Nach der ersten Variante von Cerber Ransomware geschlagen, es wurde klar, dass dies auf den ahnungslosen Benutzer Kosten eine äußerst effektive Geld Malware ist. Leider gibt es derzeit keine relevante Entschlüsselungsmethode außer dem Cerber-Datei-Entschlüsseler, der von den Cyber-Gaunern hinter der Malware verkauft wird. Nicht nur das, sondern auch diese spezielle Malware verwendet zwei Verschlüsselungsalgorithmen und verschlüsselt sogar den Entschlüsselungsschlüssel des AES-Verschlüsselers mit einer RSA-Verschlüsselung. Den Benutzern bleibt nichts anderes übrig, als hilflos in Sicherheitsforen zu betteln, damit ihre Dateien entschlüsselt werden und Malware-Forscher - na ja, Sie versuchen immer noch, eine Lösung zu finden, um mit dieser Malware fertig zu werden.

Cerber Ransomware und ihre Verbreitung
Um sich auszubreiten in die offene, Cerber verwendet möglicherweise verschiedene Arten von Malware sowie Hilfstools:
Es hängt wirklich davon ab, welche Strategie von dieser Malware verwendet wird, weil es online als Service verkauft wird und jeder Cyber-Gauner, der es kauft, die Möglichkeit hat, seine Vorlieben anzupassen. Die Trojaner-Dropper und Exploit-Kits können durch die Verwendung fortschrittlicher Kryptoren verschleiert werden, die die Malware vor den neuesten Definitionen von Antivirensoftware verbergen. Dadurch wird sichergestellt, dass die Cerber-Ransomware erfolgreich aktiviert wird und der Verschlüsselungsprozess ohne Probleme ausgeführt werden kann.
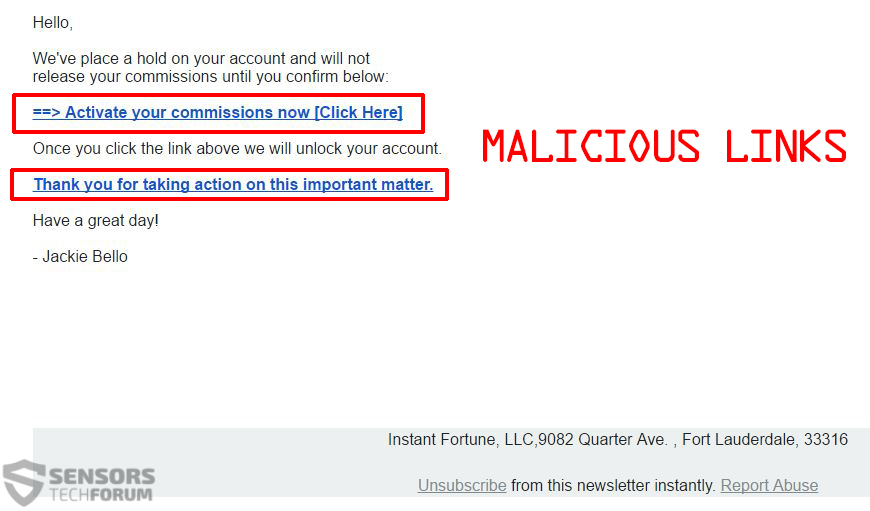
Die schädlichen Dateien können entweder mithilfe von Drive-by-Downloads und Injektoren über eine schädliche URL verteilt oder auf verschiedenen Websites als Kommentare angezeigt werden, oder als Antwort in Foren. Es ist auch durchaus möglich, dass Benutzer infiziert werden über böswillige Links, wie im folgenden Beispiel:
Darüber hinaus kann die schädliche Software auch als E-Mail-Anhang mitgeführt werden. Sobald die böswillige EXE-Datei auf Ihrem Computer ausgeführt wird, Das Windows-Dateisystem sowie die Registrierungseinträge des Betriebssystems werden sofort geändert. Dann beginnt ein Verschlüsselungsprozess mit zwei Algorithmen, auf der Suche nach einer Vielzahl von Dateierweiterungen zum Verschlüsseln. Schlimmer ist, dass Cerber auch überdurchschnittlich große Dateien verschlüsselt, die den ersten Teil der Daten der großen Datei verschlüsseln.
Wie schütze ich mich vor Cerber und anderer Ransomware?
Um sich vor jeder Art von Bedrohung zu schützen, Zuerst müssen Sie wissen, womit Sie es zu tun haben und wie es funktioniert. Jedoch, Wir haben auch den menschlichen Faktor, weil Cyberkriminelle, die hinter Ransomware stehen, Vordenker bei der Änderung der Infektionsmethoden und der Verschleierung der Malware sind. Nicht nur das, Sie tendieren aber auch dazu, andere Verbesserungen vorzunehmen, um ein stetiges Einkommen aus dieser Cyberkriminalität zu erzielen.
Der Infektionsprozess von Cerber Ransomware umfasst mehrere Skripte, mit denen das Ziel erreicht werden kann. Einer davon enthält voreingestellte Befehle, mit denen der Windows-Registrierungseditor sofort geändert und Dateien ohne Berechtigung erstellt werden können. Die Logik dahinter besteht darin, nach Software zu suchen, die es ihr nicht ermöglicht, solche nicht autorisierten Änderungen vorzunehmen. Aus diesem Grund empfehlen wir die Verwendung einer Sandbox-Software, Das wird sicherstellen, dass Sie ein bisschen besser geschützt sind.
