Não só regulares, as pessoas que pagam impostos impacientemente esperam Natal - cibercriminosos são tão inquieto.
sim, software malicioso não tira férias e que ‘funciona’ durante todo o ano. Contudo, com o Natal ao virar da esquina, atores mal-intencionados de repente estão um pouco mais determinados a cumprir seus objetivos e colher seus dados e seu dinheiro.
actualização de novembro 2017. Black Friday é um lembrete de que as férias de inverno estão perto. Infelizmente, o número cada vez maior de pessoas às compras online significa mais scams projetado especificamente para números de cartão de crédito-alvo das pessoas e informações pessoais. assim, os usuários devem estar à procura de fraudes, especialmente em compras dias farra, como Black Friday e Cyber Monday. Certifique-se de se familiarizar com o atual, 2017 tendências em campanhas maliciosas distribuído na época do Natal.
O Natal tem sido uma inspiração para os vigaristas da Internet desde "o início dos tempos". É natural nos perguntarmos… O que o Papai Noel de malware tem em estoque para sistemas desprotegidos?
Em primeiro lugar, o que é um ataque PoS?
Um ataque de POS é executado para roubar os números de cartão de crédito de 16 dígitos de clientes de varejo. Você deve ter em mente que assim que esses códigos forem obtidos por malfeitores, eles podem colocá-los à venda em fóruns clandestinos. Lá, eles podem ser vendidos por menos de $100 cada. Essas informações roubadas podem ser usadas para fazer cartões de crédito falsos.
Quais empresas são vítimas de malware PoS? As pequenas e médias empresas são mais fáceis de violar porque seus sistemas PoS são mais vulneráveis a tais ataques.
Atores mal-intencionados estão vendendo uma nova variante de malware de ponto de venda neste momento. A nova cepa está normalmente disponível no subsolo, fóruns criminais. Especialistas em ameaças alertam que esta nova peça PoS tem cerca de 76 KB e pode confundir o software AV. Também é suspeito de ter recursos de rootkit.
Um mecanismo polimórfico também foi implementado para garantir que cada construção tenha assinaturas diferentes. Isso é feito como uma medida contra a proteção contra ameaças ativas.
O 27 de novembro, também conhecido como Black Friday, aumentou o preço da cepa PoS atualizada para $2.600 para uma licença de seis meses. Os cibercriminosos também estão se certificando de estar atualizados com as tendências do sistema operacional no setor de varejo, especialmente aqueles aplicados em sistemas de back-office atuais.
Como se manter protegido contra malware PoS?
- Aplique acesso online ao seu cartão de crédito através da página do emissor do cartão de crédito.
- Certifique-se de verificar regularmente seu extrato de crédito e verificar suas transações.
- Procure por suspeitos $1 cobranças - os vigaristas iriam verificar se o seu cartão funciona fazendo tais "doações".
- Se uma transação suspeita estiver presente no extrato do seu cartão bancário, entre em contato com seu banco imediatamente. Cobranças fraudulentas podem ser revertidas, e sua conta seria congelada para evitar que atividades fraudulentas continuem.
- Em caso de violação de segurança em uma empresa, você é um cliente da, seja extremamente cauteloso. Suas credenciais e equilíbrio não podem ser prejudicados, mas isso não é uma garantia para sua segurança futura. Entre em contato com seu banco para obter conselhos. Além disso, Tenha em mente que os cibercriminosos podem reter um número de cartão de crédito roubado. O número de cartão de crédito de 16 dígitos costuma ser vendido no mercado negro.
- Seja inteligente e proteja suas informações pessoais:
- Mantenha uma ferramenta anti-malware poderosa. Às vezes, várias ferramentas de proteção do usuário podem ser aplicadas para diminuir a possibilidade de um ataque ao mínimo. Além disso, melhorar as configurações e hábitos de navegação do seu navegador.
- Evite usar a opção 'lembrar senha'. Em vez de, mantenha todos os seus logins e credenciais offline, e mudá-los com frequência. Use senhas mais fortes - combinações de números e letras maiúsculas, símbolos etc.
– Endereço;
– Número da Segurança Social;
– Data de nascimento;
– Códigos PIN;
– dados bancários;
– Logins do site;
– Buscas na web.
Malware de Natal em retrospecto
Malware PoS deixado de lado, O Natal tem testemunhado vários golpes online. E como todos os consumidores / usuários sabemos perfeitamente, tendências são importantes não só na moda, mas também na segurança cibernética. Ao dar uma olhada na linha do tempo das surpresas desagradáveis de Natal, você notará que os golpes online (como phishing) não mudou muito ao longo dos anos. Ameaças maliciosas hoje podem ser mais brilho e chitter do que antes (literalmente), mas sua funcionalidade básica permanece inalterada - para induzi-lo a executar o que nunca será executado.
Vamos dar uma olhada em alguns dos mais memoráveis "vírus" de Natal.
Apenas para fins educacionais!
Malware Natal 1987: o verme ‘Árvore de Natal’
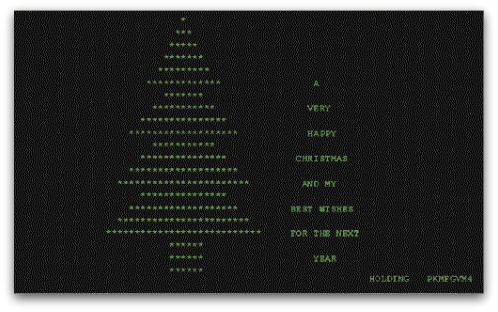
Árvore de Natal, ou CHRISTMAEXEC, é um worm que se espalhou em dezembro 1987. É um dos primeiros exemplos de worm de e-mail. Christmas Tree usou a linha de assunto
_ Deixe este executivo correr e se divertir!’
Uma vez executado, o worm exibiria um caractere EBCDIC e se encaminharia por e-mail para outros usuários.
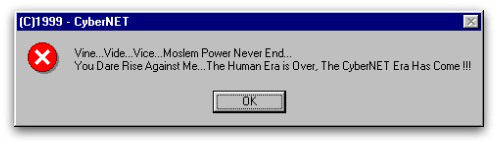
Natal 1999: o vírus Prilissa
O vírus Prillisa a.k.a. WM97 / Melissa-AS era um vírus que infectava documentos do Microsoft Word. Estava se espalhando por e-mail. Sua linha de assunto era:
‘Este documento é muito importante e você TEM que lê-lo !!!’
Abrindo o arquivo anexado, o vírus foi libertado. A carga útil seria ativada em 25 de dezembro e exibiria a seguinte mensagem:
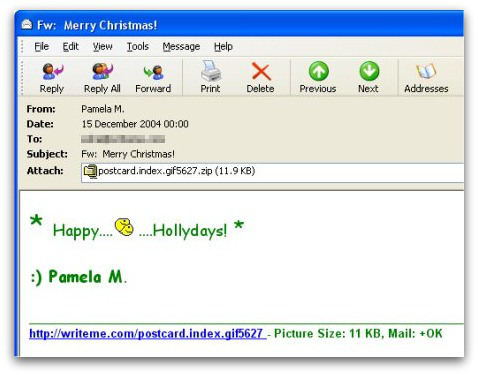
Natal 2004: o vírus Zafi-D
Natal 2004 vi um vírus bastante malévolo chamado Zafi-D. Fabricado na Hungria, o vírus se espalharia por e-mail e recitaria saudações sazonais. A ameaça também foi escrita em vários idiomas, certificando-se de que afetaria o maior número possível de usuários.
Suficientemente curioso, o vírus com tema de Natal incorporaria uma imagem GIF animada obscena de dois rostos sorridentes um em cima do outro.
Como você pode ver, os métodos aplicados por agentes mal-intencionados para induzi-lo a infectar seu PC não mudaram muito. É o malware que se tornou mais persistente e sofisticado.
assim, certifique-se de proteger seu computador antes de ser vítima de mais um golpe com tema de Natal.
Como salvar o espírito natalino e ficar longe de vírus e vermes?
- Certifique-se de usar a proteção de firewall adicional. A descarga de um segundo firewall (gostar ZoneAlarm, por exemplo) é uma excelente solução para quaisquer potenciais intrusões.
- Certifique-se de que seus programas tenham menos poder administrativo sobre o que lêem e escrevem no seu computador. Torná-los pedir-lhe acesso de administrador antes de iniciar.
- Use senhas fortes. senhas fortes (de preferência aqueles que não são palavras) são mais difíceis de rachadura por vários métodos, incluindo força bruta, uma vez que inclui listas de passagem com palavras relevantes.
- Desligue o AutoPlay. Isso protege o seu computador de arquivos executáveis maliciosos no pen drives ou outros transportadores de memória externos que são imediatamente inseridos nele.
- Desativar compartilhamento de arquivos - é recomendado se você precisar de compartilhamento de arquivos entre o seu computador para protegê-lo com senha e restringir a ameaça apenas a você se infectado.
- Desligue todos os serviços remotos - isso pode ser devastador para as redes empresariais, pois pode causar muitos danos em grande escala.
- Se você ver um serviço ou um processo que é externo e não o Windows crítico e está sendo explorada por hackers (Como Flash Player), desativá-lo até que haja uma atualização que corrige o exploit.
- Certifique-se sempre para atualizar os patches de segurança críticos para o seu software e sistema operacional.
- Configurar o servidor de correio para bloquear e apagar anexos de arquivo suspeito contendo e-mails.
- Se você tem um computador comprometido em sua rede, certifique-se de isolar-lo imediatamente por desligá-la e desconectá-lo manualmente a partir da rede.
- Desligue todos os serviços não necessários sem fio, como portas de infravermelhos ou Bluetooth - hackers gostam de usá-los para explorar dispositivos. No caso de você usar o Bluetooth, certifique-se de monitorar todos os dispositivos não autorizados que pedir-lhe para emparelhar com eles e declínio e investigar qualquer queridos suspeitos.
- Empregue uma solução anti-malware poderosa para se proteger de quaisquer ameaças futuras automaticamente.
Referências
NakedSecurity da Sophos
O registro
Norton