Not only regular, tax-paying people impatiently await Christmas – cyber crooks are just as restless.
Yes, malicious software doesn’t take vacations and it ‘works’ all year round. However, with Christmas just around the corner, malicious actors are suddenly a tad more determined to accomplish their goals and harvest your data and your money.
Update November 2017. Black Friday is a reminder that the winter holidays are near. Unfortunately, the ever increasing number of people shopping online means more scams specifically designed to target people’s credit card numbers and personal information. So, users should be on the lookout for scams especially on shopping spree days such as Black Friday and Cyber Monday. Make sure to get acquainted with the current, 2017 trends in malicious campaigns distributed around Christmas.
Christmas has been an inspiration for Internet crooks since ‘the beginning of time’. It’s only natural to ask ourselves… What does malware Santa have in stock for unprotected systems?
First of all, what is a PoS attack?
A POS attack is executed to steal the 16-digit credit card numbers of retail customers. You should keep in mind that once those codes are obtained by bad actors, they can put them for sale on underground forums. There, they can be sold for less than $100 each. This stolen information can be employed in making fake credit cards.
What companies fall victim to PoS malware? Small and medium businesses are easier to be breached because their PoS systems are more vulnerable to such attacks.
Bad actors are selling a new variant of Point-of-Sale malware as we speak. The new strain is typically available on underground, criminal forums. Threat specialists warn that this new PoS piece is just about 76KB and can baffle AV software. It is also suspected to have rootkit capabilities.
A polymorphic engine has also been implemented to make sure that each build has different signatures. This is done as a measure against active threat protection.
The 27th of November, also known as Black Friday, has increased the price of the updated PoS strain to $2.600 for a six-month license. Cyber criminals are also making sure to be up-to-date with OS trends in the retail sector, especially the ones applied in current back-office systems.
How to Stay Protected Against PoS Malware?
- Apply online access to your credit card via the credit card’s issuer page.
- Make sure to check regularly your credit statement and verify your transactions.
- Look for suspicious $1 charges – crooks would check if your card works by making such ‘donations’.
- If a suspicious transaction is present in your bank card statement, contact your bank immediately. Fraudulent charges may be reversed, and your account would be frozen to keep crook activities from continuing.
- In case of a security breach in a company you are a customer of, be extra cautious. Your credentials and balance may not be hurt, but this is not a guarantee for your future safety. Contact your bank for advice. Also, keep in mind that cyber criminals may hold on to a stolen credit card number. The 16-digit credit card number is often sold on the black market.
- Be smart and protect your personal information:
- Sustain a powerful anti-malware tool. Sometimes several tools for user protection can be applied to decrease the possibility of an attack to the minimum. Also, improve your browser’s settings and browsing habits.
- Avoid using the ‘remember password’ option. Instead, keep all your logins and credentials offline, and change them frequently. Use stronger passwords – combinations of numbers and upper case letters, symbols etc.
– Address;
– Social security number;
– Date of birth;
– PIN codes;
– Banking credentials;
– Website logins;
– Web searches.
Christmas Malware in Retrospect
PoS malware left aside, Christmas has been witnessing various online scams. And as we all consumers/ users perfectly know, trends are a thing not only in fashion but also in cyber security. By having a look at the timeline of Christmas’s nasty surprises, you will notice that online scams (such as phishing) haven’t changed much throughout the years. Malicious threats today may be more glitter and chitter than before (quite literally), but their basic functionality remains unchanged – to trick you into executing what shall never be executed.
Let’s have a look at some of the more memorable Christmas ‘viruses’.
For educational purposes only!
Christmas Malware 1987: the ‘Christmas Tree’ Worm
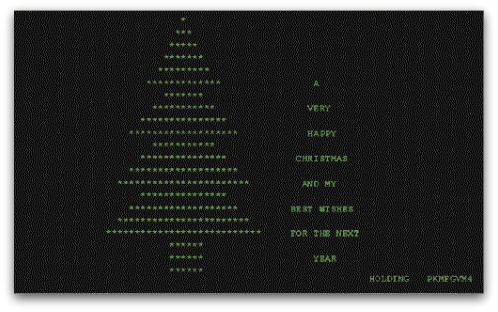
Christmas Tree, or CHRISTMAEXEC, is a worm that was spread in December 1987. It’s an early example of an email worm. Christmas Tree used the subject line
‘Let this exec run and enjoy yourself!’
Once executed, the worm would display an EBCDIC character and would forward itself via email to other users.
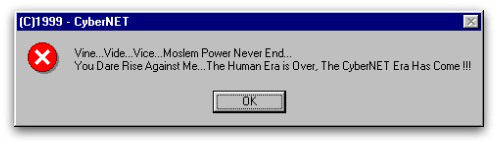
Christmas 1999: the Prilissa Virus
The Prillisa Virus a.k.a. WM97/Melissa-AS was a virus that infected Microsoft Word documents. It was spreading via email. Its subject line was:
‘This document is very Important and you’ve GOT to read this !!!’
By opening the attached file, the virus was set free. The payload would activate on December 25th and would display the following message:
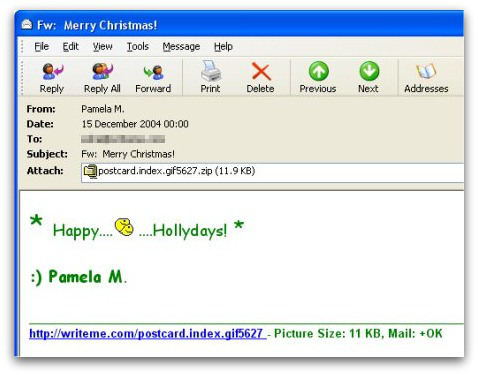
Christmas 2004: the Zafi-D Virus
Christmas 2004 saw a rather malevolent virus called Zafi-D. Crafted in Hungary, the virus would spread via email and would recite seasonal greetings. The threat was also written in various languages, making sure it would affect as many users as possible.
Curiously enough, the Christmas-themed virus would embed an obscene animated GIF image of two smiley faces on top of one another.
As you can see, the methods applied by malicious actors to trick you into infecting your PC haven’t changed that much. It’s the malware that has become more persistent and sophisticated.
So, make sure to protect your computer before you fall victim of yet another Christmas-themed scam.
How to Save the Christmas Spirit and Stay Away from Viruses and Worms?
- Make sure to use additional firewall protection. Downloading a second firewall (like ZoneAlarm, for example) is an excellent solution for any potential intrusions.
- Make sure that your programs have less administrative power over what they read and write on your computer. Make them prompt you admin access before starting.
- Use stronger passwords. Stronger passwords (preferably ones that are not words) are harder to crack by several methods, including brute forcing since it includes pass lists with relevant words.
- Turn off AutoPlay. This protects your computer from malicious executable files on USB sticks or other external memory carriers that are immediately inserted into it.
- Disable File Sharing – it is recommended if you need file sharing between your computer to password protect it to restrict the threat only to yourself if infected.
- Switch off any remote services – this can be devastating for business networks since it can cause a lot of damage on a massive scale.
- If you see a service or a process that is external and not Windows critical and is being exploited by hackers (Like Flash Player), disable it until there is an update that fixes the exploit.
- Make sure always to update the critical security patches for your software and OS.
- Configure your mail server to block out and delete suspicious file attachment containing emails.
- If you have a compromised computer in your network, make sure to isolate immediately it by powering it off and disconnecting it by hand from the network.
- Turn off any non-needed wireless services, like Infrared ports or Bluetooth – hackers love to use them to exploit devices. In case you use Bluetooth, make sure that you monitor all of the unauthorized devices that prompt you to pair with them and decline and investigate any suspicious ones.
- Employ a powerful anti-malware solution to protect yourself from any future threats automatically.
References
NakedSecurity by Sophos
TheRegister
Norton