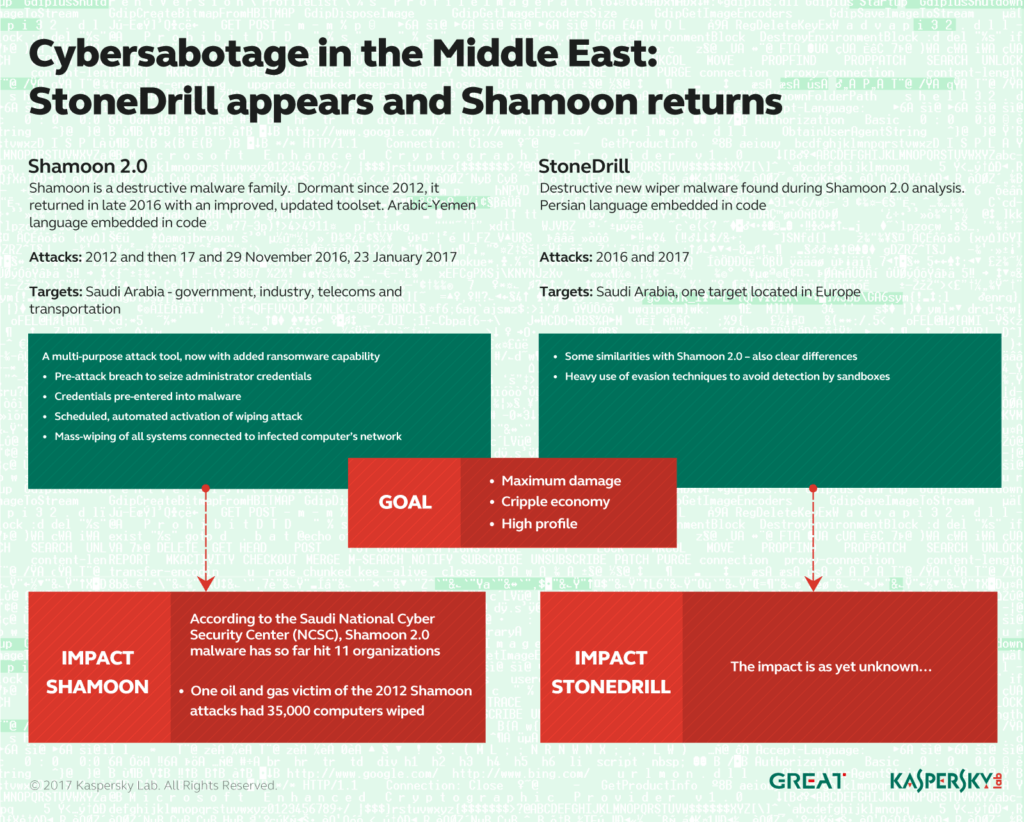
A última vez que escrevemos sobre malware de limpeza foi em dezembro, quando Shamoon voltou à cena de malware.
Shamoon, a.k.a. Disstrack foi detectado inicialmente há cerca de quatro anos em ataques contra a Saudi Oil Company Aramco. Sua intenção era limpar milhares de computadores.
Em dezembro 2016, o malware tinha como alvo outra organização saudita. E sua agenda não era apenas limpar as máquinas das empresas, mas também sobrescrever seus Master Boot Records com a imagem do cadáver de Aylan Kurdi. O ataque ocorreu em novembro 17, um feriado muçulmano. Os invasores provavelmente escolheram essa data para contornar as medidas de segurança.
relacionado: A ressurreição de Shamoon Wiper Malware
Agora, outro malware wiper apelidado de StoneDrill foi descoberto em campanhas desastrosas contra organizações da Europa e do Oriente Médio. Pesquisadores da Kaspersky Lab, Contudo, dizem que esta peça é mais sofisticada e destrutiva do que Shamoon, mesmo que os dois compartilhem muitas semelhanças. StoneDrill foi projetado para destruir tudo nas máquinas direcionadas. Mais, é persistente para detecção e erradicação.
Pesquisadores encontram StoneDrill enquanto investigam Shamoon 2.0 ataques
Começando em novembro 2016, A Kaspersky Lab observou uma nova onda de ataques de wiper direcionados a vários alvos no Oriente Médio. O malware usado nos novos ataques era uma variante do infame worm Shamoon que tinha como alvo a Saudi Aramco e Rasgas em 2012.
Shamoon 2.0 ataques compartilham muitas semelhanças com campanhas anteriores, mas apresentam novas ferramentas e técnicas, pesquisadores explicam. Durante a primeira fase de um ataque, hackers obtêm credenciais de administrador para a rede alvo. Então, eles constroem um limpador personalizado que explora as credenciais para se espalhar profundamente dentro da organização-alvo. A fase final ocorre em uma data predefinida quando o limpador é ativado, “tornando as máquinas infectadas completamente inoperantes”. A fase final é totalmente automatizada, e não há necessidade de comunicação com o servidor de comando e controle.
relacionado: Como é fácil invadir uma organização
Enquanto investigava o Shamoon 2.0 ataques, A Kaspersky Lab também descobriu um malware de limpador até então desconhecido que parece ter como alvo organizações na Arábia Saudita. Estamos chamando este novo limpador de StoneDrill.
Como já mencionado, StoneDrill compartilha algumas semelhanças com Shamoon, mas é melhor em evitar a detecção. Além de suspeitos de alvos sauditas, outra vítima do StoneDrill foi observada na Kaspersky Security Network (KSN) na Europa, de acordo com a equipe de pesquisa. “Isso nos faz acreditar que o ator de ameaça por trás do StoneDrill está expandindo suas operações de limpeza do Oriente Médio para a Europa”, a equipe Kaspersky conclui.