To no one’s surprise, there is a relatively easy way for hackers to breach thousands of smart homes. Avast researchers recently warned about the MQTT protocol (Message Queuing Telemetry Transport) which, if misconfigured, could give hackers complete access to a smart home. As a result of this security loophole, the home could be manipulated in many ways including its entertaining and voice systems, various household devices, and smart doors.
What Is the MQTT Protocol?
Interconnecting and controlling smart home devices is possible using the Message Queuing Telemetry Transport (MQTT) protocol, Avast explains adding that while the MQTT protocol itself is secure, if implemented and configured incorrectly, severe security issues may show up. To prove that, the researchers “took a closer look and using the Shodan IoT search engine found more than 49,000 MQTT servers publicly visible on the internet due to a misconfigured MQTT protocol”.
Why is exploiting a misconfigured MQTT protocol so dangerous? Simply said, because:
The protocol is meant as a subscriber/publisher model. It works like an RSS feed: you subscribe to a topic, and once someone publishes something on the topic, the payload is delivered to all subscribers.
What is mostly alarming is that this protocol is included in most smart home hub software solutions, such as Home Assistant. It is easy for users to either install a package with included MQTT or install the protocol separately when setting up the smart home hub.
It should also be mentioned that most smart home hubs typically subscribe and publish MQTT messages and provide logic. They also provide some kind of dashboard, either locally or remotely, where you can control the whole ‘smart’ home, the researchers added.
On top of that, both MQTT and Mosquitto, the most common server software that applies the protocol, have “broad security capabilities,” which are nullified if they are poorly configured:
As mentioned earlier, there isn’t a security issue with the MQTT protocol nor the most common server software that implements this protocol (or broker as it is known in the case of MQTT), which is called Mosquitto. In fact, both MQTT and Mosquitto have broad security capabilities — for example, to provide fine-grained access control by user and topic. As with many things, the problems are created in the implementation and configuration.
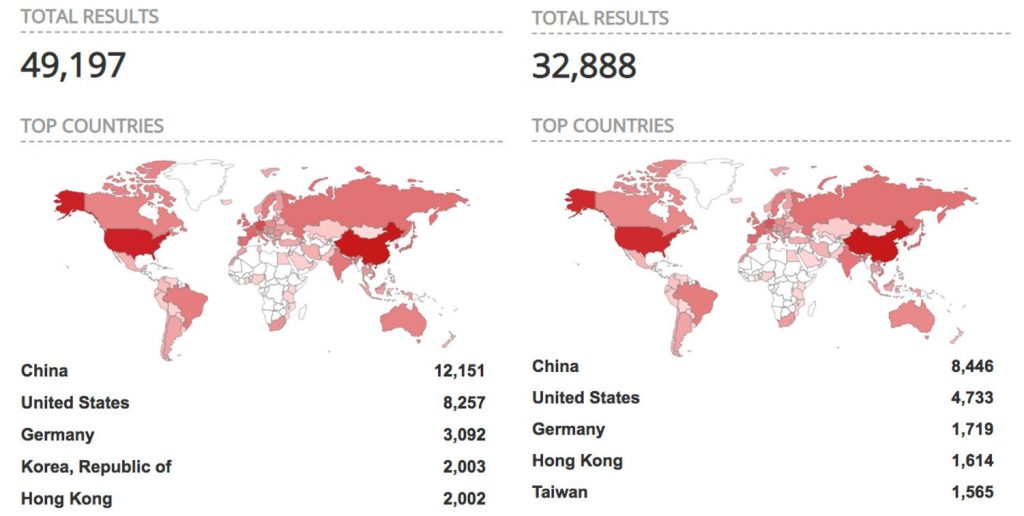
The researchers found a total of 49,197 misconfigured MQTT servers via Shodan, of which 8,257 are in the U.S. Furthermore, of the 32,888 MQTT servers with no password protection implemented, 4,733 are in the U.S., with only China having more misconfigured and unprotected MQTT servers than the U.S.
As users set up these systems to remotely control their smart home, they often expose not only the “dashboard” or control panel of the system, but also the MQTT server, as these two components usually run on the same machine or server. When this happens, it can leave users exposed, the researchers concluded.