 Durante a última semana, Os pesquisadores de segurança da Palo Alto Networks notaram que a Dridex, a versão mais recente do Trojan Cridex, um ladrão de dados também conhecido como Feodo, Bugat e Geodo foram ativados para atacar informações de segurança bancária através da incorporação de scripts automatizados com tarefas repetidas nas macros do Microsoft Office Package.
Durante a última semana, Os pesquisadores de segurança da Palo Alto Networks notaram que a Dridex, a versão mais recente do Trojan Cridex, um ladrão de dados também conhecido como Feodo, Bugat e Geodo foram ativados para atacar informações de segurança bancária através da incorporação de scripts automatizados com tarefas repetidas nas macros do Microsoft Office Package.
Segundo os pesquisadores, a campanha Dridex começou em 21 de outubro, 2014 começando a enviar mensagens alegando conter documentos financeiros eletrônicos (faturas eletrônicas, etc.) de diferentes comerciantes, incluindo Humber Merchant's Group – uma empresa que atua na área de construção.
O malware Didex é a versão mais recente do Feodo / Bugat / Cavalo de Tróia Cridex, desenvolvido em Geodo. Mantém as capacidades das suas versões anteriores para roubar informação mas estas são alteradas para os utilizadores que recebem ficheiros anexos contendo macros nas suas contas de e-mail. Uma das mudanças no vírus Dridex, notei na semana passada, está enviando documentos do Microsoft Word com macros forçando os usuários a baixar software malicioso em suas máquinas.
Depois que os usuários recebem e abrem o documento do Word infectado, as macros por trás começam a executar as tarefas incorporadas em seus scripts, tendo o mesmo objetivo – roubar certificados bancários online e informações de segurança, para que os hackers possam acessar e esvaziar as contas bancárias dos usuários.
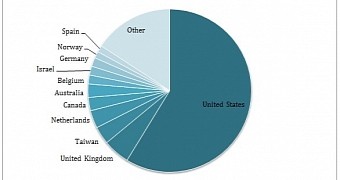
Parece que o principal objetivo do ataque são os usuários nos Estados Unidos, já que quase metade dos e-mails no extrato do pesquisador são baseados lá. Havia contas de e-mail registradas em outros países também – Austrália, Canadá, Reino Unido, Os Países Baixos, Bélgica, Alemanha, Noruega, Espanha., Israel e Taiwan.
Embora não houvesse uma declaração oficial sobre o malware Dridex da Microsoft no momento em que o artigo foi escrito, eles tomaram precauções para limitar o problema desativando macros de seus componentes do Pacote do Office. Eles podem ser ativados pelos usuários a qualquer momento, então, basicamente, uma boa proteção contra o malware é desativar as macros do seu Microsoft Word ou de qualquer outro documento do Office em que você possa ter esse tipo de execução.
O rastreador Feodo, um serviço oferecido pelo site abuse.ch para ficar de olho nos servidores de comando e controle de malware mostra que existem 93 servidores para comunicação Dridex, 12 dos quais atualmente online. Quatro deles são conhecidos por estarem localizados na Rússia.



Artigo muito útil, você tem alguma informação sobre qual AV pode detectar essa nova cepa?
Eu tentei googling para obter as informações, mas nada parece aparecer..