O que é o Zemot?
O Zemot Dropper é um tipo de download de malware. Faz parte de uma rede complexa, que inclui diferentes tipos de malware. Diferentes variantes do Zemot podem ser distribuídas com outro malware, já que um dropper pode espalhar muitas cargas maliciosas.
Quando Zemot foi descoberto?
No fim de 2013, A Microsoft notou atividade do TrojanDownloader:Win32 / Upatre.B. A empresa descobriu que ele é usado por criminosos cibernéticos para a distribuição de PWS:Win32 / Zbot.CF e PWS:Win32 / Zbot.gen!Malware AP click-fraud. Em maio 2014 Upatre.B foi renomeado para Zemot para que as duas ameaças possam ser diferenciadas. Eles são de natureza semelhante, com certas diferenças cada e, portanto, podem ser rotulados como uma nova família de malware.
Como o Zemot entra no computador do usuário?
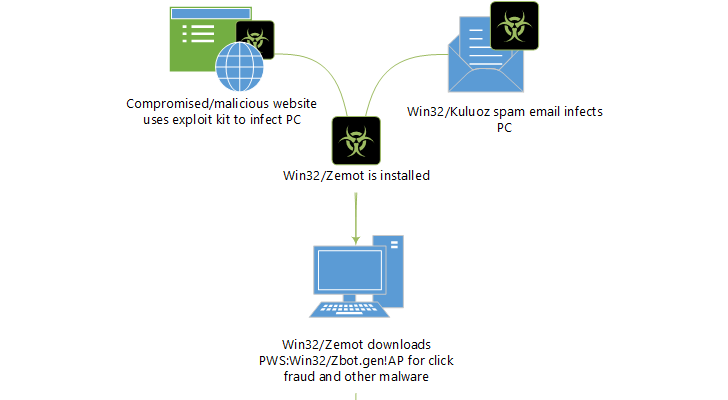
Os pesquisadores de segurança confirmam que Zemot vem de pontos de distribuição múltipla que incluem Asprox & Kuluoz botnet de envio de spam, bem como sites comprometidos. O malware também pode entrar no PC do usuário por meio dos kits de exploração de Nuclear Pack e Magnitude. Zemot usa várias técnicas para se certificar de que o módulo terá sucesso em todas as plataformas do Windows.
Como o Zemot afeta o computador do usuário?
Quando Zemot está no sistema do computador, ele se funde em malware fraudulento de cliques. De acordo com os especialistas em segurança, os computadores dos usuários também são afetados por outras ameaças, incluindo Tesch, Viknok e Rovnix. Essas ameaças são usadas para roubar malware e fazer download de novos malwares. Zemot é uma cadeia de infecção complexa que depende de vários droppers para que o malware para roubo de informações chegue ao computador infectado.
Zemot armazena os arquivos baixados dando-lhes nomes de arquivo exclusivos. Isso aumenta a detecção de evasão e aumenta o número de infecções no computador. A análise de URL, o privilégio do usuário e o método de download são retirados do código-fonte do Zbot.
O veredito
Dados de telemetria da Microsoft mostram que Zemot afetou menos computadores desde maio 2014, caindo para 30,000 máquinas em junho e agosto. No inicio de setembro, A Microsoft informou aos usuários que já iniciou rotinas para remover a ferramenta da família Zemot dos sistemas afetados e que agora faz parte da Ferramenta de Remoção de Software Malicioso.