Como todos nós sabemos e estão cientes, a maioria dos ataques phishing hackers estão sendo executadas por máquinas de bots automatizados em vez de seres humanos que vivem. A estatísticas em um estudo recente sobre o assunto Google lançou mostra que o chamado ‘hijacking o manual‘ pode ser mais bem sucedido para os hackers do que o automatizado embora.
Os resultados detalhados da pesquisa sobre esses ataques manuais podem ser encontrados em O relatório do Google e mostrar que não importa é preciso muito mais esforços para o perfil das vítimas e executar para hackers, nove de um milhão de ataques de phishing por dia são manuais.
‘Sequestro manual’ um emprego comum?
Parece que esses ataques manuais pode ser apenas um trabalho cada-dia normal para algumas pessoas. pesquisadores do Google descobriu que os ataques começar aproximadamente no mesmo tempo durante o dia, entalhe até uma queda em torno de meio-dia e fim aproximadamente na mesma hora do dia. Eles não são muito ativos durante a semana, bem.
Aqui está o que é observado pelos pesquisadores:
- Os indivíduos parecia trabalho de acordo com uma programação diária apertada. Eles começaram por volta da mesma hora todos os dias e tinha um sincronizado, pausa para o almoço de uma hora. Eles foram em grande parte inativo nos fins de semana.
- Todos os indivíduos seguido o mesmo calendário diário, definir quando para processar as listas de senha recém-reunidos, e como dividir o tempo entre fraudes em curso e novas vítimas.
- Eles estavam operando de diferentes IPs, em diferentes vítimas, e em paralelo uns com os outros, mas as ferramentas e utilitários eles utilizados foram os mesmos. Eles também compartilharam certos recursos como números de telefone.
Além disso, mesmo que tenham diferentes endereços IP (que pode ser devido a servidores proxy ou redes VPN, na verdade,) eles usam as mesmas ferramentas, até mesmo alguns recursos compartilhados, como números de telefone. Google tentou localizar os hackers por endereços IP e notei que a maioria deles parece estar localizada na China e na Malásia, mas com base no acima exposto estes resultados podem ser controversos.
Por outro lado, rastreamento dos números de telefone mostrou que dois grandes grupos poderia estar fazendo o phishing - uma na Nigéria e um na Costa do Marfim. Com base na língua mais spread para cada país, parece que o grupo Nigéria está focada em países de língua Inglês, enquanto a Costa do Marfim - sobre os de língua francesa.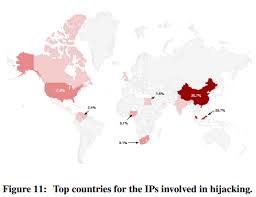
Grande desafio para os pesquisadores
Infelizmente ainda, o ‘seqüestro Manual’ é muito difícil de identificar como o volume desses ataques é muito pequena, e os criminosos variar.
‘Em nossa experiência dos maiores desafios na detecção de sequestro manual é que é extremamente baixo volume, que seqüestradores são muito versáteis, e que é difícil de encontrar o equilíbrio certo entre falsos positivos (desafiando os usuários legítimos) e falso negativo (deixando um sequestrador em) quando ele veio para’Google gravação pesquisadores.
Eles também aconselham que a forma mais eficiente de proteger os dados permanecem o processo de confirmação em 2 passos introduzida pelo Google. ‘Verificação SMS, que tem um excesso 80% taxa de sucesso, é a opção de recuperação de confiança mais por várias razões. Primeiro, os usuários tendem a manter o seu número de telefone up-to-date, que fazem números de telefone inexistentes um não-problema. em segundo lugar, ele fornece uma boa experiência do usuário. Usuários acham fácil digitar o código que recebem via SMS. Finalmente, é difícil de falsificar’, eles pensam.












