Este artigo é sobre uma ameaça ransomware recente que tem milhares de sucesso da Hewlett-Packard Empresa Integrated Lights-Out 4 as interfaces ou HPE iLO 4 abreviado. Estas interfaces fornecem acesso aos servidores HP Enterprise e seu controle remoto. A ameaça do ransomware é criptografar os discos rígidos dos servidores e, em seguida, exigir Bitcoins como resgate para restaurar os arquivos dentro das unidades. Um pesquisador de segurança que usa o apelido do Twitter @M_Shahpasandi foi o primeiro a fazer a descoberta do ataque.
O que é Hewlett-Packard Enterprise iLO e interface relacionada?
iLO é um processador de gerenciamento de servidor remoto integrado nas placas de sistema dos servidores Hewlett-Packard Enterprise ProLiant e módulos de computação Synergy. O processador de gerenciamento permite o monitoramento e controle de servidores de locais remotos. O gerenciamento HPE iLO é uma ferramenta poderosa que oferece várias maneiras de configurar, atualizar, monitor, e consertar servidores remotamente.
A interface da web do iLO agrupa tarefas semelhantes para facilitar a navegação e o fluxo de trabalho. A interface é organizada em uma árvore de navegação. Os ramos de nível superior são Informações, Federação iLO, Console remoto, Mídia virtual, Gerenciamento de energia, Rede, Suporte remoto, e administração. Em poucas palavras, essas interfaces fornecem acesso administrativo a todos os servidores que estão sob o comando da interface.
Mais informações sobre os ataques direcionados ao HPE iLO 4
Parece que, por enquanto, as interfaces HPE iLO que foram atingidas pela ameaça de ransomware são acessível publicamente. Sobre 5,000 iLO-4 foi encontrado para ser exposto publicamente como Estatísticas Shodan mostrar.
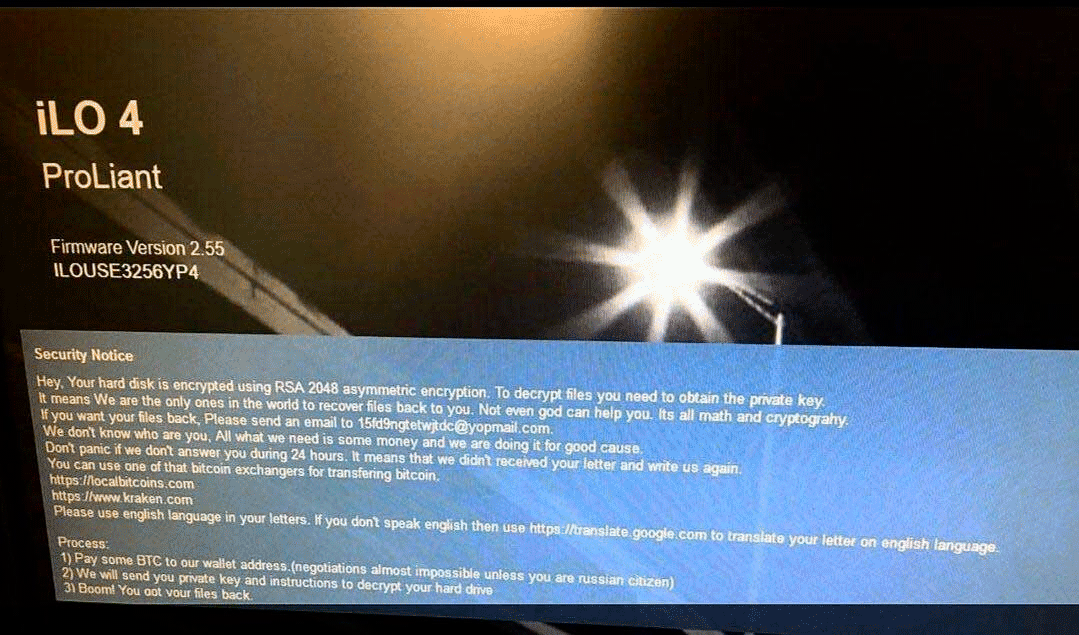
Se a interface do HPE iLO for atingida pelo ransomware, o banner de segurança será alterado. O banner de segurança de login alterado adicionado por invasores afirma o seguinte:
Aviso de Segurança
Ei. Seu disco rígido está criptografado usando RSA 2048 criptografia assimétrica. Para descriptografar arquivos que você precisa para obter a chave privada.
Isso significa que somos os únicos no mundo a recuperar os arquivos para você. Nem mesmo Deus pode te ajudar. É tudo matemática e criptografia .
Se você quiser seus arquivos de volta, Envie um e-mail para 15fd9ngtetwjtdc@yopmail.com.
Nós não sabemos quem é você, Tudo o que precisamos é de algum dinheiro e estamos fazendo isso por uma boa causa.
Não entre em pânico se não respondermos durante 24 horas. Isso significa que não recebemos sua carta e nos escrevemos novamente.
Você pode usar esses trocadores de bitcoin para transferir bitcoin.
https://localbitcoins.com
https://www.kraken.com
Por favor, use o idioma inglês em suas cartas. Se você não fala inglês, use https://translate.google.com para traduzir sua carta no idioma inglês.Processo:
1) Pague um pouco de BTC para o endereço de nossa carteira.(negociações quase impossíveis a menos que você seja um cidadão russo)
2) Enviaremos a você uma chave privada e instruções para descriptografar seu disco rígido
3) estrondo! Você recuperou seus arquivos.
Aqui está uma imagem que descreve o banner de segurança compartilhado por @M_Shahpasandi no Twitter:

As vítimas relatam que o ataque realmente criptografa ou limpa os discos rígidos que foram visados. A ordem cronológica do ataque é a seguinte:
- O acesso é obtido à interface Integrated Lights-Out
- O banner de login de segurança foi habilitado
- Um ISO remoto foi montado
- Scripts ou programas são executados a partir do ISO
- O servidor é reiniciado
Especula-se que os invasores costumavam obter acesso executando o CVE-2013-4786 vulnerabilidade, que permite um ataque de força bruta offline para um hash de senha de um usuário iLO válido ou por meio do CVE-2017-12542 vulnerabilidade, que permite um desvio de autenticação, resolvido com a atualização para a versão iLO 2.53.
Muitos pesquisadores de segurança aconselham que HPE iLO 4 ou qualquer outra interface de controle remoto semelhante para servidores nunca deve ser conectada à Internet pública. VPNs seguras devem ser usados para acesso e você deve ter o firmware mais recente instalado, que está disponível em todos os momentos.

