What Is Zemot?
Zemot Dropper is a type of malware downloader. It is part of a complex network, which includes different malware types. Different variants of Zemot can be distributed with other malware as one dropper can spread many malicious payloads.
When Was Zemot Spotted?
At the end of 2013, Microsoft noticed activity from TrojanDownloader:Win32/Upatre.B. The company found out that it is used by the cyber criminals for the distribution of PWS:Win32/Zbot.CF and PWS:Win32/Zbot.gen!AP click-fraud malware. In May 2014 Upatre.B was renamed into Zemot so that the two threats can be differentiated. They are of a similar nature, with certain differences each and thus can be labeled as a new malware family.
How Does Zemot Enter the User’s Computer?
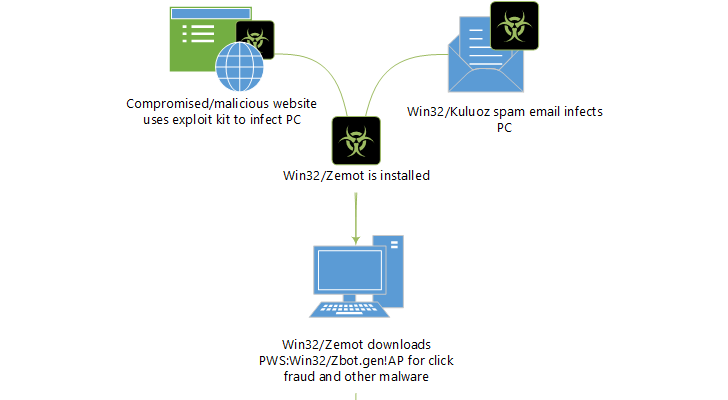
The security researchers confirm that Zemot comes from multi-distribution points which include Asprox & Kuluoz spam-sending botnet, as well as compromised websites. The malware can also enter the user’s PC through the exploit kits of Nuclear Pack and Magnitude. Zemot uses several techniques to make sure that the module will be successful on all platforms of Windows.
How Does Zemot Affect the User’s Computer?
When Zemot is in the computer’s system, it funnels into click-fraud malware. According to the security experts, the computers of the users are also affected by other threats including Tesch, Viknok and Rovnix. These threats are used for stealing malware and for downloading new malware. Zemot is a complex infection chain that relies on several droppers for the info-stealing malware to reach the infected computer.
Zemot stores the downloaded files giving them unique file names. This adds to the evading detection and increases the deal of the infections in the computer. The URL parsing, the user privilege and downloading method are taken from the Zbot source code.
The Verdict
Microsoft telemetry data shows that Zemot affected fewer computers since May 2014, dropping down to 30,000 machines in June and August. At the beginning of September, Microsoft informed the users that it has already started routines for removing Zemot family tool from the affected systems and that this is now part of the Malicious Software Removal Tool.