Um ataque DDoS / botnet muito intrigante e intenso acaba de ser investigado por pesquisadores de segurança da fornecedora de segurança norte-americana Sucuri. O botnet em questão é composto por mais de 25,000 bots que visam empresas em nível global. Mais especificamente, é uma camada 7 Ataque DDoS que engolfa servidores da web e bloqueia seus sites. Os ataques continuaram por dias. Quanto mais pesquisadores mergulharam em suas análises, os detalhes mais curiosos que encontraram.
À medida que extraímos a geolocalização dos endereços IP que geram o DDoS, notamos que eles vinham de todo o mundo, diferentes países e redes. Um total de 25,513 endereços IP únicos chegaram em algumas horas.
O que os pesquisadores da Sucuri descobriram sobre os ataques?
A pesquisa indica que o botnet consiste em sistemas CCTV internacionais comprometidos situados em vários locais ao redor do globo. A primeira colisão que Sucuri teve com o botnet aconteceu quando uma joalheria foi submetida a um ataque DDoS contínuo. O site da empresa foi movido para o WAF da Sucuri (Application Firewall Web).
Contudo, as coisas não param por aí, enquanto os ataques continuavam. Como já dissemos, o ataque inicial foi uma camada 7 DDoS um (Com mais de 35,000 Solicitações HTTP por segundo). O invasor percebeu rapidamente a proteção WAF e acelerou as coisas para 50,000 pedidos / segundo.
A fonte do ataque concentrou-se em Taiwan, com 24% do endereço IP, seguido pelos EUA com 12%, Indonésia com 9%, México com 8% e Malásia com 6%. O topo 10 os países com os dispositivos CCTV mais comprometidos usados neste ataque foram: Taiwan, EUA, Indonésia, México, Malásia, Israel, Itália, Vietnã, França.
IoT Botnet Alavancando CCTVs?
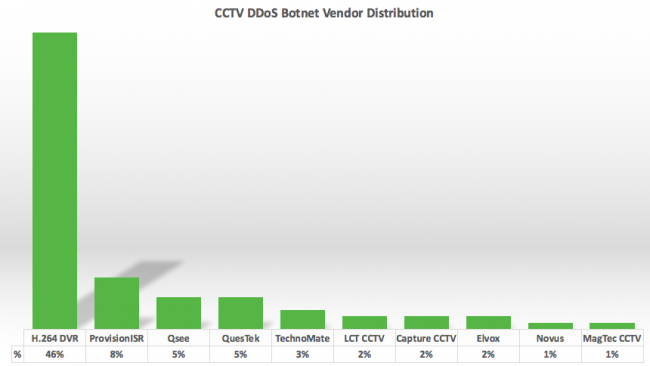
À medida que a pesquisa se aprofundava nos endereços IP, ficou claro que todos eles estavam executando o Cross Web Server, e todos tinham uma página HTTP padrão semelhante, contendo um título de componentes DVR. Foi quando os pesquisadores perceberam que provavelmente estavam lidando com um botnet IoT aproveitando CCTVs como parte do vetor de ataque. Mais longe, eles descobriram os logotipos da empresa dos revendedores e fabricantes em todos os endereços IP.
A Sucuri acredita que todos os dispositivos estão associados à investigação do pesquisador de segurança RSA Rotem Kerner Rotem Kerner, que descobriu uma porta dos fundos no firmware de 70 Fornecedores de CCTV DVR.
A Sucuri está atualmente em processo de contato com as redes que usam as câmeras comprometidas. Contudo, mesmo quando as câmeras afetadas são corrigidas, os invasores podem encontrar facilmente outros dispositivos para incluir em seus botnets. É por isso que as empresas devem pensar em proteção DDoS adequada.