Se sei un utente di Cisco Adaptive Security Appliances (fondazione), probabilmente si dovrebbe dare un'occhiata al loro ultime patch. Le patch stanno affrontando due questioni separate, CVE-2016-1385, un difetto nel parser XML ASA, e CVE-2016-1379, un difetto di esaurimento della memoria del blocco VPN. Si prega di notare che CVE-2016-1385 compromette il software ASA successivo alla versione 9.0. La vulnerabilità può essere sfruttata da remoto.

Maggiori informazioni su CVE-2016-1385
CVE-2016-1385: Descrizione ufficiale
Il software Cisco ASA è interessato da questa vulnerabilità se il sistema è configurato per la versione Internet Key Exchange 1 (IKEv1) o versione Internet Key Exchange 2 (IKEv2) VPN LAN-to-LAN o VPN di accesso remoto IKEv1 o IKEv2 con Layer 2 Protocollo di tunneling e IPsec (L2TP-IPsec), e il comando set validate-icmp-errors è configurato nella mappa crittografica. Il comando set validate-icmp-errors non è configurato per impostazione predefinita.
Cisco dice anche che se l'attaccante ha privilegi amministrativi, l'esposizione non dipenderà dalla configurazione. Se l'attaccante ha accesso a una sessione VPN SSL senza client, il software sarà vulnerabile a CVE-2016-1385 quando “funzionalità VPN SSL senza client e accesso ai file (noto anche come Sfoglia reti) tramite Common Internet File System (CIFS) o FTP è consentito“.
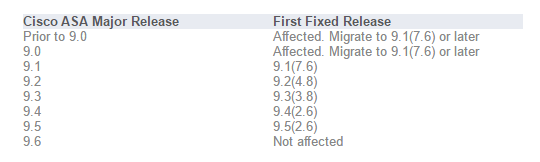
In aggiunta, tutto Rilasci di Cisco Adaptive Security Appliance sono affetti da CVE-2016-1385.

Maggiori informazioni su CVE-2016-1379
CVE-2016-1379: Descrizione ufficiale
Una vulnerabilità nel codice IPsec di Cisco Adaptive Security Appliance (ASA) Il software potrebbe consentire un'autenticazione, aggressore remoto per causare l'esaurimento di un blocco di memoria, che potrebbe causare l'interruzione dell'inoltro del traffico da parte del sistema e il conseguente denial of service (DoS) condizione.
In altre parole, di cosa tratta la vulnerabilità CVE-2016-1379? Il difetto è dovuto a un errore nell'implementazione della gestione degli errori ICMP per i pacchetti IPsec, Cisco dice. Come si può sfruttare il difetto?? Ogni volta che un utente malintenzionato invia pacchetti predisposti tramite un tunnel VPN stabilito da LAN a LA o ad accesso remoto. Se l'attacco ha successo, l'attaccante è in grado di esaurire la memoria disponibile e causare instabilità del sistema. È inoltre possibile impedire al sistema di inoltrare il traffico.
Come già accennato, Rilasci del software Cisco ASA 9.0 e dopo sono influenzato di CVE-2016-1379.
Secondo Cisco, i seguenti prodotti sono interessati e rispettivamente, fisso: