If you’re a user of Cisco’s Adaptive Security Appliances (ASAs), you should probably have a look at their latest patches. The patches are addressing two separate issues, CVE-2016-1385, a flaw in the ASA XML parser, and CVE-2016-1379, a VPN block memory exhaustion flaw. Please note that CVE-2016-1385 compromises ASA software later than version 9.0. The vulnerability can be exploited remotely.

More about CVE-2016-1385
CVE-2016-1385: Official Description
Cisco ASA Software is affected by this vulnerability if the system is configured for Internet Key Exchange Version 1 (IKEv1) or Internet Key Exchange Version 2 (IKEv2) LAN-to-LAN VPN or IKEv1 or IKEv2 Remote Access VPN with Layer 2 Tunneling Protocol and IPsec (L2TP-IPsec), and the set validate-icmp-errors command is configured in the crypto map. The set validate-icmp-errors command is not configured by default.
Cisco also says that if the attacker has administrative privileges, the exposure won’t depend on the configuration. If the attacker has access to a Clientless SSL VPN session, the software will be vulnerable to CVE-2016-1385 when “clientless SSL VPN feature and File Access (also known as Browse Networks) via Common Internet File System (CIFS) or FTP is allowed“.
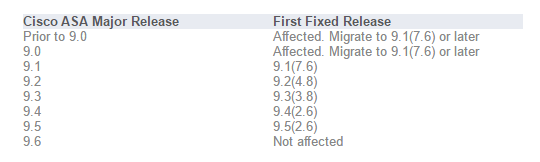
In addition, all Cisco Adaptive Security Appliance releases are affected by CVE-2016-1385.

More about CVE-2016-1379
CVE-2016-1379: Official Description
A vulnerability in the IPsec code of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to cause the depletion of a memory block, which may cause the system to stop forwarding traffic and result in a denial of service (DoS) condition.
In other words, what is the CVE-2016-1379 vulnerability about? The flaw is due to an error in the implementation of ICMP error handling for IPsec packets, Cisco says. How can the flaw be leveraged? Whenever an attacker sends crafted packets via an established LAN-to-LA or remote access VPN tunnel. If the attack is successful, the attacker is enabled to deplete available memory and cause system instability. The system can also be prevented from forwarding traffic.
As already mentioned, Cisco ASA Software releases 9.0 and later are affected by CVE-2016-1379.
According to Cisco, the following products are affected and respectively, fixed: