Outra campanha de phishing foi descoberta por pesquisadores da Heimdal, aproveitando as vantagens do Delta Air e baixando o malware Hancitor. A potencial vítima recebe um e-mail disfarçado como um e-mail de confirmação de pagamento da empresa.
Seu pedido com a Delta Air Lines foi confirmado como esquema de phishing
Conforme explicado pelos pesquisadores, usar uma companhia aérea para mascarar intenções maliciosas não é aleatório, já que muitas companhias aéreas oferecem taxas de desconto para voos de verão nesta época do ano. Se você recebeu um e-mail com o assunto “Seu pedido [números] com a Delta Air Lines foi confirmado!”Sem ter feito reserva, prossiga com cuidado!
Esta é a aparência do e-mail de spam contendo malware:
Como acontece com todo e-mail de phishing, um olhar atento detectaria imediatamente várias imprecisões apontando para a origem não autêntica da mensagem:
- Em primeiro lugar, o endereço de e-mail não é legítimo e não pertence à referida empresa. Se fosse o e-mail da empresa, deveria ter terminado com “@ delta.com” e não “@deltaa”.
- Nenhuma informação específica sobre o voo é fornecida. Se este foi realmente um e-mail de confirmação, deveria conter detalhes sobre o voo reservado, e usa a falta de informação para convencer o usuário a clicar no link fornecido.
- O formato visual do e-mail não corresponde aos e-mails usuais da Delta. Se você é um cliente da empresa, você definitivamente deve achar esta imprecisão suspeita.
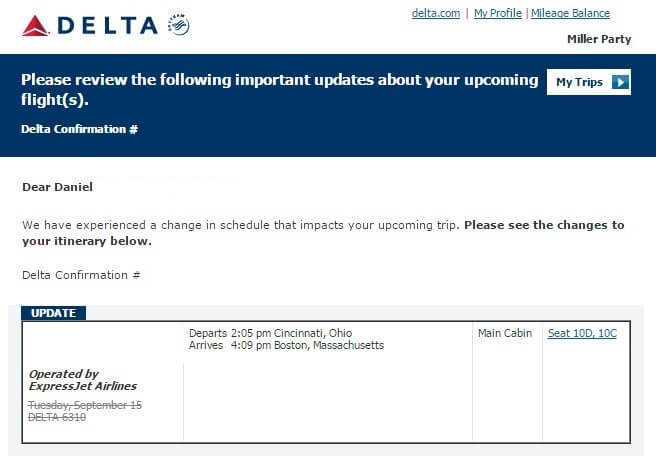
Para comparar os dois e-mails e ver as diferenças por si mesmo, aqui está a aparência de um e-mail legítimo enviado pela empresa:
Mais sobre a campanha de phishing da Delta Air
Malware Hancitor e Zloader baixados em sistemas comprometidos
O e-mail é obviamente criado para assustar o usuário e faze-lo acreditar que alguém usou suas credenciais e identidade para comprar uma passagem aérea. O usuário normalmente entraria em pânico e interagiria com os links fornecidos, o que é na verdade uma ideia muito ruim. Os links redirecionariam o usuário para sites infectados que hospedam documentos do Microsoft Word contendo o malware Hancitor. Hancitor é uma parte versátil de código malicioso, frequentemente empregado em ataques de phishing.
O malware é normalmente usado como uma ponte para permitir ataques futuros ao sistema comprometido. Isso significa que mais malware está prestes a ser baixado no computador.
relacionado: Infraestrutura de nuvem da Microsoft e do Google abusada por hackers em e-mails de phishing
Assim que o usuário baixar o Hancitor por meio de um documento malicioso do Word, o malware será ativado. Como um resultado, processos legítimos do sistema serão infectados por meio de um código PowerShell. Então, o sistema infectado será conectado a um ou mais servidores de comando e controle.
Finalmente, malware adicional da família de malware Pony será baixado.
Como escrevemos anteriormente, Pony foi introduzido pela primeira vez no mundo cibernético anos atrás. O infame ladrão de informações foi usado para espalhar os cavalos de Troia Zeus e Necurs, bem como ransomware Cryptolocker e Cribit.
Mais especificamente, este ataque de phishing usa Zloader, que é um malware baseado em Pony. Zloader é um malware bancário direcionado às contas bancárias das vítimas.