Eines der Programme, die wir getestet haben, um den böswilligen Exes entgegenzuwirken, heißt Sandboxie. Die Software konnte eine ausführbare Datei erfolgreich stoppen, indem sie in einer Sandbox geschlossen wurde von verschlüsseltem Code und erlaubt es daher nicht, Änderungen im Windows-Dateisystem vorzunehmen. Der ausführbaren Datei der Ransomware blieb nichts anderes übrig, als sich selbst zu schließen.
Dies ist ein gutes Werkzeug, aber es dient nur als erste Verteidigungslinie dagegen. Es ist bekannt, dass Sanboxing-Software Malware vorbeirutschen lässt und dennoch Chaos auf Ihrem PC anrichtet. Aus diesem Grund benötigen Sie eine zusätzliche Schutzschicht. Zum Glück, BitDefender hat sich ausgedacht Eine Anti-Ransomware-Software, die nach den spezifischen Aktionen sucht, die Ransomware ausführt, und verhindert, dass Daten verschlüsselt werden. Die Software wird ständig mit der neuesten Ransomware aktualisiert, die in freier Wildbahn herauskommt, und Experten empfehlen es sehr für den grundlegenden Schutz zu Hause gegen Ransomware.
Software-Überprüfung von BitDefender Anti-Ransomware
Jedoch, Es ist wichtig zu wissen, dass Ransomware nicht nur auf eigene ausführbare Dateien beschränkt ist. Wie zuvor erwähnt, Es erstreckt sich auch auf andere Malware, die es verwendet, um sich selbst herunterzuladen. Diese Malware kann die Software deaktivieren, die verhindert, dass die Ransomware Ihre Daten erfolgreich verschlüsselt, und die Ransomware dann auf Ihren PC herunterladen. Deshalb wir empfehlen eine erweiterte Anti-Malware-Tool die häufig mit den neuesten PUPs aktualisiert wird(Potentiell unerwünschte Programme) Dadurch werden Sie möglicherweise umgeleitet oder Anzeigen geschaltet, die auf schädliche URLs verweisen und Malware in Echtzeit stoppen.
Software-Überprüfung von SpyHunter
Auch, als zusätzliche Schutzschicht, Wir empfehlen die Verwendung eines Sicherungsdienstes. Aber wenn wir Backup-Service sagen, Wir meinen, dass Sie die Verwendung von Volume Shadow Copies in und anderen Windows-Standardsicherungsdiensten auf Ihrem PC vermeiden sollten. Dies liegt daran, dass Ransomware heutzutage normalerweise verwendet wird löscht die Schattenkopien der Windows-Computer dass es infiziert. Dies ist der Hauptgrund, warum Sie sich an der Verwendung eines externen Sicherungsdienstes orientieren sollten. Sie können Ihre Dateien manuell auf einem USB-Laufwerk speichern oder auf eine CD oder eine Speicherkarte schreiben. Jedoch, Wir empfehlen die Verwendung automatischer Cloud-Backup-Service, wie SOS Cloud Backup.
Software-Überprüfung von SOS Cloud Backup
Diese Programme können ausreichen, um Sie zu schützen, selbst wenn Sie zur Gruppe der unsicheren Benutzer gehören. Jedoch, wenn deine Paranoia dir sagt, dass es nicht genug ist, Wir empfehlen die Verwendung eine externe Firewall um Ihr Schutzniveau zu erhöhen. Solche Tools können auf einen maximalen Sicherheitsmodus eingestellt werden und erkennen jeden neuen Prozess, der versucht, Windows zu ändern. Es ist äußerst nützlich, Es ärgert Sie jedoch jedes Mal, wenn Sie ein Programm starten, mit Popups. Zum Glück für Sie, Sie können mehrere Programme, die Sie verwenden, auf vertrauenswürdige Programme setzen und verhindern, dass Sie erneut gefragt werden. Dies funktioniert im Allgemeinen mit allen Firewall-Programmen. In die meisten Anti-Malware-Tools ist eine Firewall als zusätzliche Funktion eingebettet, Unternehmen wie ZoneAlarm verwenden jedoch eine separate Firewall. Besser ist, dass diese absolut kostenlos ist.
Was ist bei der Verwendung von Schutzwerkzeugen zu beachten?
Als untere Zeile, nicht System ist 100 Prozent sicher. Und wenn Sie in Sicherheit investieren möchten, fahren Sie fort. Bedenken Sie jedoch, dass Ihr Gerät möglicherweise nicht hergestellt wird 100 Prozent sicher. Aus diesem Grund empfehlen wir, einige von uns erstellte Tipps und Empfehlungen zu implementieren, die Sie in Zukunft vor Ransomware und anderer Malware schützen:
Als Bonus, Wir haben einen Bericht für Top vorbereitet 10 kostenlose Antivirensoftware, weil wir wissen, dass nicht jeder Benutzer die Verfügbarkeit hat, in solche Programme zu investieren. Deshalb haben wir getestet 10 der größten Namen in Free Antivirus, um sicherzustellen, dass Benutzer wissen, was sie herunterladen. Sie können den Bericht unten überprüfen:
Top 10 Kostenloser Antivirensoftware-Bericht (2015)
Abschluss
Abschließend würden wir sagen, dass es gibt kein System das ist 100 Prozent sicher. Aus diesem Grund empfehlen wir dringend, dem Blog und unserem Forum sowie anderen unabhängigen Sicherheitsblogs zu folgen, die kostenlose Unterstützung bieten, um über die neuesten Malware-Updates auf dem Laufenden zu bleiben 1 den heutigen Cyber-Gaunern einen Schritt voraus.