 Ransomware-Virus, sehr viel TeslaCrypt und Locky ähnelt Ransomware, genannt Ransomcuck wurde berichtet, die betroffenen Nutzer zu sperren’ Dateien, die die AES und RSA-Verschlüsselungsalgorithmen. Der Virus verwendet die Dateierweiterungen .ransomcuck und .cuck, nachdem er die Dateien eines infizierten Computers verschlüsselt hat. Es dann, hinterlässt mehrere Lösegeldscheine, und Benutzern, die Opfer dieses Virus geworden sind, wird dringend empfohlen, kein Geld zu zahlen, das von den Cyberkriminellen in diesen Notizen verlangt wird. Da dies eine sehr verheerende Bedrohung ist, im Augenblick, Wir empfehlen dringend, es zu entfernen und zu versuchen, verschlüsselte Dateien mit den in diesem Artikel beschriebenen alternativen Methoden zu entschlüsseln, während ein tatsächlicher Entschlüsseler freigegeben wird.
Ransomware-Virus, sehr viel TeslaCrypt und Locky ähnelt Ransomware, genannt Ransomcuck wurde berichtet, die betroffenen Nutzer zu sperren’ Dateien, die die AES und RSA-Verschlüsselungsalgorithmen. Der Virus verwendet die Dateierweiterungen .ransomcuck und .cuck, nachdem er die Dateien eines infizierten Computers verschlüsselt hat. Es dann, hinterlässt mehrere Lösegeldscheine, und Benutzern, die Opfer dieses Virus geworden sind, wird dringend empfohlen, kein Geld zu zahlen, das von den Cyberkriminellen in diesen Notizen verlangt wird. Da dies eine sehr verheerende Bedrohung ist, im Augenblick, Wir empfehlen dringend, es zu entfernen und zu versuchen, verschlüsselte Dateien mit den in diesem Artikel beschriebenen alternativen Methoden zu entschlüsseln, während ein tatsächlicher Entschlüsseler freigegeben wird.

Threat Zusammenfassung
| Name | Ransomcuck |
| Art | Ransomware |
| kurze Beschreibung | Die Ransomware versucht, häufig verwendete Dateien zu verschlüsseln. Sie erhalten eine Zahlungsfrist, sonst steigt der Preis. |
| Symptome | Die Ransomware verschlüsselt Dateien, Ändern ihrer Erweiterungen in .cuck oder .ransomcuck. Danach zeigt es eine Erpresserbrief als Desktop-Hintergrund und in einem Pop-up-Fenster auf Ihrem Desktop. |
| Verteilungsmethode | Spam-E-Mails, File Sharing Networks, Ausführbare Dateien |
| Detection Tool |
Überprüfen Sie, ob Ihr System von Malware betroffen ist
Herunterladen
Malware Removal Tool
|
| Benutzererfahrung | Abonnieren Sie unseren Forum Ransomcuck zu diskutieren. |
| Data Recovery-Tool | Windows Data Recovery von Stellar Phoenix Beachten! Dieses Produkt scannt Ihr Laufwerk Sektoren verlorene Dateien wiederherzustellen, und es kann sich nicht erholen 100% der verschlüsselten Dateien, aber nur wenige von ihnen, je nach Situation und ob Sie das Laufwerk neu formatiert haben. |

Ransomcuck-Virus - Wie infiziert es sich?
Einen Angriff durchführen, Die böswillige Nutzlast von Ransomcuck muss auf dem Zielcomputer abgelegt werden. Dies kann auf zwei Arten geschehen: über eine schädliche Datei, die getarnt ist, um Benutzer zum Öffnen zu verleiten, oder über eine schädliche URL, die zum automatischen Herunterladen und Ausführen auf dem PC des Opfers führen kann.
Was auch immer der Fall sein kann, Der Virus kann über Spam-E-Mail-Nachrichten verbreitet werden, die beide enthalten können – die URLs oder böswilligen Anhänge. Sobald es massiv an eine vorprogrammierte Liste von E-Mail-Adressen gesendet wurde, können die Nachrichten mit den schädlichen Dateien variieren. Beispielsweise, Eine Spam-Nachricht kann behaupten, dass der Benutzer für eine Bestellung bezahlt hat, und eine „Rechnung“ bereitstellen, bei der es sich möglicherweise um die schädliche Datei handelt. Es kann aber auch Nachrichten geben, Der Benutzer wurde als Freund auf Facebook mit einem gefälschten "Mehr anzeigen" -Button hinzugefügt, der nicht zu Facebook führt, kann den Benutzer auf einen böswilligen Weblink übertragen, der die Infektion verursachen kann

Ransomcuck Ransomware im Detail
Sobald Ransomcuck auf Ihrem Computer ausgeführt wurde, Es kann seine Dateien ohne Erlaubnis und ohne dass Sie es bemerken, direkt löschen und ausführen. Die schädlichen Dateien können mehr als nur eine EXE-Datei sein, und sie befinden sich möglicherweise in den folgenden wichtigen Windows-Ordnern:
- %AppData%
- %Wandernd%
- %Temp%
- %Local%
- %Systemdrive%
- %System32%
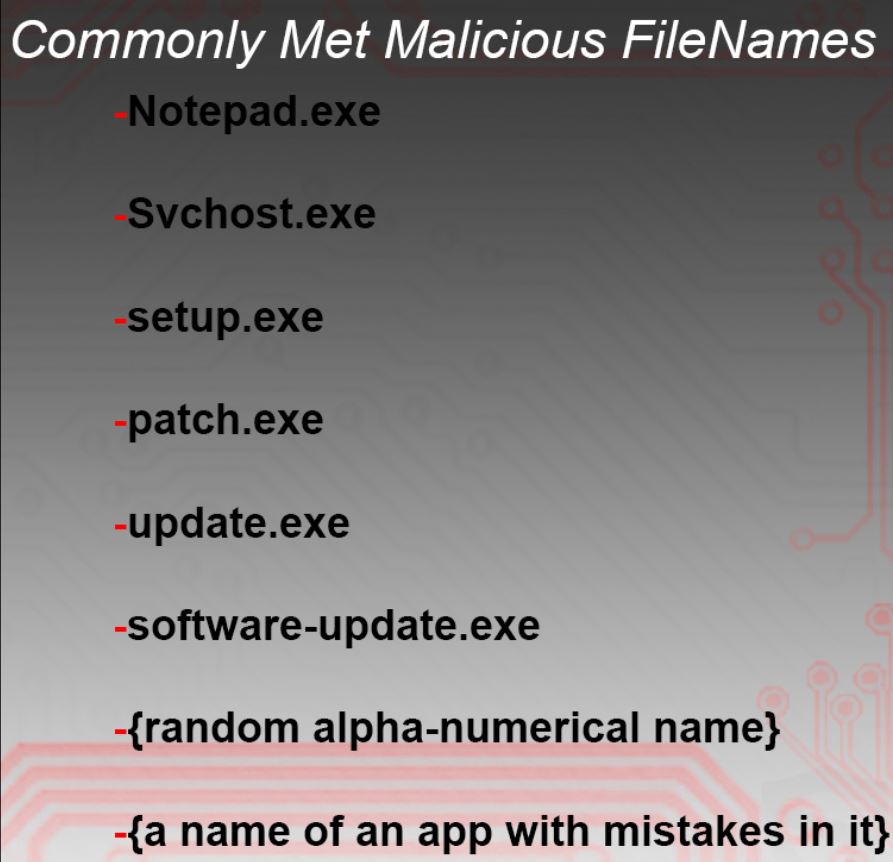
Die schädlichen Dateien von Ransomcuck kann unterschiedliche Namen enthalten, beispielsweise:
Sobald der Ransomcuck-Virus auf Ihrem Computer ist, Es kann auch die Registrierungsschlüssel Run und RunOnce angreifen, Erstellen von Wertzeichenfolgen mit dem Speicherort des Dateiverschlüsselers und den Lösegeldnotizen, damit sie bei jedem Start von Windows ausgeführt werden.
Nachdem das primäre Verschlüsselungsmodul der Ransomcuck-Malware-Infektion ausgeführt wurde, Der Virus sucht möglicherweise nach einer Vielzahl von Dateitypen, die verschlüsselt werden sollen. Es sucht hauptsächlich nach Dateien, die wichtig sind und häufig verwendet werden, sowie:
- Unterlagen.
- Datenbanken.
- Audiodateien.
- Video-Dateien.
- Dateien, die mit häufig verwendeten Programmen, wie Photoshop, beispielsweise.
- Präsentationen.
- Bilder.
Das Ransomcuck-Virus ist in seinen Aktionen sehr klug, Überspringen wichtiger Windows-Ordner, um Dateien darin zu verschlüsseln, da dies Ihr Betriebssystem beschädigen kann.
Um die Dateien der Opfer zu verschlüsseln, Der Ransomcuck-Virus verwendet nach den Dateien die Dateierweiterungen .cuck oder .ransomcuck. Mit dieser Ransomware verschlüsselte Dateien, sieht wie folgt aus und kann von keiner Software geöffnet werden:
Dies liegt daran, dass der Ransomcuck-Virus zwei der stärksten Verschlüsselungsalgorithmen verwendet, um den Strukturcode der Dateien zu verschlüsseln - AES (Advanced Encryption Standard) und RSA (Rivest-Shamir-Adleman) Chiffren. Die AES-Verschlüsselung wird zu einem einzigen Zweck verwendet, um die Dateien selbst zu verschlüsseln, Generieren eines eindeutigen Entschlüsselungsschlüssels. Dieser Entschlüsselungsschlüssel wird dann gespeichert und mit dem RSA-Algorithmus verschlüsselt, und dann werden diese Informationen entweder über TCP- oder UDP-Verkehr an die Server der Cyberkriminellen gesendet, Damit sind sie die einzigen, die die Dateien entschlüsseln können.
In Verbindung stehende Artikel: Ransomware Encryption erklärt - Warum ist es so effektiv?
Nach der Verschlüsselung, Dieser Virus hinterlässt dann auf dem %Desktop-% zwei Dateien:
- How_to_Recover_ Files.html
- How_to_Recover_ Files.txt
Es wird berichtet, dass die Dateien den folgenden Lösegeldschein enthalten:
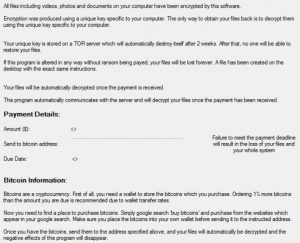
→„Alle Dateien einschließlich Videos, Fotos, und Dokumente auf Ihrem Computer wurden mit dieser Software verschlüsselt.
 Die Verschlüsselung wurde mit einem eindeutigen Schlüssel für Ihren Computer erstellt. Die einzige Möglichkeit, Ihre Dateien zurückzugewinnen, besteht darin, sie mit dem für Ihren Computer spezifischen eindeutigen Schlüssel zu entschlüsseln.
Die Verschlüsselung wurde mit einem eindeutigen Schlüssel für Ihren Computer erstellt. Die einzige Möglichkeit, Ihre Dateien zurückzugewinnen, besteht darin, sie mit dem für Ihren Computer spezifischen eindeutigen Schlüssel zu entschlüsseln.
Ihr eindeutiger Schlüssel wird auf einem TOR-Server gespeichert, der sich danach automatisch selbst zerstört 2 Wochen. Danach, Niemand kann Ihre Dateien wiederherstellen.
Wenn dieses Programm in irgendeiner Weise geändert wird, ohne dass Lösegeld gezahlt wird, Ihre Dateien sind für immer verloren. Auf dem Desktop wurde eine Datei mit genau denselben Anweisungen erstellt.
Ihre Dateien werden automatisch entschlüsselt, sobald die Zahlung eingegangen ist.
Dieses Programm kommuniziert automatisch mit dem Server und entschlüsselt Ihre Dateien, sobald die Zahlung eingegangen ist. “

Ransomcuck-Virus - Schlussfolgerung, Entfernung, und Dateiwiederherstellung Alternativen
Malware-Forscher glauben, dass dieses Virus von demselben Codierer erstellt wurde, der hinter dem stand DetoxCrypto Virus. Da arbeiten sie ständig und suchen nach einer kostenlosen Entschlüsselungsmethode, Es ist NICHT ratsam, Lösegeld an die Kriminellen zu zahlen, die hinter diesem Virus stehen. Stattdessen, Wir empfehlen Ihnen, es zu entfernen, Verwenden Sie die folgenden Anweisungen und probieren Sie alternative Methoden zum Entschlüsseln Ihrer Dateien aus. Denken Sie daran, dass für maximale Effektivität beim Entfernen von Ransomcuck, Experten empfehlen eine erweiterte Anti-Malware-Programm. Einige alternative Techniken finden Sie in Schritt „3.Wiederherstellen von mit Ransomcuck verschlüsselten Dateien“ weiter unten. Diese temporären Lösungen sind möglicherweise nicht so effektiv wie der eigentliche Entschlüsselungsschlüssel, Sie sind jedoch eine gute Methode, während Sie darauf warten, dass eine kostenlose Entschlüsselung veröffentlicht wird. Wir empfehlen Ihnen, diesen Artikel häufig zu lesen, da wir ihn aktualisieren werden, sobald ein kostenloser Entschlüsseler verfügbar ist.
- Schritt 1
- Schritt 2
- Schritt 3
- Schritt 4
- Schritt 5
Schritt 1: Scannen Sie mit dem SpyHunter Anti-Malware Tool nach Ransomcuck



Automatische Entfernung von Ransomware - Videoanleitung
Schritt 2: Uninstall Ransomcuck and related malware from Windows
Hier ist ein Verfahren, in wenigen einfachen Schritten der in der Lage sein sollte, die meisten Programme deinstallieren. Egal ob Sie mit Windows arbeiten 10, 8, 7, Vista oder XP, diese Schritte werden den Job zu erledigen. Ziehen Sie das Programm oder den entsprechenden Ordner in den Papierkorb kann eine sehr schlechte Entscheidung. Wenn Sie das tun, Bits und Stücke des Programms zurückbleiben, und das kann zu instabilen Arbeit von Ihrem PC führen, Fehler mit den Dateitypzuordnungen und anderen unangenehmen Tätigkeiten. Der richtige Weg, um ein Programm von Ihrem Computer zu erhalten, ist es zu deinstallieren. Um das zu tun:


 Befolgen Sie die obigen Anweisungen und Sie werden die meisten unerwünschten und bösartigen Programme erfolgreich löschen.
Befolgen Sie die obigen Anweisungen und Sie werden die meisten unerwünschten und bösartigen Programme erfolgreich löschen.
Schritt 3: Reinigen Sie alle Register, erstellt von Ransomcuck auf Ihrem Computer.
Die in der Regel gezielt Register von Windows-Rechnern sind die folgenden:
- HKEY_LOCAL_MACHINE Software Microsoft Windows Currentversion Run
- HKEY_CURRENT_USER Software Microsoft Windows Currentversion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows Currentversion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows Currentversion RunOnce
Sie können auf sie zugreifen, indem Sie den Windows-Registrierungs-Editor und löschen Sie alle Werte öffnen, dort von Ransomcuck erstellt. Dies kann passieren, darunter indem Sie die Schritte:


 Spitze: Um einen Virus erstellten Wert zu finden, Sie können sich auf der rechten Maustaste und klicken Sie auf "Ändern" um zu sehen, welche Datei es wird ausgeführt. Ist dies der Virus Speicherort, Entfernen Sie den Wert.
Spitze: Um einen Virus erstellten Wert zu finden, Sie können sich auf der rechten Maustaste und klicken Sie auf "Ändern" um zu sehen, welche Datei es wird ausgeführt. Ist dies der Virus Speicherort, Entfernen Sie den Wert.
Bevor es losgeht "Schritt 4", Bitte booten wieder in den Normalmodus, falls Sie sich gerade im abgesicherten Modus.
Dies ermöglicht es Ihnen, zu installieren und zu Verwendung SpyHunter 5 erfolgreich.
Schritt 4: Starten Sie Ihren PC im abgesicherten Modus, um Ransomcuck zu isolieren und zu entfernen





Schritt 5: Versuchen Sie, mit Ransomcuck verschlüsselte Dateien wiederherzustellen.
Verfahren 1: Verwenden Sie STOP Decrypter von Emsisoft.
Nicht alle Varianten dieser Ransomware können kostenlos entschlüsselt werden, aber wir haben die Entschlüsselungsvorrichtung, die von Forschern hinzugefügt, die häufig mit den Varianten aktualisiert wird, die schließlich entschlüsselt worden. Sie können Ihre Dateien mit den nachstehenden Anweisungen versuchen und entschlüsseln, aber wenn sie nicht funktionieren, leider Ihre Variante der Ransomware Virus dann nicht entschlüsselbar.
Folgen Sie den Anweisungen unten, um den Decrypter Emsisoft zu verwenden und entschlüsseln Sie Ihre Dateien kostenlos. Sie können Download der Emsisoft Entschlüsselungs-Tool verknüpft hier und dann folgen die nachstehenden Schritte zur Verfügung gestellt:
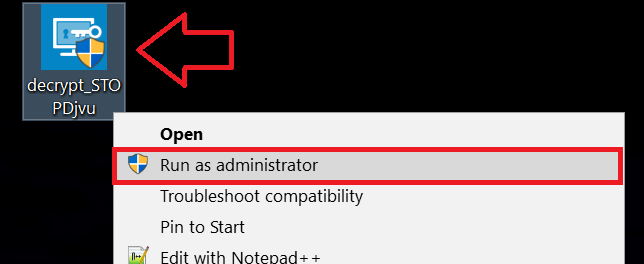
1 Rechtsklick auf dem Decrypter und klicken Sie auf Als Administrator ausführen Wie nachfolgend dargestellt:
2. Vereinbaren Sie mit den Lizenzbedingungen:
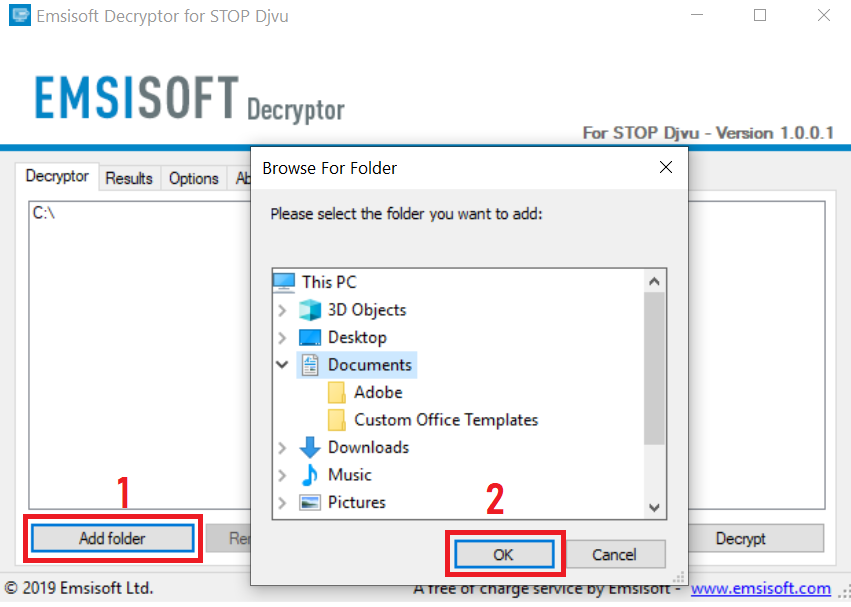
3. Klicke auf "Ordner hinzufügen" und fügen Sie dann die Ordner, in denen Sie Dateien entschlüsselt wollen wie unten gezeigt:
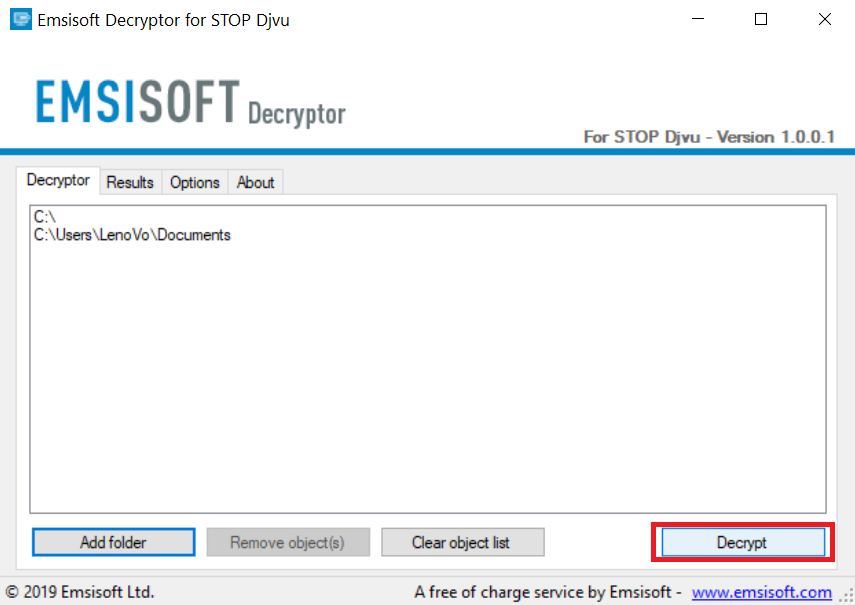
4. Klicke auf "Entschlüsselt" und warten auf Ihre Dateien decodiert werden.
Notiz: Kredit für den decryptor geht Forscher Emsisoft, die den Durchbruch mit diesem Virus gemacht haben.
Verfahren 2: Verwenden Sie eine Datenwiederherstellungssoftware
Ransomware-Infektionen und Ransomcuck zielen darauf ab, Ihre Dateien mit einem Verschlüsselungsalgorithmus zu verschlüsseln, der möglicherweise sehr schwer zu entschlüsseln ist. Dies ist, warum wir ein Datenrückgewinnungsverfahren vorgeschlagen haben, die Sie um direkte Entschlüsselung gehen können helfen und versuchen, Ihre Dateien wiederherstellen. Beachten Sie, dass diese Methode nicht sein kann 100% wirksam, aber Sie können auch ein wenig oder viel in verschiedenen Situationen helfen.
Klicken Sie einfach auf den Link und oben auf die Menüs der Website, wählen Datenwiederherstellung - Datenwiederherstellungs-Assistent für Windows oder Mac (abhängig von Ihrem Betriebssystem), Laden Sie das Tool herunter und führen Sie es aus.
Ransomcuck-FAQ
What is Ransomcuck Ransomware?
Ransomcuck ist ein Ransomware Infektion - Die schädliche Software, die still in Ihren Computer eindringt und entweder den Zugriff auf den Computer selbst blockiert oder Ihre Dateien verschlüsselt.
Viele Ransomware-Viren verwenden ausgefeilte Verschlüsselungsalgorithmen, um Ihre Dateien unzugänglich zu machen. Das Ziel von Ransomware-Infektionen besteht darin, eine Lösegeldzahlung zu verlangen, um wieder auf Ihre Dateien zugreifen zu können.
What Does Ransomcuck Ransomware Do?
Ransomware im Allgemeinen ist ein schädliche Software das ist entworfen um den Zugriff auf Ihren Computer oder Ihre Dateien zu blockieren bis ein Lösegeld gezahlt wird.
Ransomware-Viren können das auch Ihr System beschädigen, Daten beschädigen und Dateien löschen, was zum dauerhaften Verlust wichtiger Dateien führt.
How Does Ransomcuck Infect?
Ransomcuck Ransomware infiziert Computer durch Senden über Phishing-E-Mails, mit Virusanhaftung. Dieser Anhang wird normalerweise als wichtiges Dokument maskiert, wie eine Rechnung, Bankdokument oder sogar ein Flugticket und es sieht für Benutzer sehr überzeugend aus.
Another way you may become a victim of Ransomcuck is if you Laden Sie ein gefälschtes Installationsprogramm herunter, Crack oder Patch von einer Website mit geringer Reputation oder wenn Sie auf einen Virenlink klicken. Viele Benutzer berichten von einer Ransomware-Infektion durch Herunterladen von Torrents.
How to Open .Ransomcuck files?
Sie can't ohne Entschlüsseler. An dieser Stelle, die .Ransomcuck Dateien sind verschlüsselt. Sie können sie erst öffnen, wenn sie mit einem bestimmten Entschlüsselungsschlüssel für den jeweiligen Algorithmus entschlüsselt wurden.
Was tun, wenn ein Entschlüsseler nicht funktioniert??
Keine Panik, und Sichern Sie die Dateien. Wenn ein Entschlüsseler Ihre nicht entschlüsselt hat .Ransomcuck Dateien erfolgreich, dann verzweifle nicht, weil dieser Virus noch neu ist.
Kann ich wiederherstellen ".Ransomcuck" Dateien?
Ja, Manchmal können Dateien wiederhergestellt werden. Wir haben mehrere vorgeschlagen Methoden zur Wiederherstellung von Dateien Das könnte funktionieren, wenn Sie wiederherstellen möchten .Ransomcuck Dateien.
Diese Methoden sind in keiner Weise 100% garantiert, dass Sie Ihre Dateien zurückerhalten können. Aber wenn Sie ein Backup haben, Ihre Erfolgschancen sind viel größer.
How To Get Rid of Ransomcuck Virus?
Der sicherste und effizienteste Weg zur Entfernung dieser Ransomware-Infektion ist die Verwendung von a professionelles Anti-Malware-Programm.
Es sucht nach Ransomcuck-Ransomware, findet sie und entfernt sie dann, ohne Ihren wichtigen .Ransomcuck-Dateien zusätzlichen Schaden zuzufügen.
Kann ich Ransomware den Behörden melden??
Falls Ihr Computer mit einer Ransomware-Infektion infiziert wurde, Sie können es den örtlichen Polizeibehörden melden. Es kann Behörden weltweit dabei helfen, die Täter hinter dem Virus zu verfolgen und zu ermitteln, der Ihren Computer infiziert hat.
Unten, Wir haben eine Liste mit Regierungswebsites erstellt, Hier können Sie einen Bericht einreichen, falls Sie Opfer eines Cyberkriminalität:
Cyber-Sicherheitsbehörden, Verantwortlich für die Bearbeitung von Ransomware-Angriffsberichten in verschiedenen Regionen auf der ganzen Welt:
Deutschland - Offizielles Portal der deutschen Polizei
Vereinigte Staaten - IC3 Internet Crime Complaint Center
Großbritannien - Action Fraud Police
Frankreich - Innenministerium
Italien - Staatliche Polizei
Spanien - Nationale Polizei
Niederlande - Strafverfolgung
Polen - Polizei
Portugal - Justizpolizei
Griechenland - Cyber Crime Unit (Griechische Polizei)
Indien - Polizei von Mumbai - CyberCrime-Untersuchungszelle
Australien - Australisches High Tech Crime Center
Berichte können in unterschiedlichen Zeiträumen beantwortet werden, abhängig von Ihren lokalen Behörden.
Können Sie verhindern, dass Ransomware Ihre Dateien verschlüsselt??
Ja, Sie können Ransomware verhindern. Der beste Weg, dies zu tun, besteht darin, sicherzustellen, dass Ihr Computersystem mit den neuesten Sicherheitspatches aktualisiert wird, Verwenden Sie ein seriöses Anti-Malware-Programm und Firewall, Sichern Sie Ihre wichtigen Dateien regelmäßig, und vermeiden Sie das Anklicken bösartige Links oder unbekannte Dateien herunterladen.
Can Ransomcuck Ransomware Steal Your Data?
Ja, in den meisten Fällen Ransomware wird Ihre Informationen stehlen. It is a form of malware that steals data from a user's computer, verschlüsselt es, und fordert dann ein Lösegeld, um es zu entschlüsseln.
Vielfach, die Malware-Autoren oder Angreifer drohen damit, die Daten zu löschen bzw veröffentlichen Sie es online es sei denn, das Lösegeld wird bezahlt.
Kann Ransomware WLAN infizieren?
Ja, Ransomware kann WLAN-Netzwerke infizieren, da böswillige Akteure damit die Kontrolle über das Netzwerk erlangen können, vertrauliche Daten stehlen, und Benutzer sperren. Wenn ein Ransomware-Angriff erfolgreich ist, Dies könnte zu einem Dienst- und/oder Datenverlust führen, und in einigen Fällen, finanzielle Verluste.
Soll ich Ransomware bezahlen?
Nicht, Sie sollten Ransomware-Erpresser nicht bezahlen. Ihre Zahlung ermutigt nur Kriminelle und garantiert nicht, dass die Dateien oder Daten wiederhergestellt werden. Der bessere Ansatz besteht darin, ein sicheres Backup wichtiger Daten zu haben und von vornherein auf die Sicherheit zu achten.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, Die Hacker haben möglicherweise immer noch Zugriff auf Ihren Computer, Daten, oder Dateien und kann weiterhin damit drohen, sie offenzulegen oder zu löschen, oder sie sogar zur Begehung von Cyberkriminalität nutzen. In einigen Fällen, sie können sogar weiterhin zusätzliche Lösegeldzahlungen verlangen.
Kann ein Ransomware-Angriff erkannt werden??
Ja, Ransomware erkannt werden kann. Anti-Malware-Software und andere fortschrittliche Sicherheitstools kann Ransomware erkennen und den Benutzer warnen wenn es auf einer Maschine vorhanden ist.
Es ist wichtig, über die neuesten Sicherheitsmaßnahmen auf dem Laufenden zu bleiben und die Sicherheitssoftware auf dem neuesten Stand zu halten, um sicherzustellen, dass Ransomware erkannt und verhindert werden kann.
Werden Ransomware-Kriminelle erwischt??
Ja, Ransomware-Kriminelle werden erwischt. Strafverfolgungsbehörden, wie das FBI, Interpol und andere waren erfolgreich dabei, Ransomware-Kriminelle in den USA und anderen Ländern aufzuspüren und strafrechtlich zu verfolgen. Da Ransomware-Bedrohungen weiter zunehmen, ebenso die Durchsetzungstätigkeit.
About the Ransomcuck Research
Die Inhalte, die wir auf SensorsTechForum.com veröffentlichen, this Ransomcuck how-to removal guide included, ist das Ergebnis umfangreicher Recherchen, harte Arbeit und die Hingabe unseres Teams, um Ihnen zu helfen, die spezifische Malware zu entfernen und Ihre verschlüsselten Dateien wiederherzustellen.
Wie haben wir die Recherche zu dieser Ransomware durchgeführt??
Unsere Forschung basiert auf einer unabhängigen Untersuchung. Wir stehen in Kontakt mit unabhängigen Sicherheitsforschern, und als solche, Wir erhalten täglich Updates zu den neuesten Malware- und Ransomware-Definitionen.
Weiter, the research behind the Ransomcuck ransomware threat is backed with Virustotal und die NoMoreRansom Projekt.
Um die Ransomware-Bedrohung besser zu verstehen, Bitte lesen Sie die folgenden Artikel, die sachkundige Details bieten.
Als Website, die sich seitdem der Bereitstellung kostenloser Anweisungen zum Entfernen von Ransomware und Malware widmet 2014, Die Empfehlung von SensorsTechForum lautet: Achten Sie nur auf vertrauenswürdige Quellen.
Wie man vertrauenswürdige Quellen erkennt:
- Immer überprüfen "Über uns" Website.
- Profil des Inhaltserstellers.
- Stellen Sie sicher, dass sich echte Personen hinter der Website befinden und keine falschen Namen und Profile.
- Überprüfen Sie Facebook, Persönliche Profile von LinkedIn und Twitter.