Pesquisadores da Palo Alto Networks descobriram uma nova família de malware afetando Apple OS X e iOS. Dublado WireLurker, o malware compromete até mesmo dispositivos iOS sem jailbreak.
Este é o primeiro tipo de malware que infecta aplicativos iOS de uma maneira que um vírus tradicional faz. O WireLurker também automatiza os aplicativos iOS maliciosos por meio da substituição de arquivos binários. O malware foi detectado pela primeira vez em junho deste ano por um desenvolvedor chinês da Tencent Company. Pouco depois de sua descoberta, vários usuários começaram a relatar sobre aplicativos estranhos sendo instalados em seus iPads e iPhones sem jailbreak. Os usuários de Mac também reclamaram de daemons de inicialização com nomes como “WatchProc” em suas máquinas. As vítimas disseram ter instalado aplicativos da App Store da Maijadi anteriormente.
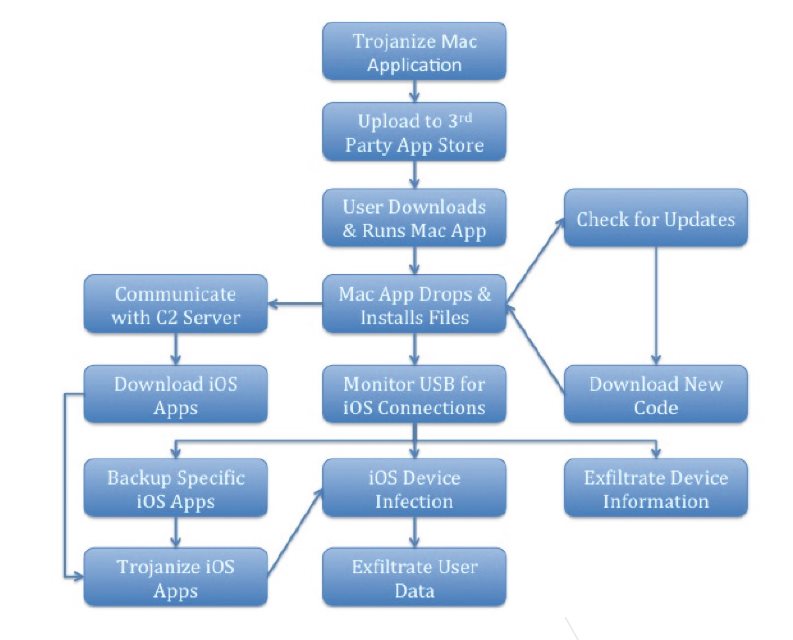
WireLurker - Métodos de infiltração e comportamento
Os pesquisadores descobriram que os aplicativos para Mac baixados desta loja no período de abril 30 para junho 11 continha WireLurker. 467 aplicativos que provaram ser positivos para cavalos de Troia foram baixados 356, 104 vezes. O WireLurker seria distribuído para a máquina da vítima em um desses aplicativos trojanizados. Após a instalação, o malware entra em contato com o Control and Command Server e solicita atualizações. Caso o Mac comprometido esteja conectado a outros dispositivos iOS via USB, o malware os detectaria e definiria se o dispositivo está desbloqueado ou não.
- Dispositivos desbloqueados: O WireLurker faria backup de determinados aplicativos do dispositivo para o Mac e os reempacotaria com um arquivo binário malicioso. Os aplicativos modificados seriam então instalados por meio de um protocolo iTunes.
- Dispositivos sem jailbreak: WireLurker iria instalar aplicativos iOS que ele baixa e explorar protocolos do iTunes que foram implementados pela biblioteca libimobiledevice.
Até agora, o WireLurker foi atualizado várias vezes. No início, não era capaz de afetar dispositivos iOS, e a comunicação com o servidor de Comando e Controle estava em texto simples.
Missão da WireLurker
O principal objetivo do malware é coletar informações específicas do dispositivo, como:
- Modelo, serial, número de telefone
- Tipo de dispositivo
- ID Apple do usuário
- Endereço wi-fi
- Dados de uso de disco
WireLurker irá então enviar as informações coletadas para o C&servidor C. A estrutura do código exibida pelo malware é complexa, suas versões contêm vários componentes, e usa criptografia personalizada para evitar a reversão. Os pesquisadores acreditam que o WireLurker está sendo desenvolvido ativamente no momento. O que seria usado no futuro ainda é um borrão.
Os usuários são aconselhados a não baixar aplicativos de lojas de terceiros e, sob nenhuma circunstância, conectar seu dispositivo iOS a um PC em que não confiem. Caso você suspeite que seu dispositivo já está comprometido, verifique os processos em busca de arquivos questionáveis.

