 Questo articolo è stato creato per spiegare qual è lo scopo della .Virus file LTML e come rimuovere questa infezione dal PC più Come cercare di file che sono stati crittografati ripristino da essa sul vostro computer.
Questo articolo è stato creato per spiegare qual è lo scopo della .Virus file LTML e come rimuovere questa infezione dal PC più Come cercare di file che sono stati crittografati ripristino da essa sul vostro computer.
Proveniente dall'abbreviazione Long Term Memory Loss, questa infezione da ransomware mira a utilizzare l'algoritmo di crittografia AES per crittografare i file importanti sui computer infettati da esso e quindi richiedere una forte tassa di riscatto dalla vittima affinché i file vengano ripristinati al loro stato originale. Nel caso in cui il computer è stato infettato dal .Ransomware LTML virus, nel caso in cui abbia iniziato a infettare le vittime, è probabile che i tuoi file abbiano l'estensione .Estensione del file LTML aggiunto a loro. Se questo è il caso, ti consigliamo di leggere il seguente articolo per sapere come rimuovere questa infezione da ransomware dal tuo computer e come ripristinare i file che sono stati crittografati da .Ransomware LTML sul vostro PC.

Sommario minaccia
| Nome | LTML Virus |
| Tipo | Ransomware, Cryptovirus |
| breve descrizione | Mira a crittografare i file sul computer della vittima tramite algoritmo di crittografia AES. Sviluppato in Visual Studio 2017 |
| Sintomi | Uno dei sintomi principali sono i file crittografati con un'estensione .Suffusso di file LTML a loro. |
| Metodo di distribuzione | Email spam, Allegati e-mail, I file eseguibili |
| Detection Tool |
Verifica se il tuo sistema è stato interessato da malware
Scarica
Strumento di rimozione malware
|
Esperienza utente | Iscriviti alla nostra Forum per discutere di virus LTML. |
| Strumento di recupero dati | Windows Data Recovery da Stellar Phoenix Avviso! Questo prodotto esegue la scansione settori di unità per recuperare i file persi e non può recuperare 100% dei file crittografati, ma solo pochi di essi, a seconda della situazione e se non è stato riformattato l'unità. |

.Virus file LTML - Come sono stato infettato
Per diventare una vittima di questo virus ransomware, possono essere possibili diversi scenari, la più probabile delle quali è aprire un allegato di posta elettronica dannoso inviato al tuo computer a seguito di essere ingannato da un messaggio di posta elettronica di spam. Tali messaggi contengono spesso testi ingannevoli, con l'obiettivo di convincere gli utenti che i loro allegati sono documenti importanti come:
- Fatture.
- ricevute.
- Conferma dell'ordine.
- Altro file importante.
In aggiunta a questo, le e-mail possono anche fingere di provenire anche da grandi aziende, come:
- FedEx.
- PayPal.
- Dropbox.
- eBay.
- Amazon.
Gli allegati stessi sono generalmente file eseguibili o documet per Microsoft Office che potrebbero contenere macro dannose incorporate al loro interno che attivano il processo di infezione. È sempre consigliabile eseguire la scansione di tali allegati di posta elettronica prima di aprirli effettivamente.
Oltre alla via e-mail, questa infezione da ransomware può anche essere diffusa tramite altri metodi, come:
- Configurazione falsa del software.
- Programma di attivazione del software falso.
- generatore di chiavi (keygen).
- Crack fix per programmi o giochi.
- Attivatori di licenza per vari programmi.

.LTML Ransomware - Ulteriori informazioni e attività
Il .Ransomware LTML è ancora in fase di sviluppo ma potrebbe aver già iniziato a infettare le vittime. Il malware può avviare il processo di infezione connettendosi a un host remoto e scaricando il payload dannoso. Questo payload è costituito da diversi file di modulo che aiutano il virus ransomware ad aumentare i suoi privilegi e a condurre le sue attività dannose senza interruzioni. I file possono essere sotto nomi diversi, come:
- Un nome, imitando un programma sul tuo computer.
- Un nome alfanumerico completamente casuale che ha anche lettere maiuscole e minuscole.
- Nome del virus ransomware (LTML).
I file possono trovarsi in varie cartelle differenti in Windows, ma i più mirati di questi sono i seguenti:
- %AppData%
- %Roaming%
- %Del posto%
- %Temp%
- %LocalLow%
- %Finestre%
- %System32%
In aggiunta a questo, il ransomware LTML può anche creare voci di registro nelle seguenti sottochiavi di registro di Windows:
→ HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Questo è probabilmente fatto con lo scopo di rendere possibile in modo che i file dannosi del ransomware LTML vengano eseguiti automaticamente sul sistema del computer non appena viene avviato Windows. Oltre a quelle chiavi, il virus può anche aggiungere voci di registro nelle seguenti sottochiavi per aumentare molti dei suoi privilegi:
→ HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows CurrentVersion Autenticazione LogonUI Background
HKEY_LOCAL_MACHINE Software Policies Microsoft Windows Personalizzazione
HKEY_CURRENT_USER Control Panel Desktop ScreenSaveTimeOut
HKEY_CURRENT_USER Control Panel Desktop
Inoltre, il virus LTML può anche eliminare le copie shadow del volume sul computer infetto eseguendo i seguenti comandi amministrativi nel prompt dei comandi di Windows senza che tu te ne accorga:
→ chiamata processo di creare “cmd.exe / c Vssadmin.exe eliminare ombre / all / quiet & bcdedit.exe / set {predefinito} recoveryenabled no & bcdedit.exe / set {predefinito} ignoreallfailures bootstatuspolicy”
Non appena vengono eseguiti i file dannosi di questo virus ransomware, inizia le procedure di crittografia.

LTML Ransomware – crittografia
Al fine di crittografare i file sui computer che sono stati infettati da esso, il virus ransomware LTML può iniziare la scansione di vari tipi di file che vengono utilizzati molto spesso sul computer della vittima. Tali file includono:
- Documenti.
- Video.
- Immagini.
- Archivio.
- file Virtual Drive.
- file Adobe.
Il virus esegue la scansione per l'estensione del file dei file, il che significa che i seguenti tipi di file possono essere a rischio di crittografia, se il tuo computer viene infettato da LTML:
"PNG .PSD .PspImage .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF xlr .XLS .XLSX .accdb .DB DBF MDB PDB .SQL .apk .APP bat .cgi .COM .EXE .gadget .JAR PIF wsf .DEM .gam .NES .ROM .SAV CAD .dwg .DXF GIS file .GPX .KML .KMZ .ASP ASPX .CER .CFM .CSR .CSS .HTM .HTML .JS .jsp .PHP .rss .xhtml. DOC DOCX .LOG .MSG .ODT .pagine .RTF .tex .TXT .WPD .WPS .CSV .DAT .ged .KEY .keychain .PPS .PPT PPTX ini .PRF .HQX .mim .uue .7z. CBR .deb .GZ .PKG .RAR .rpm .sitx .TAR.GZ .ZIP .ZIPX BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML file audio .AIF .IFF .M3U .M4A .MID .MP3 .mpa WAV WMA file video .3g2 .3GP .ASF .AVI FLV .m4v .MOV .MP4 .MPG .RM .SRT .SWF VOB WMV .3dm 3D. 3DS .MAX obj R.BMP .DDS .GIF .JPG ..CRX .PLUGIN .FNT .FON .OTF .TTF CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV ICNS .ICO .LNK .SYS. CFG”
Per crittografare i file sul computer infetto, il virus ransomware LTML utilizza uno dei più potenti algoritmi di crittografia disponibili pubblicamente in circolazione, noto come AES (Advanced Encryption Standard). Genera una crittografia automatica dei file e chiavi di decrittazione simmetriche casuali per ciascuna infezione. Le informazioni possono quindi essere inviate ai cyber-criminali il cui scopo principale è quello di venderti un decrypter per farti pagare una forte tassa di riscatto per ottenerlo. I file crittografati possono avere l'estensione .LTML e possono apparire come l'immagine qui sotto:

Come rimuovere LTML Ransomware e ripristinare i file
Al fine di rimuovere virus ransowmare come LTML, è importante isolarli dall'essere operativa. Per farlo, si consiglia di seguire le istruzioni di rimozione in basso. Essi sono separati nelle istruzioni automatiche e manuali di rimozione. Se ti manca l'esperienza in di rimozione malware, si consiglia di rimuovere automaticamente LTML ransowmare preferibilmente scaricando un software anti-malware avanzato. Ciò garantirà che il tuo computer sia libero da tutti i malware senza dover reinstallare Windows e proteggerà il tuo computer da infezioni come LTML anche in futuro.
Se desideri ripristinare i file che sono stati crittografati dalle infezioni ransomware LTML, ti consigliamo vivamente di concentrarti sulla prova dei nostri metodi alternativi di recupero da ransomware nel passaggio "2.Ripristina i file crittografati da LTML Virus" di seguito. Questi metodi non sono 100% garantire che si sarà in grado di ripristinare tutti i file crittografati da questo virus, ma possono aiutare a recuperare almeno una parte dei dati codificati.
- Passo 1
- Passo 2
- Passo 3
- Passo 4
- Passo 5
Passo 1: Scansione per virus LTML con lo strumento SpyHunter Anti-Malware



Rimozione automatica ransomware - Videoguida
Passo 2: Uninstall LTML Virus and related malware from Windows
Ecco un metodo in pochi semplici passi che dovrebbero essere in grado di disinstallare maggior parte dei programmi. Non importa se si utilizza Windows 10, 8, 7, Vista o XP, quei passi otterrà il lavoro fatto. Trascinando il programma o la relativa cartella nel cestino può essere un molto cattiva decisione. Se lo fai, frammenti di programma vengono lasciati, e che possono portare al lavoro instabile del PC, errori con le associazioni di tipo file e altre attività spiacevoli. Il modo corretto per ottenere un programma dal computer è di disinstallarlo. Per fare questo:


 Segui le istruzioni sopra e cancellerai con successo la maggior parte dei programmi indesiderati e dannosi.
Segui le istruzioni sopra e cancellerai con successo la maggior parte dei programmi indesiderati e dannosi.
Passo 3: Pulire eventuali registri, creato da LTML Virus sul tuo computer.
I registri di solito mirati di macchine Windows sono i seguenti:
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
È possibile accedere aprendo l'editor del registro di Windows e l'eliminazione di tutti i valori, creato da LTML Virus lì. Questo può accadere seguendo la procedura sotto:


 Mancia: Per trovare un valore virus creato, è possibile fare clic destro su di esso e fare clic su "Modificare" per vedere quale file è impostato per funzionare. Se questa è la posizione file del virus, rimuovere il valore.
Mancia: Per trovare un valore virus creato, è possibile fare clic destro su di esso e fare clic su "Modificare" per vedere quale file è impostato per funzionare. Se questa è la posizione file del virus, rimuovere il valore.
Prima di cominciare "Passo 4", Per favore l'avvio in modalità normale, nel caso in cui siete attualmente in modalità provvisoria.
Questo vi permetterà di installare e uso SpyHunter 5 con successo.
Passo 4: Avvia il tuo PC in modalità provvisoria per isolare e rimuovere LTML Virus





Passo 5: Prova a ripristinare i file crittografati da LTML Virus.
Metodo 1: Utilizza STOP Decrypter di Emsisoft.
Non tutte le varianti di questo ransomware possono essere decifrati gratis, ma abbiamo aggiunto il decryptor utilizzato dai ricercatori che viene spesso aggiornato con le varianti che diventano poi decifrati. Si può cercare di decifrare i file utilizzando le istruzioni riportate di seguito, ma se non funzionano, poi purtroppo la vostra variante del virus ransomware non è decifrabile.
Seguire le istruzioni riportate di seguito per utilizzare il decrypter Emsisoft e decrittografare i file gratuitamente. Puoi scaricare lo strumento di decrittazione Emsisoft legata qui e quindi seguire i passaggi indicati di seguito:
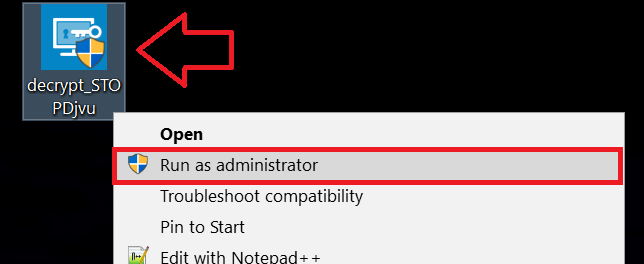
1 Pulsante destro del mouse sulla Decrypter e cliccare su Esegui come amministratore come mostrato di seguito:
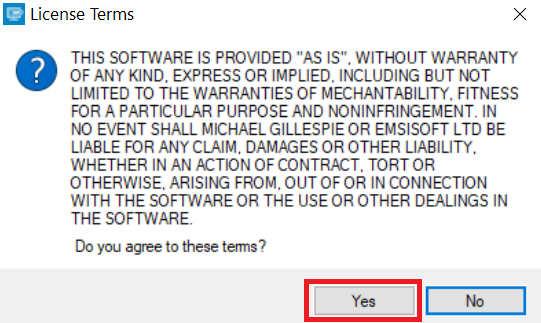
2. D'accordo con i termini della licenza:
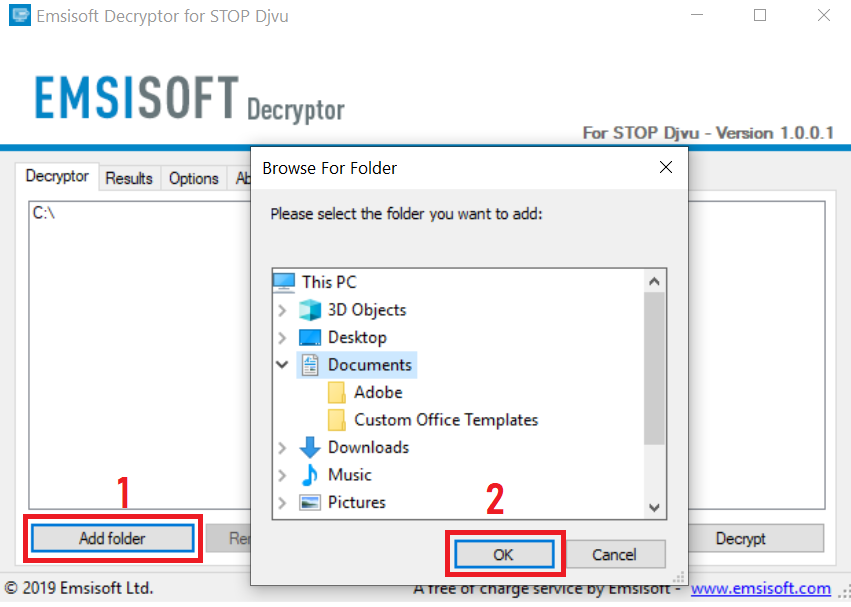
3. Clicca su "Aggiungi cartella" e poi aggiungere le cartelle in cui si desidera i file decriptati come mostrato sotto:
4. Clicca su "decrypt" e attendere che i file da decodificare.
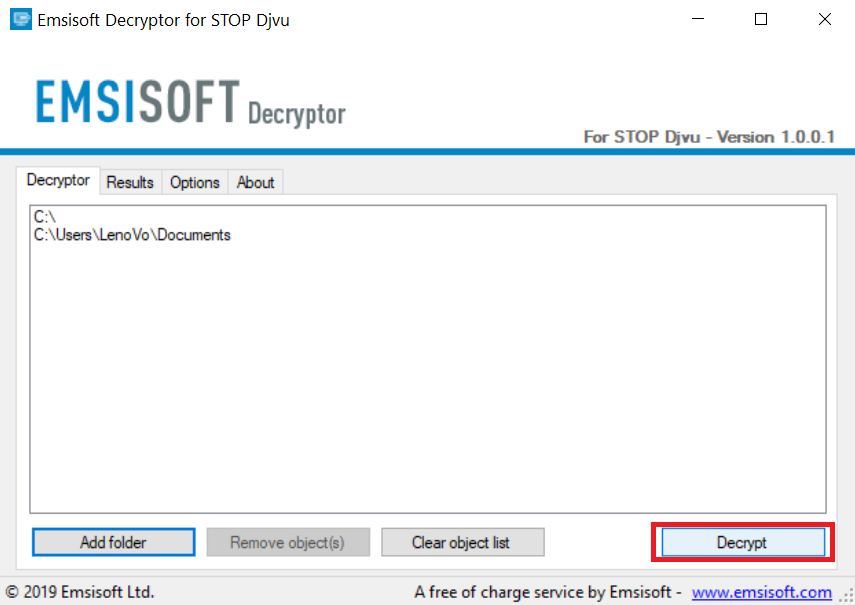
Nota: Credito per il decryptor va a Emsisoft ricercatori che hanno fatto il passo avanti con questo virus.
Metodo 2: Utilizzare un software di recupero dati
Le infezioni ransomware e LTML Virus mirano a crittografare i file utilizzando un algoritmo di crittografia che potrebbe essere molto difficile da decrittografare. Questo è il motivo per cui abbiamo suggerito un metodo di recupero di dati che possono aiutare a andare in giro decrittazione diretta e cercare di ripristinare i file. Tenete a mente che questo metodo non può essere 100% efficace, ma può anche aiutare un po 'o molto in situazioni diverse.
Basta cliccare sul link e sui menu del sito in alto, scegliere Recupero dati - Procedura guidata di recupero dati per Windows o Mac (a seconda del tuo sistema operativo), e quindi scaricare ed eseguire lo strumento.
LTML Virus-FAQ
What is LTML Virus Ransomware?
LTML Virus è un file ransomware infezione - il software dannoso che entra silenziosamente nel tuo computer e blocca l'accesso al computer stesso o crittografa i tuoi file.
Molti virus ransomware utilizzano sofisticati algoritmi di crittografia per rendere inaccessibili i tuoi file. L'obiettivo delle infezioni da ransomware è richiedere il pagamento di un riscatto per ottenere l'accesso ai file.
What Does LTML Virus Ransomware Do?
Il ransomware in generale è un software dannoso quello è progettato per bloccare l'accesso al tuo computer o ai tuoi file fino al pagamento del riscatto.
Anche i virus ransomware possono danneggiare il tuo sistema, corrompere i dati ed eliminare i file, con conseguente perdita permanente di file importanti.
How Does LTML Virus Infect?
In diversi modi LTML Virus Ransomware infetta i computer inviandoli tramite e-mail di phishing, contenente allegato virus. Questo allegato è di solito mascherato come documento importante, come una fattura, documento bancario o anche un biglietto aereo e sembra molto convincente per gli utenti.
Another way you may become a victim of LTML Virus is if you scaricare un programma di installazione falso, crack o patch da un sito Web con bassa reputazione o se si fa clic sul collegamento di un virus. Molti utenti segnalano di avere un'infezione da ransomware scaricando torrent.
How to Open .LTML Virus files?
tu can't senza decrittatore. A questo punto, il .LTML Virus file sono criptato. Puoi aprirli solo dopo che sono stati decrittografati utilizzando una chiave di decrittografia specifica per il particolare algoritmo.
Cosa fare se un decryptor non funziona?
Niente panico, e eseguire il backup dei file. Se un decryptor non ha decifrato il tuo .LTML Virus file correttamente, quindi non disperare, perché questo virus è ancora nuovo.
Posso ripristinare ".LTML Virus" File?
Sì, a volte i file possono essere ripristinati. Ne abbiamo suggeriti diversi metodi di recupero file che potrebbe funzionare se si desidera ripristinare .LTML Virus file.
Questi metodi non sono in alcun modo 100% garantito che sarai in grado di recuperare i tuoi file. Ma se hai un backup, le tue possibilità di successo sono molto maggiori.
How To Get Rid of LTML Virus Virus?
Il modo più sicuro e più efficace per la rimozione di questa infezione da ransomware è l'uso a programma anti-malware professionale.
Eseguirà la scansione e individuerà il ransomware LTML Virus, quindi lo rimuoverà senza causare ulteriori danni ai tuoi file importanti .LTML Virus.
Posso segnalare il ransomware alle autorità?
Nel caso in cui il tuo computer sia stato infettato da un'infezione da ransomware, puoi segnalarlo ai dipartimenti di Polizia locale. Può aiutare le autorità di tutto il mondo a rintracciare e determinare gli autori del virus che ha infettato il tuo computer.
Sotto, abbiamo preparato un elenco con i siti web del governo, dove puoi presentare una segnalazione nel caso in cui sei vittima di un file criminalità informatica:
Autorità di sicurezza informatica, responsabile della gestione dei rapporti sugli attacchi ransomware in diverse regioni del mondo:
Germania - Portale ufficiale della polizia tedesca
stati Uniti - IC3 Internet Crime Complaint Center
Regno Unito - Polizia antifrode
Francia - Ministro degli Interni
Italia - Polizia Di Stato
Spagna - Polizia nazionale
Paesi Bassi - Forze dell'ordine
Polonia - Polizia
Portogallo - Polizia giudiziaria
Grecia - Unità per la criminalità informatica (Polizia ellenica)
India - Polizia di Mumbai - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
È possibile rispondere ai rapporti in tempi diversi, a seconda delle autorità locali.
Puoi impedire al ransomware di crittografare i tuoi file?
Sì, puoi prevenire il ransomware. Il modo migliore per farlo è assicurarsi che il sistema del computer sia aggiornato con le ultime patch di sicurezza, utilizzare un programma anti-malware affidabile e firewall, eseguire frequentemente il backup dei file importanti, ed evitare di fare clic su link malevoli o il download di file sconosciuti.
Can LTML Virus Ransomware Steal Your Data?
Sì, nella maggior parte dei casi ransomware ruberà le tue informazioni. It is a form of malware that steals data from a user's computer, lo crittografa, e poi chiede un riscatto per decifrarlo.
In molti casi, il autori di malware o gli aggressori minacciano di eliminare i dati o pubblicalo online a meno che non venga pagato il riscatto.
Il ransomware può infettare il WiFi?
Sì, il ransomware può infettare le reti WiFi, poiché gli attori malintenzionati possono usarlo per ottenere il controllo della rete, rubare dati riservati, e bloccare gli utenti. Se un attacco ransomware ha successo, potrebbe portare alla perdita del servizio e/o dei dati, e in alcuni casi, perdite finanziarie.
Dovrei pagare ransomware?
No, non dovresti pagare gli estorsori di ransomware. Il loro pagamento incoraggia solo i criminali e non garantisce che i file oi dati verranno ripristinati. L'approccio migliore consiste nell'avere un backup sicuro dei dati importanti ed essere vigili sulla sicurezza in primo luogo.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, gli hacker potrebbero ancora avere accesso al tuo computer, dati, o file e potrebbe continuare a minacciare di esporli o eliminarli, o addirittura usarli per commettere crimini informatici. In alcuni casi, potrebbero persino continuare a richiedere pagamenti di riscatto aggiuntivi.
È possibile rilevare un attacco ransomware?
Sì, ransomware può essere rilevato. Software anti-malware e altri strumenti di sicurezza avanzati può rilevare il ransomware e avvisare l'utente quando è presente su una macchina.
È importante rimanere aggiornati sulle ultime misure di sicurezza e mantenere aggiornato il software di sicurezza per garantire che il ransomware possa essere rilevato e prevenuto.
I criminali ransomware vengono catturati?
Sì, i criminali ransomware vengono catturati. Le forze dell'ordine, come l'FBI, L'Interpol e altri sono riusciti a rintracciare e perseguire i criminali di ransomware negli Stati Uniti e in altri paesi. Mentre le minacce ransomware continuano ad aumentare, così fa l'attività di esecuzione.
About the LTML Virus Research
I contenuti che pubblichiamo su SensorsTechForum.com, this LTML Virus how-to removal guide included, è il risultato di ricerche approfondite, duro lavoro e la dedizione del nostro team per aiutarti a rimuovere il malware specifico e ripristinare i tuoi file crittografati.
Come abbiamo condotto la ricerca su questo ransomware??
La nostra ricerca si basa su un'indagine indipendente. Siamo in contatto con ricercatori di sicurezza indipendenti, e come tale, riceviamo aggiornamenti quotidiani sulle ultime definizioni di malware e ransomware.
Inoltre, the research behind the LTML Virus ransomware threat is backed with VirusTotal e la progetto NoMoreRansom.
Per comprendere meglio la minaccia ransomware, si prega di fare riferimento ai seguenti articoli che forniscono dettagli informati.
Come sito dedicato da allora a fornire istruzioni di rimozione gratuite per ransomware e malware 2014, La raccomandazione di SensorsTechForum è di prestare attenzione solo a fonti affidabili.
Come riconoscere fonti affidabili:
- Controlla sempre "Riguardo a noi" pagina web.
- Profilo del creatore di contenuti.
- Assicurati che dietro al sito ci siano persone reali e non nomi e profili falsi.
- Verifica Facebook, Profili personali di LinkedIn e Twitter.













