Para ninguém de surpresa, existe uma maneira relativamente fácil para os hackers invadirem milhares de casas inteligentes. Pesquisadores do Avast alertaram recentemente sobre o protocolo MQTT (Transporte de telemetria de enfileiramento de mensagens) qual, se mal configurado, poderia dar aos hackers acesso completo a uma casa inteligente. Como resultado dessa brecha de segurança, a casa pode ser manipulada de várias maneiras, incluindo seus sistemas de entretenimento e voz, vários aparelhos domésticos, e portas inteligentes.
O que é o protocolo MQTT?
É possível interconectar e controlar dispositivos domésticos inteligentes usando o Transporte de Telemetria de Enfileiramento de Mensagens (MQTT) protocolo, Avast explica acrescentando que, embora o próprio protocolo MQTT seja seguro, se implementado e configurado incorretamente, problemas graves de segurança podem aparecer. Para provar que, Os pesquisadores "deu uma olhada mais de perto e usando o mecanismo de pesquisa Shodan IoT encontrou mais de 49,000 Servidores MQTT publicamente visíveis na internet devido a um protocolo MQTT configurado incorretamente”.
Por que explorar um protocolo MQTT mal configurado é tão perigoso? basta dizer, Porque:
O protocolo é um modelo de assinante / editor. Funciona como um feed RSS: você se inscreve em um tópico, e uma vez que alguém publica algo sobre o assunto, a carga útil é entregue a todos os assinantes.
O que é mais alarmante é que este protocolo é incluído na maioria das soluções de software de hub de casa inteligente, como Home Assistant. É fácil para os usuários instalar um pacote com MQTT incluído ou instalar o protocolo separadamente ao configurar o hub de casa inteligente.
Também deve ser mencionado que a maioria dos hubs domésticos inteligentes normalmente assinam e publicam mensagens MQTT e fornecem lógica. Eles também fornecem algum tipo de painel, local ou remotamente, onde você pode controlar toda a casa ‘inteligente’, os pesquisadores acrescentaram.
Em cima disso, MQTT e Mosquitto, o software de servidor mais comum que aplica o protocolo, têm “amplas capacidades de segurança,”Que são anulados se estiverem mal configurados:
Como mencionado anteriormente, não há um problema de segurança com o protocolo MQTT nem o software de servidor mais comum que implementa este protocolo (ou corretor, como é conhecido no caso de MQTT), que é chamado de Mosquitto. De fato, MQTT e Mosquitto têm amplos recursos de segurança - por exemplo, para fornecer controle de acesso refinado por usuário e tópico. Como com muitas coisas, os problemas são criados na implementação e configuração.
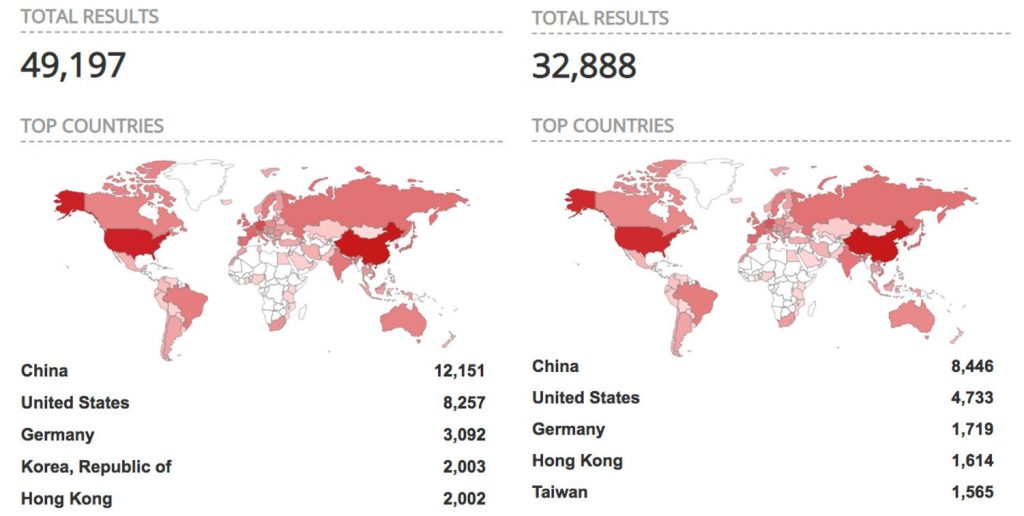
Os pesquisadores descobriram um total de 49,197 servidores MQTT configurados incorretamente via Shodan, das quais 8,257 estão nos EUA. além disso, do 32,888 Servidores MQTT sem proteção de senha implementada, 4,733 estão nos EUA, com apenas a China tendo mais servidores MQTT mal configurados e desprotegidos do que os EUA.
Conforme os usuários configuram esses sistemas para controlar remotamente sua casa inteligente, muitas vezes eles expõem não apenas o "painel" ou painel de controle do sistema, mas também o servidor MQTT, já que esses dois componentes geralmente são executados na mesma máquina ou servidor. Quando isso acontece, pode deixar os usuários expostos, Os pesquisadores concluiu.