Se você é um usuário dos dispositivos de segurança adaptáveis da Cisco (Como ... como), você provavelmente deve dar uma olhada em seus patches mais recentes. Os patches estão tratando de dois problemas separados, CVE-2016-1385, uma falha no analisador ASA XML, e CVE-2016-1379, uma falha de esgotamento de memória de bloco VPN. Observe que o CVE-2016-1385 compromete o software ASA posterior à versão 9.0. A vulnerabilidade pode ser explorada remotamente.

Mais sobre CVE-2016-1385
CVE-2016-1385: Descrição Oficial
O software Cisco ASA é afetado por esta vulnerabilidade se o sistema estiver configurado para a versão do Internet Key Exchange 1 (IKEv1) ou versão do Internet Key Exchange 2 (IKEv2) VPN LAN-to-LAN ou VPN de acesso remoto IKEv1 ou IKEv2 com camada 2 Protocolo de encapsulamento e IPsec (L2TP-IPsec), e o comando set validate-icmp-errors é configurado no mapa de criptografia. O comando set validate-icmp-errors não é configurado por padrão.
A Cisco também diz que se o invasor tiver privilégios administrativos, a exposição não dependerá da configuração. Se o invasor tiver acesso a uma sessão de VPN SSL sem cliente, o software estará vulnerável a CVE-2016-1385 quando “recurso de VPN SSL sem cliente e acesso a arquivos (também conhecido como Browse Networks) via sistema de arquivos comum da Internet (CIFS) ou FTP é permitido“.
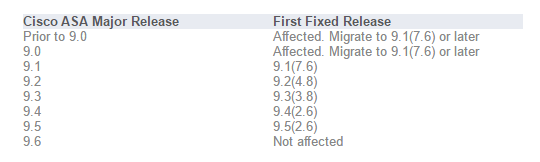
além do que, além do mais, todos Lançamentos do Cisco Adaptive Security Appliance são afetados por CVE-2016-1385.

Mais sobre CVE-2016-1379
CVE-2016-1379: Descrição Oficial
Uma vulnerabilidade no código IPsec do Cisco Adaptive Security Appliance (TÃO) O software pode permitir um autenticado, atacante remoto para causar o esgotamento de um bloco de memória, o que pode fazer com que o sistema pare de encaminhar o tráfego e resultar em negação de serviço (DoS) condição.
Em outras palavras, sobre o que é a vulnerabilidade CVE-2016-1379? A falha é devido a um erro na implementação do tratamento de erros ICMP para pacotes IPsec, Cisco diz. Como a falha pode ser aproveitada? Sempre que um invasor envia pacotes criados por meio de um túnel LAN para LA estabelecido ou túnel VPN de acesso remoto. Se o ataque for bem sucedido, o invasor está habilitado para esgotar a memória disponível e causar instabilidade do sistema. O sistema também pode ser impedido de encaminhar o tráfego.
Como já mencionado, Lançamentos de software Cisco ASA 9.0 e mais tarde são afetado por CVE-2016-1379.
De acordo com Cisco, os seguintes produtos são afetados e respectivamente, fixo: