De acordo com o FBI, embuste um BEC, ou um compromisso golpe Negócios Email, é uma fraude on-line sofisticado que tem como alvo empresas trabalhando com fornecedores estrangeiros e regularmente realizando pagamentos de transferência bancária. Também conhecida como uma farsa Man-in-the-mail, O BEC se tornou uma das principais ameaças cibernéticas, colocando em risco as finanças de uma empresa e a segurança online.
No período entre outubro 2013 e agosto 2015, scams BEC causaram perdas a empresas dos EUA Na quantia de $750 Milhão de dolares, deixando mais do que 7,000 vítimas em desespero. Outro relatório indica que os cibercriminosos ganharam aproximadamente $50 milhões de dólares de vítimas em todo o mundo.
Qual é a magnitude dos golpes de BEC em 2016?
Um dos golpes de BEC mais recentes causou estragos no exterior, uma vez que leva à perda de um fundo de investimento $6 milhões para tal fraude. O caso literalmente se transformou em uma batalha, como uma ação judicial foi movida há vários dias pelo Tillage Commodities Fund. O processo alega que SS&A Tecnologia C mostrou uma flagrante falta de diligência e cuidado, quando foram enganados por um golpe de e-mail que levou os hackers na China a obter $5.9 milhão.
De acordo com a lavoura, WL&C não apenas não cumpriu com suas próprias políticas, mas também ajudou os criminosos corrigindo ordens de transferência que haviam falhado inicialmente. Os documentos eram publicado online para todos verem.
É claro que o caso não é apenas sobre o roubo em si, mas também sobre uma desintegração da política corporativa e desconsideração da segurança de dados e ativos.
WL&C tem diretrizes internas focadas especificamente na detecção e proteção contra golpes de comprometimento de e-mail comercial. Os funcionários são instruídos a inspecionar todos os campos de e-mail (como para:, CC:, De:) por sinais de fraude ou spoofing.
WL&C também exigiu que quatro pessoas aprovassem os pedidos de transferência do fundo de lavoura, e pediu ao Tillage para verificar os desembolsos anexando uma fatura para apoiar a despesa ou no caso de resgate, fornecer cartas de resgate e instruções de investidores de fundos, SCMagazine escreve.
Se as políticas tivessem sido seguidas, o BEC poderia ter sido evitado, documentos mostram. Em março 3, 2016, algo deu terrivelmente errado e não deu certo. Foi quando os golpistas estavam mirando na conta bancária do Tillage e começaram a solicitar transferências para a conta bancária de Hong Kong de um “vagamente identificado” empresa de tecnologia. O processo alega que todo o esquema foi executado por fraudadores inexperientes e até mesmo soletrou o nome Tillage errado. Isso deveria ter servido como uma indicação clara de tentativas de fraude. Além disso, os e-mails continham “sintaxe inadequada e erros gramaticais - que eram totalmente inconsistentes com as comunicações anteriores de preparo do solo - e que eram totalmente obscuros em substância.”
O que é pior é que este definitivamente não é o primeiro golpe de BEC que causou milhões de dólares em perdas de negócios. Mas é de fato um caso que tem chamado a atenção da mídia internacional e que deve servir de alerta.
O caso do cultivo à parte, como exatamente um BEC é realizado? Como um golpe de BEC é iniciado?
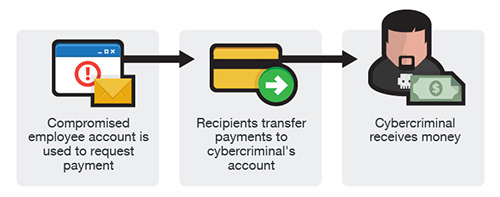
O BEC geralmente começa com um fraudador comprometendo a conta de e-mail de um executivo de negócios. Um e-mail listado publicamente também pode ser direcionado. Para fazê-lo, o fraudador empregaria um keylogger e truques de phishing. Seria criado um domínio muito semelhante ao da empresa-alvo. Ou um e-mail falsificado seria enviado que levaria o alvo a fornecer os detalhes da conta. Então, o fraudador tentaria descobrir quem inicia as transferências eletrônicas e quem as solicita. Em muitos casos, o fraudador gastaria muitas horas pesquisando para localizar uma empresa que mudou de liderança no departamento financeiro. Outro alvo preferencial seria uma empresa onde os executivos viajam muito.
