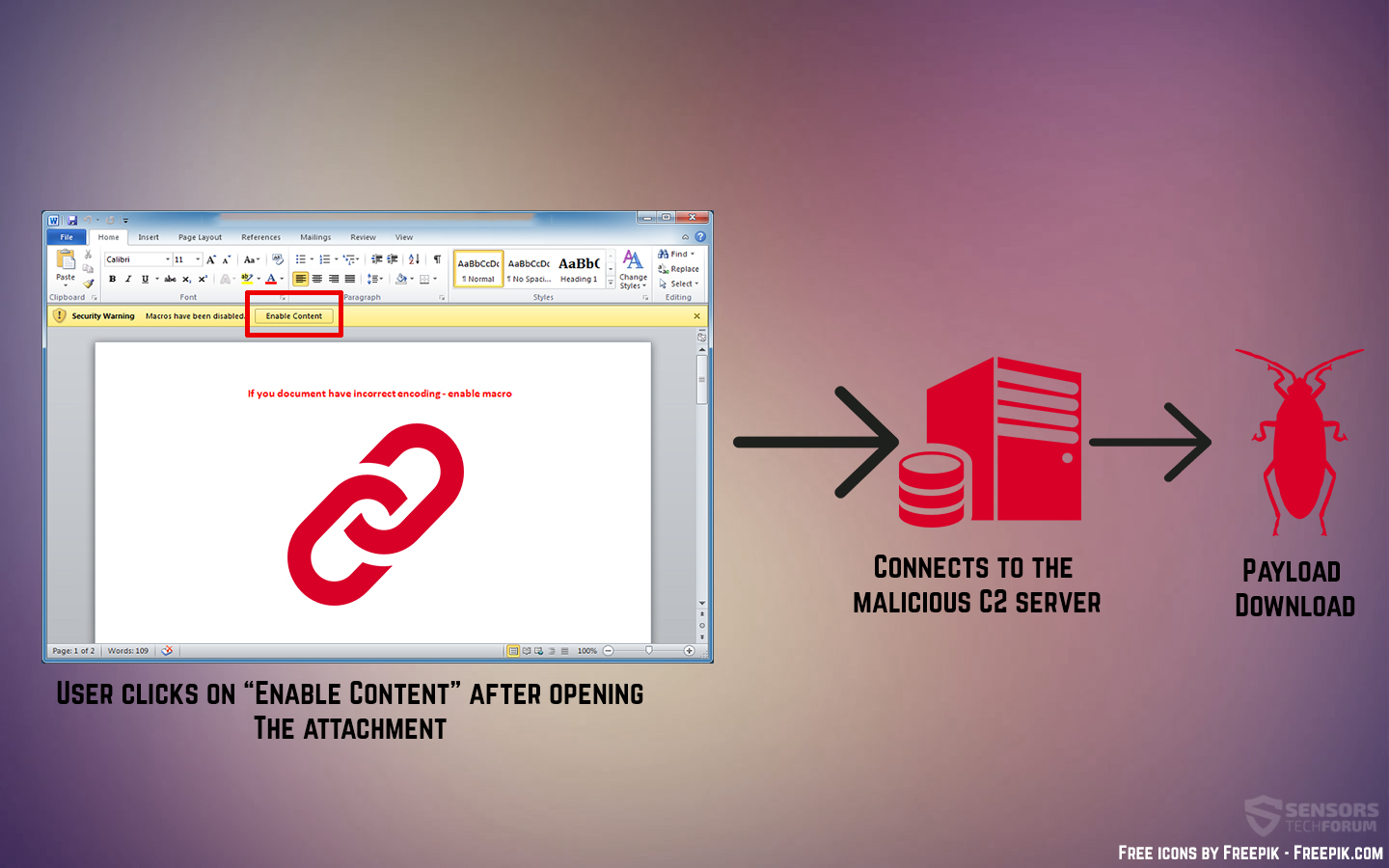

Vega Stealer – Analyse
Når Vega Stealer er blevet installeret på din computer, malwaren kan begynde at udføre en række opgaver og aktiviteter på din computer. Disse opgaver har den ene og eneste formål at først tjekke din computer for forskellige detaljer:
- Hvis det allerede er blevet inficeret med denne virus.
- Det er systemoplysninger.
- Sikkerhed software installeret.
Derefter, hvis alt tjekker, Vega Stealer dråber flere forskellige filer på computeren af ofrene. Disse filer kan være midlertidig eller eksekverbar form af moduler, og de kan køre med eskalerede rettigheder på din computer. Filerne kan opholde sig i følgende Windows mapper:
- %AppData%
- %Temp%
- %Lokal%
- %LocalLow%
- %Roaming%
Når ondsindede filer er downloadet på brugerens computer, de kan begynde at ændre forskellige systemindstillinger, såsom:
- Opret planlagte opgaver til at køre automatisk.
- Rediger Run og RunOnce Windows registreringsdatabasen sub-nøgler.
- Gør det, som om de ondsindede filer er løb som legitime Windows processer, ligesom injicere skadelig kode i svchost.exe for at skjule malware fra Antivirus og anden beskyttelse software.
Derefter, malwaren kan udløse det er funktioner, der er en hel del, det vigtigste er at stjæle forskellige typer af information objekter fra din computer, lignende:
- Adgangskoder.
- finansielle oplysninger.
- Stjæl filer ved at kopiere dem og sende dem til tredjeparts værter.
- Tag screenshots.
- Brug keyloggers til at indsamle oplysninger om, hvad du skriver.
- Aktiver dit kamera.
Ud over dette, Vega Info stjæler kan også udføre andre aktiviteter i computeren af brugeren, såsom få brugerne til at udføre flere andre end at stjæle filer forskellige aktiviteter, svarer til, hvad de fleste malware plejer hele tiden:
- opdatere sig selv.
- Hent andre vira på computeren.
- Installer adware og spyware moduler.
- Opret kopier af sig selv, hvis du fjerner det vigtigste fil.

Fjern Vega Stealer fra computeren fuldstændigt
Hvis du vil fjerne denne information stjæler fra din PC, Vi anbefaler, at du følger fjernelse instruktioner nedenunder denne artikel. De er blevet oprettet for at hjælpe dig med at slette denne malware enten manuelt eller automatisk fra din computer. Hvis manuel fjernelse ikke gøre arbejdet for dig, Vi anbefaler, at du fjerner denne malware automatisk, helst ved at downloade og køre en scanning via en avanceret anti-malware-software, som de fleste eksperter anbefaler. Dette skyldes, at sådan software effektivt vil sørge for, at alle de skadelige software er fjernet fra din pc, og at den forbliver beskyttet mod fremtidige infektioner samt.
Preparation before removing Vega Infostealer.
, Før den egentlige fjernelse proces, Vi anbefaler, at du gør følgende forberedelse trin.
- Sørg for at have disse instruktioner altid åben og foran dine øjne.
- Gør en sikkerhedskopi af alle dine filer, selv om de kunne blive beskadiget. Du bør sikkerhedskopiere dine data med en sky backup-løsning og forsikre dine filer mod enhver form for tab, selv fra de mest alvorlige trusler.
- Vær tålmodig, da det kan tage et stykke tid.
- Scan for malware
- Rette registre
- Fjern virusfiler
Trin 1: Scan efter Vega Infostealer med SpyHunter Anti-Malware-værktøj



Trin 2: Rens eventuelle registre, oprettet af Vega Infostealer på din computer.
De normalt målrettede registre af Windows-maskiner er følgende:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Du kan få adgang til dem ved at åbne Windows Registry Editor og slette eventuelle værdier, oprettet af Vega Infostealer der. Dette kan ske ved at følge trinene nedenunder:


 Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.
Tip: For at finde en virus-skabt værdi, du kan højreklikke på det og klikke "Modificere" at se, hvilken fil det er indstillet til at køre. Hvis dette er virus fil placering, fjerne værdien.Trin 3: Find virus files created by Vega Infostealer on your PC.
1.For Windows 8, 8.1 og 10.
For Nyere Windows-operativsystemer
1: På dit tastatur tryk + R og skrive explorer.exe i Løbe tekstboks og derefter klikke på Ok knap.

2: Klik på din pc fra hurtig adgang bar. Dette er normalt et ikon med en skærm og dets navn er enten "Min computer", "Min PC" eller "Denne PC" eller hvad du har navngivet det.

3: Naviger til søgefeltet øverst til højre på din pc's skærm og type "fileextension:" og hvorefter skrive filtypen. Hvis du er på udkig efter ondsindede eksekverbare, et eksempel kan være "fileextension:exe". Efter at gøre det, efterlade et mellemrum og skriv filnavnet du mener malware har skabt. Her er, hvordan det kan se ud, hvis der er fundet din fil:

NB. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.I Windows XP, Vista, og 7.
For ældre Windows-operativsystemer
I ældre Windows OS bør den konventionelle tilgang være den effektive:
1: Klik på Start Menu ikon (normalt på din nederste venstre) og vælg derefter Søg præference.

2: Efter søgningen vises, vælge Flere avancerede indstillinger fra søgningen assistent boksen. En anden måde er ved at klikke på Alle filer og mapper.

3: Efter denne type navnet på den fil, du søger, og klik på knappen Søg. Dette kan tage noget tid, hvorefter resultater vises. Hvis du har fundet den skadelig fil, du må kopiere eller åbne sin placering ved højreklikke på det.
Nu skulle du være i stand til at opdage en fil på Windows, så længe det er på din harddisk og ikke skjult via speciel software.
Vega Infostealer FAQ
What Does Vega Infostealer Trojan Do?
The Vega Infostealer Trojan er et ondsindet computerprogram designet til at forstyrre, skade, eller få uautoriseret adgang til et computersystem.
Det kan bruges til at stjæle følsomme data, få kontrol over et system, eller starte andre ondsindede aktiviteter.
Kan trojanske heste stjæle adgangskoder?
Ja, Trojans, like Vega Infostealer, kan stjæle adgangskoder. Disse ondsindede programmer are designed to gain access to a user's computer, spionere på ofrene og stjæle følsomme oplysninger såsom bankoplysninger og adgangskoder.
Can Vega Infostealer Trojan Hide Itself?
Ja, det kan. En trojaner kan bruge forskellige teknikker til at maskere sig selv, inklusive rootkits, kryptering, og formørkelse, at gemme sig fra sikkerhedsscannere og undgå registrering.
Kan en trojaner fjernes ved fabriksnulstilling?
Ja, en trojansk hest kan fjernes ved at nulstille din enhed til fabriksindstillinger. Dette skyldes, at det vil gendanne enheden til sin oprindelige tilstand, eliminering af skadelig software, der måtte være blevet installeret. Husk på, at der er mere sofistikerede trojanske heste, der efterlader bagdøre og geninficerer selv efter fabriksnulstilling.
Can Vega Infostealer Trojan Infect WiFi?
Ja, det er muligt for en trojaner at inficere WiFi-netværk. Når en bruger opretter forbindelse til det inficerede netværk, trojaneren kan spredes til andre tilsluttede enheder og kan få adgang til følsomme oplysninger på netværket.
Kan trojanske heste slettes?
Ja, Trojanske heste kan slettes. Dette gøres typisk ved at køre et kraftfuldt anti-virus eller anti-malware program, der er designet til at opdage og fjerne ondsindede filer. I nogle tilfælde, manuel sletning af trojaneren kan også være nødvendig.
Kan trojanske heste stjæle filer?
Ja, Trojanske heste kan stjæle filer, hvis de er installeret på en computer. Dette gøres ved at tillade malware forfatter eller bruger for at få adgang til computeren og derefter stjæle filerne, der er gemt på den.
Hvilken anti-malware kan fjerne trojanske heste?
Anti-malware programmer som f.eks SpyHunter er i stand til at scanne efter og fjerne trojanske heste fra din computer. Det er vigtigt at holde din anti-malware opdateret og regelmæssigt scanne dit system for skadelig software.
Kan trojanske heste inficere USB?
Ja, Trojanske heste kan inficere USB enheder. USB-trojanske heste spredes typisk gennem ondsindede filer downloadet fra internettet eller delt via e-mail, allowing the hacker to gain access to a user's confidential data.
About the Vega Infostealer Research
Indholdet udgiver vi på SensorsTechForum.com, this Vega Infostealer how-to removal guide included, er resultatet af omfattende forskning, hårdt arbejde og vores teams hengivenhed til at hjælpe dig med at fjerne det specifikke trojanske problem.
How did we conduct the research on Vega Infostealer?
Bemærk venligst, at vores forskning er baseret på en uafhængig undersøgelse. Vi er i kontakt med uafhængige sikkerhedsforskere, takket være, at vi modtager daglige opdateringer om de seneste malware-definitioner, herunder de forskellige typer trojanske heste (bagdør, Downloader, infostealer, løsesum, etc.)
Endvidere, the research behind the Vega Infostealer threat is backed with VirusTotal.
For bedre at forstå truslen fra trojanske heste, Se venligst følgende artikler, som giver kyndige detaljer.