A pesquisa da TrendMicro ilustra três tipos básicos de golpes de BEC:
O Esquema de Fatura BEC do Bogus
Este tipo de BEC geralmente envolve uma empresa que tem um relacionamento estabelecido com um fornecedor. O fraudador pede para transferir fundos para o pagamento da fatura a um alternativo, conta fraudulenta por meio de e-mail falsificado, Telefone, ou fac-símile.
O Golpe do Executivo de Negócios BEC
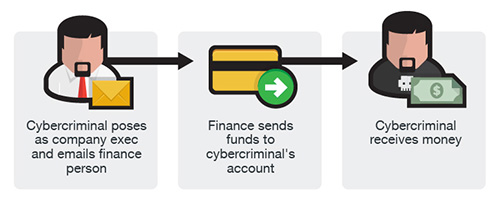
Os fraudadores se identificam como executivos de alto nível (Diretor Financeiro, CEO, CTO, etc.), advogados, ou outros tipos de representantes legais e pretendem estar lidando com assuntos confidenciais ou urgentes e iniciam uma transferência eletrônica para uma conta que controlam. Em alguns casos, a solicitação fraudulenta de transferência eletrônica é enviada diretamente para a instituição financeira com instruções para enviar fundos com urgência para um banco.
O Golpe de Múltiplos Fornecedores BEC
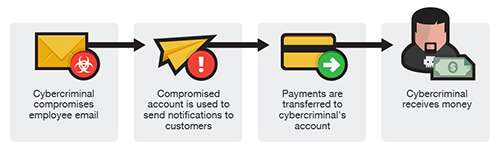
Semelhante às outras duas versões, uma conta de e-mail de um funcionário é invadida e usada para fazer solicitações de pagamentos de faturas para contas bancárias controladas por fraudadores. As mensagens são enviadas para vários fornecedores identificados na lista de contatos do funcionário. A empresa pode não tomar conhecimento do esquema até que seus fornecedores façam o acompanhamento para verificar o status do pagamento da fatura.
Crescimento de ataques de BEC e ransomware – Emails são o vetor de ataque número um
De acordo com vários relatórios de cibersegurança, e-mails se tornaram o vetor de infecção número um. Dito, Os golpes de BEC e infecções de ransomware têm sido uma grande ameaça para as empresas em todo o mundo.
Em casos recentes, infecções de ransomware geralmente começam por e-mail, com muitas famílias de ransomware escolhendo spam como o método de entrega de seu malware. Mas os golpes de BEC já provaram ser muito lucrativos, como visível pelo caso de cultivo. Tanto usuários quanto empresas estão sendo direcionados em vários níveis, drenando finanças e extorquindo dinheiro.
Já escrevemos muitos artigos sobre prevenção ransomware e proteção.
E quanto à prevenção de golpes de BEC?
Em geral, soluções de segurança pesquisam documentos maliciosos ou URLs conhecidos na lista negra para determinar se um e-mail é suspeito. BEC scam emails, Contudo, muitas vezes carecem de quaisquer sinais que revelariam intenções maliciosas. Os golpes de BEC dependem principalmente de engenharia social e exploram as fraquezas dos funcionários, e são altamente direcionados. Contudo, o fato de que BEC e phishing compartilham algumas semelhanças dá aos usuários (e empregados) a chance de monitorar sinais específicos no conteúdo de tais e-mails, como apontado por Proofpoint pesquisadores:
- Executivos de alto nível pedindo informações incomuns;
- Solicitações para não se comunicar com outras pessoas,
- Solicitações que ignoram os canais normais;
- Problemas de idioma e formatos de data incomuns;
- Endereços “Responder para” que não correspondem aos endereços do remetente;
Além disso, além de educar seus funcionários (CEOs incluídos!), as empresas devem olhar para os serviços de proteção de e-mail e aplicativos fornecidos por fornecedores de segurança. A proteção de e-mail é “O agora” de segurança online.b